* initialcut Signed-off-by: Gordonby <gordon.byers@microsoft.com> * formatting Signed-off-by: Gordonby <gordon.byers@microsoft.com> * removing externaldns for war Signed-off-by: Gordonby <gordon.byers@microsoft.com> * reframed war ingress Signed-off-by: Gordonby <gordon.byers@microsoft.com> * remove dns and reorder Signed-off-by: Gordonby <gordon.byers@microsoft.com> * reformatted the ingress options Signed-off-by: Gordonby <gordon.byers@microsoft.com> * fixed param and promoted NatGw out of preview flag Signed-off-by: Gordonby <gordon.byers@microsoft.com> * postdeploy check ingress on affirmitive Signed-off-by: Gordonby <gordon.byers@microsoft.com> Signed-off-by: Gordonby <gordon.byers@microsoft.com> |
||
|---|---|---|
| .devcontainer | ||
| .github | ||
| .vscode | ||
| bicep | ||
| docs | ||
| helper | ||
| postdeploy | ||
| samples | ||
| .gitignore | ||
| CODE_OF_CONDUCT.md | ||
| CONTRIBUTING.md | ||
| LICENSE | ||
| README.md | ||
| SECURITY.md | ||
| SUPPORT.md | ||
| cspell.json | ||
| ps-rule.yaml | ||
| referencearchs.md | ||
README.md
AKS Accelerator
Building a complete Kubernetes operational environment is hard work! AKS Accelerator dramatically speeds up this work by providing the templates and deployment scripts to quickly create a fully configured, Kubernetes environment, tailored to meet your operational and security needs, ready to run your workloads in production.
QuickStart
-
Step 1
Navigate to the AKS Construction helper
-
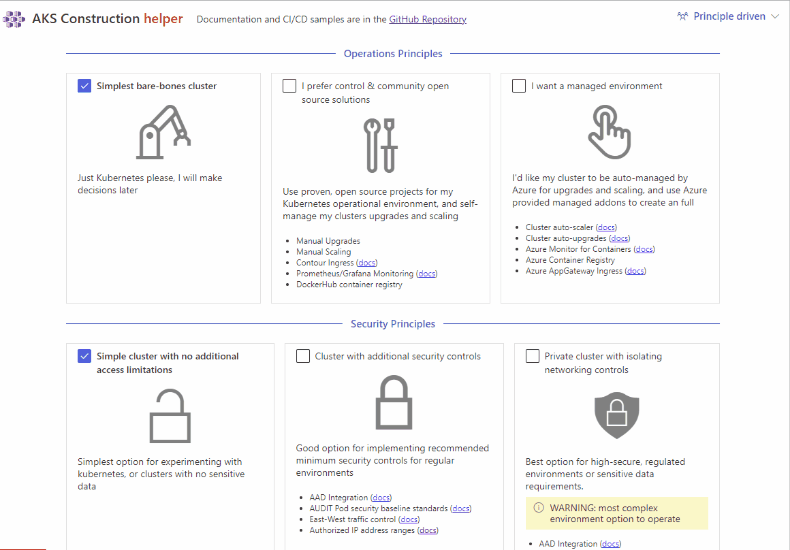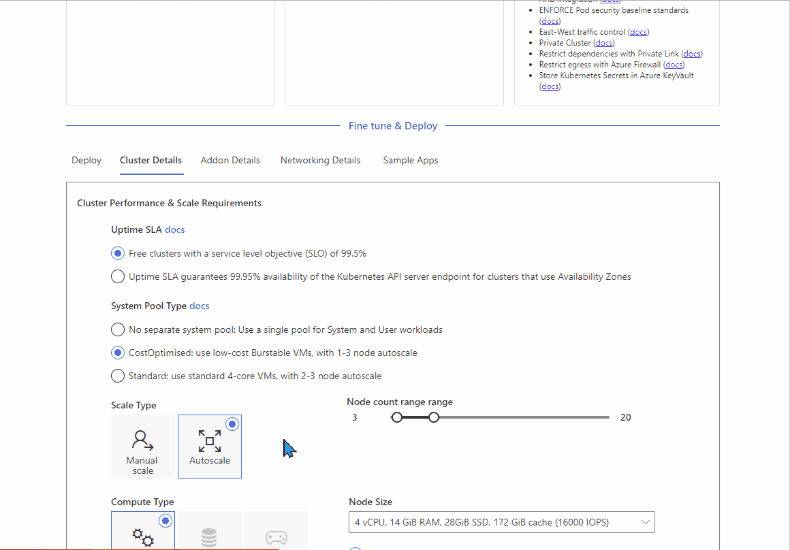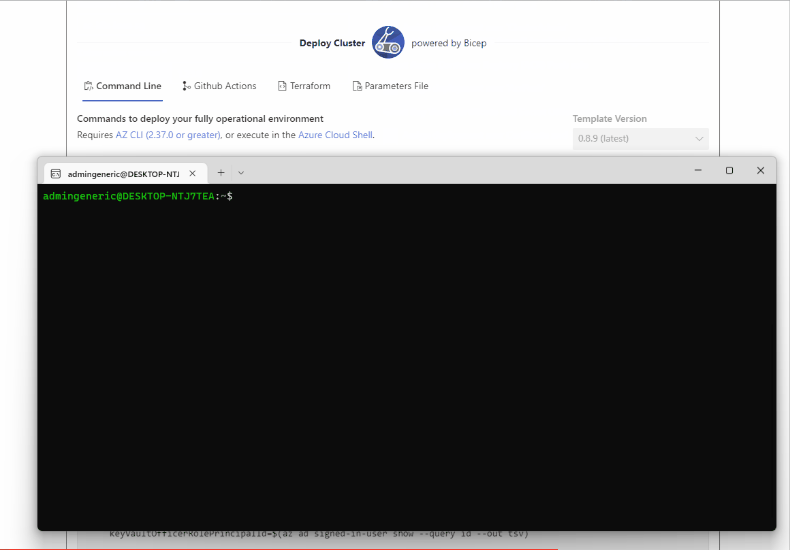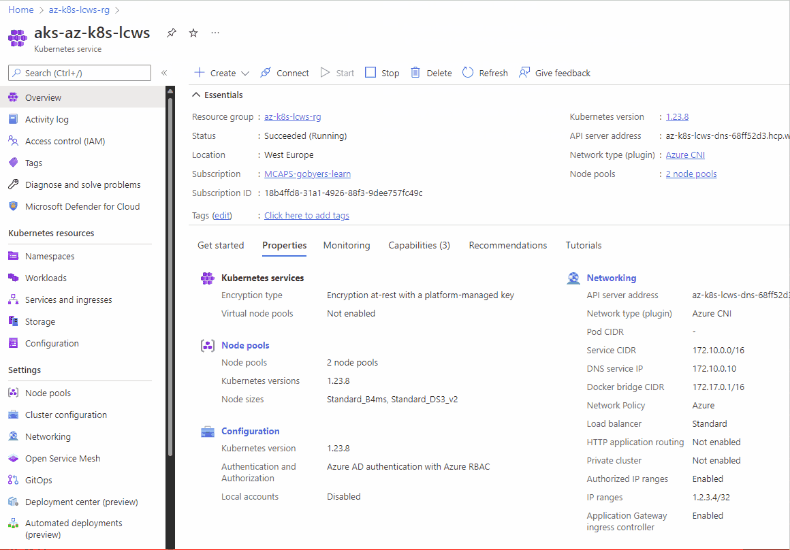
Step 2 Select your Requirements (optional)
Select your base
OperationalandSecurityPrinciples using the presets that have been designed from our field experienceNote If following Azure's Landing Zone methodology, select
Enterprise Scalefrom the dropdown, then select your environment type -
Step 3 Fine tune (optional)
Use the tabs to fine tune your cluster requirements
-
Step 4 Deploy
In the
Deploytab, choose how you will deploy your new cluster, and follow the instructions
Project components
IaC - Bicep code files
IaC (Infrastructure as Code) code files have been modularised into their component areas. Main.bicep references them and they are expected to be present in the same directory. The Deployment Helper leverages an Arm json compiled version of all the bicep files.
Releases are used to version the bicep code files, they can be leveraged directly for use in your project or you can opt to Fork the repo if you prefer.
DevOps - GitHub Actions
A number of GitHub actions are used in the repo that run on push/pr/schedules. These can be copied into your own repo and customised for your CI/CD pipeline. A robust deployment pipeline is essential when coordinating the deployment of multiple Azure services that work together, additionally there is configuration that cannot be set in the template and that needs to be automated (and tested) consistently.
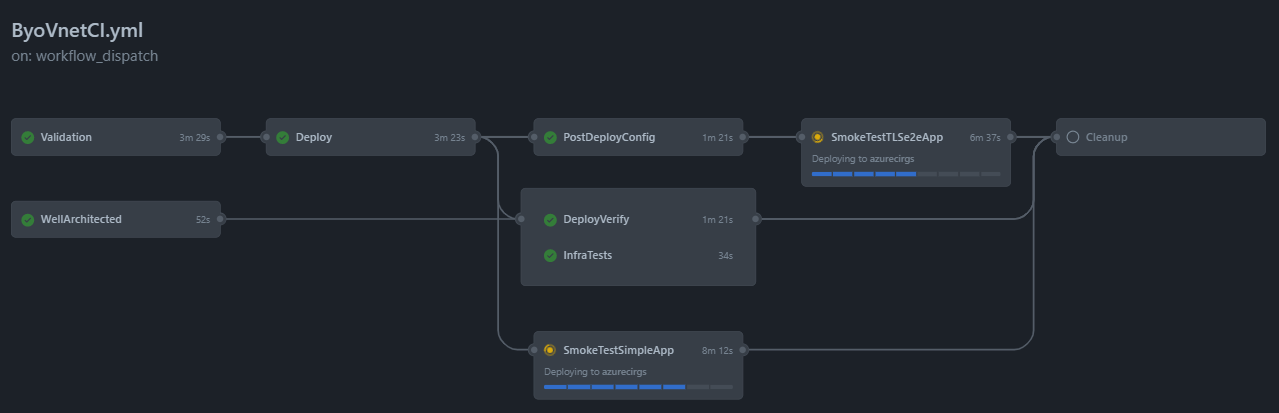
| CI Name | Actions Workflow | Parameter file | CI Status | Notes |
|---|---|---|---|---|
| Starter cluster | StandardCI.yml | ESLZ Sandbox | A simple deployment example, good for first time users of this project to start with | |
| BYO Vnet | ByoVnetCI.yml | ESLZ Byo peered vnet | Comprehensive IaC flow deploying multiple smoke-test apps | |
| Private cluster | ByoVnetPrivateCI.yml | ESLZ Byo private vnet | A private AKS cluster that deploys a vnet with private link services. |
For a more in depth look at the GitHub Actions used in this project, which steps are performed and the different CI practices they demonstrate, please refer to this page.
Background
This project unifies guidance provided by the AKS Secure Baseline, Well Architected Framework, Cloud Adoption Framework and Enterprise-Scale by providing tangible artifacts to deploy Azure resources from CLI or CI/CD systems.
This project is part of the official AKS Landing Zone Accelerator (Enterprise Scale) architectural approach. To read more about this project and how the it fits with Enterprise Scale and the AKS Secure Baseline, look here.
Project Principals
The guiding principal we have with this project is to focus on the the downstream use of the project (see releases). As such, these are our specific practices.
- Deploy all components through a single, modular, idempotent bicep template Converge on a single bicep template, which can easily be consumed as a module
- Provide best-practice defaults, then use parameters for different environment deployments
- Minimise "manual" steps for ease of automation
- Maintain quality through validation & CI/CD pipelines that also serve as working samples/docs
- Focus on AKS and supporting services, linking to other repos to solve; Demo apps / Developer workstations / Jumpboxes / CI Build Agents / Certificate Authorities
Contributing
If you're interested in contributing, please refer to the contribution guide
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit https://cla.opensource.microsoft.com.
When you submit a pull request, a CLA bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., status check, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
Trademarks
This project may contain trademarks or logos for projects, products, or services. Authorized use of Microsoft trademarks or logos is subject to and must follow Microsoft's Trademark & Brand Guidelines. Use of Microsoft trademarks or logos in modified versions of this project must not cause confusion or imply Microsoft sponsorship. Any use of third-party trademarks or logos are subject to those third-party's policies.