|
…
|
||
|---|---|---|
| .. | ||
| Images | ||
| README.md | ||
| azuredeploy.json | ||
README.md
AS-IP-Blocklist-Remove-IPs
Author: Accelerynt
For any technical questions, please contact info@accelerynt.com
This playbook is intended to be run from a Microsoft Sentinel Incident. It will remove the IP address from Microsoft Sentinel Incidents from a Microsoft Azure Conditional Access Named Locations list, indicating compromised IP addresses.
Requirements
The following items are required under the template settings during deployment:
- A Microsoft Azure Named Locations List
- An App Registration for using the Microsoft Graph API
- An Azure Key Vault Secret containing your App Registration Secret
Setup
Create a Named Locations list:
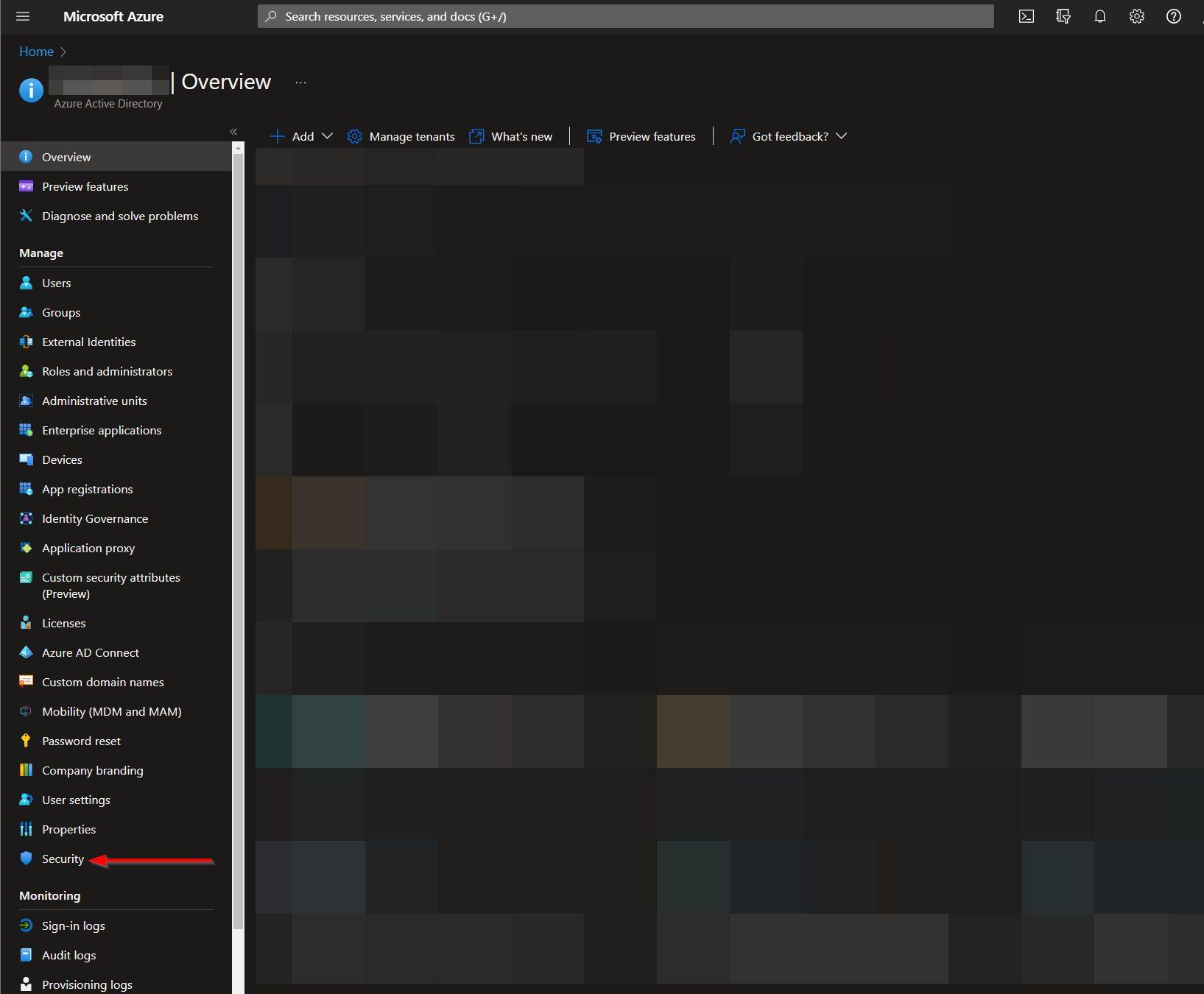
Navigate to the Microsoft Entra ID Menu:
https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Overview
From there, click the "Security" menu option.
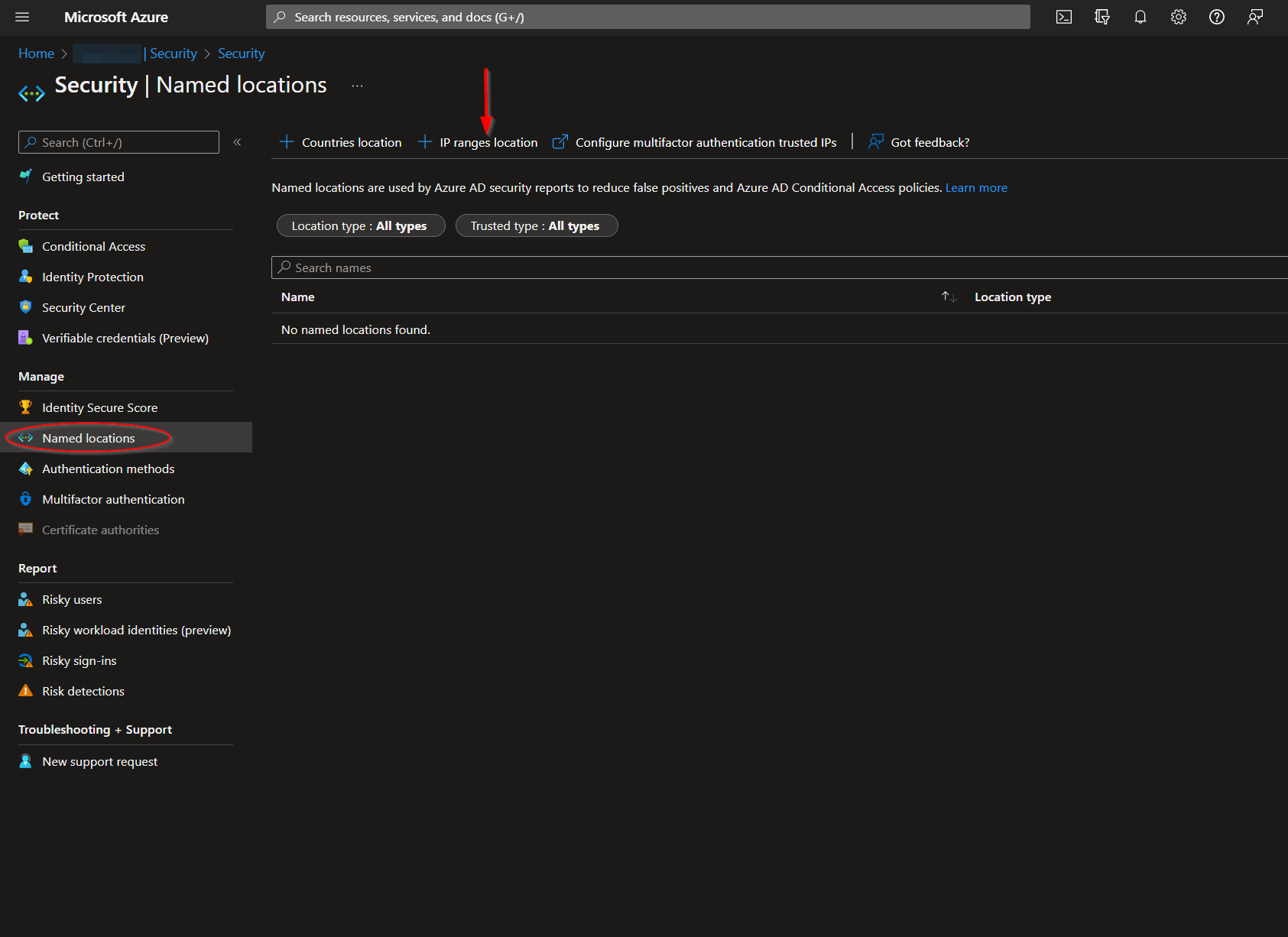
Navigate to the "Named locations" menu option and then click "IP ranges location".
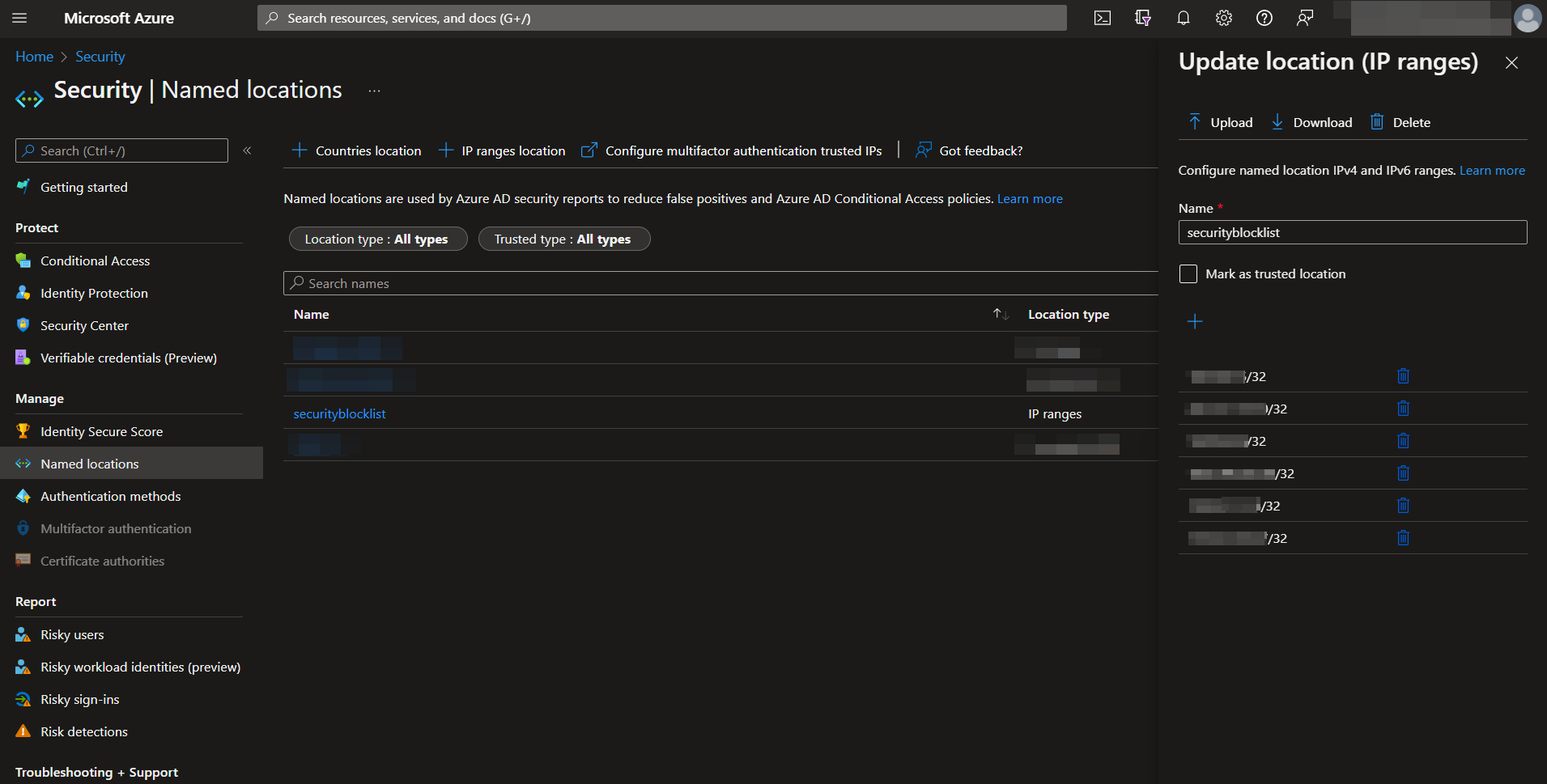
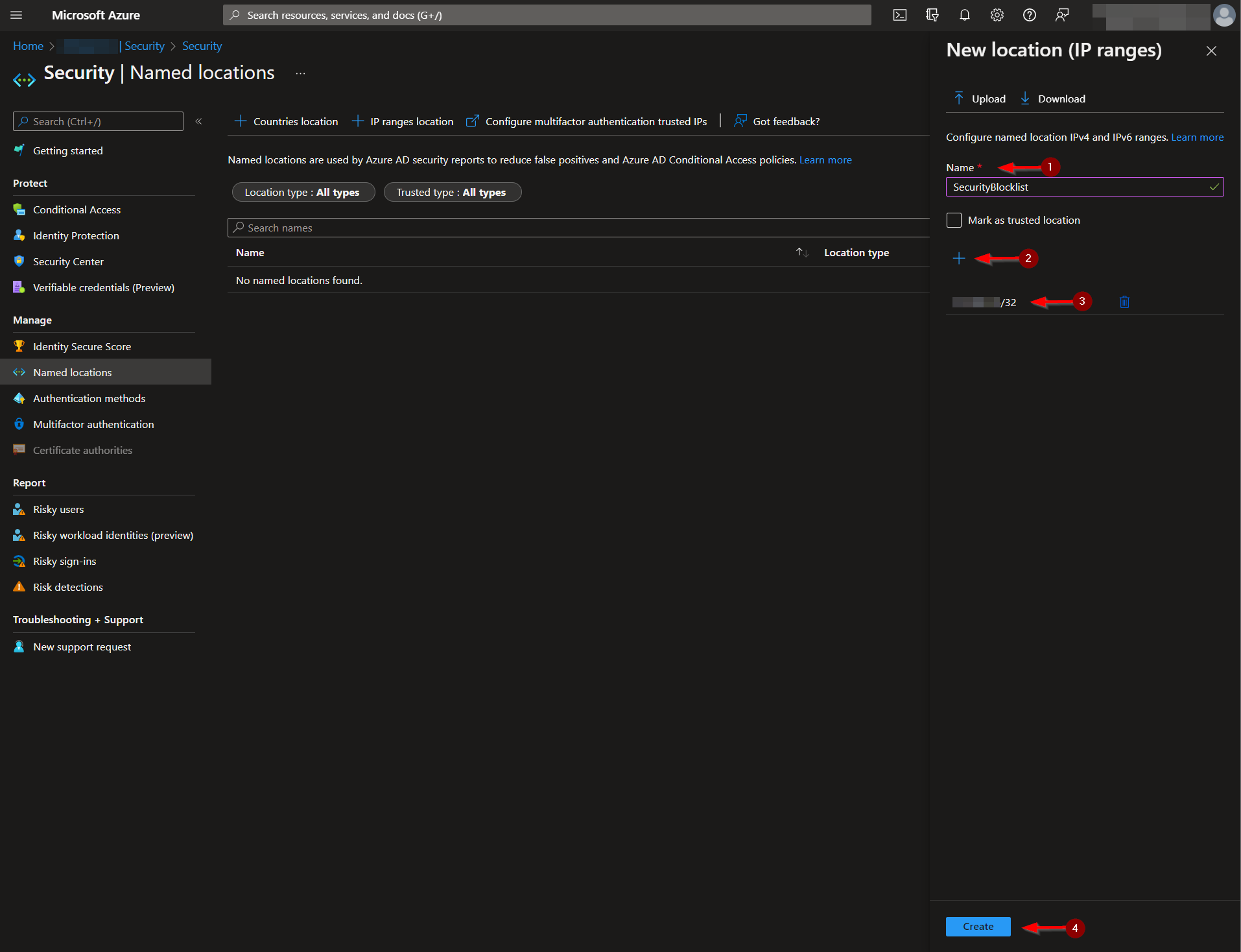
Create a name for your Named Locations list. The list cannot be saved without an initiating value. It should be noted IPs are only accepted in a CIDR range notation. Individual IPs processed by this playbook will have a "/32" appended to them to fit this format.
The name of your Named Locations list, along with its ID, should be noted, as these will be required for the deployment of this playbook.
The list ID may be more difficult to track down, as it is currently not displayed in the URL upon selection. Our solution for this was to send a GET request from https://developer.microsoft.com/en-us/graph/graph-explorer to the following endpoint: https://graph.microsoft.com/v1.0/identity/conditionalAccess/namedLocations.
The JSON response body includes all Named Location lists, along with their IDs.
Create an App Registration:
Navigate to the Navigate to the Microsoft Entra ID App Registrations page:
https://portal.azure.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade
From there, click "New registration".
Select a name for your App Registration, such as "Update-Named-Locations". All else can be left as is, then click "Register".
Once the app registration is created, you will be redirected to the "Overview" page. Under the "Essentials" section, take note of the "Application (client) ID", as this will be needed for deployment.
Next, you will need to add permissions for the app registration to call the Microsoft Graph API update user endpoint. From the left menu blade, click "API permissions" under the "Manage" section. Then, click "Add a permission".
From the "Select an API" pane, click the "Microsoft APIs" tab and select "Microsoft Graph".
Under "Application permissions", search for "Policy", then select the "Policy.Read.All" and ""Policy.ReadWrite.ConditionalAccess" checkboxes. Click "Add permissions".
Admin consent will be needed before your app registration can use the assigned permissions. Click "Grant admin consent for (name)".
Lastly, a client secret will need to be generated for the app registration. From the left menu blade, click "Certificates & secrets" under the "Manage" section. Then, click "New client secret".
Enter a description and select the desired expiration date, then click "Add".
Copy the generated "Value" and save it for the next step, Create an Azure Key Vault Secret.
Create an Azure Key Vault Secret:
Navigate to the Azure Key Vaults page: https://portal.azure.com/#view/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults
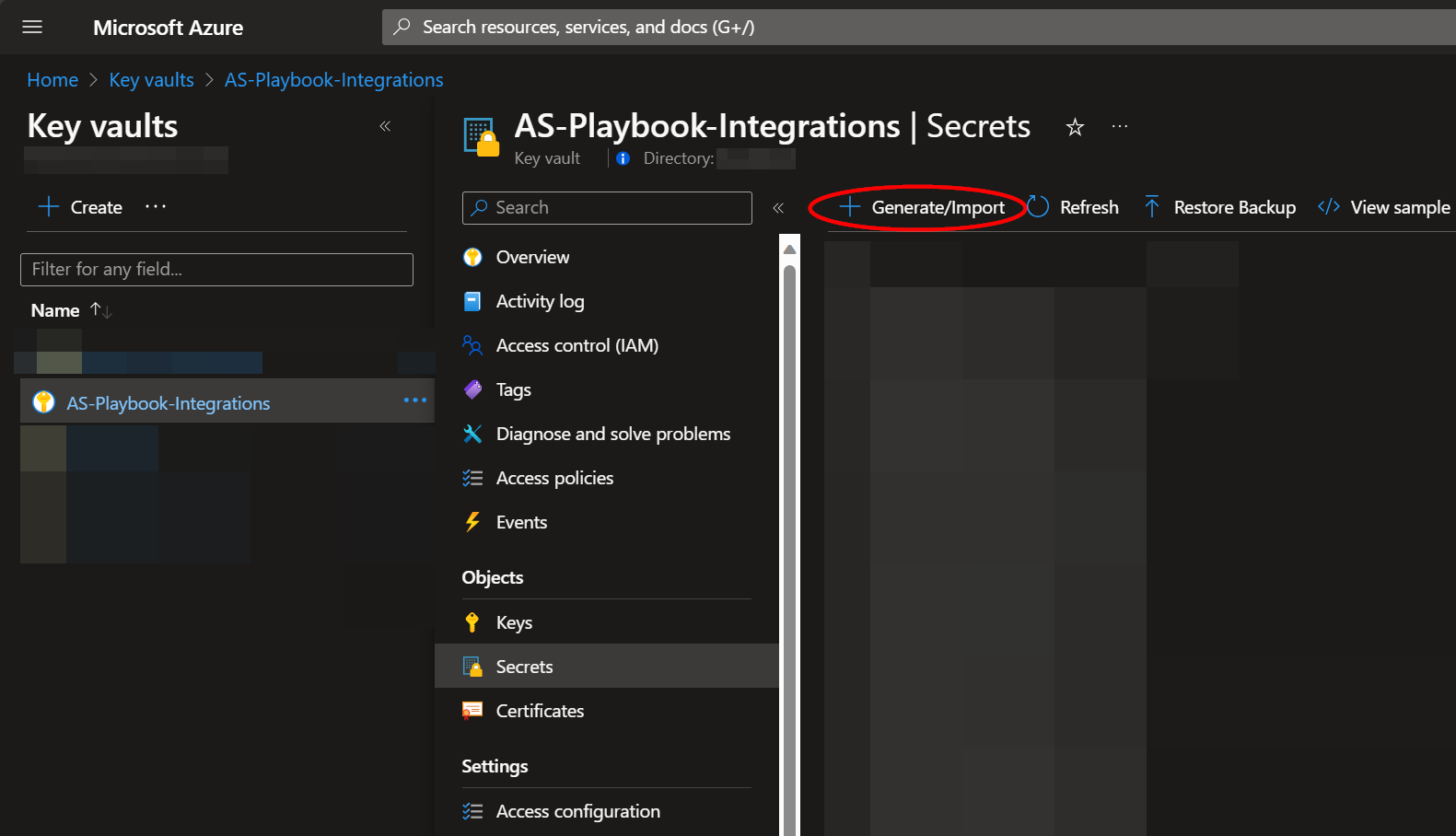
Navigate to an existing Key Vault or create a new one. From the Key Vault overview page, click the "Secrets" menu option, found under the "Settings" section. Click "Generate/Import".
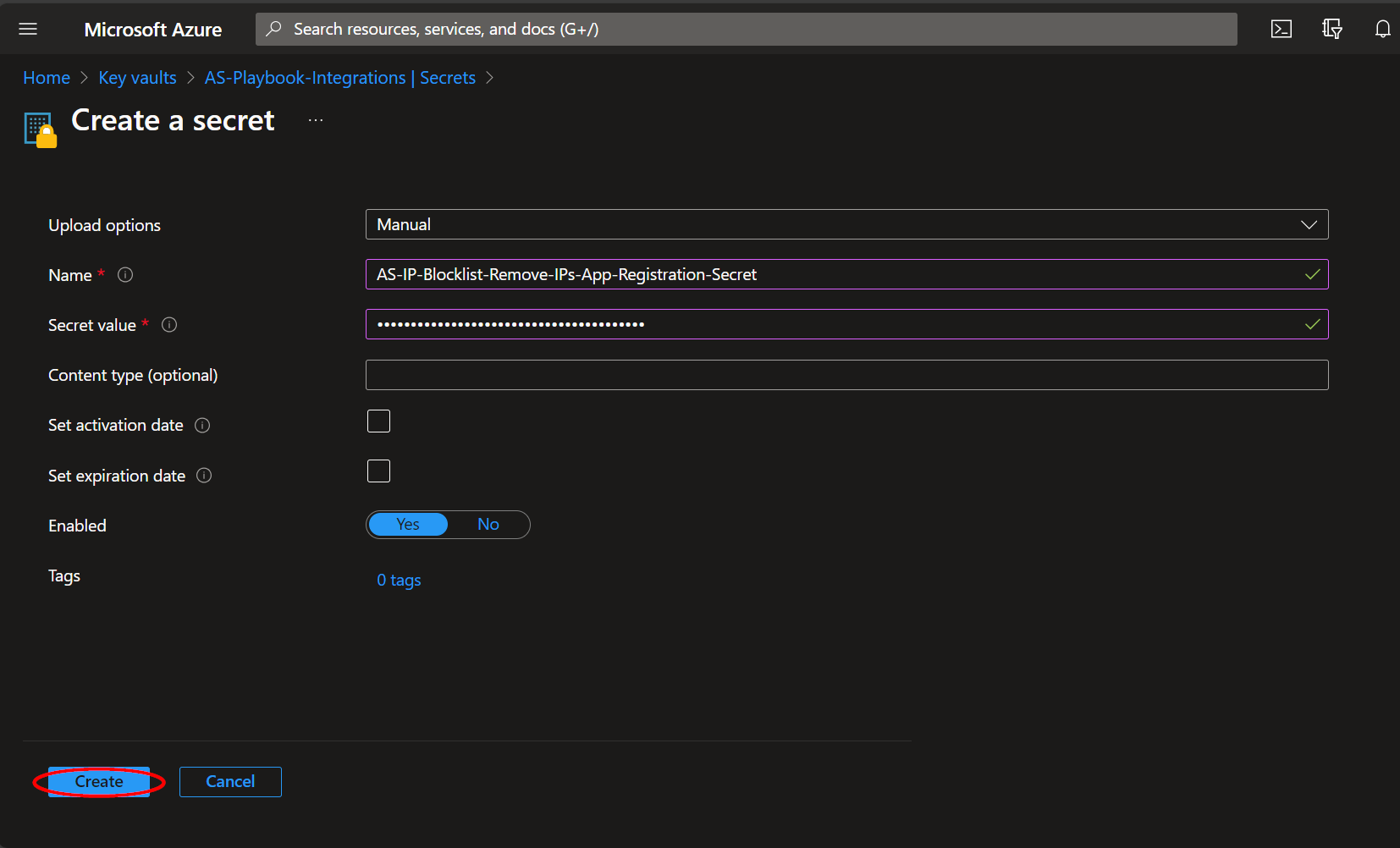
Choose a name for the secret, such as "Update-Named-Locations--App-Registration-Secret", and enter the App Registration Secret copied previously in the "Value" field. All other settings can be left as is. Click "Create".
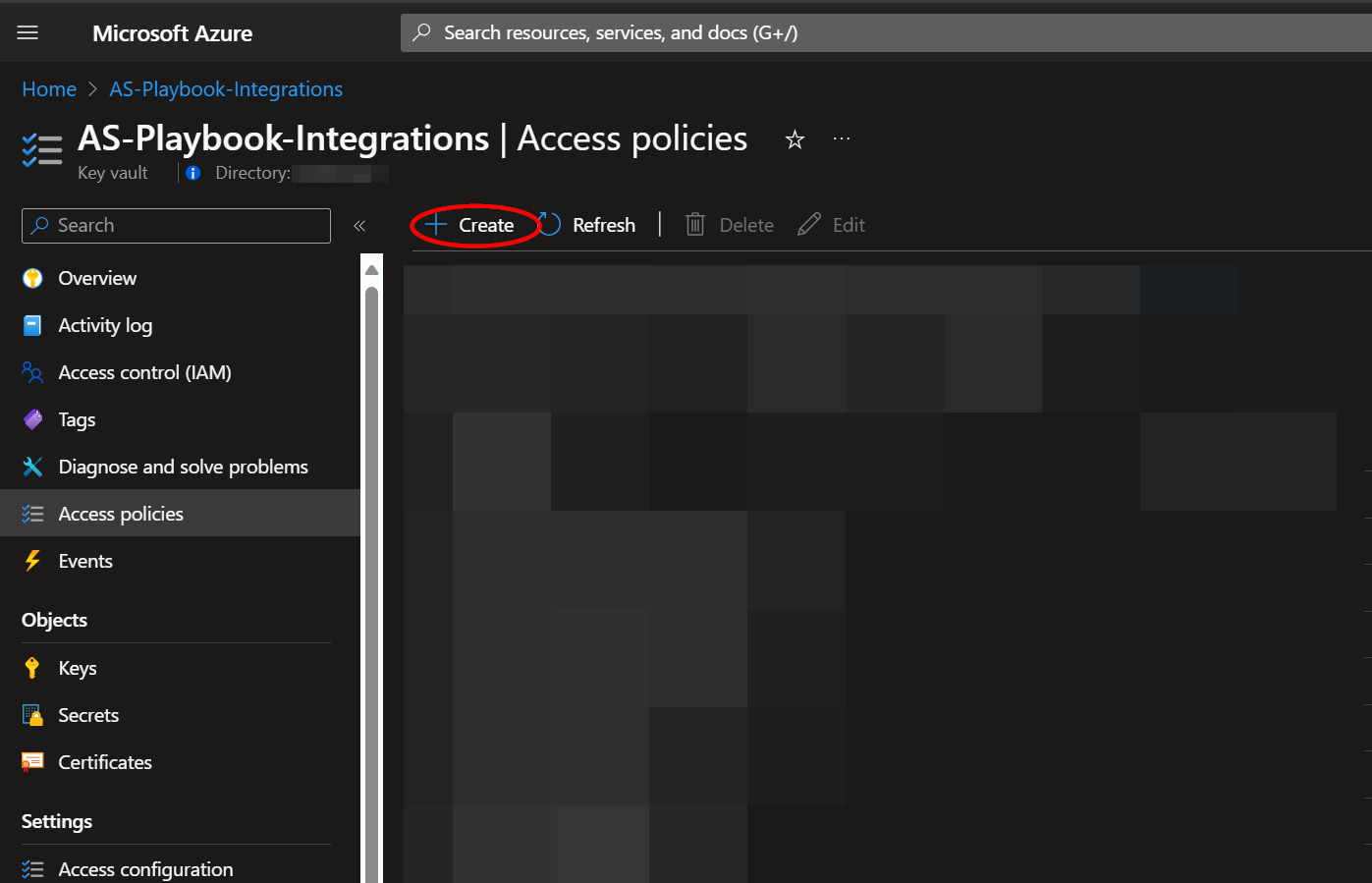
Once your secret has been added to the vault, navigate to the "Access policies" menu option, also found under the "Settings" section on the Key Vault page menu. Leave this page open, as you will need to return to it once the playbook has been deployed. See Granting Access to Azure Key Vault.
Deployment
To configure and deploy this playbook:
Open your browser and ensure you are logged into your Microsoft Sentinel workspace. In a separate tab, open the link to our playbook on the Accelerynt Security GitHub Repository:
https://github.com/Accelerynt-Security/AS-IP-Blocklist-Remove-IPs
Click the “Deploy to Azure” button at the bottom and it will bring you to the custom deployment template.
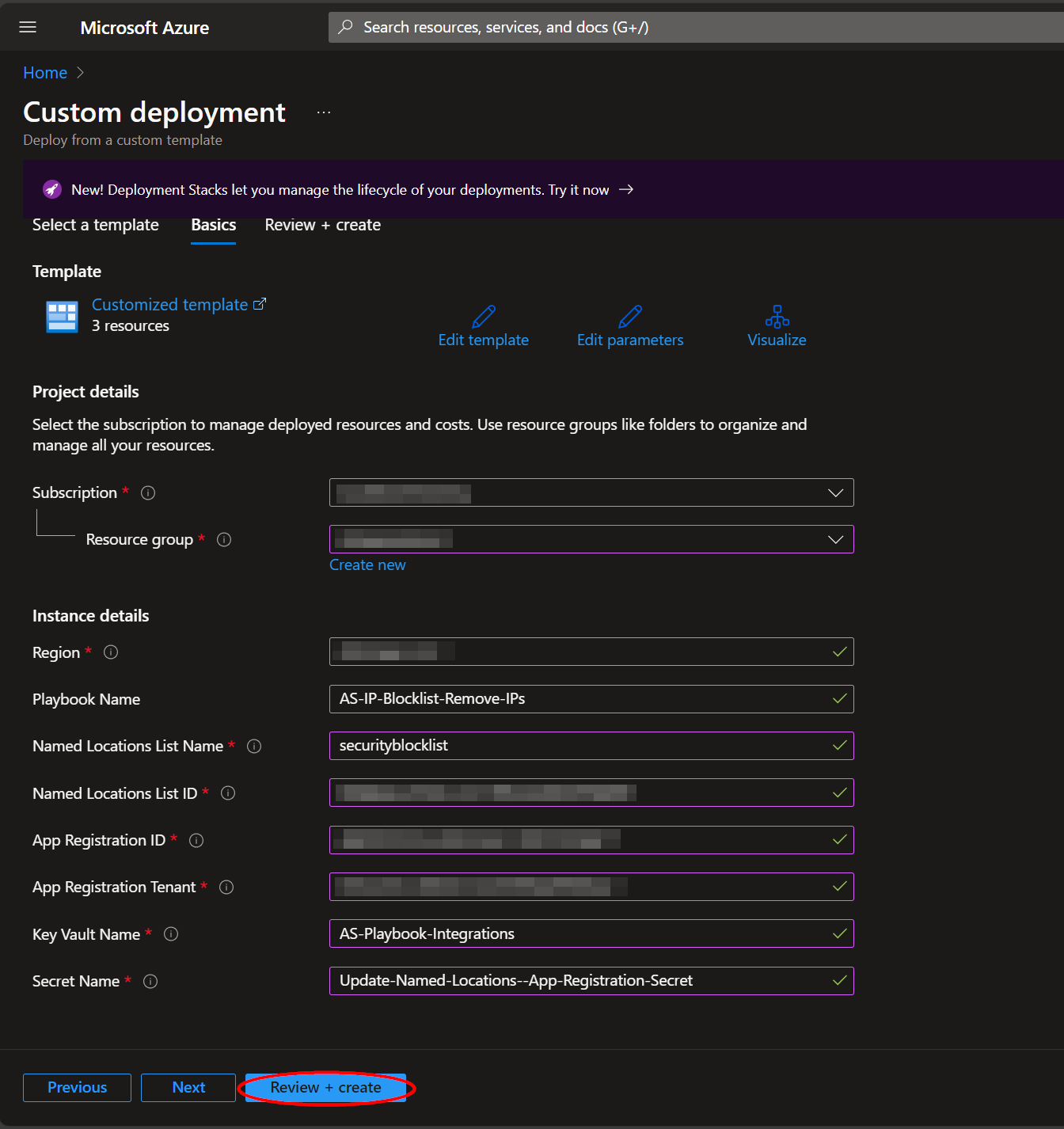
In the Project Details section:
- Select the “Subscription” and “Resource Group” from the dropdown boxes you would like the playbook deployed to.
In the Instance Details section:
-
Playbook Name: This can be left as "AS-IP-Blocklist-Remove-IPs" or you may change it.
-
Named Locations List Name: Enter the value of the Named Locations list created in Create a Named Locations list.
-
Named Locations List ID: Enter the value of the Named Locations list ID referenced in Create a Named Locations list.
-
App Registration ID: Enter the value of the Application (client) ID referenced in Create an App Registration.
-
App Registration Tenant: Enter the value of the Directory (tenant) ID referenced in Create an App Registration.
-
Key Vault Name: Enter the name of the Key Vault referenced in Create an Azure Key Vault Secret.
-
Secret Name: Enter the name of the Key Vault Secret created in Create an Azure Key Vault Secret.
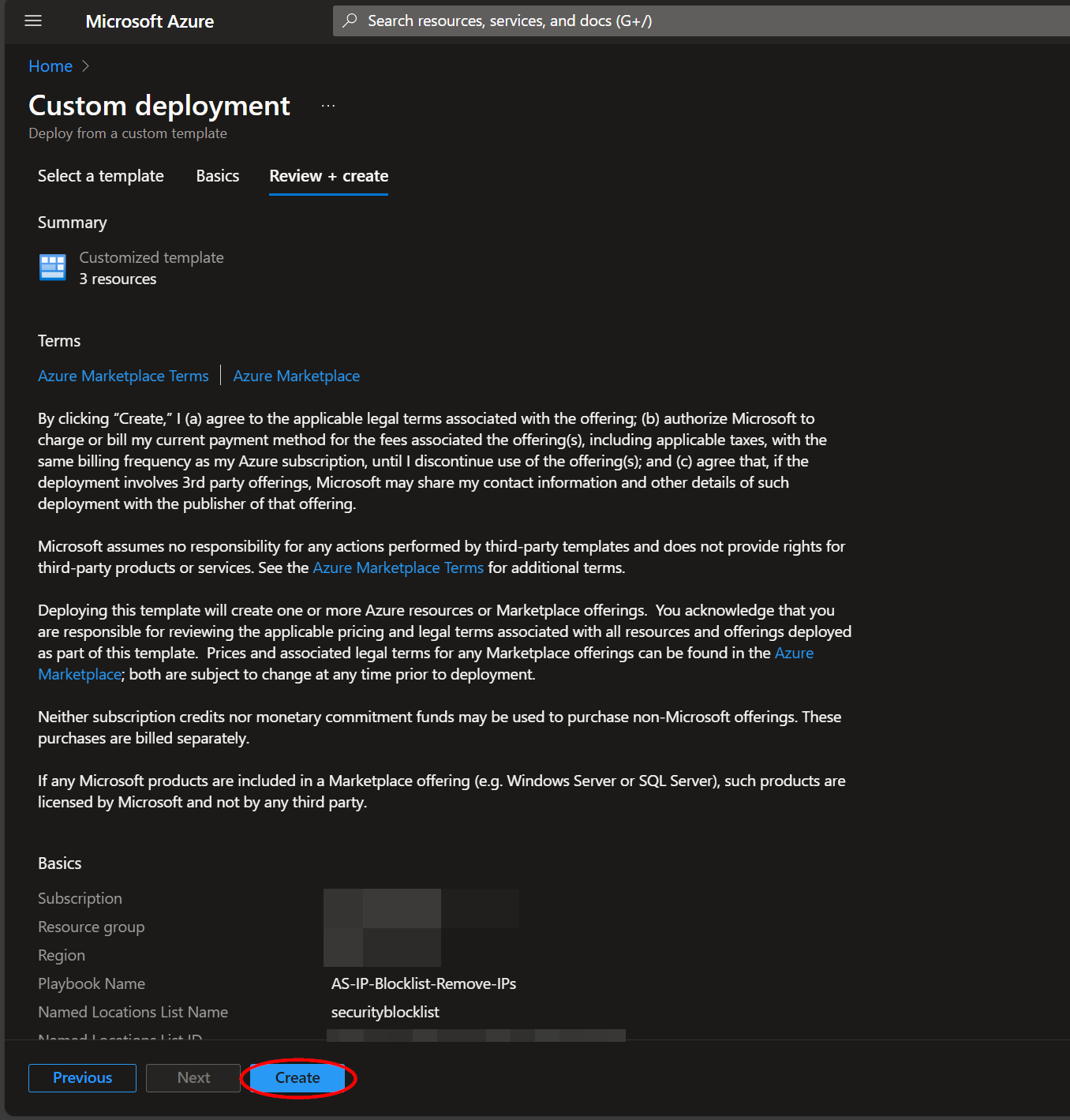
Towards the bottom, click on “Review + create”.
Once the resources have validated, click on "Create".
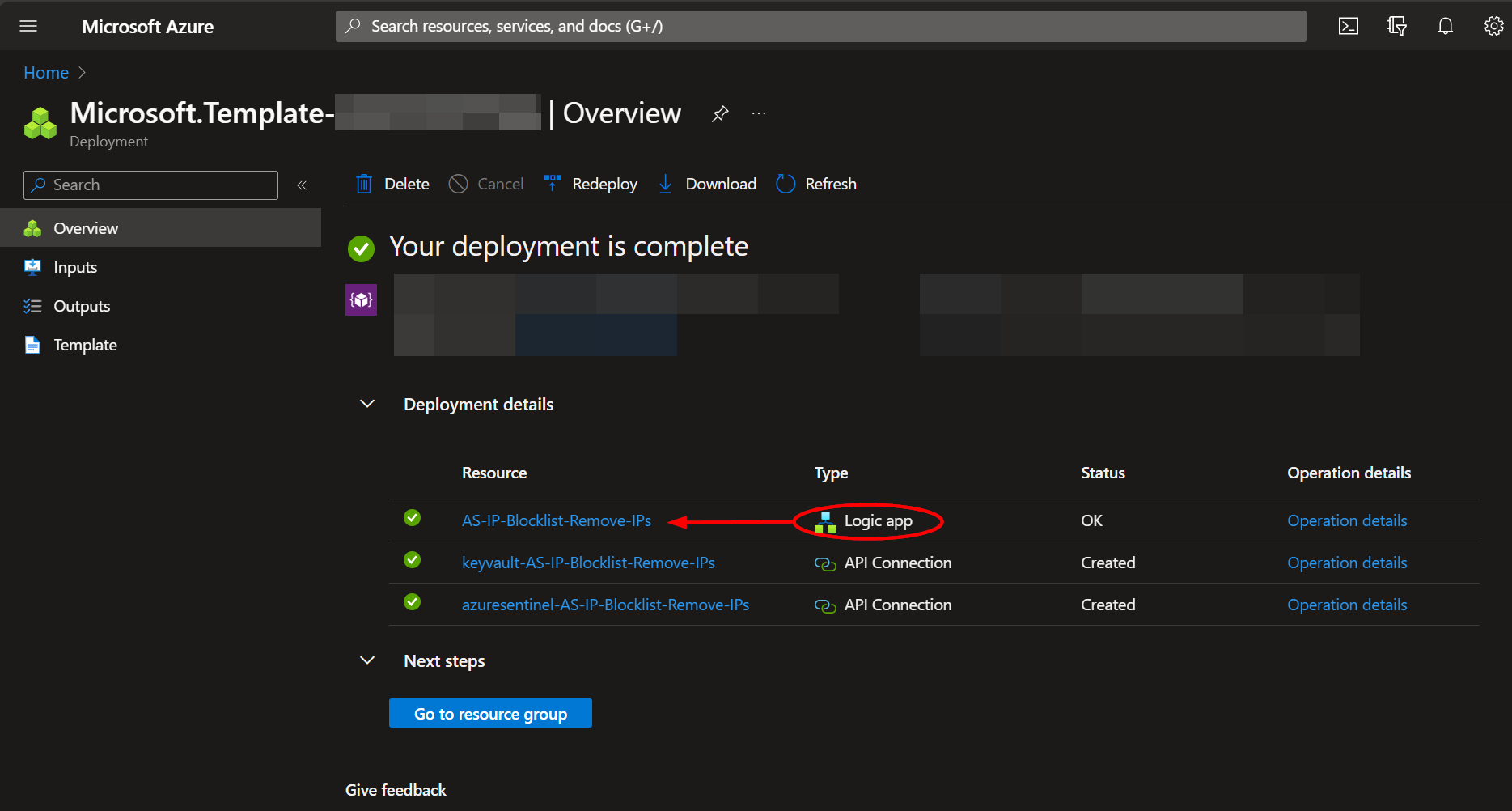
The resources should take around a minute to deploy. Once the deployment is complete, you can expand the "Deployment details" section to view them. Click the one corresponding to the Logic App.
Granting Access to Azure Key Vault
Before the Logic App can run successfully, the Key Vault connection created during deployment must be granted access to the Key Vault storing your App Registration Secret.
From the Key Vault "Access policies" page, click "Add Access Policy".
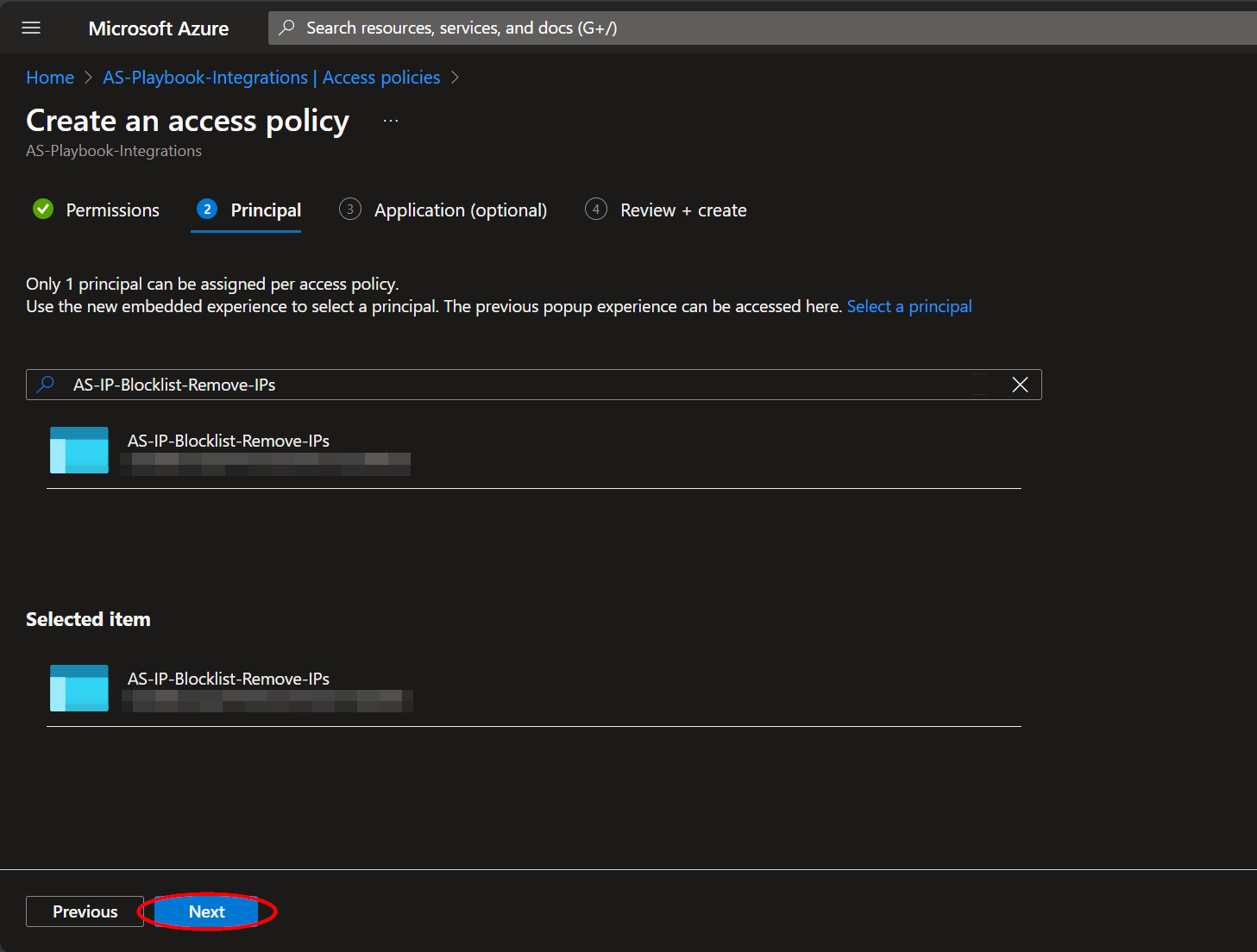
Select the "Get" checkbox in the "Secret permissions" list field. Then click the blue "None selected" text next to the "Select principal" field.
Paste "AS-IP-Blocklist-Remove-IPs" into the principal search box and click the option that appears. Click "Select" towards the bottom of the page.
Click "Add".