Fixed broken links and added link to the blog (blog will be online on Tuesday) |
||
|---|---|---|
| .. | ||
| images | ||
| TasksRepository.csv | ||
| TasksRepositoryWatchlistTemplate.json | ||
| azuredeploynmi.json | ||
| readme.md | ||
readme.md
Tasks-Repository
author: Benji Kovacevic
This solution contains Tasks Repository Watchlist and Playbook that are used to assign tasks automaticlly based on incident title.
This solution is explained in details in this blog - Create Tasks Repository in Microsoft Sentinel.
Prerequisites
Permissions
- Watchlist:
Permission needed to deploy: Microsoft Sentinel Contributor - Playbook:
Permission needed to deploy: Logic App Contributor
Permission needed to assign RBAC to managed identity: User Access Administrator or Owner on Resource Group where Microsoft Sentinel is - Automation rule:
Permission needed to create: Microsoft Sentinel Responder
Quick Deployment
, or using raw CSV file and following instructions on how to create watchlist manually.
Note:
When creating watchlist manually, use TasksRepository for alias, or this field will need to be updated in the playbook after deploying it. Also, map SearchKey to IncidentTitle column as playbook is using it as well.
-
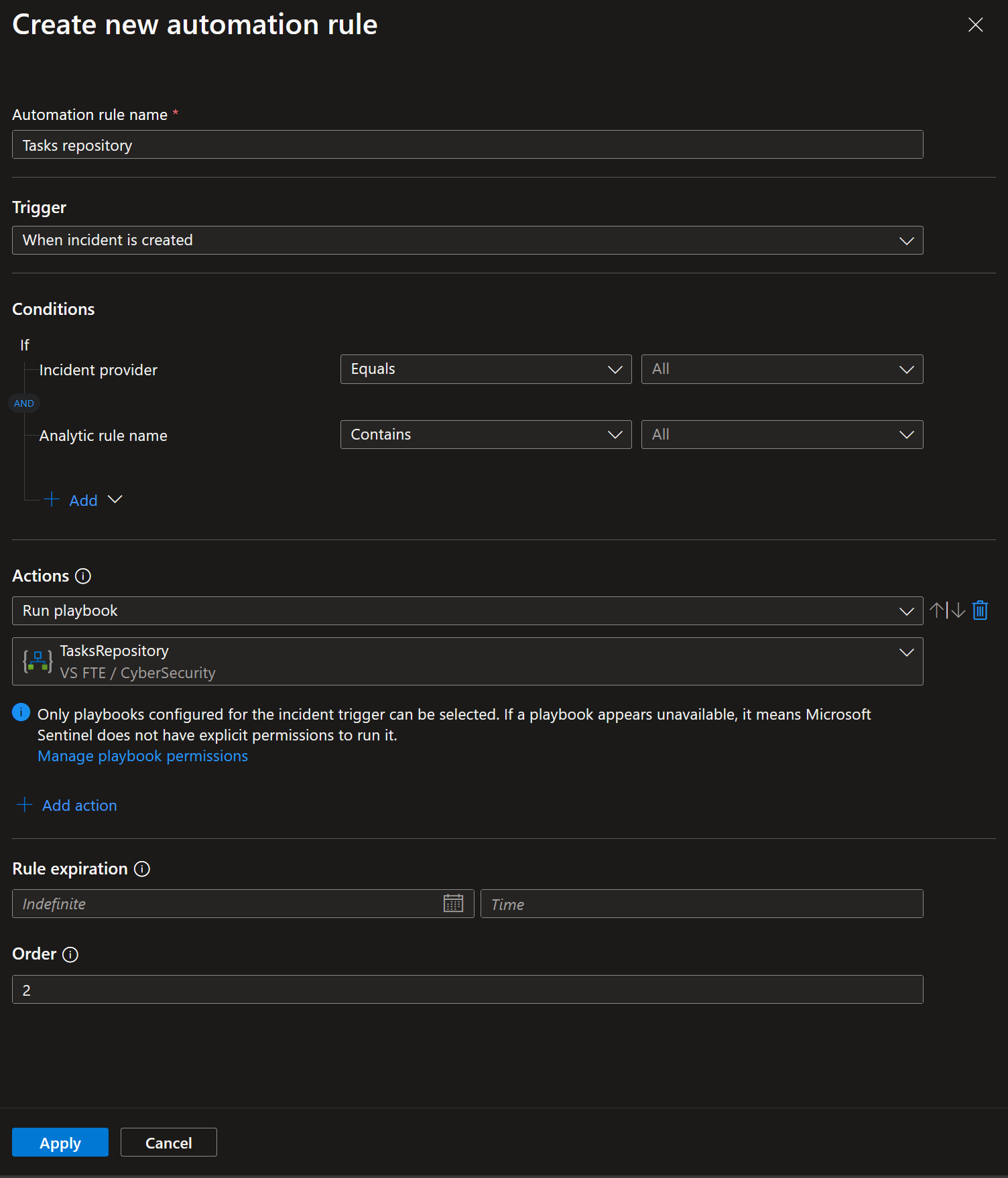
Final step is to create an automation rule that will run on incident creation on all incidents, and as an action will run playbook.
- Title: Tasks repository
- Trigger: When incident is created
- Actions: Run playbook -> TasksRepository
Post-deployment
- Assign Microsoft Sentinel Responder role to the managed identity. To do so, choose Identity blade under Settings of the Logic App.
- Open Edit mode of the playbook, and add managed identity to Azure Monitor Logs action
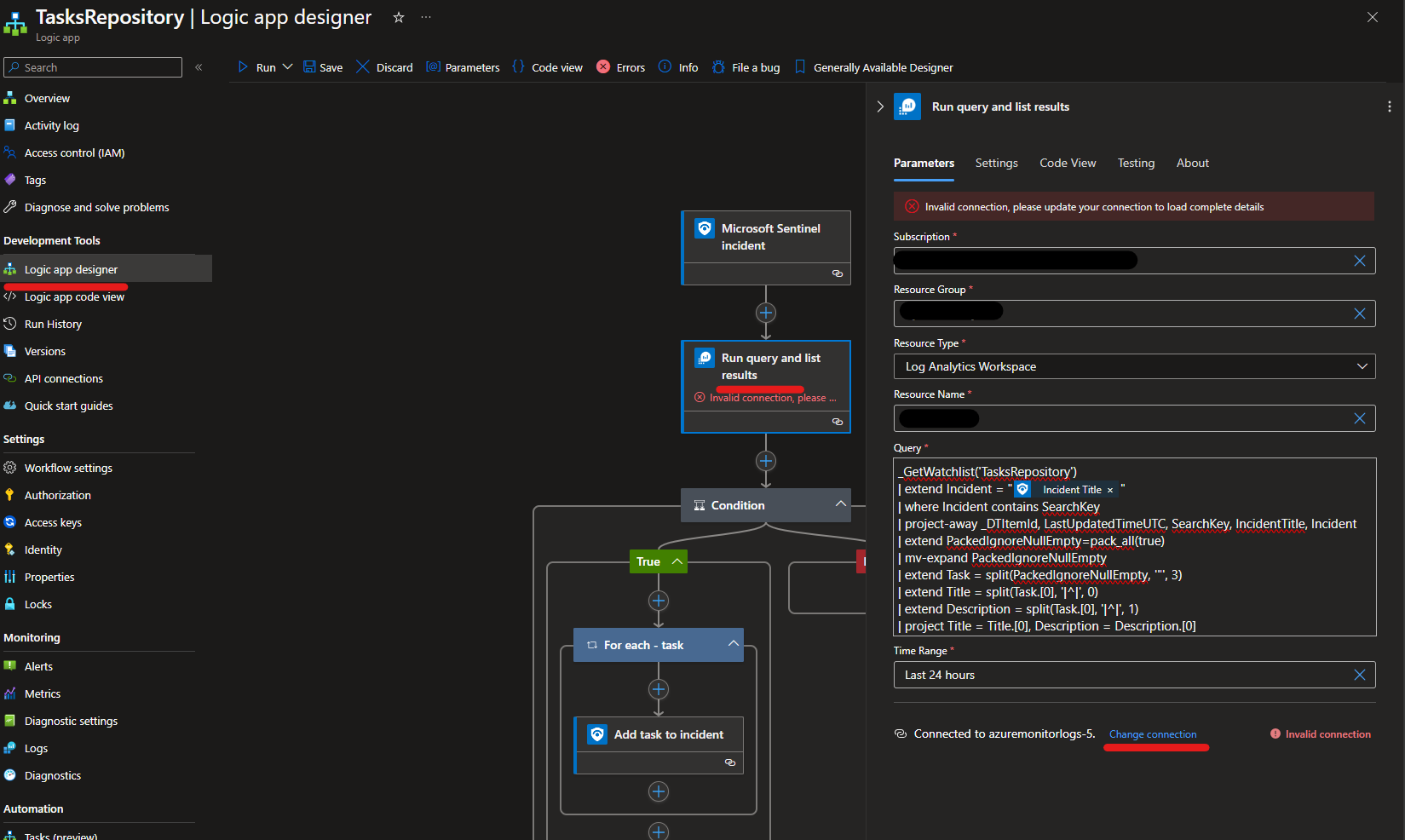
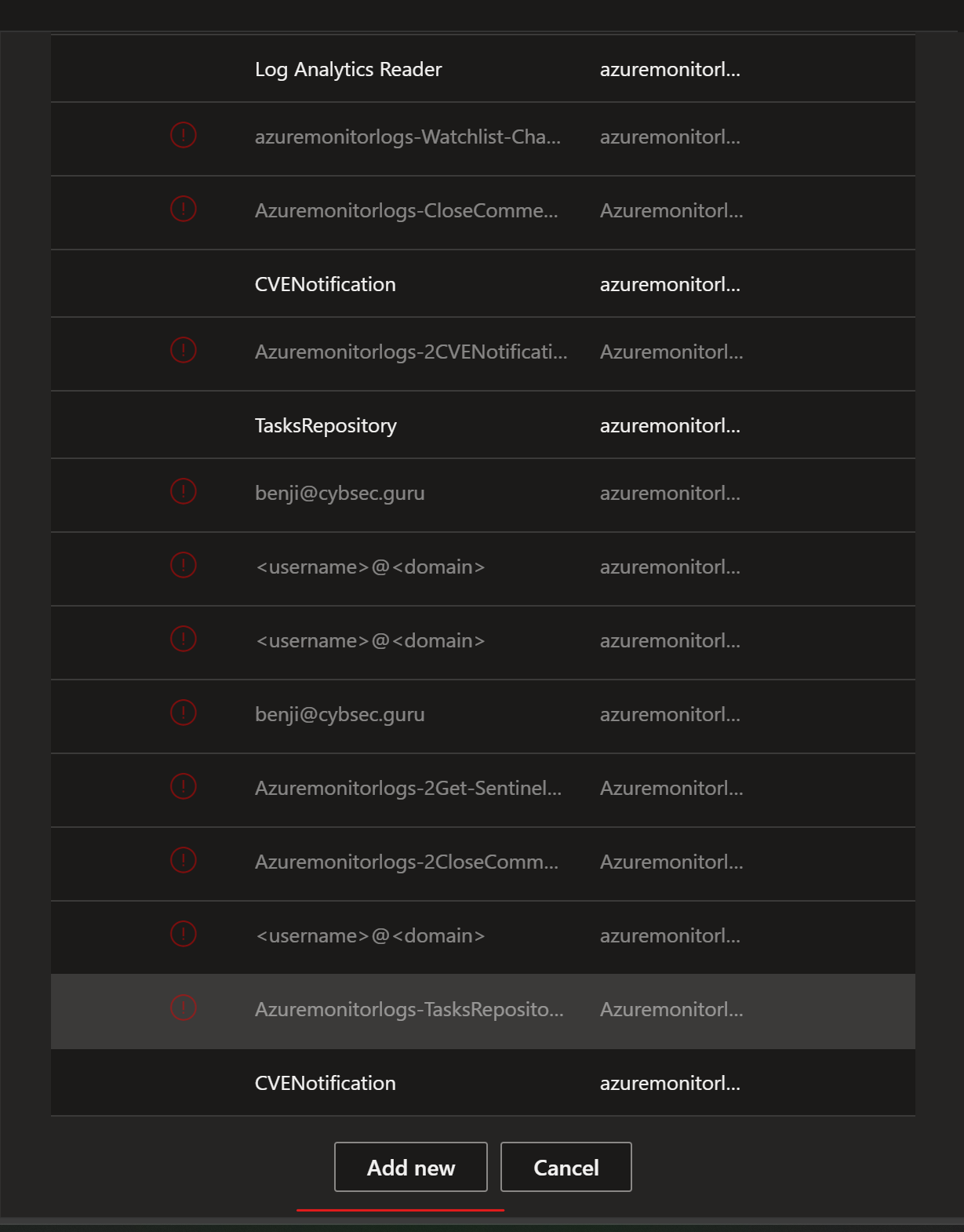
For Connection Name enter: Azuremonitorlogs-TasksRepository
For Authentication Type choose: Logic Apps Managed Identity
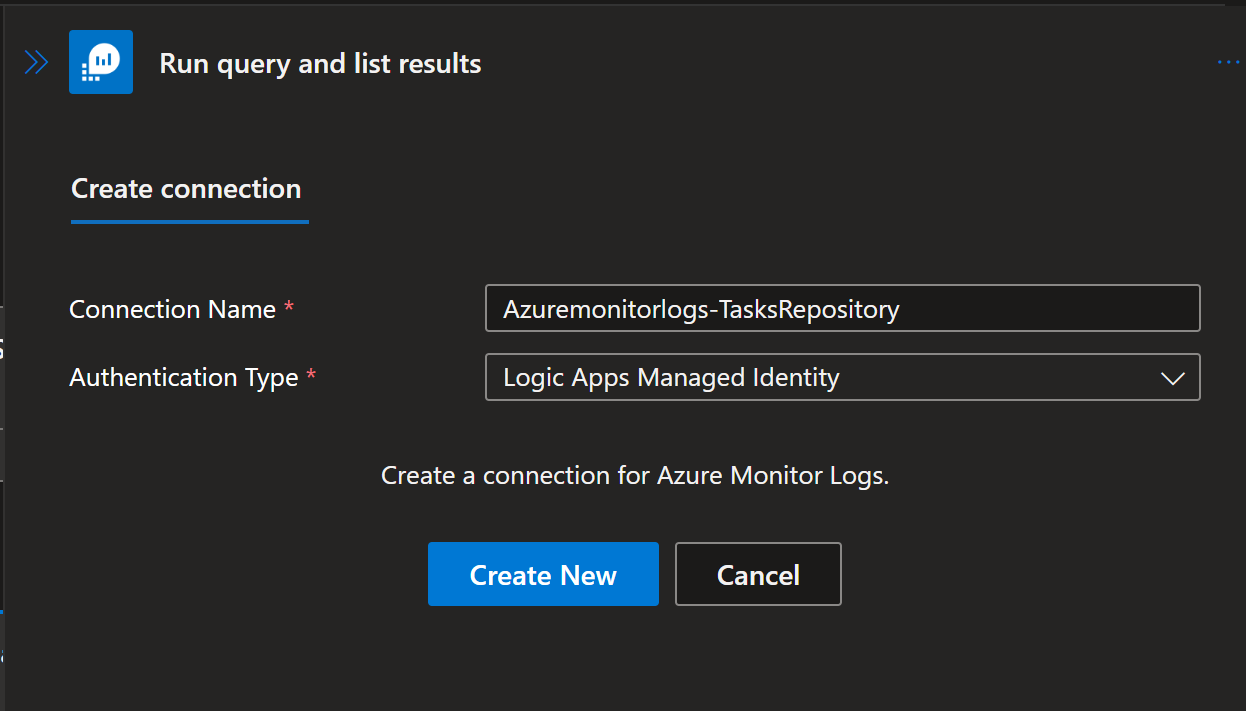
Select Create New, and then Save the playbook. - Add tasks to the Tasks Repository watchlist. Note: When adding additional tasks, there is a format that should be used so that playbook can map tasks title and description field. Each tasks filed should look like Tasks title, unique separator |^|, followed by Tasks description. Unique separator |^| is used in playbook to separate title and description of the tasks into its appropriate fields. In watchlist example, in column Task01 we can see example - Task 1|^|Task description.