|
|
||
|---|---|---|
| .. | ||
| Images | ||
| azuredeploy.json | ||
| readme.md | ||
readme.md
Enrich-SentinelIncident-GreyNoise-IP
author: Nathan Swift
This playbook uses the GreyNoise APIs to automatically enrich incidents generated by Sentinel for IP addresses. You need a valid GreyNoise API Key in order to use the playbook. To learn more about the service and request a trial key, see the Setting up an Account.
For details around the APIs used see the RIOT API documentation and the IP Context API documentation.
Additional Post Install Notes:
Authorize the web.connection APIs deployed into the ResourceGroup.
The Logic App creates and uses a Managed System Identity (MSI) to update the Azure Sentinel Incident.
Assign RBAC 'Azure Sentinel Responder' role to the Logic App at the Resource Group level of the Log Analytics Workspace.
Initial Setup
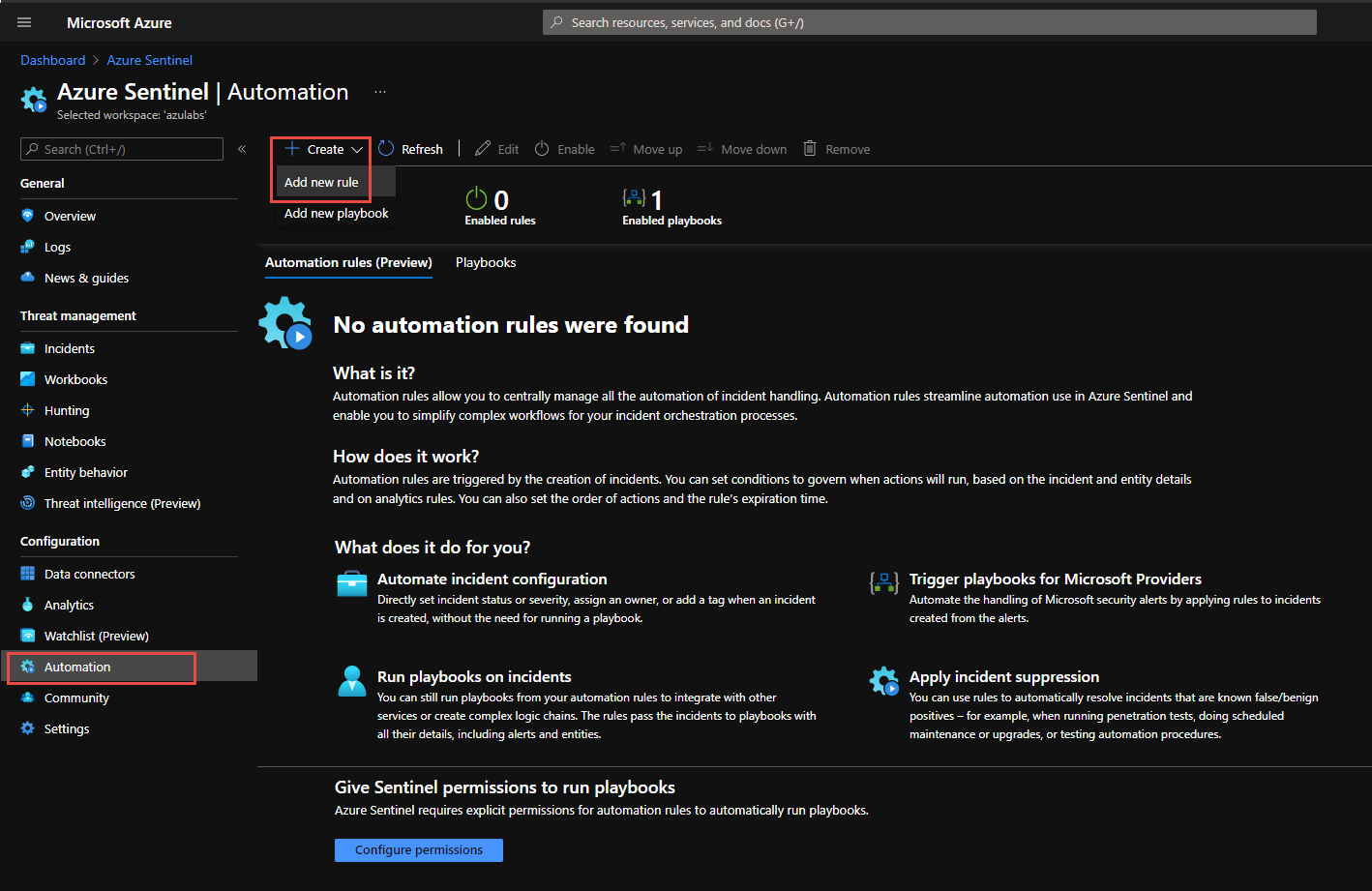
Logic App is utilitzed by Automation rules. You must setup an Automation rule. Go to the Automation Rules blade in Azure Sentinel.
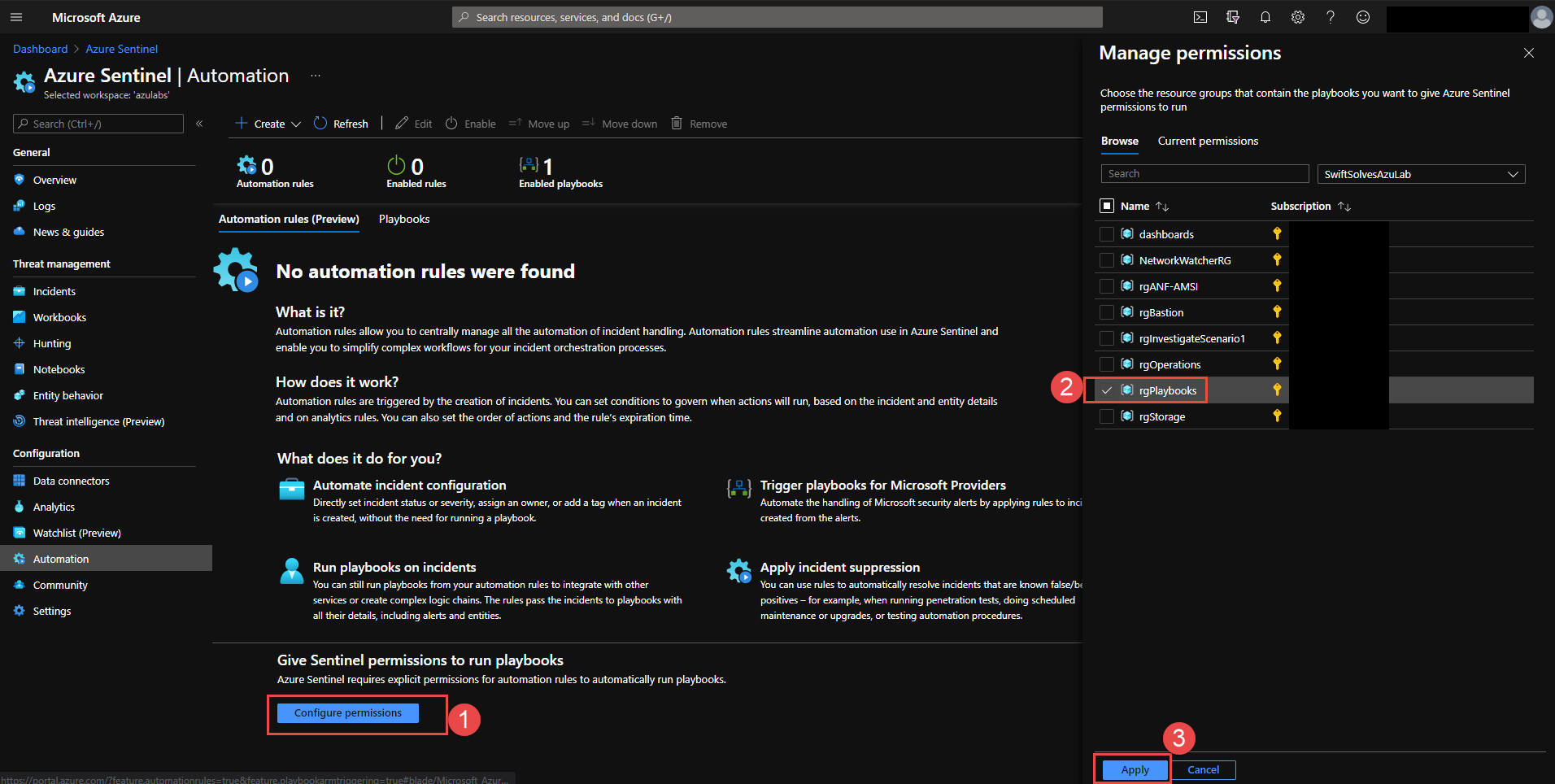
If you have not set permissions yet, review here
Once permission are set, click on + Create and Add New Rule
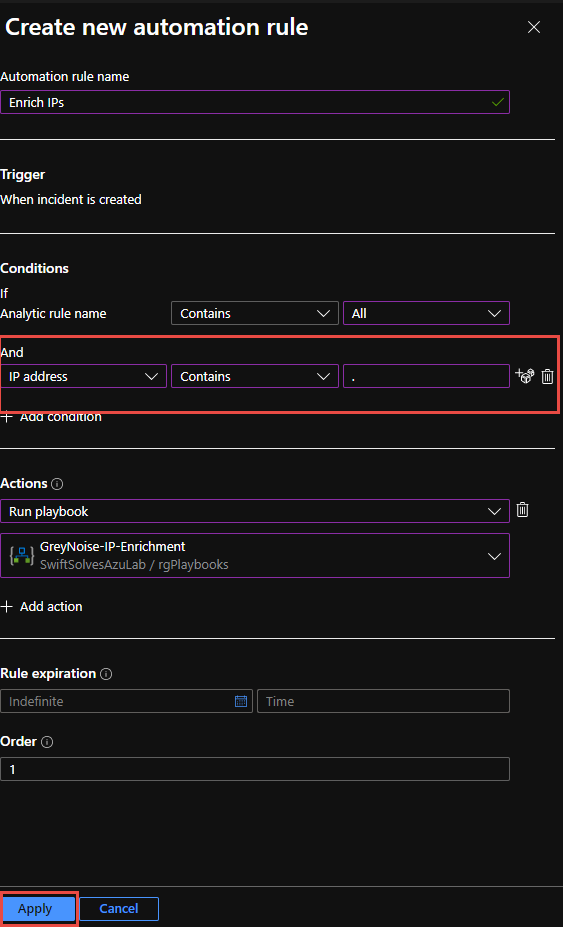
An new automation rule blade on right will open up. fill in the fields be sure to select all the Analytic rules you want this enrichment playbook to run on and also add a second condition IP Address contains .
Be sure under Actions to choose Run playbook and choose the GreyNoise-IP-Enrichment playbook from the drop down menu.
Once completed press Apply button at bottom to add the Automation rule.