|
|
||
|---|---|---|
| .. | ||
| alert-trigger | ||
| incident-trigger | ||
| readme.md | ||
readme.md
Get-MDEStatistics
author: Nicholas DiCola
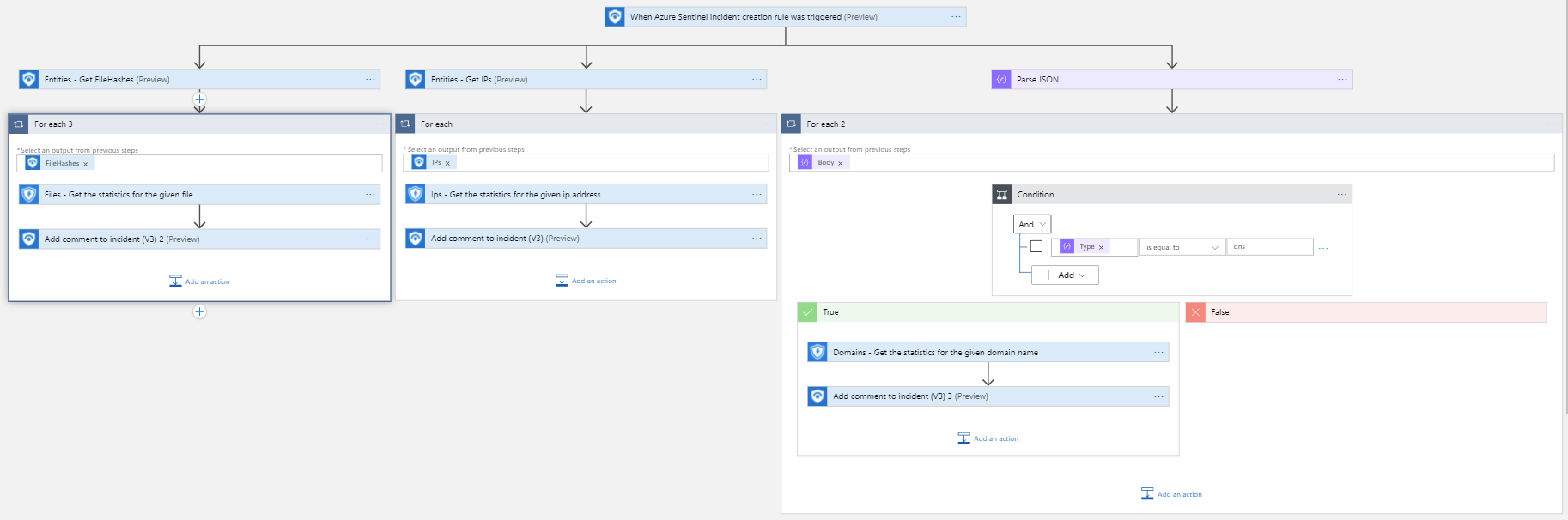
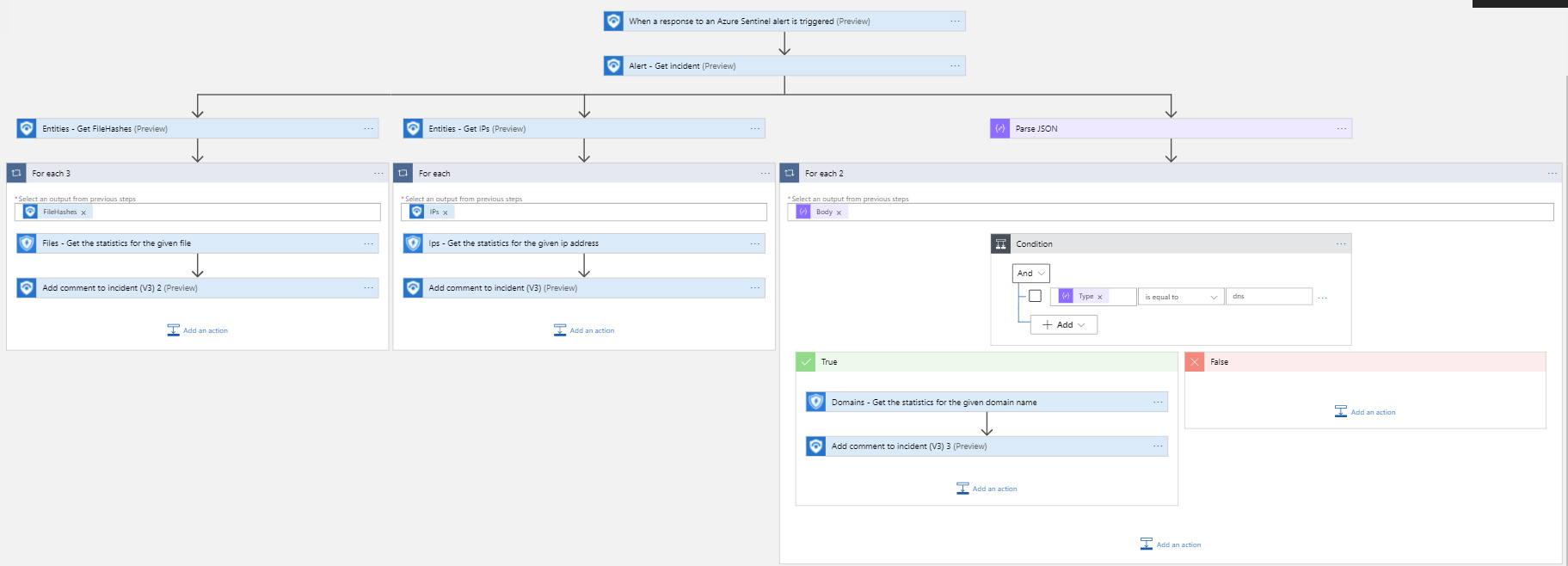
This playbook will get IP, File and Domain statistics from Microsoft Defender for Endpoint and them to a comment on the Incident in Azure Sentinel.
Quick Deployment
Deploy with incident trigger (recommended)
After deployment, attach this playbook to an automation rule so it runs when the incident is created.
Learn more about automation rules

Deploy with alert trigger
After deployment, you can run this playbook manually on an alert or attach it to an analytics rule so it will rune when an alert is created.

Prerequisites
- You will need to grant Ip.Read.All, Url.Read.All, and File.Read.All permissions to the managed identity. Run the following code replacing the managed identity object id. You find the managed identity object id on the Identity blade under Settings for the Logic App.
$MIGuid = "<Enter your managed identity guid here>"
$MI = Get-AzureADServicePrincipal -ObjectId $MIGuid
$MDEAppId = "fc780465-2017-40d4-a0c5-307022471b92"
$PermissionName = "Ip.Read.All"
$MDEServicePrincipal = Get-AzureADServicePrincipal -Filter "appId eq '$MDEAppId'"
$AppRole = $MDEServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains "Application"}
New-AzureAdServiceAppRoleAssignment -ObjectId $MI.ObjectId -PrincipalId $MI.ObjectId `
-ResourceId $MDEServicePrincipal.ObjectId -Id $AppRole.Id
$PermissionName = "Url.Read.All"
$AppRole = $MDEServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains "Application"}
New-AzureAdServiceAppRoleAssignment -ObjectId $MI.ObjectId -PrincipalId $MI.ObjectId `
-ResourceId $MDEServicePrincipal.ObjectId -Id $AppRole.Id
$PermissionName = "File.Read.All"
$AppRole = $MDEServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains "Application"}
New-AzureAdServiceAppRoleAssignment -ObjectId $MI.ObjectId -PrincipalId $MI.ObjectId `
-ResourceId $MDEServicePrincipal.ObjectId -Id $AppRole.Id