|
|
||
|---|---|---|
| .. | ||
| CustomConnector | ||
| Playbook | ||
| images | ||
| readme.md | ||
readme.md
Enrich-MalwareBazaar
Add information from MalwareBazaar aka abuse.ch to a Sentinel Incident
Quick Deployment
Deploy with incident trigger (recommended)
After deployment, attach this playbook to an automation rule so it runs when the incident is created.
Learn more about automation rules
Prerequisites
- API key is not required for malwarebazaar
- Logic Apps Custom Connector for MalwareBazaar
- Logic App managed identity should be given Sentinel Responder role to read incident trigger and write comment/tag to incident
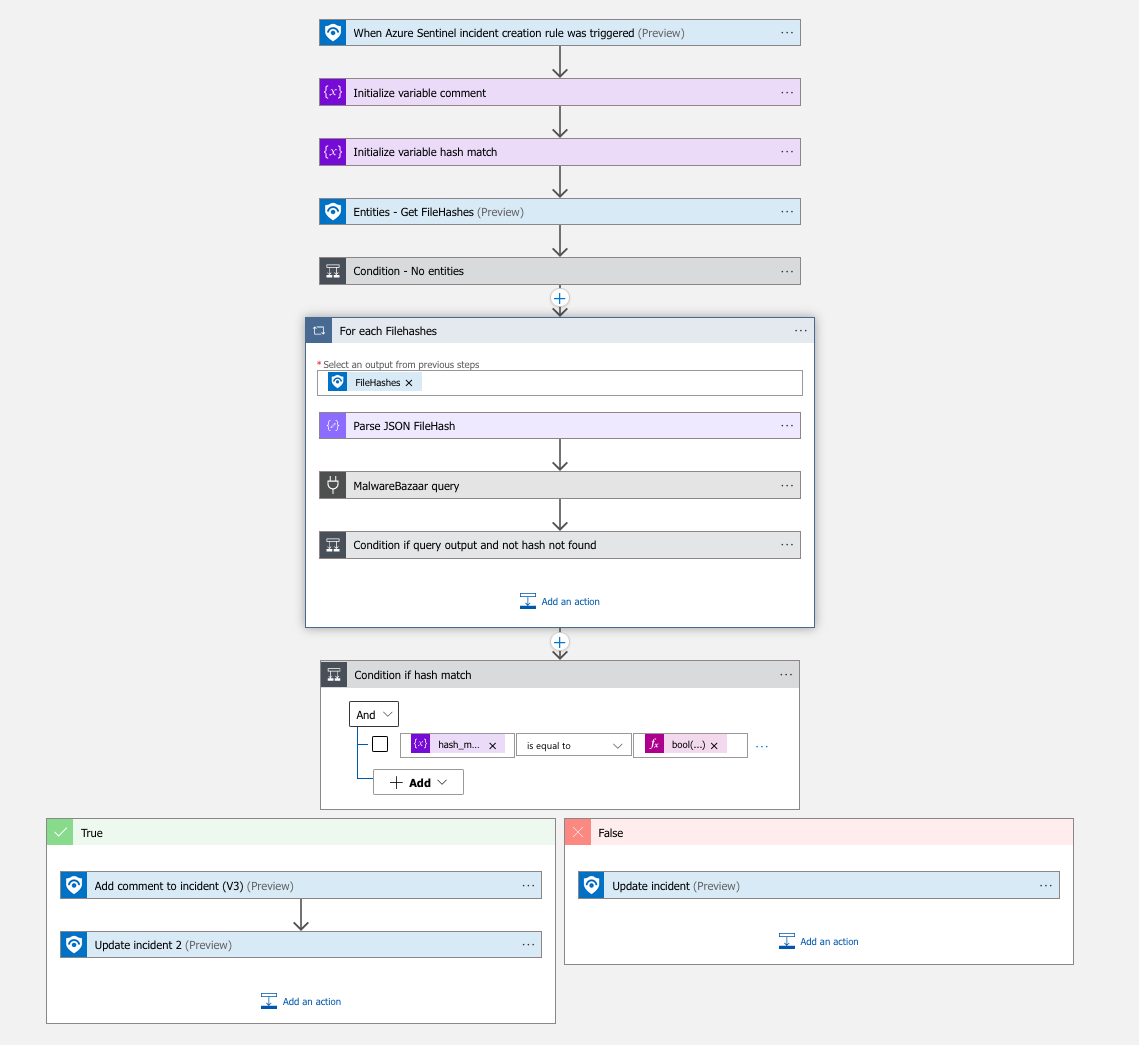
Screenshots
Workflow explained
(step by step pseudo-code)
- Sentinel incident trigger
- Get FileHashes entities
- Validate that entities list is not empty or terminate
- For each FileHashes, do a malwarebazaar query and append output to comment
- Update sentinel incident with comment and appropriate tag Found/NotFound