|
|
||
|---|---|---|
| .. | ||
| Images | ||
| README.md | ||
| azuredeploy.json | ||
README.md
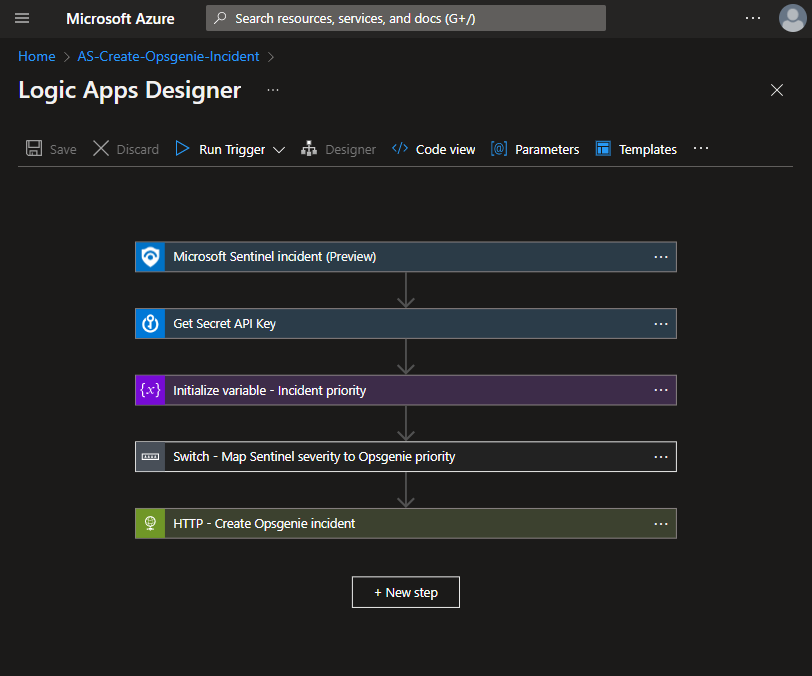
AS-Create-Opsgenie-Incident
Author: Accelerynt
For any technical questions, please contact info@accelerynt.com
This playbook is intended to be run from a Microsoft Sentinel Incident. It will create either an incident or an alert in Opsgenie with the information from a Microsoft Sentinel incident.
This playbook maps Microsoft Sentinel incident severity over to Opsgenie incident/alert priority like so:
| Microsoft Sentinel | Opsgenie |
|---|---|
| High | P2 - High |
| Medium | P3 - Moderate |
| Low | P4 - Low |
| Informational | P5 - Informational |
Requirements
The following items are required under the template settings during deployment:
- An Opsgenie account and an API integration
- For creating Opsgenie incidents, a standard or enterprise plan is needed. This is not a requirement for creating Opsgenie alerts. It should be noted that structurally, incident and alert objects are nearly identical in Opsgenie, and either works well with Microsoft Sentinel incident data. If you are using a trial account, select the alert endpoint during deployment
- An Azure Key Vault Secret containing your Okta API Token
Setup
Create an Opsgenie API integration
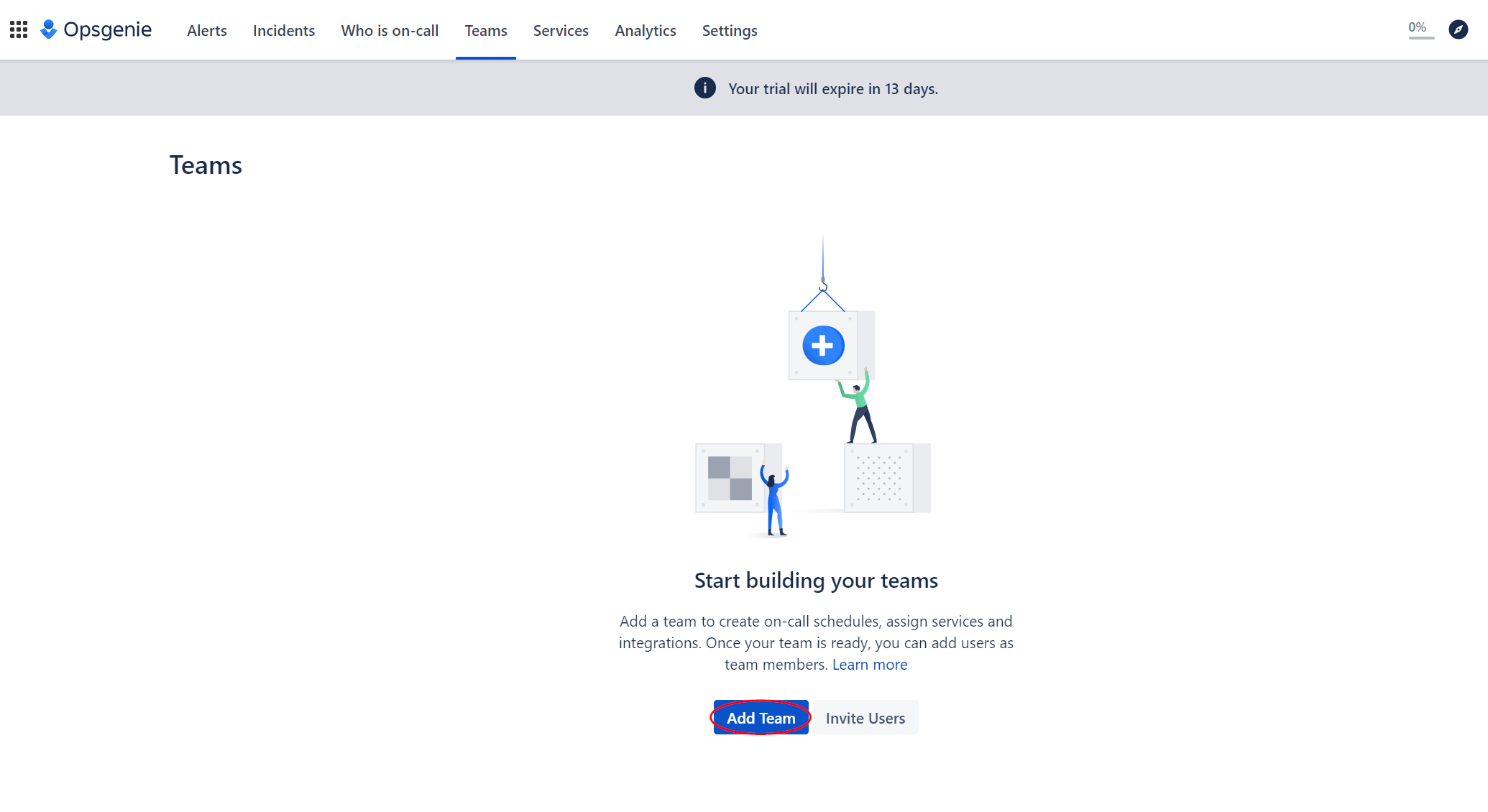
From your Opsgenie account, select the "Teams" tab, and then click "Add Team".
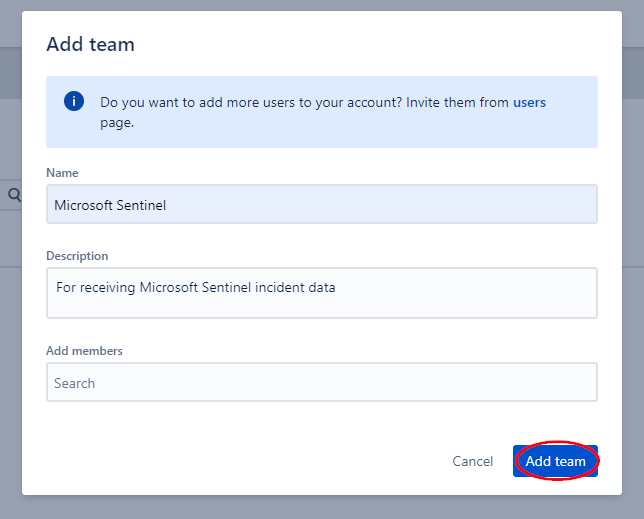
Enter "Microsoft Sentinel" in the name field and add an optional description, then click "Add team".
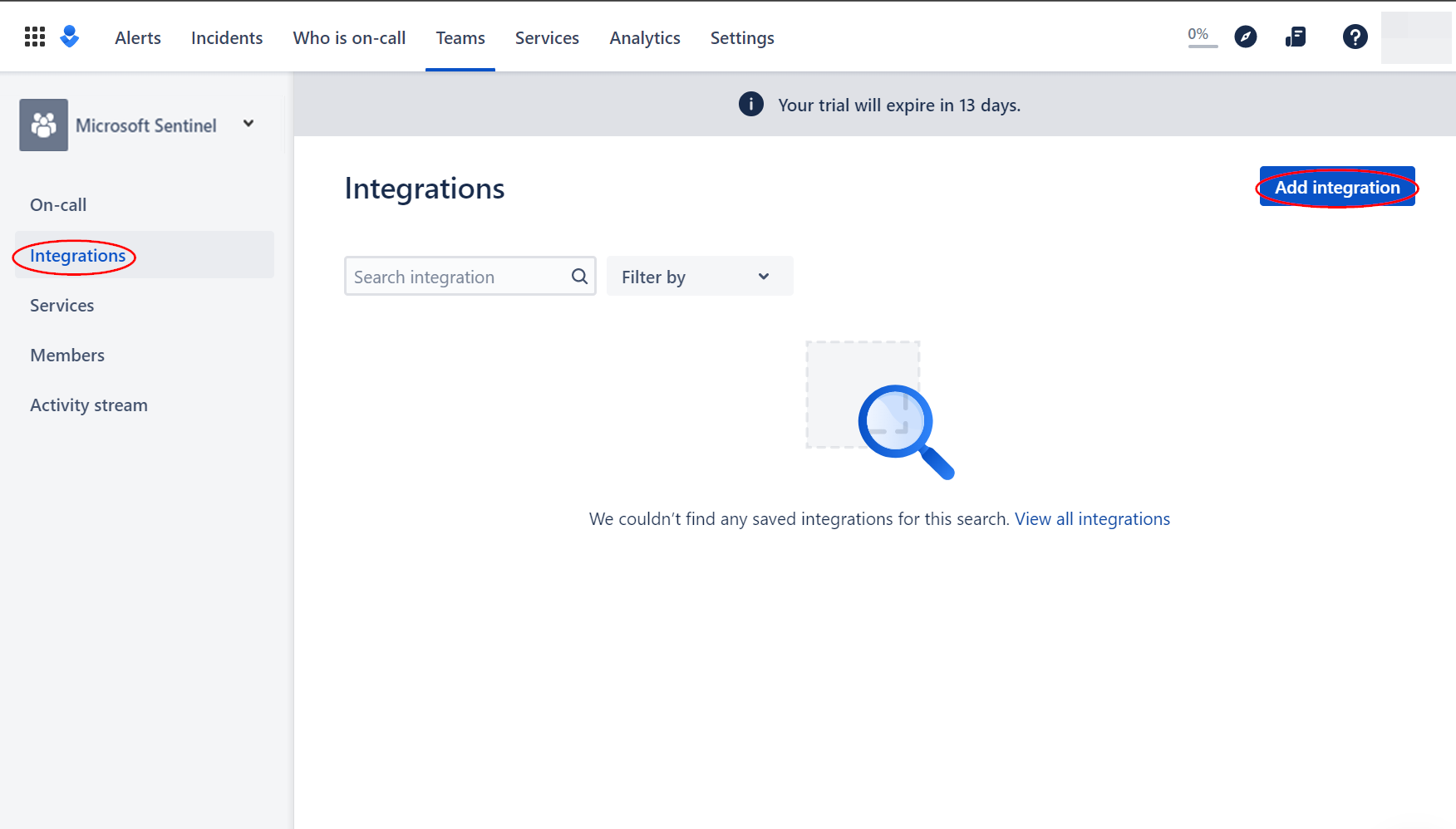
From the newly created team page, navigate to "Integrations" from the left menu blade, then click "Add integration".
Although there are pre-built integration apps for Microsoft Azure, there is currently not one for Microsoft Sentinel, therefore the "API" integration must be selected.
Take note of the "API Key" that is generated, as it will be needed later, then click "Save integration".
Create an Azure Key Vault Secret:
Navigate to the Azure Key Vaults page: https://portal.azure.com/#view/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults
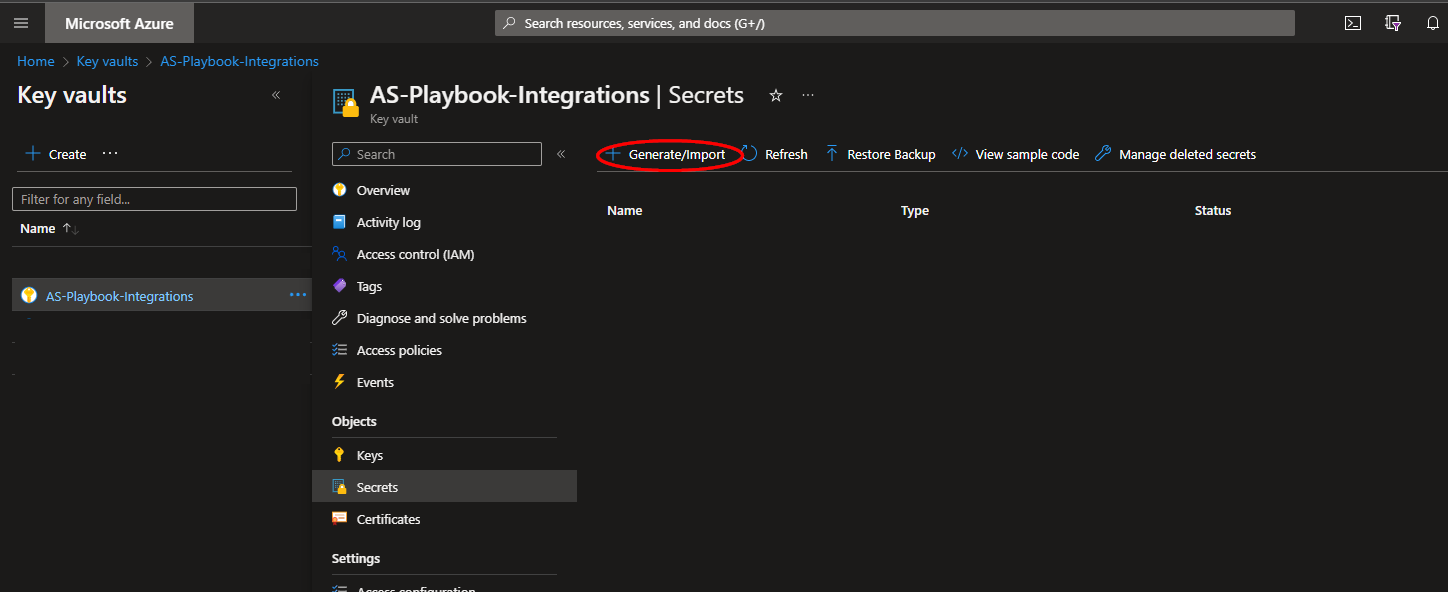
Navigate to an existing Key Vault or create a new one. From the Key Vault overview page, click the "Secrets" menu option, found under the "Settings" section. Click "Generate/Import".
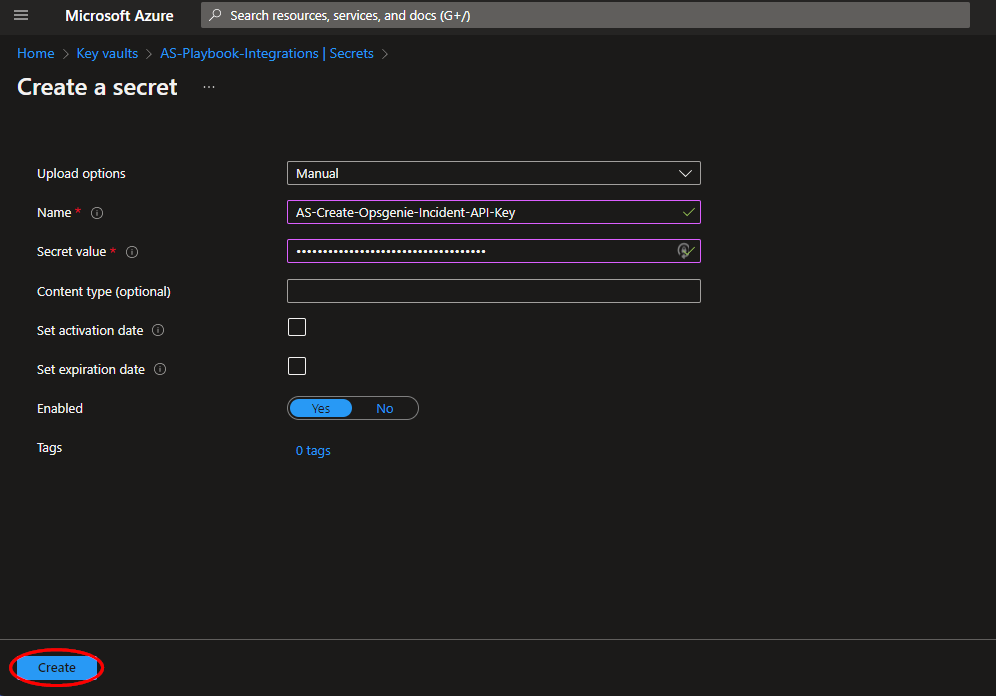
Choose a name for the secret, such as "AS-Create-Opsgenie-Incident-API-Key", and enter the Opsgenie API Key copied previously in the previous section. All other settings can be left as is. Click "Create".
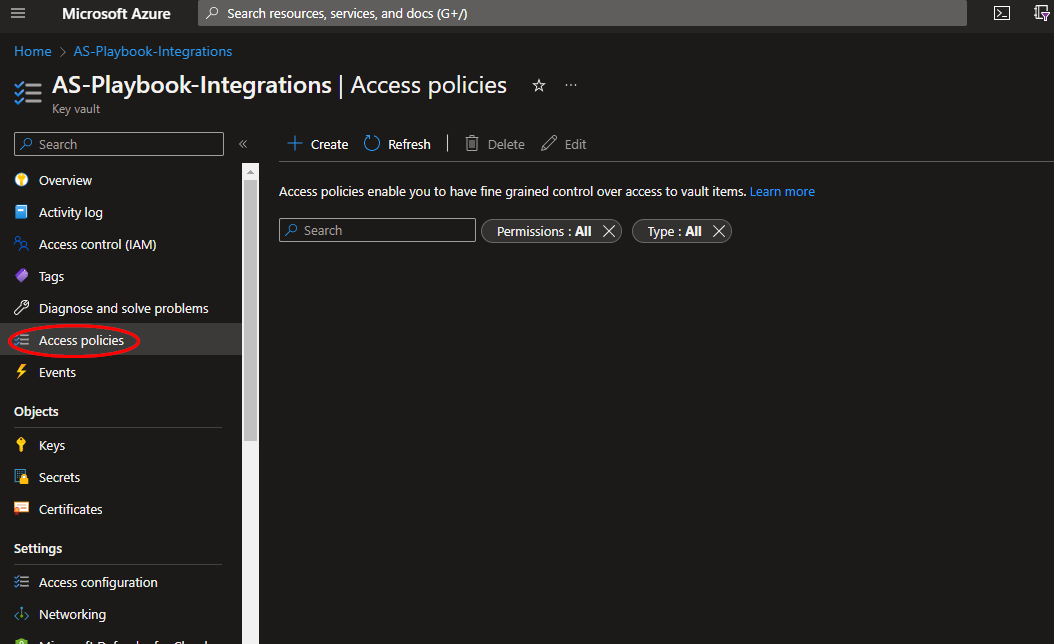
Once your secret has been added to the vault, navigate to the "Access policies" menu option, also found under the "Settings" section on the Key Vault page menu. Leave this page open, as you will need to return to it once the playbook has been deployed. See Granting Access to Azure Key Vault.
Deployment
To configure and deploy this playbook:
Open your browser and ensure you are logged into your Microsoft Sentinel workspace. In a separate tab, open the link to our playbook on the Accelerynt Security GitHub Repository:
https://github.com/Accelerynt-Security/AS-Create-Opsgenie-Incident
Click the “Deploy to Azure” button at the bottom and it will bring you to the custom deployment template.
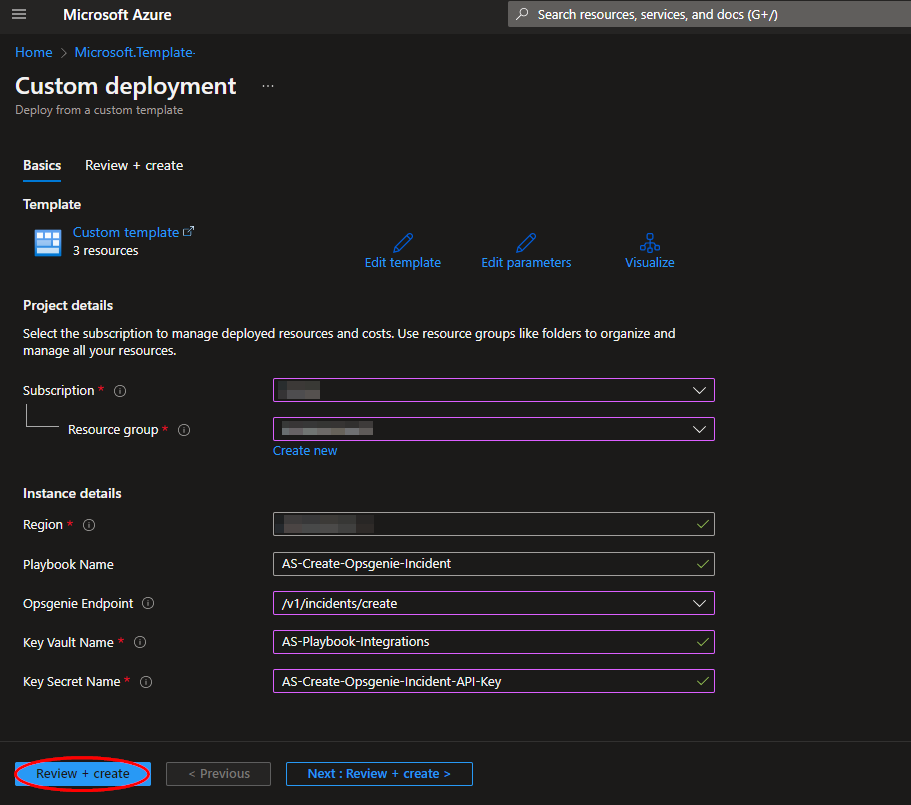
In the Project Details section:
- Select the “Subscription” and “Resource Group” from the dropdown boxes you would like the playbook deployed to.
In the Instance Details section:
-
Playbook Name: This can be left as "AS-Create-Opsgenie-Incident" or you may change it.
-
Opsgenie Endpoint: This can be left as "/v1/incidents/create" if mapping Microsoft Sentinel incidents to Opsgenie incidents, or changed to "/v2/alerts" if mapping Microsoft Sentinel incidents to Opsgenie alerts.
-
Key Vault Name: Enter the name of the Key Vault referenced in Create an Azure Key Vault Secret.
-
Secret Name: Enter the name of the Key Vault Secret created in Create an Azure Key Vault Secret.
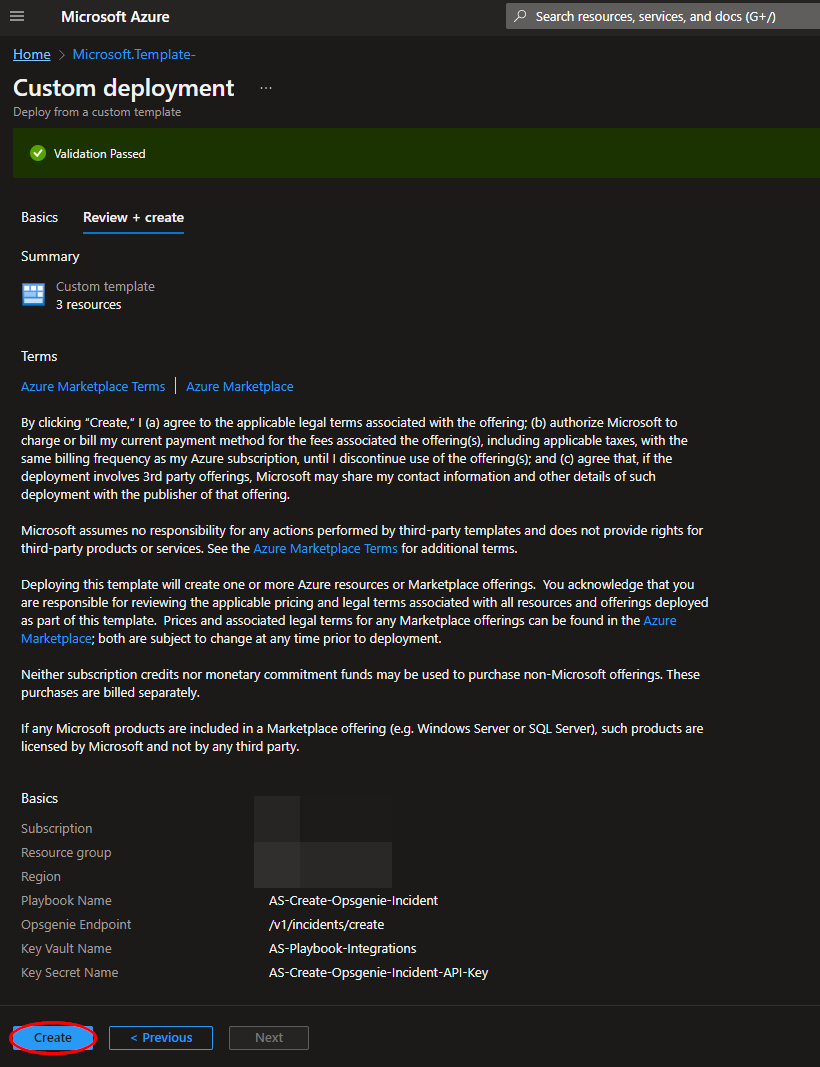
Towards the bottom, click on “Review + create”.
Once the resources have validated, click on "Create".
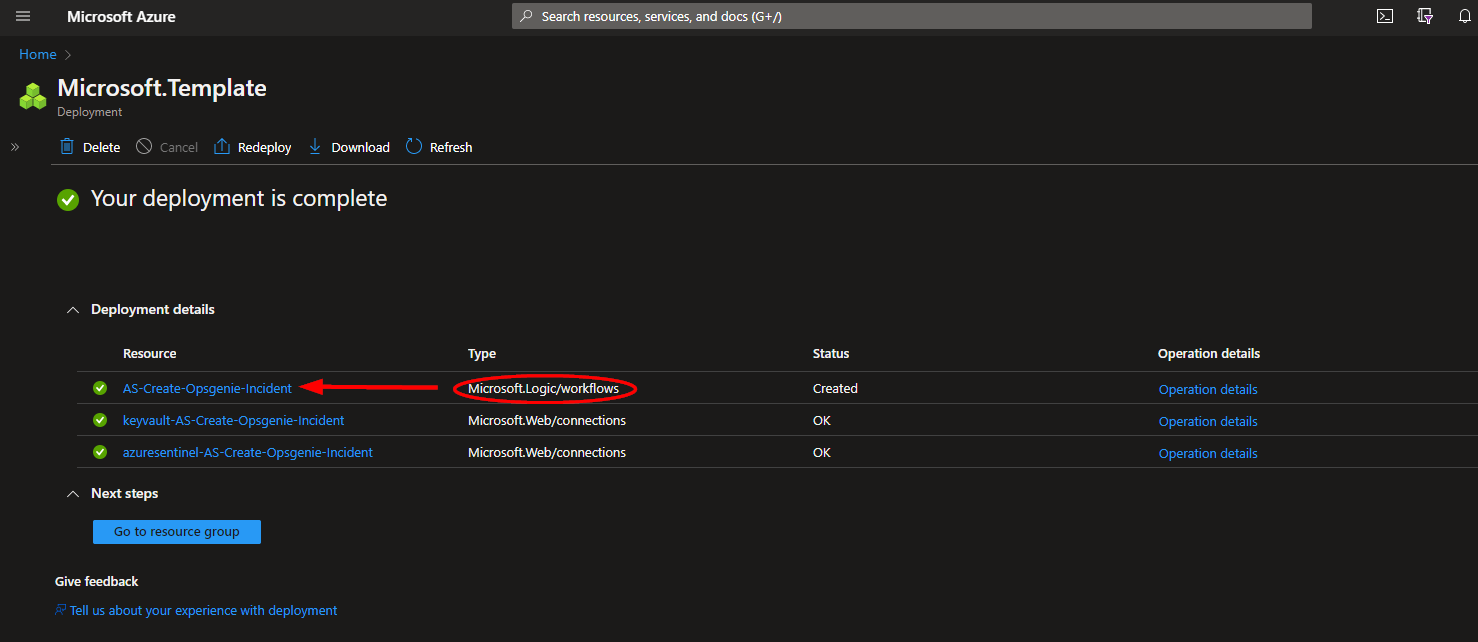
The resources should take around a minute to deploy. Once the deployment is complete, you can expand the "Deployment details" section to view them. To view the deployed Logic App, click the resource that corresponds to it.
Granting Access to Azure Key Vault
Before the Logic App can run successfully, the Key Vault connection created during deployment must be granted access to the Key Vault storing your Okta API Token.
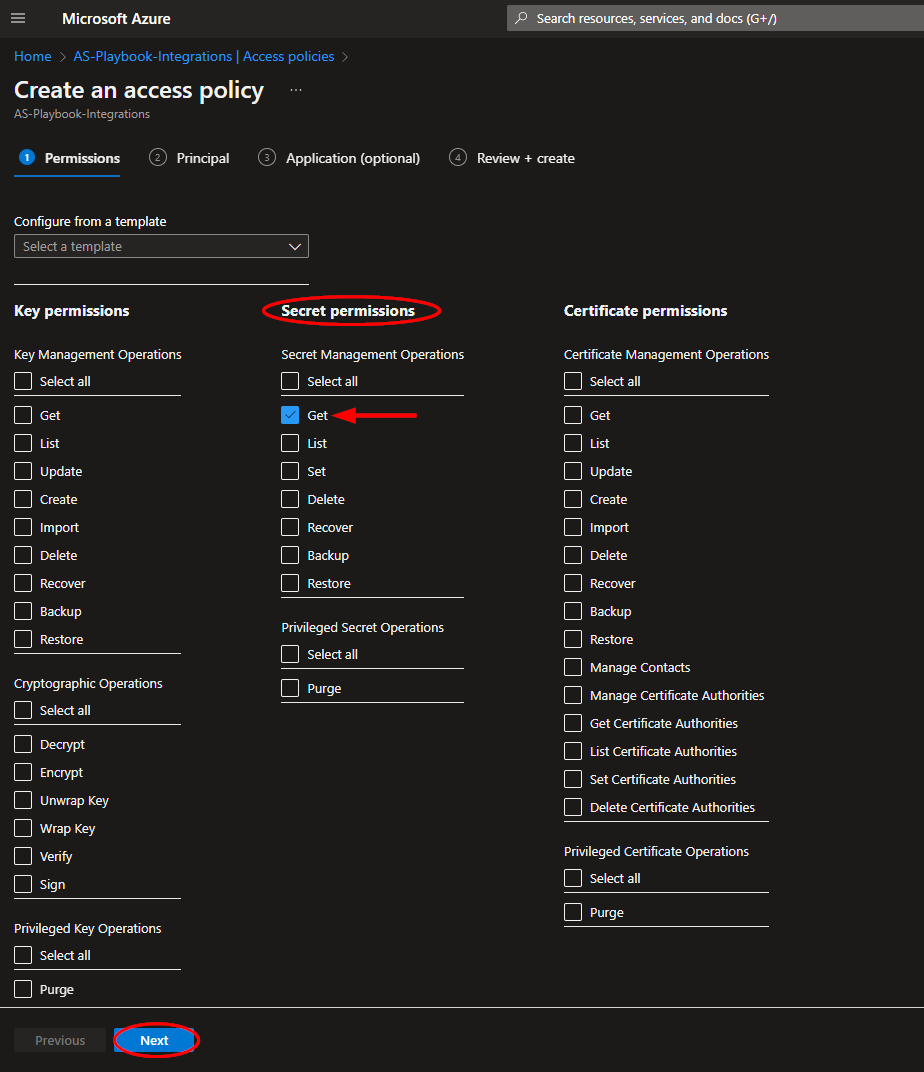
From the Key Vault "Access policies" page, click "Create".
Select the "Get" checkbox under "Secret permissions", then click "Next".
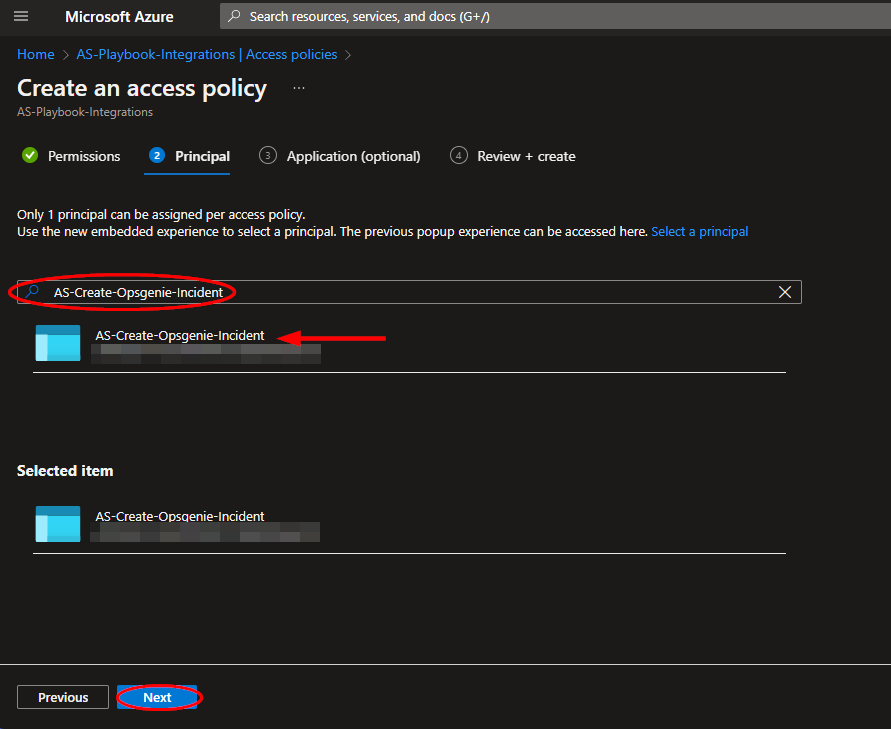
Paste "AS-Create-Opsgenie-Incident" into the principal search box and click the option that appears. Click "Next" towards the bottom of the page.
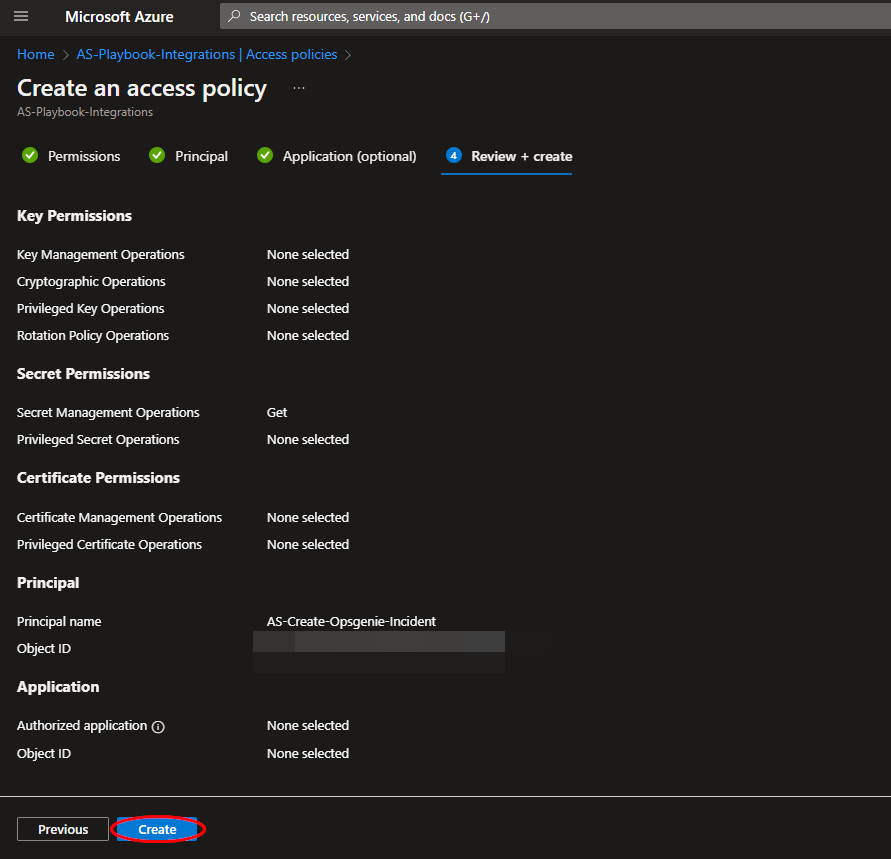
Navigate to the "Review + create" section and click "Create".