1052 строки
938 KiB
JSON
1052 строки
938 KiB
JSON
{
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "1.0.0.0",
|
||
"metadata": {
|
||
"author": "Microsoft - support@microsoft.com",
|
||
"comments": "Solution template for ZeroTrust(TIC3.0)"
|
||
},
|
||
"parameters": {
|
||
"location": {
|
||
"type": "string",
|
||
"minLength": 1,
|
||
"defaultValue": "[resourceGroup().location]",
|
||
"metadata": {
|
||
"description": "Not used, but needed to pass arm-ttk test `Location-Should-Not-Be-Hardcoded`. We instead use the `workspace-location` which is derived from the LA workspace"
|
||
}
|
||
},
|
||
"workspace-location": {
|
||
"type": "string",
|
||
"defaultValue": "",
|
||
"metadata": {
|
||
"description": "[concat('Region to deploy solution resources -- separate from location selection',parameters('location'))]"
|
||
}
|
||
},
|
||
"workspace": {
|
||
"defaultValue": "",
|
||
"type": "string",
|
||
"metadata": {
|
||
"description": "Workspace name for Log Analytics where Microsoft Sentinel is setup"
|
||
}
|
||
},
|
||
"workbook1-name": {
|
||
"type": "string",
|
||
"defaultValue": "ZeroTrust(TIC3.0)",
|
||
"minLength": 1,
|
||
"metadata": {
|
||
"description": "Name for the workbook"
|
||
}
|
||
}
|
||
},
|
||
"variables": {
|
||
"email": "support@microsoft.com",
|
||
"_email": "[variables('email')]",
|
||
"_solutionName": "ZeroTrust(TIC3.0)",
|
||
"_solutionVersion": "3.0.1",
|
||
"solutionId": "azuresentinel.azure-sentinel-solution-zerotrust",
|
||
"_solutionId": "[variables('solutionId')]",
|
||
"workbookVersion1": "1.0.0",
|
||
"workbookContentId1": "ZeroTrust(TIC3.0)Workbook",
|
||
"workbookId1": "[resourceId('Microsoft.Insights/workbooks', variables('workbookContentId1'))]",
|
||
"workbookTemplateSpecName1": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat(parameters('workspace'),'-wb-',uniquestring(variables('_workbookContentId1'))))]",
|
||
"_workbookContentId1": "[variables('workbookContentId1')]",
|
||
"workspaceResourceId": "[resourceId('microsoft.OperationalInsights/Workspaces', parameters('workspace'))]",
|
||
"_workbookcontentProductId1": "[concat(take(variables('_solutionId'),50),'-','wb','-', uniqueString(concat(variables('_solutionId'),'-','Workbook','-',variables('_workbookContentId1'),'-', variables('workbookVersion1'))))]",
|
||
"analyticRuleObject1": {
|
||
"analyticRuleVersion1": "1.0.0",
|
||
"_analyticRulecontentId1": "4942992d-a4d3-44b0-9cf4-b5a23811d82d",
|
||
"analyticRuleId1": "[resourceId('Microsoft.SecurityInsights/AlertRuleTemplates', '4942992d-a4d3-44b0-9cf4-b5a23811d82d')]",
|
||
"analyticRuleTemplateSpecName1": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat(parameters('workspace'),'-ar-',uniquestring('4942992d-a4d3-44b0-9cf4-b5a23811d82d')))]",
|
||
"_analyticRulecontentProductId1": "[concat(take(variables('_solutionId'),50),'-','ar','-', uniqueString(concat(variables('_solutionId'),'-','AnalyticsRule','-','4942992d-a4d3-44b0-9cf4-b5a23811d82d','-', '1.0.0')))]"
|
||
},
|
||
"Notify_GovernanceComplianceTeam-ZeroTrust": "Notify_GovernanceComplianceTeam-ZeroTrust",
|
||
"_Notify_GovernanceComplianceTeam-ZeroTrust": "[variables('Notify_GovernanceComplianceTeam-ZeroTrust')]",
|
||
"playbookVersion1": "1.0",
|
||
"playbookContentId1": "Notify_GovernanceComplianceTeam-ZeroTrust",
|
||
"_playbookContentId1": "[variables('playbookContentId1')]",
|
||
"playbookId1": "[resourceId('Microsoft.Logic/workflows', variables('playbookContentId1'))]",
|
||
"playbookTemplateSpecName1": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat(parameters('workspace'),'-pl-',uniquestring(variables('_playbookContentId1'))))]",
|
||
"_playbookcontentProductId1": "[concat(take(variables('_solutionId'),50),'-','pl','-', uniqueString(concat(variables('_solutionId'),'-','Playbook','-',variables('_playbookContentId1'),'-', variables('playbookVersion1'))))]",
|
||
"Open_DevOpsTaskRecommendation-ZeroTrust": "Open_DevOpsTaskRecommendation-ZeroTrust",
|
||
"_Open_DevOpsTaskRecommendation-ZeroTrust": "[variables('Open_DevOpsTaskRecommendation-ZeroTrust')]",
|
||
"playbookVersion2": "1.0",
|
||
"playbookContentId2": "Open_DevOpsTaskRecommendation-ZeroTrust",
|
||
"_playbookContentId2": "[variables('playbookContentId2')]",
|
||
"playbookId2": "[resourceId('Microsoft.Logic/workflows', variables('playbookContentId2'))]",
|
||
"playbookTemplateSpecName2": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat(parameters('workspace'),'-pl-',uniquestring(variables('_playbookContentId2'))))]",
|
||
"_playbookcontentProductId2": "[concat(take(variables('_solutionId'),50),'-','pl','-', uniqueString(concat(variables('_solutionId'),'-','Playbook','-',variables('_playbookContentId2'),'-', variables('playbookVersion2'))))]",
|
||
"Open_JIRATicketRecommendation-ZeroTrust": "Open_JIRATicketRecommendation-ZeroTrust",
|
||
"_Open_JIRATicketRecommendation-ZeroTrust": "[variables('Open_JIRATicketRecommendation-ZeroTrust')]",
|
||
"playbookVersion3": "1.0",
|
||
"playbookContentId3": "Open_JIRATicketRecommendation-ZeroTrust",
|
||
"_playbookContentId3": "[variables('playbookContentId3')]",
|
||
"playbookId3": "[resourceId('Microsoft.Logic/workflows', variables('playbookContentId3'))]",
|
||
"playbookTemplateSpecName3": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat(parameters('workspace'),'-pl-',uniquestring(variables('_playbookContentId3'))))]",
|
||
"_playbookcontentProductId3": "[concat(take(variables('_solutionId'),50),'-','pl','-', uniqueString(concat(variables('_solutionId'),'-','Playbook','-',variables('_playbookContentId3'),'-', variables('playbookVersion3'))))]",
|
||
"_solutioncontentProductId": "[concat(take(variables('_solutionId'),50),'-','sl','-', uniqueString(concat(variables('_solutionId'),'-','Solution','-',variables('_solutionId'),'-', variables('_solutionVersion'))))]"
|
||
},
|
||
"resources": [
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentTemplates",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"name": "[variables('workbookTemplateSpecName1')]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"dependsOn": [
|
||
"[extensionResourceId(resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspace')), 'Microsoft.SecurityInsights/contentPackages', variables('_solutionId'))]"
|
||
],
|
||
"properties": {
|
||
"description": "ZeroTrustTIC3 Workbook with template version 3.0.1",
|
||
"mainTemplate": {
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "[variables('workbookVersion1')]",
|
||
"parameters": {},
|
||
"variables": {},
|
||
"resources": [
|
||
{
|
||
"type": "Microsoft.Insights/workbooks",
|
||
"name": "[variables('workbookContentId1')]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"kind": "shared",
|
||
"apiVersion": "2021-08-01",
|
||
"metadata": {
|
||
"description": "Sets the time name for analysis"
|
||
},
|
||
"properties": {
|
||
"displayName": "[parameters('workbook1-name')]",
|
||
"serializedData": "{\"version\":\"Notebook/1.0\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a4b4e975-fa7c-46a3-b669-850aacc88134\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Help\",\"label\":\"🔎 Guide\",\"type\":10,\"isRequired\":true,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Yes\\\", \\\"label\\\": \\\"Yes\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"No\\\", \\\"label\\\": \\\"No\\\"}\\r\\n]\",\"value\":\"No\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"DefaultSubscription_Internal\",\"type\":1,\"isRequired\":true,\"query\":\"where type =~ 'microsoft.operationalinsights/workspaces'\\r\\n| take 1\\r\\n| project subscriptionId\",\"crossComponentResources\":[\"value::selected\"],\"isHiddenWhenLocked\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\"},{\"id\":\"e6ded9a1-a83c-4762-938d-5bf8ff3d3d38\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Subscription\",\"type\":6,\"isRequired\":true,\"multiSelect\":true,\"quote\":\"'\",\"delimiter\":\",\",\"query\":\"summarize by subscriptionId\\r\\n| project value = strcat(\\\"/subscriptions/\\\", subscriptionId), label = subscriptionId, selected = iff(subscriptionId =~ '{DefaultSubscription_Internal}', true, false)\",\"crossComponentResources\":[\"value::all\"],\"typeSettings\":{\"additionalResourceOptions\":[\"value::all\"],\"showDefault\":false},\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"value\":[\"value::all\"]},{\"id\":\"e3225ed0-6210-40a1-b2d0-66e42ffa71d6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Workspace\",\"type\":5,\"isRequired\":true,\"multiSelect\":true,\"quote\":\"'\",\"delimiter\":\",\",\"query\":\"resources\\r\\n| where type =~ 'microsoft.operationalinsights/workspaces'\\r\\n| order by name asc\\r\\n| summarize Selected = makelist(id, 10), All = makelist(id, 1000)\\r\\n| mvexpand All limit 100\\r\\n| project value = tostring(All), label = tostring(All), selected = iff(Selected contains All, true, false)\",\"crossComponentResources\":[\"{Subscription}\"],\"typeSettings\":{\"additionalResourceOptions\":[\"value::all\"],\"showDefault\":false},\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"value\":[\"value::all\"]},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"TimeRange\",\"type\":4,\"isRequired\":true,\"value\":{\"durationMs\":604800000},\"typeSettings\":{\"selectableValues\":[{\"durationMs\":604800000},{\"durationMs\":1209600000},{\"durationMs\":2592000000}],\"allowCustom\":true},\"id\":\"6539479a-3e0d-42c6-bcbe-2d1f11bb9896\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Parameter Selectors\"},{\"type\":1,\"content\":{\"json\":\"<svg viewBox=\\\"0 0 19 19\\\" width=\\\"20\\\" class=\\\"fxt-escapeShadow\\\" role=\\\"presentation\\\" focusable=\\\"false\\\" xmlns:svg=\\\"http://www.w3.org/2000/svg\\\" xmlns:xlink=\\\"http://www.w3.org/1999/xlink\\\" aria-hidden=\\\"true\\\"><g><path fill=\\\"#1b93eb\\\" d=\\\"M16.82 8.886c0 4.81-5.752 8.574-7.006 9.411a.477.477 0 01-.523 0C8.036 17.565 2.18 13.7 2.18 8.886V3.135a.451.451 0 01.42-.419C7.2 2.612 6.154.625 9.5.625s2.3 1.987 6.8 2.091a.479.479 0 01.523.419z\\\"></path><path fill=\\\"url(#0024423711759027356)\\\" d=\\\"M16.192 8.99c0 4.392-5.333 7.947-6.483 8.575a.319.319 0 01-.418 0c-1.15-.732-6.483-4.183-6.483-8.575V3.762a.575.575 0 01.313-.523C7.2 3.135 6.258 1.357 9.4 1.357s2.2 1.882 6.274 1.882a.45.45 0 01.419.418z\\\"></path><path d=\\\"M9.219 5.378a.313.313 0 01.562 0l.875 1.772a.314.314 0 00.236.172l1.957.284a.314.314 0 01.174.535l-1.416 1.38a.312.312 0 00-.09.278l.334 1.949a.313.313 0 01-.455.33l-1.75-.92a.314.314 0 00-.292 0l-1.75.92a.313.313 0 01-.455-.33L7.483 9.8a.312.312 0 00-.09-.278L5.977 8.141a.314.314 0 01.174-.535l1.957-.284a.314.314 0 00.236-.172z\\\" class=\\\"msportalfx-svg-c01\\\"></path></g></svg> <span style=\\\"font-family: Open Sans; font-weight: 620; font-size: 14px;font-style: bold;margin:-10px 0px 0px 0px;position: relative;top:-3px;left:-4px;\\\"> Please take time to answer a quick survey,\\r\\n</span>[<span style=\\\"font-family: Open Sans; font-weight: 620; font-size: 14px;font-style: bold;margin:-10px 0px 0px 0px;position: relative;top:-3px;left:-4px;\\\"> click here. </span>](https://forms.office.com/r/0xxx6arkaS)\"},\"name\":\"Survey\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"## Getting Started\\r\\nThis solution is designed to augment staffing through automation, machine learning, query/alerting generation, and visualizations. This workbook leverages Azure Policy, Azure Resource Graph, and Azure Log Analytics to align with Zero Trust (TIC 3.0) control requirements. A filter set is available for custom reporting by guides, subscriptions, workspaces, time-filtering, control family, and controls. This offering telemetry from 25+ Microsoft Security and partner offerings, while only Microsoft Sentinel and Microsoft Defender for Cloud are required to get started, each offering provides additional enrichment for aligning with control requirements. Each control includes a Control Card detailing an overview of requirements, primary/secondary controls, deep-links to referenced product pages/portals, recommendations, implementation guides, compliance cross-walks and tooling telemetry for building situational awareness of cloud workloads. \\r\\n\\r\\n### [Recommended Microsoft Sentinel Roles](https://docs.microsoft.com/azure/sentinel/roles) / [Recommended Microsoft Defender for Cloud Roles](https://docs.microsoft.com/azure/defender-for-cloud/permissions#roles-and-allowed-actions)\\r\\n| <strong> Roles </strong> | <strong> Rights </strong> | \\r\\n|:--|:--|\\r\\n|Security Reader | View Workbooks, Analytics, Hunting, Security Recommendations |\\r\\n|Security Contributor| Deploy/Modify Workbooks, Analytics, Hunting Queries, Apply Security Recommendations |\\r\\n|Automation Contributor| Deploy/Modify Playbooks & Automation Rules |\\r\\n\\r\\n### Onboarding Prerequisites \\r\\n1️⃣ [Access Microsoft 365 Compliance Manager: Assessments](https://compliance.microsoft.com/compliancemanager?viewid=Assessments)<br>\\r\\n2️⃣ [Onboard Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/quickstart-onboard)<br>\\r\\n3️⃣ [Onboard Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/security-center-get-started)<br>\\r\\n4️⃣ [Continuously Export Security Center Data to Log Analytics Workspace](https://docs.microsoft.com/azure/security-center/continuous-export)<br>\\r\\n5️⃣ [Extend Microsoft Sentinel Across Workspaces and Tenants](https://docs.microsoft.com/azure/sentinel/extend-sentinel-across-workspaces-tenants)<br>\\r\\n6️⃣ [Implement CLAW Aggregator](https://github.com/Azure/trusted-internet-connection)<br>\\r\\n7️⃣ [Configure Auto Provisioning of Microsoft Defender for Cloud Agents](https://docs.microsoft.com/azure/defender-for-cloud/enable-data-collection)<br>\\r\\n8️⃣ [Review Microsoft Service Trust Portal Documentation/Audit/Resources](https://servicetrust.microsoft.com/)<br>\\r\\n\\r\\n### Recommended Enrichments\\r\\n✳️[Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n✳️[Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n✳️[Azure Firewall Premium](https://azure.microsoft.com/services/azure-firewall)<br>\\r\\n✳️[Microsoft Defender for Endpoint](https://www.microsoft.com/microsoft-365/security/endpoint-defender)<br>\\r\\n✳️[Azure Virtual Desktop](https://azure.microsoft.com/services/virtual-desktop/)<br>\\r\\n✳️[Azure Web Application Firewall](https://azure.microsoft.com/services/web-application-firewall/)<br>\\r\\n✳️[Azure Information Protection](https://azure.microsoft.com/services/information-protection/)<br>\\r\\n✳️[Microsoft 365 Defender](https://www.microsoft.com/microsoft-365/security/microsoft-365-defender)<br>\\r\\n✳️[Microsoft Defender for Cloud Apps](https://www.microsoft.com/microsoft-365/enterprise-mobility-security/cloud-app-security)<br>\\r\\n✳️[Key Vault](https://azure.microsoft.com/services/key-vault/)<br>\\r\\n✳️[Azure DDoS Protection](https://azure.microsoft.com/services/ddos-protection/)<br>\\r\\n✳️[Microsoft Defender for Identity](https://www.microsoft.com/microsoft-365/security/identity-defender)<br>\\r\\n\\r\\n### Print/Export Report\\r\\n1️⃣ Set Background Theme: Settings > Appearance > Theme: Azure > Apply<br>\\r\\n2️⃣ Print/Export Report: More Content Actions (...) > Print Content<br>\\r\\n3️⃣ Settings: Layout (Landscape), Pages (All), Print (One Sided), Scale (60), Pages Per Sheet (1), Quality (1,200 DPI), Margins (None) > Print<br>\\r\\n\\r\\n### Important\\r\\nThis solution provides visibility and situational awareness for security capabilities delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user and some panels may require additional configurations for operation. Recommendations do not imply coverage of respective controls as they are often one of several courses of action for approaching requirements which is unique to each customer. Recommendations should be considered a starting point for planning full or partial coverage of respective requirements. Each control is associated with one or more 💡[Azure Policy](https://docs.microsoft.com/azure/governance/policy/overview) definitions. These policies may help you 💡[assess compliance](https://docs.microsoft.com/azure/governance/policy/how-to/get-compliance-data) with the control; however, there often is not a one-to-one or complete match between a control and one or more policies. As such, Compliant in Azure Policy refers only to the policy definitions themselves; this doesn't ensure you're fully compliant with all requirements of a control. In addition, the compliance standard includes controls that aren't addressed by any Azure Policy definitions at this time. Therefore, compliance in Azure Policy is only a partial view of your overall compliance status. The associations between compliance domains, controls, and Azure Policy definitions for this compliance standard may change over time. \",\"style\":\"info\"},\"name\":\"Help\"},{\"type\":1,\"content\":{\"json\":\"# ✳️ [Microsoft Zero Trust Deployment Center](https://docs.microsoft.com/security/zero-trust)\\r\\n\\r\\n\\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"Help\",\"comparison\":\"isEqualTo\",\"value\":\"Yes\"},\"name\":\"Zero Trust Model\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"10\",\"conditionalVisibility\":{\"parameterName\":\"Help\",\"comparison\":\"isEqualTo\",\"value\":\"Yes\"},\"name\":\"text - 109\"},{\"type\":1,\"content\":{\"json\":\"# ✳️ [Trusted Internet Connections 3.0](https://www.cisa.gov/trusted-internet-connections)\\r\\n\\r\\n| <em> Security Objectives </em> |\\r\\n| : | : | \\r\\n| <strong> Manage Traffic </strong>| Observe, validate, and filter data connections to align with authorized activities; least privilege and default deny |\\r\\n| <strong> Protect Traffic Confidentiality </strong>| Ensure only authorized parties can discern the contents of data in transit; sender and receiver identification and enforcement |\\r\\n| <strong> Protect Traffic Integrity </strong>| Prevent alteration of data in transit; detect altered data in transit |\\r\\n| <strong> Ensure Service Resiliency </strong>| Promote resilient application and security services for continuous operation as the technology and threat landscape evolve |\\r\\n| <strong> Ensure Effective Response </strong>| Promote timely reaction and adapt future response to discovered threats; policies defined and implemented; simplified adoption of new countermeasures |\\r\\n\\r\\n\"},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"Help\",\"comparison\":\"isEqualTo\",\"value\":\"Yes\"},\"name\":\"Trusted Internet Connections 3.0\"}],\"exportParameters\":true},\"conditionalVisibility\":{\"parameterName\":\"Help\",\"comparison\":\"isEqualTo\",\"value\":\"Yes\"},\"name\":\"Help Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Zero Trust (TIC 3.0) Solution](https://docs.microsoft.com/security/zero-trust/integrate/sentinel-solution)\\n---\\nThe Microsoft Sentinel Zero Trust (TIC 3.0) Solution provides a mechanism for viewing log queries aligned to Zero Trust and Trusted Internet Connections models across the Microsoft and partner ecosystem. This solution enables governance and compliance teams to design, build, monitor, and respond to Zero Trust (TIC 3.0) requirements across cloud, multi-cloud, 1st/3rd party workloads. The solution includes the new Zero Trust (TIC 3.0) Workbook, (1) Analytics Rule, and (3) Playbooks. While only Microsoft Sentinel and Microsoft Defender for Cloud are required to get started, the solution is enhanced with numerous Microsoft offerings. This Solution enables Security Architects, Engineers, SecOps Analysts, Managers, and IT Pros to gain situational awareness visibility for the security posture of cloud, multi-cloud, hybrid, and on-premise workloads. For more information, see 💡[Microsoft Zero Trust Model](https://www.microsoft.com/security/business/zero-trust) 💡[Trusted Internet Connections](https://www.cisa.gov/trusted-internet-connections)\"},\"name\":\"Workbook Overview\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/next-evolution-of-the-microsoft-sentinel-zero-trust-tic-3-0/ba-p/3278097\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/CxLzTRPuw-4\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/ZeroTrust(TIC3.0)\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"}]},\"customWidth\":\"79\",\"name\":\"group - 22\"},{\"type\":1,\"content\":{\"json\":\" \"},\"customWidth\":\"21\",\"name\":\"Microsoft Sentinel Logo\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Executive Summary\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Assessment\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Controls Crosswalk\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"CC\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Recommended Data Connectors\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"DC\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Recommended Content\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"GC\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Azure Lighthouse\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"AL\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Universal Security Capabilities\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Universal Security Capabilities\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Files\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Files\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Capabilities\\\\\\\": \\\\\\\"Email\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Email\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 107\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"cec6c07e-2856-4c77-8b48-98935f2c1218\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAssessmentVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Assessment\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isControlsCrosswalkVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"CC\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"20f1daf6-59a0-4673-b1bf-cc388d52debf\"},{\"id\":\"2919b971-fb14-440c-ab42-50304df3ceab\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDCVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"DC\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isGCVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"GC\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"fa7b0ee3-8d6e-4ff7-bb64-cf2241f30f98\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAzureLighthouseVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"AL\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"9944cda7-77aa-4189-8061-afc260130b84\"},{\"id\":\"eab3e5a8-66c3-4304-8c2b-43264e858ba8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isUniversalSecurityCapabilitiesVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Universal Security Capabilities\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isFilesVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Files\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"67de7a24-1840-4fc5-94d5-a6b5d7520a7c\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEmailVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Email\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"ec480379-6561-4a30-b005-7533da78ed14\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"isVisible Navigation\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Web\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Web\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Networking\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Networking\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Resiliency\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Resiliency\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"DNS\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"DNS\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Intrusion Detection\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Intrusion Detection\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Enterprise\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Enterprise\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Unified Communications & Collaboration\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Unified Communications & Collaboration\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control Family\\\\\\\": \\\\\\\"Data Protection\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data Protection\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 109\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"740b611b-8155-4e96-bbcc-bbdba0541143\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isWebVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Web\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"62d67234-8fb2-43e6-b5d2-945692493431\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isNetworkingVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Networking\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isResiliencyVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Resiliency\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"4f04758a-2908-474e-bfe0-13d072241fd2\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDNSVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"DNS\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"9cb339a8-c8b4-43ad-b2e5-76f61b87d8c1\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIntrusionDetectionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Intrusion Detection\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"4b799471-726e-432c-b577-2f45474d883c\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEnterpriseVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Enterprise\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"584fbe21-b31b-49cb-bd65-62ef850a8310\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isUnifiedCommunicationsCollaborationVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Unified Communications & Collaboration\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"78d61c25-823a-4232-8a32-1a7e7018e596\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataProtectionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data Protection\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"4da988d5-15f9-4ea8-bbd5-2153bfcae0a0\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"isVisible Navigation - Copy\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Executive Summary](https://docs.microsoft.com/azure/defender-for-cloud/review-security-recommendations)\\r\\n---\\r\\nThis section provides a mechanism to find, fix, and resolve Zero Trust (TIC 3.0) recommendations. A selector provides capability to filter by all, specific, or groups of TIC 3.0 control families. Upon selection, subordinate panels will summarize recommendations by control family, status over time, recommendations, and resources identified. These panels are helpful for identifying the controls of interest, status over time, and impacted resources. The recommendation details pane provides a mechanism to identify specific recommendation details with deep-links to pivot to Microsoft Defender for Cloud for remediation. \"},\"customWidth\":\"40\",\"name\":\"text - 5\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"10\",\"name\":\"text - 7\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"99a47f97-1aa4-4840-91ee-119aad6d6217\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ControlFamily\",\"label\":\"Control Family\",\"type\":2,\"isRequired\":true,\"multiSelect\":true,\"quote\":\"'\",\"delimiter\":\",\",\"value\":[\"value::all\"],\"typeSettings\":{\"additionalResourceOptions\":[\"value::all\"],\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Universal Security Capabilities\\\", \\\"label\\\": \\\"Universal Security Capabilities\\\"},\\r\\n {\\\"value\\\": \\\"Files\\\", \\\"label\\\": \\\"Files\\\"},\\r\\n {\\\"value\\\": \\\"Email\\\", \\\"label\\\": \\\"Email\\\"},\\r\\n {\\\"value\\\": \\\"Web\\\", \\\"label\\\": \\\"Web\\\"},\\r\\n {\\\"value\\\": \\\"Networking\\\", \\\"label\\\": \\\"Networking\\\"},\\r\\n {\\\"value\\\": \\\"Resiliency\\\", \\\"label\\\": \\\"Resiliency\\\"},\\r\\n {\\\"value\\\": \\\"DNS\\\", \\\"label\\\": \\\"DNS\\\"},\\r\\n {\\\"value\\\": \\\"Intrusion Detection\\\", \\\"label\\\": \\\"Intrusion Detection\\\"},\\r\\n {\\\"value\\\": \\\"Enterprise\\\", \\\"label\\\": \\\"Enterprise\\\"},\\r\\n {\\\"value\\\": \\\"Unified Communications & Collaboration\\\", \\\"label\\\": \\\"Unified Communications & Collaboration\\\"},\\r\\n {\\\"value\\\": \\\"Data Protection\\\", \\\"label\\\": \\\"Data Protection\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":7776000000},\"timeContextFromParameter\":\"TimeRange\",\"defaultValue\":\"value::all\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"40\",\"name\":\"parameters - 26\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityRecommendation\\r\\n| where RecommendationDisplayName <> \\\"\\\"\\r\\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\\\"email\\\"), \\\"Email\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"apps\\\", \\\"teams\\\", \\\"meeting\\\", \\\"call\\\"), \\\"Unified Communications & Collaboration\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"dns\\\", \\\"domain\\\"), \\\"DNS\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"endpoint protection\\\", \\\"malware\\\", \\\"file\\\", \\\"files\\\",\\\"IaaSAntimalware\\\"), \\\"Files\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"Security Center\\\",\\\"defender\\\", \\\"adaptive\\\", \\\"HoneyTokens\\\", \\\"honey\\\", \\\"deception\\\", \\\"intrusion\\\", \\\"incident\\\", \\\"incidents\\\"), \\\"Intrusion Detection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"firewall\\\", \\\"watcher\\\", \\\"proxy\\\", \\\"certificate\\\", \\\"url\\\", \\\"web\\\"), \\\"Web\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"network\\\", \\\"segment\\\", \\\"network security groups\\\", \\\"subnet\\\", \\\"application gateway\\\", \\\"security groups\\\", \\\"IP forwarding\\\", \\\"port\\\", \\\"ports\\\", \\\"networks\\\"), \\\"Networking\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"backup\\\",\\\"denial\\\", \\\"DDoS\\\", \\\"load\\\", \\\"scale\\\", \\\"front\\\", \\\"traffic manager\\\", \\\"pool\\\", \\\"disaster\\\", \\\"region\\\", \\\"redundant\\\", \\\"geo\\\"), \\\"Resiliency\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"rest\\\", \\\"transit\\\", \\\"data\\\", \\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\"), \\\"Data Protection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"private\\\", \\\"vpn\\\", \\\"automation\\\", \\\"playbook\\\", \\\"logic\\\", \\\"notification\\\", \\\"authorized\\\", \\\"safe\\\", \\\"network gateway\\\", \\\"express\\\", \\\"VPC\\\"), \\\"Enterprise\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"recover\\\", \\\"log\\\", \\\"configured\\\", \\\"configuration\\\", \\\"identity\\\", \\\"privilege\\\", \\\"admin\\\", \\\"authentication\\\", \\\"JIT\\\", \\\"just\\\", \\\"password\\\", \\\"time\\\", \\\"sync\\\", \\\"vulnerability\\\", \\\"Vulnerabilities\\\", \\\"updates\\\", \\\"update\\\", \\\"upgrade\\\", \\\"audit\\\", \\\"account\\\", \\\"guest\\\", \\\"shared\\\", \\\"access\\\", \\\"machines\\\", \\\"rights\\\", \\\"VM\\\", \\\"key\\\", \\\"keys\\\", \\\"IAM\\\", \\\"EC2\\\", \\\"GuardDuty\\\", \\\"logs\\\", \\\"CloudTrail\\\", \\\"MFA\\\", \\\"External accounts\\\", \\\"accounts\\\", \\\"config\\\", \\\"credentials\\\", \\\"privileged\\\", \\\"owner\\\", \\\"owners\\\", \\\"login\\\", \\\"logon\\\", \\\"virtual machine\\\", \\\"container\\\", \\\"containers\\\", \\\"Kubernetes\\\"), \\\"Universal Security Capabilities\\\", \\\"Other\\\")))))))))))\\r\\n| where ControlFamily in ({ControlFamily})\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by ControlFamily\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| project ControlFamily, Total, PassedControls, Passed, Failed\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Recommendations by Control Family\",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_compositeBar_Total_1\",\"sortOrder\":2}]},\"sortBy\":[{\"itemKey\":\"$gen_compositeBar_Total_1\",\"sortOrder\":2}]},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationDisplayName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName <> \\\"\\\"\\r\\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\\\"email\\\"), \\\"Email\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"apps\\\", \\\"teams\\\", \\\"meeting\\\", \\\"call\\\"), \\\"Unified Communications & Collaboration\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"dns\\\", \\\"domain\\\"), \\\"DNS\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"endpoint protection\\\", \\\"malware\\\", \\\"file\\\", \\\"files\\\",\\\"IaaSAntimalware\\\"), \\\"Files\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"Security Center\\\",\\\"defender\\\", \\\"adaptive\\\", \\\"HoneyTokens\\\", \\\"honey\\\", \\\"deception\\\", \\\"intrusion\\\", \\\"incident\\\", \\\"incidents\\\"), \\\"Intrusion Detection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"firewall\\\", \\\"watcher\\\", \\\"proxy\\\", \\\"certificate\\\", \\\"url\\\", \\\"web\\\"), \\\"Web\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"network\\\", \\\"segment\\\", \\\"network security groups\\\", \\\"subnet\\\", \\\"application gateway\\\", \\\"security groups\\\", \\\"IP forwarding\\\", \\\"port\\\", \\\"ports\\\", \\\"networks\\\"), \\\"Networking\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"backup\\\",\\\"denial\\\", \\\"DDoS\\\", \\\"load\\\", \\\"scale\\\", \\\"front\\\", \\\"traffic manager\\\", \\\"pool\\\", \\\"disaster\\\", \\\"region\\\", \\\"redundant\\\", \\\"geo\\\"), \\\"Resiliency\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"rest\\\", \\\"transit\\\", \\\"data\\\", \\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\"), \\\"Data Protection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"private\\\", \\\"vpn\\\", \\\"automation\\\", \\\"playbook\\\", \\\"logic\\\", \\\"notification\\\", \\\"authorized\\\", \\\"safe\\\", \\\"network gateway\\\", \\\"express\\\", \\\"VPC\\\"), \\\"Enterprise\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"recover\\\", \\\"log\\\", \\\"configured\\\", \\\"configuration\\\", \\\"identity\\\", \\\"privilege\\\", \\\"admin\\\", \\\"authentication\\\", \\\"JIT\\\", \\\"just\\\", \\\"password\\\", \\\"time\\\", \\\"sync\\\", \\\"vulnerability\\\", \\\"Vulnerabilities\\\", \\\"updates\\\", \\\"update\\\", \\\"upgrade\\\", \\\"audit\\\", \\\"account\\\", \\\"guest\\\", \\\"shared\\\", \\\"access\\\", \\\"machines\\\", \\\"rights\\\", \\\"VM\\\", \\\"key\\\", \\\"keys\\\", \\\"IAM\\\", \\\"EC2\\\", \\\"GuardDuty\\\", \\\"logs\\\", \\\"CloudTrail\\\", \\\"MFA\\\", \\\"External accounts\\\", \\\"accounts\\\", \\\"config\\\", \\\"credentials\\\", \\\"privileged\\\", \\\"owner\\\", \\\"owners\\\", \\\"login\\\", \\\"logon\\\", \\\"virtual machine\\\", \\\"container\\\", \\\"containers\\\", \\\"Kubernetes\\\"), \\\"Universal Security Capabilities\\\", \\\"Other\\\")))))))))))\\r\\n| where ControlFamily in ({ControlFamily})\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationDisplayName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationDisplayName\\r\\n| project RecommendationDisplayName, Total, RecommendationLink, PassedControls, Passed, Failed, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"rowLimit\":2500,\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_compositeBar_Total_1\",\"sortOrder\":2}]},\"sortBy\":[{\"itemKey\":\"$gen_compositeBar_Total_1\",\"sortOrder\":2}]},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityRecommendation\\r\\n| where RecommendationDisplayName <> \\\"\\\"\\r\\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\\\"email\\\"), \\\"Email\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"apps\\\", \\\"teams\\\", \\\"meeting\\\", \\\"call\\\"), \\\"Unified Communications & Collaboration\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"dns\\\", \\\"domain\\\"), \\\"DNS\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"endpoint protection\\\", \\\"malware\\\", \\\"file\\\", \\\"files\\\",\\\"IaaSAntimalware\\\"), \\\"Files\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"Security Center\\\",\\\"defender\\\", \\\"adaptive\\\", \\\"HoneyTokens\\\", \\\"honey\\\", \\\"deception\\\", \\\"intrusion\\\", \\\"incident\\\", \\\"incidents\\\"), \\\"Intrusion Detection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"firewall\\\", \\\"watcher\\\", \\\"proxy\\\", \\\"certificate\\\", \\\"url\\\", \\\"web\\\"), \\\"Web\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"network\\\", \\\"segment\\\", \\\"network security groups\\\", \\\"subnet\\\", \\\"application gateway\\\", \\\"security groups\\\", \\\"IP forwarding\\\", \\\"port\\\", \\\"ports\\\", \\\"networks\\\"), \\\"Networking\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"backup\\\",\\\"denial\\\", \\\"DDoS\\\", \\\"load\\\", \\\"scale\\\", \\\"front\\\", \\\"traffic manager\\\", \\\"pool\\\", \\\"disaster\\\", \\\"region\\\", \\\"redundant\\\", \\\"geo\\\"), \\\"Resiliency\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"rest\\\", \\\"transit\\\", \\\"data\\\", \\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\"), \\\"Data Protection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"private\\\", \\\"vpn\\\", \\\"automation\\\", \\\"playbook\\\", \\\"logic\\\", \\\"notification\\\", \\\"authorized\\\", \\\"safe\\\", \\\"network gateway\\\", \\\"express\\\", \\\"VPC\\\"), \\\"Enterprise\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"recover\\\", \\\"log\\\", \\\"configured\\\", \\\"configuration\\\", \\\"identity\\\", \\\"privilege\\\", \\\"admin\\\", \\\"authentication\\\", \\\"JIT\\\", \\\"just\\\", \\\"password\\\", \\\"time\\\", \\\"sync\\\", \\\"vulnerability\\\", \\\"Vulnerabilities\\\", \\\"updates\\\", \\\"update\\\", \\\"upgrade\\\", \\\"audit\\\", \\\"account\\\", \\\"guest\\\", \\\"shared\\\", \\\"access\\\", \\\"machines\\\", \\\"rights\\\", \\\"VM\\\", \\\"key\\\", \\\"keys\\\", \\\"IAM\\\", \\\"EC2\\\", \\\"GuardDuty\\\", \\\"logs\\\", \\\"CloudTrail\\\", \\\"MFA\\\", \\\"External accounts\\\", \\\"accounts\\\", \\\"config\\\", \\\"credentials\\\", \\\"privileged\\\", \\\"owner\\\", \\\"owners\\\", \\\"login\\\", \\\"logon\\\", \\\"virtual machine\\\", \\\"container\\\", \\\"containers\\\", \\\"Kubernetes\\\"), \\\"Universal Security Capabilities\\\", \\\"Other\\\")))))))))))\\r\\n| where ControlFamily in ({ControlFamily})\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by AssessedResourceId\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| project AssessedResourceId, Total, PassedControls, Passed, Failed\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Recommendations by Asset\",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"AssessedResourceId\",\"formatter\":13,\"formatOptions\":{\"linkTarget\":\"Resource\",\"showIcon\":true}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityRecommendation\\r\\n| where RecommendationDisplayName <> \\\"\\\"\\r\\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\\\"email\\\"), \\\"Email\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"apps\\\", \\\"teams\\\", \\\"meeting\\\", \\\"call\\\"), \\\"Unified Communications & Collaboration\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"dns\\\", \\\"domain\\\"), \\\"DNS\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"endpoint protection\\\", \\\"malware\\\", \\\"file\\\", \\\"files\\\",\\\"IaaSAntimalware\\\"), \\\"Files\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"Security Center\\\",\\\"defender\\\", \\\"adaptive\\\", \\\"HoneyTokens\\\", \\\"honey\\\", \\\"deception\\\", \\\"intrusion\\\", \\\"incident\\\", \\\"incidents\\\"), \\\"Intrusion Detection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"firewall\\\", \\\"watcher\\\", \\\"proxy\\\", \\\"certificate\\\", \\\"url\\\", \\\"web\\\"), \\\"Web\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"network\\\", \\\"segment\\\", \\\"network security groups\\\", \\\"subnet\\\", \\\"application gateway\\\", \\\"security groups\\\", \\\"IP forwarding\\\", \\\"port\\\", \\\"ports\\\", \\\"networks\\\"), \\\"Networking\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"backup\\\",\\\"denial\\\", \\\"DDoS\\\", \\\"load\\\", \\\"scale\\\", \\\"front\\\", \\\"traffic manager\\\", \\\"pool\\\", \\\"disaster\\\", \\\"region\\\", \\\"redundant\\\", \\\"geo\\\"), \\\"Resiliency\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"rest\\\", \\\"transit\\\", \\\"data\\\", \\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\"), \\\"Data Protection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"private\\\", \\\"vpn\\\", \\\"automation\\\", \\\"playbook\\\", \\\"logic\\\", \\\"notification\\\", \\\"authorized\\\", \\\"safe\\\", \\\"network gateway\\\", \\\"express\\\", \\\"VPC\\\"), \\\"Enterprise\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"recover\\\", \\\"log\\\", \\\"configured\\\", \\\"configuration\\\", \\\"identity\\\", \\\"privilege\\\", \\\"admin\\\", \\\"authentication\\\", \\\"JIT\\\", \\\"just\\\", \\\"password\\\", \\\"time\\\", \\\"sync\\\", \\\"vulnerability\\\", \\\"Vulnerabilities\\\", \\\"updates\\\", \\\"update\\\", \\\"upgrade\\\", \\\"audit\\\", \\\"account\\\", \\\"guest\\\", \\\"shared\\\", \\\"access\\\", \\\"machines\\\", \\\"rights\\\", \\\"VM\\\", \\\"key\\\", \\\"keys\\\", \\\"IAM\\\", \\\"EC2\\\", \\\"GuardDuty\\\", \\\"logs\\\", \\\"CloudTrail\\\", \\\"MFA\\\", \\\"External accounts\\\", \\\"accounts\\\", \\\"config\\\", \\\"credentials\\\", \\\"privileged\\\", \\\"owner\\\", \\\"owners\\\", \\\"login\\\", \\\"logon\\\", \\\"virtual machine\\\", \\\"container\\\", \\\"containers\\\", \\\"Kubernetes\\\"), \\\"Universal Security Capabilities\\\", \\\"Other\\\")))))))))))\\r\\n| where ControlFamily in ({ControlFamily})\\r\\n| where RecommendationState == \\\"Unhealthy\\\"\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by ControlFamily\\r\\n| render timechart\",\"size\":0,\"showAnalytics\":true,\"title\":\"Recommendations over Time\",\"noDataMessage\":\"No Current Zero Trust(TIC 3.0) Recommendations in this Area. Confirm the CMMC Level 3 Assessment is Enabled in Microsoft Defender for Cloud: Regulatory Compliance Blade.\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"greenRed\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityRecommendation\\r\\n| where RecommendationDisplayName <> \\\"\\\"\\r\\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\\\"email\\\"), \\\"Email\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"apps\\\", \\\"teams\\\", \\\"meeting\\\", \\\"call\\\"), \\\"Unified Communications & Collaboration\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"dns\\\", \\\"domain\\\"), \\\"DNS\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"endpoint protection\\\", \\\"malware\\\", \\\"file\\\", \\\"files\\\",\\\"IaaSAntimalware\\\"), \\\"Files\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"Security Center\\\",\\\"defender\\\", \\\"adaptive\\\", \\\"HoneyTokens\\\", \\\"honey\\\", \\\"deception\\\", \\\"intrusion\\\", \\\"incident\\\", \\\"incidents\\\"), \\\"Intrusion Detection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"firewall\\\", \\\"watcher\\\", \\\"proxy\\\", \\\"certificate\\\", \\\"url\\\", \\\"web\\\"), \\\"Web\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"network\\\", \\\"segment\\\", \\\"network security groups\\\", \\\"subnet\\\", \\\"application gateway\\\", \\\"security groups\\\", \\\"IP forwarding\\\", \\\"port\\\", \\\"ports\\\", \\\"networks\\\"), \\\"Networking\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"backup\\\",\\\"denial\\\", \\\"DDoS\\\", \\\"load\\\", \\\"scale\\\", \\\"front\\\", \\\"traffic manager\\\", \\\"pool\\\", \\\"disaster\\\", \\\"region\\\", \\\"redundant\\\", \\\"geo\\\"), \\\"Resiliency\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"rest\\\", \\\"transit\\\", \\\"data\\\", \\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\"), \\\"Data Protection\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"private\\\", \\\"vpn\\\", \\\"automation\\\", \\\"playbook\\\", \\\"logic\\\", \\\"notification\\\", \\\"authorized\\\", \\\"safe\\\", \\\"network gateway\\\", \\\"express\\\", \\\"VPC\\\"), \\\"Enterprise\\\",\\r\\niff(RecommendationDisplayName has_any(\\\"recover\\\", \\\"log\\\", \\\"configured\\\", \\\"configuration\\\", \\\"identity\\\", \\\"privilege\\\", \\\"admin\\\", \\\"authentication\\\", \\\"JIT\\\", \\\"just\\\", \\\"password\\\", \\\"time\\\", \\\"sync\\\", \\\"vulnerability\\\", \\\"Vulnerabilities\\\", \\\"updates\\\", \\\"update\\\", \\\"upgrade\\\", \\\"audit\\\", \\\"account\\\", \\\"guest\\\", \\\"shared\\\", \\\"access\\\", \\\"machines\\\", \\\"rights\\\", \\\"VM\\\", \\\"key\\\", \\\"keys\\\", \\\"IAM\\\", \\\"EC2\\\", \\\"GuardDuty\\\", \\\"logs\\\", \\\"CloudTrail\\\", \\\"MFA\\\", \\\"External accounts\\\", \\\"accounts\\\", \\\"config\\\", \\\"credentials\\\", \\\"privileged\\\", \\\"owner\\\", \\\"owners\\\", \\\"login\\\", \\\"logon\\\", \\\"virtual machine\\\", \\\"container\\\", \\\"containers\\\", \\\"Kubernetes\\\"), \\\"Universal Security Capabilities\\\", \\\"Other\\\")))))))))))\\r\\n| where ControlFamily in ({ControlFamily})\\r\\n| where RecommendationState == \\\"Unhealthy\\\"\\r\\n| parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *\\r\\n| project ResourceID=AssessedResourceId, RecommendationName=RecommendationDisplayName, ControlFamily, Severity=RecommendationSeverity, CurrentState=RecommendationState, RecommendationLink, DiscoveredTimeUTC, assessmentKey\\r\\n| extend Rank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, 0)))\\r\\n| sort by Rank desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Recommendation Details\",\"noDataMessage\":\"No Current Zero Trust (TIC 3.0) Recommendations in this Area. Confirm the CMMC Level 3 Assessment is Enabled in Microsoft Defender for Cloud: Regulatory Compliance Blade.\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ResourceID\",\"formatter\":13,\"formatOptions\":{\"linkTarget\":\"Resource\",\"showIcon\":true}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"linkIsContextBlade\":false,\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Rank\",\"formatter\":5},{\"columnMatch\":\"RecommendationSeverity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}}],\"rowLimit\":2500,\"filter\":true}},\"name\":\"query - 6\"}]},\"conditionalVisibility\":{\"parameterName\":\"isAssessmentVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"group - 1\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Controls Crosswalk](https://docs.microsoft.com/security/zero-trust/integrate/sentinel-solution)\\r\\n---\\r\\nControls crosswalk provides a mapping of Zero Trust (TIC 3.0) controls across additional compliance frameworks. This provides free-text search capabilities mapping Zero Trust pillars, TIC 3.0 controls, Microsoft offering overlays, and the NIST Cybersecurity Framework.\"},\"customWidth\":\"40\",\"name\":\"Controls Mapping\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let Crosswalk = datatable([\\\"Control Name\\\"]: string, [\\\"Zero Trust Pillars\\\"]: string, [\\\"TIC 3.0 Control Family\\\"]: string, [\\\"NIST Cybersecurity Framework\\\"]: string, [\\\"Microsoft Offerings\\\"]: string) [\\r\\n\\\"Backup & Recovery\\\", \\\"Data, Infrastructure\\\", \\\"Universal Security Capabilities\\\", \\\"ID.BE, PR.IP, PR.DS, RS.MI, RC.RP\\\", \\\"Backup Vaults, Recovery Services Vaults, Microsoft Defender for Cloud\\\",\\r\\n\\\"Central Log Management with Analysis\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, PR.PT, DE.AE, RS.AN\\\", \\\"Microsoft Defender for Cloud, Azure Monitor, Azure Lighthouse\\\",\\r\\n\\\"Configuration Management\\\", \\\"Endpoints, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.BE, PR.DS, PR.IP, PR.MA\\\", \\\"Automation Accounts, Azure Active Directory, Microsoft Defender for Cloud\\\",\\r\\n\\\"Incident Response Plan & Incident Handling\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.GV, ID.RA, PR.IP, DE.DP, DE.AE, RS.RP, RS.CO, RS.AN, RS.MI\\\", \\\"Microsoft Sentinel\\\",\\r\\n\\\"Inventory\\\", \\\"Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, PR.AC, PR.DS, PR.IP\\\", \\\"Azure Resource Graph Explorer, Azure Active Directory, Microsoft Defender for Cloud, Microsoft 365 Defender\\\",\\r\\n\\\"Least Privilege\\\", \\\"Identities\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, PR.AC, PR.IP, PR.PT, DE.CM\\\", \\\"Azure Active Directory, Microsoft Sentinel, Microsoft Defender for Cloud\\\",\\r\\n\\\"Secure Administration\\\", \\\"Identities\\\", \\\"Universal Security Capabilities\\\", \\\"PR.MA\\\", \\\"Azure Active Directory, Privileged Identity Management, Microsoft Defender for Cloud\\\",\\r\\n\\\"Strong Authentication\\\", \\\"Identities\\\", \\\"Universal Security Capabilities\\\", \\\"PR.AC\\\", \\\"Azure Active Directory, Microsoft Defender for Cloud, Microsoft Sentinel, Key Vault\\\",\\r\\n\\\"Time Synchronization\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"PR.IP\\\", \\\"Azure Portal, Virtual Machines, Microsoft Defender for Cloud\\\",\\r\\n\\\"Vulnerability Management\\\", \\\"Endpoints, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.RA, PR.IP, DE.AE, DE.CM, DE.DP\\\", \\\"Microsoft Defender for Cloud, Microsoft 365 Defender\\\",\\r\\n\\\"Patch Management\\\", \\\"Endpoints, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, PR.IP, PR.MA\\\", \\\"Automation Accounts, Microsoft Defender for Cloud\\\",\\r\\n\\\"Auditing & Accounting\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.SC, PR.AC, PR.PT\\\", \\\"Azure Active Directory, Microsoft Defender for Cloud, Microsoft Sentinel\\\",\\r\\n\\\"Resilience\\\", \\\"Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.BE, PR.PT\\\", \\\"DDoS Protection Plans, Availability Sets, Load Balancing, Virtual Machine Scale Sets\\\",\\r\\n\\\"Enterprise Threat Intelligence\\\", \\\"Visibility & Analytics\\\", \\\"Universal Security Capabilities\\\", \\\"ID.RA, DE.AE, DE.CM, DE.DP\\\", \\\"Microsoft Sentinel, Microsoft Defender Security Intelligence Portal, MSTICpy\\\",\\r\\n\\\"Situational Awareness\\\", \\\"Visibility & Analytics\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, ID.RA, PR.DS, PR.IP, DE.AE, DE.CM, DE.DP, RS.CO\\\", \\\"Microsoft Sentinel\\\",\\r\\n\\\"Dynamic Threat Discovery\\\", \\\"Visibility & Analytics\\\", \\\"Universal Security Capabilities\\\", \\\"ID.RA, DE.AE, DE.CM, DE.DP\\\", \\\"Microsoft Sentinel, Microsoft Defender for Cloud\\\",\\r\\n\\\"Policy Enforcement Parity\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"PR.DS, PR.IP, PR.MA\\\", \\\"Azure Policy, Microsoft Defender for Cloud\\\",\\r\\n\\\"Effective Use of Shared Services\\\", \\\"Data, Apps\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, ID.GV, ID.RM, ID.SC, PR.AT, RS.CO\\\", \\\"Azure Lighthouse, Customer Lockbox, Azure Active Directory\\\",\\r\\n\\\"Integrated Desktop, Mobile, & Remote Policies\\\", \\\"Identities, Endpoints, Data, Apps, Infrastructure, Network\\\", \\\"Universal Security Capabilities\\\", \\\"ID.AM, PR.AC, PR.DS, PR.IP, PR.MA\\\", \\\"Azure Active Directory, Microsoft Endpoint Manager\\\",\\r\\n\\\"Anti-Malware\\\", \\\"Endpoints, Apps, Infrastructure, Network\\\", \\\"Files\\\", \\\"PR.DS, PR.PT, DE.CM, DE.DP, RS.MI\\\", \\\"Microsoft Sentinel, Microsoft Defender for Cloud, Microsoft Defender for Identity, Microsoft 365 Defender, Microsoft Defender for Cloud Apps\\\",\\r\\n\\\"Content Disarm & Reconstruction\\\", \\\"Data, Apps\\\", \\\"Files\\\", \\\"PR.PT, DE.CM, DE.DP\\\", \\\"Microsoft 365 Defender, Microsoft Endpoint Manager Admin Center, Microsoft Sentinel\\\",\\r\\n\\\"Detonation Chamber\\\", \\\"Endpoints, Apps, Infrastructure, Network\\\", \\\"Files\\\", \\\"DE.CM, DE.DP, RS.AN, RS.MI\\\", \\\"Microsoft 365 Defender, Microsoft Endpoint Manager, Microsoft Sentinel\\\",\\r\\n\\\"Data Loss Prevention\\\", \\\"Data\\\", \\\"Files\\\", \\\"PR.DS\\\", \\\"Azure Information Protection, Microsoft Sentinel, Office 365 Security & Compliance Center\\\",\\r\\n\\\"Anti-Phishing Protections\\\", \\\"Identity, Endpoints, Data\\\", \\\"Email\\\", \\\"PR.AT, PR.PT, DE.CM\\\", \\\"Microsoft 365 Defender\\\",\\r\\n\\\"Anti-SPAM Protections\\\", \\\"Identity, Endpoints, Data\\\", \\\"Email\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft 365 Defender\\\",\\r\\n\\\"Authenticated Received Chain\\\", \\\"Authenticated Received Chain\\\", \\\"Email\\\", \\\"PR.AC\\\", \\\"Microsoft 365 Defender, Microsoft 365 Admin Center\\\",\\r\\n\\\"Data Loss Prevention\\\", \\\"Data\\\", \\\"Email\\\", \\\"PR.DS\\\", \\\"Azure Information Protection, Microsoft 365 Defender\\\",\\r\\n\\\"DMARC for Incoming Email\\\", \\\"Identities, Data\\\", \\\"Email\\\", \\\"PR.PT, PR.IP\\\", \\\"Microsoft 365 Defender, Microsoft 365 Admin Center\\\",\\r\\n\\\"DMARC for Outgoing Email\\\", \\\"Identities, Data\\\", \\\"Email\\\", \\\"PR.PT, PR.IP\\\", \\\"Microsoft 365 Defender, Microsoft 365 Admin Center\\\",\\r\\n\\\"Encryption for Email Transmission\\\", \\\"Data\\\", \\\"Email\\\", \\\"PR.PT, PR.DS\\\", \\\"Microsoft 365 Admin Center, Microsoft 365 Defender, Microsoft Defender for Cloud\\\",\\r\\n\\\"Malicious URL Protections\\\", \\\"Network\\\", \\\"Email\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft 365 Defender, Microsoft Sentinel\\\",\\r\\n\\\"URL Click-Through Protection\\\", \\\"Network\\\", \\\"Email\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft 365 Defender, Microsoft Sentinel\\\",\\r\\n\\\"Break & Inspect\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT, DE.CM\\\", \\\"Firewall Policies, Network Watcher\\\",\\r\\n\\\"Active Content Mitigation\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT, DE.CM\\\", \\\"Web Application Firewall Policies, Microsoft 365 Defender, Microsoft Defender for Cloud\\\",\\r\\n\\\"Certificate Denylisting\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft Defender for Cloud, Firewall Policies, Key Vault\\\",\\r\\n\\\"Content Filtering\\\", \\\"Endpoints, Network\\\", \\\"Web\\\", \\\"PR.PT, DE.CM, DE.DP\\\", \\\"Firewalls, Firewall Policies, Microsoft 365 Defender\\\",\\r\\n\\\"Authenticated Proxy\\\", \\\"Identities, Network\\\", \\\"Web\\\", \\\"PR.AC\\\", \\\"Azure Active Directory, Microsoft Defender for Cloud Apps\\\",\\r\\n\\\"Data Loss Prevention\\\", \\\"Data\\\", \\\"Web\\\", \\\"PR.DS\\\", \\\"Microsoft Sentinel, Microsoft Defender for Cloud, Microsoft Defender for Identity Portal, Microsoft 365 Defender, Microsoft Defender for Cloud Apps, Office 365 Security & Compliance Center, Azure Information Protection\\\",\\r\\n\\\"DNS-over-HTTPS Filtering\\\", \\\"Endpoints, Network\\\", \\\"Web\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft Defender for Cloud, Azure Firewall, Microsoft 365 Defender\\\",\\r\\n\\\"RFC Compliance Enforcement\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT\\\", \\\"Web Application Firewall, Azure Firewall\\\",\\r\\n\\\"Domain Category Filtering\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.AC, PR.IP\\\", \\\"Azure Firewall\\\",\\r\\n\\\"Domain Reputation Filter\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT\\\", \\\"Azure Firewall, Microsoft Sentinel\\\",\\r\\n\\\"Bandwidth Control\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.PT\\\", \\\"Azure Firewall\\\",\\r\\n\\\"Malicious Content Filtering\\\", \\\"Network\\\", \\\"Web\\\", \\\"PR.DS, PR.PT, PR.CM\\\", \\\"Microsoft Defender for Cloud, Microsoft Sentinel, Azure Firewall, Web Application Firewall\\\",\\r\\n\\\"Access Control\\\", \\\"Identities, Network\\\", \\\"Web\\\", \\\"PR.AC\\\", \\\"Microsoft Defender for Cloud, Privileged Identity Management\\\",\\r\\n\\\"Access Control\\\", \\\"Infrastructure, Network\\\", \\\"Networking\\\", \\\"PR.AC, PR.IP, DE.CM\\\", \\\"Microsoft Defender for Cloud, Network Security Groups, Azure Firewall, Web Application Firewall, Virtual Network Gateways, ExpressRoute Circuits\\\",\\r\\n\\\"IP Denylisting\\\", \\\"Infrastructure, Network\\\", \\\"Networking\\\", \\\"PR.PT, DE.CM\\\", \\\"Microsoft Sentinel, Azure Firewall\\\",\\r\\n\\\"Host Containment\\\", \\\"Endpoints, Infrastructure, Network\\\", \\\"Networking\\\", \\\"PR.AC, PR.IP, PR.PT\\\", \\\"Microsoft Sentinel, Microsoft Defender for Cloud, Microsoft 365 Defender\\\",\\r\\n\\\"Network Segmentation\\\", \\\"Infrastructure, Network\\\", \\\"Networking\\\", \\\"PR.AC\\\", \\\"Virtual Networks, Microsoft Defender for Cloud\\\",\\r\\n\\\"Microsegmentation\\\", \\\"Infrastructure, Network\\\", \\\"Networking\\\", \\\"PR.AC, PR.DS, PR.IP, PR.PT\\\", \\\"Application Security Groups, Network Security Groups, Microsoft Defender for Cloud\\\",\\r\\n\\\"DDoS Protections\\\", \\\"Data, Apps, Infrastructure, Network\\\", \\\"Resiliency\\\", \\\"PR.PT\\\", \\\"DDoS Protection Plans, Microsoft Sentinel\\\",\\r\\n\\\"Elastic Expansion\\\", \\\"Infrastructure\\\", \\\"Resiliency\\\", \\\"ID.AM, PR.DS\\\", \\\"Virtual Machine Scale Sets, Azure SQL, Load Balancer, Traffic Manager Profiles, Microsoft Defender for Cloud\\\",\\r\\n\\\"Regional Delivery\\\", \\\"Infrastructure\\\", \\\"Resiliency\\\", \\\"ID.AM, PR.AC, PR.DS\\\", \\\"Availability Sets, Azure Active Directory, Microsoft Defender for Cloud\\\",\\r\\n\\\"DNS Sinkholing\\\", \\\"Network\\\", \\\"DNS\\\", \\\"PR.PT\\\", \\\"DNS Zones, Azure Firewall, Microsoft Defender for Cloud, Microsoft Sentinel\\\",\\r\\n\\\"DNSSEC for Agency Clients\\\", \\\"Network\\\", \\\"DNS\\\", \\\"PR.PT\\\", \\\"DNS Zones, Azure Firewall, Microsoft Defender for Cloud, Microsoft Sentinel\\\",\\r\\n\\\"DNSSEC for Agency Domains\\\", \\\"Network\\\", \\\"DNS\\\", \\\"PR.PT\\\", \\\"DNS Zones, Microsoft Defender for Cloud, Microsoft 365 Defender\\\",\\r\\n\\\"Endpoint Detection & Response\\\", \\\"Endpoints, Infrastructure\\\", \\\"Intrusion Detection\\\", \\\"DE.AE, DE.CM, RS.AN\\\", \\\"Microsoft 365 Defender, Microsoft Defender for Cloud\\\",\\r\\n\\\"Intrusion Protection Systems (IPS)\\\", \\\"Network\\\", \\\"Intrusion Detection\\\", \\\"DE.AE, DE.CM, DE.DP, RS.AN\\\", \\\"Azure Firewall, Microsoft Sentinel\\\",\\r\\n\\\"Adaptive Access Control\\\", \\\"Identities\\\", \\\"Intrusion Detection\\\", \\\"PR.AC, DE.CM\\\", \\\"Microsoft Defender for Cloud, Azure Active Directory\\\",\\r\\n\\\"Deception Platforms\\\", \\\"Identities\\\", \\\"Intrusion Detection\\\", \\\"PR.PT, DE.AE, RS.AN\\\", \\\"Microsoft Sentinel, Microsoft Defender for Identity\\\",\\r\\n\\\"Certificate Transparency Log Monitoring\\\", \\\"Infrastructure, Apps\\\", \\\"Intrusion Detection\\\", \\\"DE.CM\\\", \\\"Key Vault, Microsoft Sentinel, Microsoft Defender for Cloud\\\",\\r\\n\\\"Security Orchestration, Automation, & Response (SOAR)\\\", \\\"Visibility & Automation\\\", \\\"Enterprise\\\", \\\"DE.AE, DE.CM, DE.DP, RS.CO, RS.AN, RC.RP\\\", \\\"Microsoft Sentinel\\\",\\r\\n\\\"Shadow IT Detection\\\", \\\"Endpoints, Infrastructure, Apps\\\", \\\"Enterprise\\\", \\\"PR.IP, PR.MA, DE.CM\\\", \\\"Microsoft Defender for Cloud Apps, Microsoft Defender for Cloud, Microsoft Sentinel, Microsoft 365 Defender, Microsoft Defender for IoT\\\",\\r\\n\\\"Virtual Private Network (VPN)\\\", \\\"Network\\\", \\\"Enterprise\\\", \\\"PR.AC, PR.DS, PR.IP, PR.MA, PR.PT\\\", \\\"Virtual Network Gateways, Microsoft Defender for Cloud\\\",\\r\\n\\\"UCC Identity Verification\\\", \\\"Identities\\\", \\\"Unified Communications & Collaboration\\\", \\\"PR.AC\\\", \\\"Microsoft 365 Admin Center, Azure Active Directory\\\",\\r\\n\\\"UCC Encrypted Communication\\\", \\\"Data\\\", \\\"Unified Communications & Collaboration\\\", \\\"PR.PT, PR.DS\\\", \\\"Microsoft 365 Admin Center\\\",\\r\\n\\\"UCC Connection Termination\\\", \\\"Identities\\\", \\\"Unified Communications & Collaboration\\\", \\\"PR.AC, PR.IP, PR.AT\\\", \\\"Microsoft Teams\\\",\\r\\n\\\"UCC Data Loss Prevention\\\", \\\"Data\\\", \\\"Unified Communications & Collaboration\\\", \\\"PR.DS\\\", \\\"Microsoft 365 Defender, Microsoft 365 Compliance Center\\\",\\r\\n\\\"Access Control\\\", \\\"Identities\\\", \\\"Data Protection\\\", \\\"PR.AC, PR.IP, DE.CM\\\", \\\"Azure Active Directory\\\",\\r\\n\\\"Protections for Data at Rest\\\", \\\"Data\\\", \\\"Data Protection\\\", \\\"PR.DS\\\", \\\"Microsoft Defender for Cloud, Key Vault\\\",\\r\\n\\\"Protections for Data in Transit\\\", \\\"Data\\\", \\\"Data Protection\\\", \\\"PR.DS\\\", \\\"Microsoft Defender for Cloud, Key Vault\\\",\\r\\n\\\"Data Loss Prevention\\\", \\\"Data\\\", \\\"Data Protection\\\", \\\"PR.DS\\\", \\\"Azure Information Protection, Microsoft Sentinel, Office 365 Security & Compliance Center\\\",\\r\\n\\\"Data Access & Use Telemetry\\\", \\\"Data\\\", \\\"Data Protection\\\", \\\"ID.AM, PR.AC, PR.DS, PR.PT, DE.AE, DE.CM\\\", \\\"Azure Active Directory, Azure Information Protection, Microsoft 365 Compliance Center\\\"\\r\\n];\\r\\nCrosswalk\\r\\n| project [\\\"Control Name\\\"],[\\\"Zero Trust Pillars\\\"],[\\\"TIC 3.0 Control Family\\\"],[\\\"NIST Cybersecurity Framework\\\"],[\\\"Microsoft Offerings\\\"]\",\"size\":0,\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Control Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"TIC 3.0 Control Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Execution\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Microsoft Offerings\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"name\":\"query - 1\"}]},\"conditionalVisibility\":{\"parameterName\":\"isControlsCrosswalkVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Controls Mapping\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Recommended Data Connectors](https://docs.microsoft.com/azure/sentinel/connect-data-sources)\\r\\n---\\r\\n\\r\\nAfter onboarding Microsoft Sentinel into your workspace, connect data sources to start ingesting your data into Microsoft Sentinel. Microsoft Sentinel comes with many connectors for Microsoft products, available out of the box and providing real-time integration. For example, service-to-service connectors include Microsoft 365 Defender connectors and Microsoft 365 sources, such as Office 365, Microsoft Entra ID, Microsoft Defender for Identity, and Microsoft Defender for Cloud Apps. Check out these references if you're new to Microsoft Sentinel.\"},\"customWidth\":\"40\",\"name\":\"NS Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"10\",\"name\":\"text - 2\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"b1cd1f8a-e807-4deb-93f4-7812e5ed014a\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Data Connectors >>\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorsBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\"}}]},\"customWidth\":\"20\",\"name\":\"EL0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://docs.microsoft.com/azure/sentinel/best-practices\",\"linkTarget\":\"Url\",\"linkLabel\":\"Best Practices\",\"style\":\"link\"},{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/azure-sentinel-all-in-one-accelerator/ba-p/1807933\",\"linkTarget\":\"Url\",\"linkLabel\":\"Microsoft Sentinel All-In-One Accelerator\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://docs.microsoft.com/learn/browse/?wt.mc_id=resilience_skilling_webpage_gdc&terms=sentinel\",\"linkTarget\":\"Url\",\"linkLabel\":\"Microsoft Sentinel Training\",\"style\":\"link\"}]},\"customWidth\":\"40\",\"name\":\"links - 29\"}],\"exportParameters\":true},\"name\":\"group - 7\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"## Foundational Connectors\",\"style\":\"info\"},\"name\":\"text - 13\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Activity Connector](https://docs.microsoft.com/azure/azure-monitor/essentials/activity-log)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"909d0019-23cb-43ad-8285-9f1dca1cd1be\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AzureActivity\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureActivity\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"58cc25ab-a9af-4516-99e1-fa22e0637a76\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureActivity\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"33\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Entra ID Connector](https://docs.microsoft.com/azure/sentinel/connect-azure-active-directory)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"23ba579d-c894-43be-9fe1-d1b04bc34d7a\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"SignInLogs\",\"label\":\"Status\",\"type\":1,\"query\":\"SigninLogs\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Active Directory\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"7c97e893-29f3-4d4c-a379-f220bb82518c\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureActiveDirectory\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Active Directory (AAD) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Office 365 Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#microsoft-office-365)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"68bd12c8-e473-45d1-8bbc-2dd9f326ea69\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"OfficeActivity\",\"label\":\"Status\",\"type\":1,\"query\":\"OfficeActivity\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"6a86eb8d-5487-4aad-ae7b-b526e68a249f\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"Office365\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Office 365 Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Defender for Cloud Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#microsoft-defender-for-cloud)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"1673e4cf-354f-4a42-bed2-2374be47779e\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"MDfC\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityAlert\\r\\n| where ProviderName == \\\"Azure Security Center\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"56600b70-0e55-433a-be86-b7c561bced8b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureSecurityCenter\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Microsoft Defender for Cloud Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Network Security Groups (NSG) Connector](https://docs.microsoft.com/azure/virtual-network/virtual-network-nsg-manage-log)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"b17ce357-e8d5-4c7c-a4f0-765598462a1c\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"NSG\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"NetworkSecurityGroupEvent\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"935bb630-1fce-4021-b7b4-c010b9e05973\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureNSG\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Network Security Groups (NSG) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Windows Security Events (AMA) Connector](https://docs.microsoft.com/azure/sentinel/connect-azure-windows-microsoft-services?tabs=SA%2CAMA#windows-agent-based-connections)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"d9af27d9-8c90-4c85-a57f-f329257d9956\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AMA\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityEvent\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d002eb41-c632-429b-8504-846b69314620\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"WindowsSecurityEvents\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Windows Security Events (AMA) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Security Events via Legacy Agent Connector](https://docs.microsoft.com/azure/sentinel/connect-azure-windows-microsoft-services?tabs=SA%2CLAA#windows-agent-based-connections)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"b2737fbc-c0e2-4584-9fba-ee7d057d7db0\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"SecurityEvent\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityEvent\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"9a8b0649-e79b-4a30-be25-4a5486f302ee\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"SecurityEvents\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Security Events via Legacy Agent Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [DNS Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#windows-dns-server-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"8b7ac3ca-b46c-43e0-ae8c-e2b5189596bc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"DNS\",\"label\":\"Status\",\"type\":1,\"query\":\"DnsEvents\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"2d8731f5-c225-4a39-9914-6391b2c89ecb\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"DNS\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"DNS Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Storage Accounts Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-storage-account)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"4f291c03-8d98-47b6-ba82-1282322bb7a5\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"StorageLogs\",\"label\":\"Status\",\"type\":1,\"query\":\"StorageBlobLogs\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"6d9cd26b-3fcd-4556-b2eb-3dcb711c4de4\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureStorageAccount\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Storage Logs Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Common Event Format (CEF) Connector](https://docs.microsoft.com/azure/sentinel/connect-common-event-format)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"4fcf795c-75b8-4010-bd24-1d66511ff6e8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"CommonSecurityLog\",\"label\":\"Status\",\"type\":1,\"query\":\"CommonSecurityLog\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"452e02e1-b0c4-4b9b-8a54-bc9295db22b9\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"CEF\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Common Event Format (CEF) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Syslog Connector](https://docs.microsoft.com/azure/sentinel/connect-syslog)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"fa63a08f-dd08-4e11-bcb6-c075a6d6c15c\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Syslog\",\"label\":\"Status\",\"type\":1,\"query\":\"Syslog\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"021644a3-bd51-4b09-8117-017a89c71d58\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"Syslog\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Syslog Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Amazon Web Services (AWS) Connector](https://docs.microsoft.com/azure/sentinel/connect-aws?tabs=s3)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"18ed59f0-c497-44b1-94b7-8700051cf189\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AWS\",\"label\":\"Status\",\"type\":1,\"query\":\"AWSCloudTrail\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"393c465e-4398-428b-8da2-87ac07d8a987\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AWS\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Amazon Web Services (AWS) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Amazon Web Services (AWS) S3 Connector](https://docs.microsoft.com/azure/sentinel/connect-aws?tabs=s3)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AWSS3\",\"label\":\"Status\",\"type\":1,\"query\":\"AWSVPCFlow\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AwsS3\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Amazon Web Services (AWS) S3 Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Google Cloud Platform IAM Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#google-workspace-g-suite-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"GCP\",\"label\":\"Status\",\"type\":1,\"query\":\"GCP_IAM_CL\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"1f2ba663-dd7a-49b6-87ba-0b8adf6d2d34\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Amazon Web Services (AWS) S3 Connector - Copy\",\"styleSettings\":{\"showBorder\":true}}],\"exportParameters\":true},\"name\":\"group - 5\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"## Basic Connectors\",\"style\":\"info\"},\"name\":\"text - 13\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft 365 Defender Connector](https://docs.microsoft.com/azure/sentinel/connect-microsoft-365-defender?tabs=MDE)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"M365Defender\",\"label\":\"Status\",\"type\":1,\"query\":\"AlertEvidence\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"MicrosoftThreatProtection\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Microsoft 365 Defender Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Defender for Endpoint Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#microsoft-defender-for-endpoint)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"MDE\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityAlert\\r\\n| where ProviderName == \\\"MDATP\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"MicrosoftDefenderAdvancedThreatProtection\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Microsoft 365 Defender Connector - Copy\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Firewall Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-firewall)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AzureFirewall\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics\\r\\n| where ResourceType == \\\"AZUREFIREWALLS\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureFirewall\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Firewall Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Windows Firewall Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#windows-firewall)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"WindowsFirewall\",\"label\":\"Status\",\"type\":1,\"query\":\"WindowsFirewall\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"WindowsFirewall\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Windows Firewall Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Web Application Firewall Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-web-application-firewall-waf)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AzureWAF\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics | where ResourceType in (\\\"APPLICATIONGATEWAYS\\\", \\\"FRONTDOORS\\\", \\\"CDNWEBAPPLICATIONFIREWALLPOLICIES\\\", \\\"PROFILES\\\")\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"WAF\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Web Application Firewall Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure SQL Databases Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-sql-databases)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"8b7ac3ca-b46c-43e0-ae8c-e2b5189596bc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"SQL\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics | where Category contains \\\"SQL\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"2d8731f5-c225-4a39-9914-6391b2c89ecb\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureSql\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"SQL Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Key Vault Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-key-vault)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AzureKeyVault\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics | where ResourceProvider == \\\"MICROSOFT.KEYVAULT\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureKeyVault\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Key Vault Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure DDoS Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-ddos-protection)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"DDoS\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics | where ResourceType == \\\"PUBLICIPADDRESSES\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"Azure Activity Connector - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy - Copy\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"DDOS\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure DDoS Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [VMware ESXi Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#vmware-esxi-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"VMwareESXi\",\"label\":\"Status\",\"type\":1,\"query\":\"VMwareESXi\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"VMwareESXi\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"VMware ESXi Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Defender for Cloud: Continuous Export](https://docs.microsoft.com/azure/defender-for-cloud/continuous-export?tabs=azure-portal)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"SecurityRecommendation\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityRecommendation\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 3\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Feature\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"SecurityMenuBlade\",\"extensionName\":\"Microsoft_Azure_Security\"}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Continuous Export Connector\",\"styleSettings\":{\"showBorder\":true}}],\"exportParameters\":true},\"name\":\"group - 6\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"## Intermediate Connectors\",\"style\":\"info\"},\"name\":\"text - 13\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Information Protection Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-information-protection-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"InformationProtectionLogs_CL\",\"type\":1,\"query\":\"InformationProtectionLogs_CL\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"label\":\"Status\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureInformationProtection\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Information Protection Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Dynamics 365 Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#dynamics-365)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Dynamics365Activity\",\"label\":\"Status\",\"type\":1,\"query\":\"Dynamics365Activity\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"Dynamics365\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Dynamics 365 Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Azure Kubernetes Service (AKS) Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-kubernetes-service-aks)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AKS\",\"label\":\"Status\",\"type\":1,\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"kube-audit\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureKubernetes\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Kubernetes Service (AKS) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Qualys Vulnerability Management Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#qualys-vulnerability-management-vm-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Qualys\",\"label\":\"Status\",\"type\":1,\"query\":\"QualysHostDetection_CL\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"QualysVulnerabilityManagement\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Qualys Vulnerability Management Connector\",\"styleSettings\":{\"showBorder\":true}}],\"exportParameters\":true},\"name\":\"group - 6\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"## Advanced Connectors\",\"style\":\"info\"},\"name\":\"text - 13\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Entity Behavior (UEBA)](https://docs.microsoft.com/azure/sentinel/enable-entity-behavior-analytics)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"BehaviorAnalytics\",\"label\":\"Status\",\"type\":1,\"query\":\"BehaviorAnalytics\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Feature\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"EntitySearchBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\"}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Entity Behavior (UEBA) Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Entra ID Protection Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#azure-active-directory-identity-protection)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"AADIP\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityAlert | where ProductName == \\\"Azure Active Directory Identity Protection\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"AzureActiveDirectoryIdentityProtection\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Azure Active Directory Identity Protection Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Threat Intelligence TAXII Connector](https://docs.microsoft.com/azure/sentinel/connect-threat-intelligence-taxii)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"TAXII\",\"label\":\"Status\",\"type\":1,\"query\":\"ThreatIntelligenceIndicator | where SourceSystem !in (\\\"SecurityGraph\\\", \\\"Azure Sentinel\\\", \\\"Microsoft Sentinel\\\") \\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"ThreatIntelligenceTaxii\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Threat Intelligence TAXII Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Threat Intelligence Platform Connector](https://docs.microsoft.com/azure/sentinel/connect-threat-intelligence-tip)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ThreatIntelligence\",\"label\":\"Status\",\"type\":1,\"query\":\"ThreatIntelligenceIndicator | where SourceSystem in (\\\"SecurityGraph\\\", \\\"Azure Sentinel\\\", \\\"Microsoft Sentinel\\\") \\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"ThreatIntelligence\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Threat Intelligence Platform Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Defender for IoT Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#microsoft-defender-for-iot)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"MD4IOT\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityAlert | where ProductName == \\\"Azure Security Center for IoT\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"IoT\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Microsoft Defender for IoT Connector\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"loadType\":\"always\",\"items\":[{\"type\":1,\"content\":{\"json\":\"### [Microsoft Purview: Insider Risk Management Connector](https://docs.microsoft.com/azure/sentinel/data-connectors-reference#microsoft-purview-insider-risk-management-irm-preview)\"},\"customWidth\":\"33\",\"name\":\"text - 2\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"crossComponentResources\":[\"{Workspace}\"],\"parameters\":[{\"id\":\"548cdd92-87c3-4e69-be08-52ecca0f76a8\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"IRM\",\"label\":\"Status\",\"type\":1,\"query\":\"SecurityAlert\\r\\n| where ProductName == \\\"Microsoft 365 Insider Risk Management\\\"\\r\\n| limit 1\\r\\n| summarize count()\\r\\n| extend Results = iff(count_ ==0, \\\"❌ Not Connected\\\", \\\"✅ Connected\\\")\\r\\n| project Results\",\"crossComponentResources\":[\"{Workspace}\"],\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"33\",\"name\":\"parameters - 1\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"d9b9144c-69bc-4eb2-a747-a9e0d206780b\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Enable Connector\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"DataConnectorBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"dataConnectorId\",\"source\":\"static\",\"value\":\"OfficeIRM\"}]}}]},\"customWidth\":\"33\",\"name\":\"EL0\"}],\"exportParameters\":true},\"name\":\"Microsoft Purview: Insider Risk Management Connector\",\"styleSettings\":{\"showBorder\":true}}]},\"name\":\"group - 6\"}],\"exportParameters\":true},\"conditionalVisibility\":{\"parameterName\":\"isDCVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Recommended Data Connectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Recommended Content](https://docs.microsoft.com/azure/sentinel/sentinel-solutions-catalog)\\r\\n---\\r\\n\\r\\nThe following content packages provide utility for regulated industries use cases.\"},\"name\":\"NS Guide\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://docs.microsoft.com/azure/sentinel/sentinel-solutions\",\"linkTarget\":\"Url\",\"linkLabel\":\"About Microsoft Sentinel Content & Solutions\",\"style\":\"link\"},{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://docs.microsoft.com/azure/sentinel/sentinel-solutions-catalog\",\"linkTarget\":\"Url\",\"linkLabel\":\"Content Hub Catalog\",\"style\":\"link\"}]},\"name\":\"links - 29\"}]},\"customWidth\":\"40\",\"name\":\"group - 4\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"10\",\"name\":\"text - 2\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"76c7831e-386d-4289-8145-486f52cba8ec\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Content Hub >>\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"ContentHub.ReactView\",\"extensionName\":\"Microsoft_Azure_SentinelUS\"}}]},\"customWidth\":\"40\",\"name\":\"EL0\"}]},\"name\":\"group - 7\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Zero Trust (TIC 3.0) Solution](https://docs.microsoft.com/security/zero-trust/integrate/sentinel-solution)\\r\\n\\r\\n---\\r\\nThe Microsoft Sentinel Zero Trust (TIC 3.0) Solution provides a mechanism for viewing log queries aligned to Zero Trust and Trusted Internet Connections models across the Microsoft and partner ecosystem. This solution enables governance and compliance teams to design, build, monitor, and respond to Zero Trust (TIC 3.0) requirements across cloud, multi-cloud, 1st/3rd party workloads. The solution includes the new Zero Trust (TIC 3.0) Workbook, (1) Analytics Rule, and (3) Playbooks. While only Microsoft Sentinel and Microsoft Defender for Cloud are required to get started, the solution is enhanced with numerous Microsoft offerings.<br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FZeroTrust(TIC3.0)%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FZeroTrust(TIC3.0)%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/next-evolution-of-the-microsoft-sentinel-zero-trust-tic-3-0/ba-p/3278097\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/CxLzTRPuw-4\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/ZeroTrust(TIC3.0)\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"\\r\\n\\r\\n\"},\"customWidth\":\"80\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"Zero Trust Solution\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [NIST SP 800-53 Solution](https://docs.microsoft.com/security/zero-trust/integrate/sentinel-solution)\\r\\n\\r\\n---\\r\\nThis solution is designed to augment staffing through automation, machine learning, query/alerting generation, and visualizations. This workbook leverages Azure Policy, Azure Resource Graph, and Azure Log Analytics to align with NIST SP 800-53 control requirements. This offering telemetry from 25+ Microsoft Security products (1P/3P/Multi-Cloud/Hybrid/On-Premises). Each NIST SP 800-53 control includes a Control Card detailing an overview of requirements, primary/secondary controls, deep-links to referenced product pages/portals, recommendations, implementation guides, compliance cross-walks and tooling telemetry for building situational awareness of cloud workloads.<br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FNISTSP80053%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FNISTSP80053%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/announcing-the-microsoft-sentinel-nist-sp-800-53-solution/ba-p/3381485\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/ju9hxtYnj7s\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/NISTSP80053\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"90\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 10\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Cybersecurity Maturity Model Certification (CMMC) 2.0](https://www.acq.osd.mil/cmmc/index.html)\\r\\n---\\r\\n\\r\\nThis solution enables Compliance Teams, Architects, SecOps Analysts, and Consultants to gain situational awareness for cloud workload security posture. This solution is designed to augment staffing through automation, visibility, assessment, monitoring and remediation. This solution includes (1) Workbook for build/design/assessment/reporting, (2) Analytics rules for monitoring and (3) Playbooks for response/remediation. CMMC 2.0 is the next iteration of the Department’s CMMC cybersecurity model. It streamlines requirements to three levels of cybersecurity – Foundational, Advanced and Expert – and aligns the requirements at each level with well-known and widely accepted NIST cybersecurity standards.<br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FCybersecurityMaturityModelCertification(CMMC)2.0%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FCybersecurityMaturityModelCertification(CMMC)2.0%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/announcing-the-microsoft-sentinel-cybersecurity-maturity-model/ba-p/3295095\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/-_a5HxJgriE\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/CybersecurityMaturityModelCertification(CMMC)2.0\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"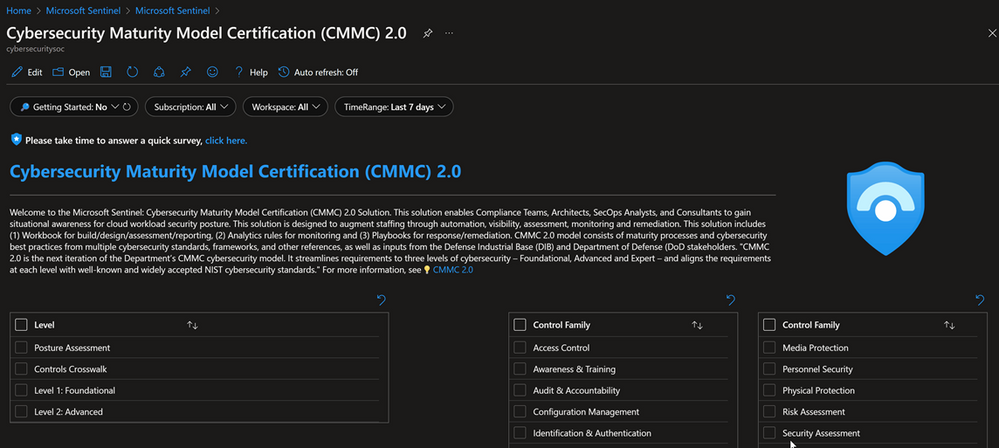\"},\"customWidth\":\"75\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 9\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Azure Security Benchmark v3](https://docs.microsoft.com/security/benchmark/azure/)\\r\\n---\\r\\n\\r\\nEnables Cloud Architects, Security Engineers, and Governance Risk Compliance Professionals to gain situational awareness for cloud security posture and hardening. Benchmark recommendations provide a starting point for selecting specific security configuration settings and facilitate risk reduction. The Azure Security Benchmark includes a collection of high-impact security recommendations for improving posture. This workbook provides visibility and situational awareness for security capabilities delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user and some panels may require additional configurations for operation. <br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Security-Center%2Fmain%2FWorkbooks%2FAzure%20Security%20Benchmark%20v3%2FarmTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Security-Center%2Fmain%2FWorkbooks%2FAzure%20Security%20Benchmark%20v3%2FarmTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/azure-security-benchmark-v3-workbook/ba-p/3257673\",\"linkTarget\":\"Url\",\"linkLabel\":\"Announce Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/v57gWjvcY4o\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"cc5f4830-f090-4f5e-afb2-47adba6be532\",\"cellValue\":\"https://youtu.be/qVJjwOipHDA\",\"linkTarget\":\"Url\",\"linkLabel\":\"ASC in the Field\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Microsoft-Defender-for-Cloud/tree/main/Workbooks/Azure%20Security%20Benchmark%20v3\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"86\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 9\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Microsoft Insider Risk Management Solution](https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/announcing-the-microsoft-sentinel-microsoft-insider-risk/ba-p/2955786)\\r\\n---\\r\\n\\r\\nInsider risk management helps minimize internal risks by enabling you to detect, investigate, and act on malicious and inadvertent activities in your organization. Insider risk policies allow you to define the types of risks to identify and detect in your organization, including acting on cases and escalating cases to Microsoft Advanced eDiscovery. Risk analysts in your organization can quickly take appropriate actions to make sure users are compliant with your organization's compliance standards. Insider risks come in various forms including both witting (intentional) and unwitting (unintentional). This workbook provides an automated visualization of Insider risk behavior cross walked to Microsoft security offerings. <br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FMicrosoftPurviewInsiderRiskManagement%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FMicrosoftPurviewInsiderRiskManagement%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/announcing-the-microsoft-sentinel-microsoft-insider-risk/ba-p/2955786\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/MicrosoftPurviewInsiderRiskManagement\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"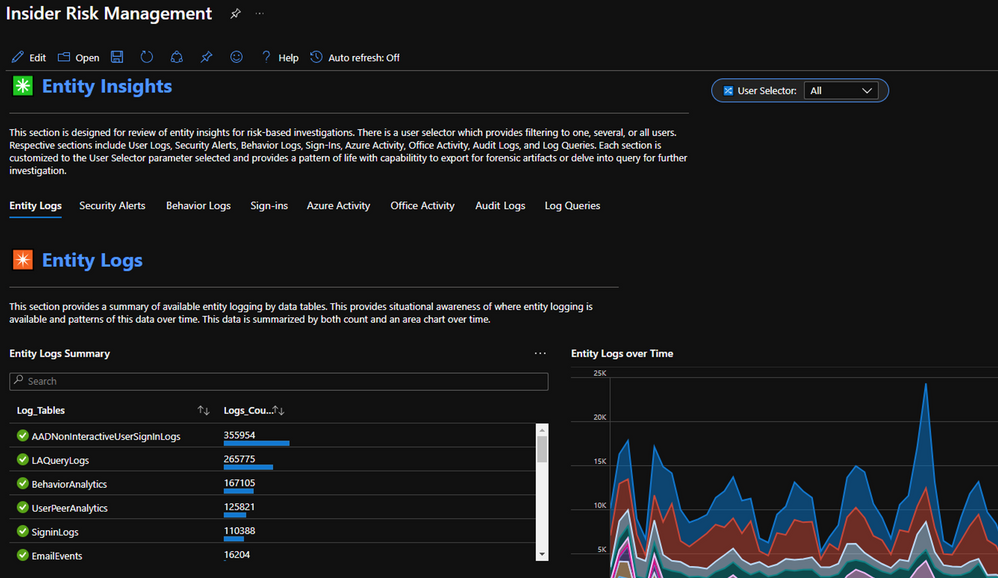\"},\"customWidth\":\"75\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 9\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [IT/OT Threat Monitoring Solution](https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/defending-critical-infrastructure-with-the-microsoft-sentinel-it/ba-p/3061184)\\r\\n---\\r\\n\\r\\nThis solution provides the foundation for building a SOC for monitoring IoT/ OT and includes (1) workbook for visibility/reporting, (14) analytics rules for monitoring, and (4) playbooks for response. The workbook leverages Microsoft Sentinel telemetry to create visualization to understand, analyze, and respond to IoT/OT threats. Understanding alerts over time provides unprecedented insights into security posture and where teams need to focus to harden against threats. Deep links directly to Microsoft Defender for IoT alerts empower analysts to focus on remediating threats rather than pivoting between tools. <br>\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FIoTOTThreatMonitoringwithDefenderforIoT%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FIoTOTThreatMonitoringwithDefenderforIoT%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/defending-critical-infrastructure-with-the-microsoft-sentinel-it/ba-p/3061184\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"8f7dce97-a41c-42b3-b62f-a21fbf5a1420\",\"cellValue\":\"https://youtu.be/hZS2aplJoy8\",\"linkTarget\":\"Url\",\"linkLabel\":\"YouTube Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/blob/master/Solutions/IoTOTThreatMonitoringwithDefenderforIoT/readme.md\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"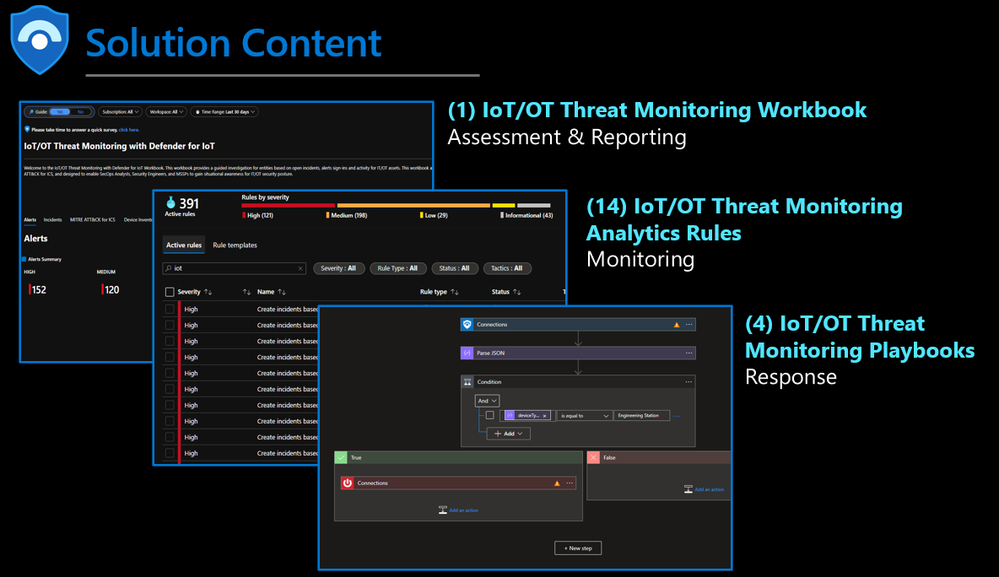\"},\"customWidth\":\"75\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 9\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Maturity Model for Event Log Management Solution](https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/modernize-log-management-with-the-maturity-model-for-event-log/ba-p/3072842)\\r\\n---\\r\\n\\r\\nThis solution is designed to enable Cloud Architects, Security Engineers, and Governance Risk Compliance Professionals to increase visibility before, during, and after a cybersecurity incident.\\\"Executive Order 14028, Improving the Nation's Cybersecurity, directs decisive action to improve the Federal Government’s investigative and remediation capabilities. This memorandum was developed in accordance with and addresses the requirements in section 8 of the Executive Order for logging, log retention, and log management, with a focus on ensuring centralized access and visibility for the highest-level enterprise security operations center (SOC) of each agency.\\\" For more information, see 💡[OMB's M-21-31 Memorandum](https://www.whitehouse.gov/wp-content/uploads/2021/08/M-21-31-Improving-the-Federal-Governments-Investigative-and-Remediation-Capabilities-Related-to-Cybersecurity-Incidents.pdf)\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FMaturityModelForEventLogManagementM2131%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FMaturityModelForEventLogManagementM2131%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/modernize-log-management-with-the-maturity-model-for-event-log/ba-p/3072842\",\"linkTarget\":\"Url\",\"linkLabel\":\"Solution Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/quV_80ts__k\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/MaturityModelForEventLogManagementM2131\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"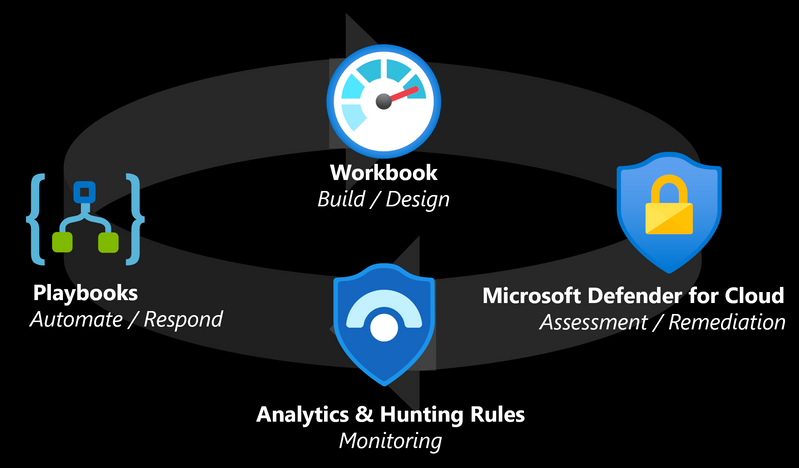\"},\"customWidth\":\"75\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 8\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Threat Analysis & Response Solution](https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/ThreatAnalysis%26Response)\\r\\n---\\r\\n\\r\\nThis solution enables SecOps Analysts, Threat Intelligence Professional, and Threat Hunters to gain situational awareness for threats in cloud environment. The Solution includes (2) Workbooks designed to enable threat hunting programs. Threat analysis provides an understanding of where the attacker is in the cycle which often drives both a historic lens of where the threat may have progressed, but also predictive analytics on the threat’s objectives. This approach is adversarial as understanding of the threat’s attack cycle drives defense actions in a red versus blue model. The Threat Analysis & Response Solution augments the customer burden of building threat hunting programs.\\r\\n\\r\\n---\\r\\n<a href=\\\"https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FThreatAnalysis%26Response%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazurebutton\\\"/></a>\\r\\n<a href=\\\"https://portal.azure.us/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2FAzure%2FAzure-Sentinel%2Fmaster%2FSolutions%2FThreatAnalysis%26Response%2FPackage%2FmainTemplate.json\\\" target=\\\"_blank\\\"><img src=\\\"https://aka.ms/deploytoazuregovbutton\\\"/></a>\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/tree/master/Solutions/ThreatAnalysis%26Response\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"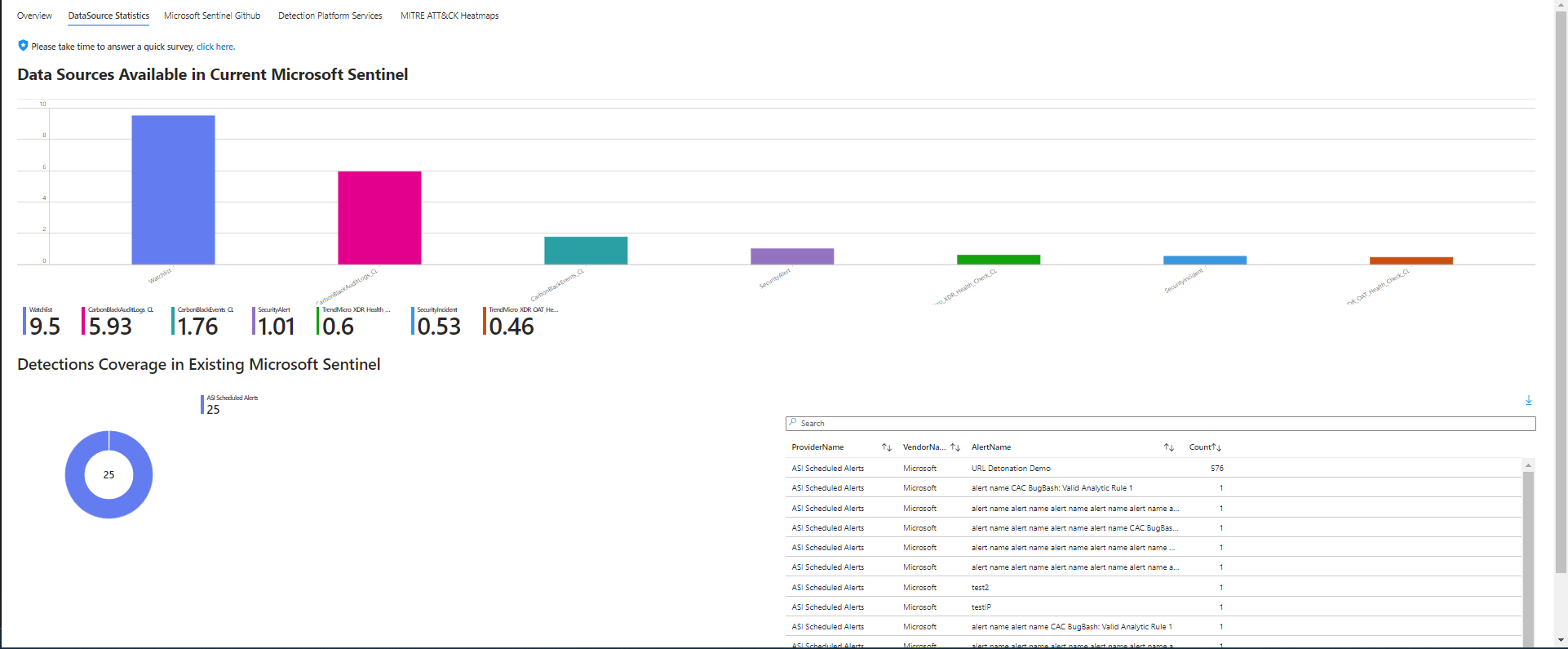\"},\"customWidth\":\" 100\",\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"group - 9\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Threat Intelligence Workbook](https://docs.microsoft.com/security/benchmark/azure/)\\r\\n---\\r\\n\\r\\nThe most commonly used form of CTI is threat indicators, also known as Indicators of Compromise or IoCs. Threat indicators are data that associate observed artifacts such as URLs, file hashes, or IP addresses with known threat activity such as phishing, botnets, or malware. This form of threat intelligence is often called tactical threat intelligence because it can be applied to security products and automation in large scale to detect potential threats to an organization and protect against them. In Microsoft Sentinel, you can use threat indicators to help detect malicious activity observed in your environment and provide context to security investigators to help inform response decisions. <br>\\r\\n\\r\\n---\"},\"name\":\"text - 0\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"nav\",\"links\":[{\"id\":\"1bad541e-219a-4277-9510-876b0e8cad51\",\"cellValue\":\"https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/what-s-new-azure-sentinel-threat-intelligence-workbook/ba-p/2858265\",\"linkTarget\":\"Url\",\"linkLabel\":\"Workbook Blog\",\"style\":\"link\"},{\"id\":\"b9a6293e-1c7b-4ec2-ad2a-d72b5ee01722\",\"cellValue\":\"https://youtu.be/SjEG7iVVBbI\",\"linkTarget\":\"Url\",\"linkLabel\":\"Video Demo\",\"style\":\"link\"},{\"id\":\"7e8ff8aa-f632-4a4d-90cf-a71da0dc6b31\",\"cellValue\":\"https://github.com/Azure/Azure-Sentinel/blob/master/Workbooks/ThreatIntelligence.json\",\"linkTarget\":\"Url\",\"linkLabel\":\"GitHub Repo\",\"style\":\"link\"}]},\"name\":\"links - 29\"},{\"type\":1,\"content\":{\"json\":\"\"},\"name\":\"text - 2\"}]},\"customWidth\":\"50\",\"name\":\"Zero Trust Solution - Copy - Copy - Copy\"}]},\"conditionalVisibility\":{\"parameterName\":\"isGCVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Recommended Content\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Azure Lighthouse](https://azure.microsoft.com/services/azure-lighthouse/)\\r\\n---\\r\\nAzure Lighthouse helps service providers simplify customer engagement and onboarding experiences, while managing delegated resources at scale with agility and precision. Authorized users, groups, and service principals can work directly in the context of a customer subscription without having an account in that customer's Microsoft Entra ID tenant or being a co-owner of the customer's tenant. The mechanism used to support this access is called Azure delegated resource management. \"},\"customWidth\":\"40\",\"name\":\"text - 5\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"10\",\"name\":\"text - 2\"},{\"type\":11,\"content\":{\"version\":\"LinkItem/1.0\",\"style\":\"list\",\"links\":[{\"id\":\"1cf637a7-121d-4722-b511-b0c460625e31\",\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Access Azure Lighthouse\",\"style\":\"secondary\",\"bladeOpenContext\":{\"bladeName\":\"LighthouseBlade\",\"extensionName\":\"Microsoft_Azure_CustomerHub\"}}]},\"customWidth\":\"50\",\"name\":\"links - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"managedservicesresources\\r\\n| where type == \\\"microsoft.managedservices/registrationassignments\\\"\\r\\n| where properties.provisioningState == \\\"Succeeded\\\"\\r\\n| extend ManageeTenantName = properties.registrationDefinition.properties.manageeTenantName\\r\\n| extend ManagedByTenantName = properties.registrationDefinition.properties.managedByTenantName\\r\\n| extend ManagedByTenantId = properties.registrationDefinition.properties.managedByTenantId\\r\\n| extend ManageeTenantId = tostring(properties.registrationDefinition.properties.manageeTenantId)\\r\\n| extend PermanentAccess = properties.registrationDefinition.properties.authorizations\\r\\n| extend JITAccess = properties.registrationDefinition.properties.eligibleAuthorizations\\r\\n| extend AddedDate = properties.registrationDefinition.systemData.createdAt\\r\\n| extend CreatedBy = systemData.createdBy\\r\\n| project ManageeTenantName, ManageeTenantId, ManagedByTenantName, ManagedByTenantId, AddedDate, CreatedBy\",\"size\":1,\"showAnalytics\":true,\"title\":\"Azure Lighthouse Delegations\",\"noDataMessage\":\"No Azure Lighthouse Delegations/Customers Detected\",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Subscription}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ManageeTenantName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Download\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ManageeTenantId\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true}},{\"columnMatch\":\"ManagedByTenantName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Upload\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ManagedByTenantId\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true}},{\"columnMatch\":\"AddedDate\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Clock\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"CreatedBy\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"PermanentAccess\",\"formatter\":1},{\"columnMatch\":\"JITAccess\",\"formatter\":1}],\"filter\":true}},\"name\":\"query - 21 - Copy\"}]},\"conditionalVisibility\":{\"parameterName\":\"isAzureLighthouseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"group - 21\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Universal Security Capabilities](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\n---\\r\\nUniversal capabilities are enterprise-level capabilities that outline guiding principles for TIC use cases. Universal capabilities are selected to be broadly applicable; the same list of capabilities apply to every use case. However, certain use cases may provide unique guidance on specific capabilities where necessary. Agencies have significant discretion regarding how to meet the individual security capability requirements and address their particular needs. Agencies are free to determine the level of rigor necessary for applying universal capabilities based on federal guidelines and risk tolerance. While it is expected that agencies may often be able to employ a common solution to fulfill multiple roles or serve multiple purposes, the selection of an appropriate set of solutions is left to each agency.\"},\"customWidth\":\"40\",\"name\":\"text - 105\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 105\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Backup and Recovery\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Backup\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Central Log Management with Analysis\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Central\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Configuration Management\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Configuration\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Incident Response Plan and Incident Handling\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Incident\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Inventory\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Inventory\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Least Privilege\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Least\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Secure Administration\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Secure\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Strong Authentication\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Strong\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Time Synchronization\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Time\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Vulnerability Management\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Vulnerability\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"2adea420-fa6e-4073-8a78-1aeada742e2c\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isBackupVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Backup\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isCentralVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Central\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"04e846bb-6bca-4981-863b-76f4e8ea5667\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isConfigurationVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Configuration\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"7498b0e3-e4dd-44c9-868d-d5baef71ba17\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIncidentVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Incident\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"7010b3e9-27e4-40b0-8d4b-fdd05f940d92\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isInventoryVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Inventory\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"c9285caf-952f-458a-ac89-3fdb2871151f\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isLeastVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Least\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"356132e1-e5e8-4fd4-8a56-95bd91bc9470\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isSecureVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Secure\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"8d5eb913-9e91-4f61-930b-26335aaad1cf\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isStrongVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Strong\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"232d115f-5a82-4a70-aa2d-12fb00993230\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isTimeVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Time\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"da3d19be-b7ed-4449-83ea-c9a001f54315\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isVulnerabilityVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Vulnerability\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"5e32dd42-2359-4ed6-a5e9-303873a50442\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors - Copy\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Patch Management\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Patch\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Auditing and Accounting\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Auditing\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Resilience\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Resilience\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Enterprise Threat Intelligence\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Enterprise\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Situational Awareness\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Situational\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Dynamic Threat Discovery\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Dynamic\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Policy Enforcement Parity\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Policy\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Effective Use of Shared Services\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Effective\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Integrated Desktop, Mobile, and Remote Policies\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Integrated\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8 - Copy\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"2dc83cdc-c5e9-4ea7-a986-0294effc2e8e\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isPatchVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Patch\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAuditingVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Auditing\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"be23e804-75f9-486d-8478-8af0ed3b0b6d\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isResilienceVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Resilience\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"41d2063e-0f2b-47dc-9c7c-2cdcdafb80ec\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEnterpriseVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Enterprise\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b2752897-08eb-4f06-adae-d7e0b278acef\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isSituationalVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Situational\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"0531d0e3-8eb9-4c7f-bedb-d29aed642c1b\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDynamicVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Dynamic\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"ee837eb2-25bb-4a51-bdd7-5d58640fb780\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isPolicyVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Policy\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"683d9906-de4f-400f-b92e-8f6d5f346db7\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEffectiveVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Effective\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"6e5570df-f9fa-4ce9-b79c-74068100c9c6\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIntegratedVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Integrated\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"e7db70e6-eafa-4cb0-ac08-58719fad7c33\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors - Copy - Copy\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Backup and Recovery](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nKeeping copies of configuration and data, as needed, to allow for the quick restoration of service in the event of malicious incidents, system failures, or corruption.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> 🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure Backup](https://azure.microsoft.com/services/backup/)\\r\\n\\r\\n### Implementation \\r\\n💡 [What is the Azure Backup Service?](https://docs.microsoft.com/azure/backup/backup-overview)<br>\\r\\n💡 [Review Your Security Recommendations](https://docs.microsoft.com/azure/security-center/security-center-recommendations)<br>\\r\\n💡 [Configure Recovery Service Vaults](https://docs.microsoft.com/azure/backup/backup-azure-recovery-services-vault-overview)<br>\\r\\n💡 [Apply Azure security baselines to machines](https://docs.microsoft.com/azure/defender-for-cloud/apply-security-baseline)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Backup Vaults](https://portal.azure.com/#blade/Microsoft_Azure_Policy/PolicyMenuBlade/Overview) <br>\\r\\n🔀 [Recovery Services Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.RecoveryServices%2Fvaults) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.BE, PR.IP, PR.DS, RS.MI, RC.RP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 0\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Text Group\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"back\\\" or RecommendationDisplayName contains \\\"recover\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"recover\\\" or type contains \\\"restore\\\" or type contains \\\"back\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Backup & Recovery Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"back\\\" or Description contains \\\"restore\\\" or Description contains \\\"recover\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"back\\\" or Description contains \\\"restore\\\" or Description contains \\\"recover\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"back\\\" or Description contains \\\"restore\\\" or Description contains \\\"recover\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isBackupVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Backup and Recovery\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Central Log Management & Analysis](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCollecting, storing, and analyzing telemetry, where the collection and storage are designed to facilitate data fusion and the security analysis aids in discovery and response to malicious activity.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> 🔷 [Usage](https://docs.microsoft.com/azure/azure-monitor/reference/tables/usage) 🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure Monitor](https://azure.microsoft.com/services/monitor/)\\r\\n\\r\\n### Microsoft Reference \\r\\n💡 [Create Diagnostic Settings to Send Platform Logs and Metrics to Different Destinations](https://docs.microsoft.com/azure/azure-monitor/platform/diagnostic-settings)<br>\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n💡 [What is Azure Lighthouse?](https://docs.microsoft.com/azure/lighthouse/overview)<br>\\r\\n\\t\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n🔀 [Azure Monitor](https://portal.azure.com/#blade/Microsoft_Azure_Monitoring/AzureMonitoringBrowseBlade/overview) <br>\\r\\n🔀 [Azure Lighthouse](https://portal.azure.com/#blade/Microsoft_Azure_CustomerHub/LighthouseBlade)<br> \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.PT, DE.AE, RS.AN](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"log\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type == \\\"microsoft.operationalinsights/workspaces\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Logging Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"union withsource=_TableName *\\r\\n| summarize Entries = count(), Size = sum(_BilledSize), last_log = datetime_diff(\\\"second\\\",now(), max(TimeGenerated)), estimate = sumif(_BilledSize, _IsBillable==true) by _TableName, _IsBillable\\r\\n| project ['Table Name'] = _TableName, ['Table Size'] = Size, ['Table Entries'] = Entries,\\r\\n ['Size per Entry'] = 1.0 * Size / Entries, ['IsBillable'] = _IsBillable\\r\\n| order by ['Table Size'] desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Log Table Management\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Table Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"uninitialized\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Table Size\",\"formatter\":8,\"formatOptions\":{\"palette\":\"purple\"},\"numberFormat\":{\"unit\":2,\"options\":{\"style\":\"decimal\",\"useGrouping\":false}}},{\"columnMatch\":\"Table Entries\",\"formatter\":8,\"formatOptions\":{\"palette\":\"turquoise\"},\"numberFormat\":{\"unit\":2,\"options\":{\"style\":\"decimal\",\"useGrouping\":false}}},{\"columnMatch\":\"Size per Entry\",\"formatter\":8,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":2,\"options\":{\"style\":\"decimal\",\"useGrouping\":false}}},{\"columnMatch\":\"IsBillable\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"True\",\"representation\":\"2\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"False\",\"representation\":\"success\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Important\",\"text\":\"{0}{1}\"}]}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_thresholds_IsBillable_4\",\"sortOrder\":2}]},\"sortBy\":[{\"itemKey\":\"$gen_thresholds_IsBillable_4\",\"sortOrder\":2}],\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"DataType\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"maximumSignificantDigits\":3,\"maximumFractionDigits\":2}}},\"showBorder\":false}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 5\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isCentralVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Central Log Management with Analysis\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Configuration Management](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nImplementing a formal plan for documenting, managing changes to the environment, and monitoring for deviations, preferably automated.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) 🔷 [SecurityBaseline](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n🔷 [AuditLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/auditlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Enable Change Tracking and Inventory From an Automation Account](https://docs.microsoft.com/azure/automation/change-tracking/enable-from-automation-account)<br>\\r\\n💡 [Ensure Your Endpoints Are Configured Properly](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/configure-machines)<br>\\r\\n💡 [Secure Score in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/secure-score-security-controls)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Automation Accounts](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Automation%2FAutomationAccounts) <br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.BE, PR.DS, PR.IP, PR.MA](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"config\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"config\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"config\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"config\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AuditLogs\\r\\n| summarize count() by OperationName\\r\\n| where OperationName <> \\\"Other\\\"\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Audit Logs\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 4\"}]},\"conditionalVisibility\":{\"parameterName\":\"isConfigurationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Configuration Management\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Incident Response Plan and Incident Handling](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDocumenting and implementing a set of instructions, procedures, or technical capabilities to sense and detect, respond to, limit consequences of malicious cyber attacks, and restore the integrity of the network and associated systems.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Quickstart: Tutorial: Investigate incidents with Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/tutorial-investigate-cases)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.GV, ID.RA, PR.IP, DE.DP, DE.AE, RS.RP, RS.CO, RS.AN, RS.MI](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"title\":\"Security Incidents\",\"items\":[{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\n| where Status == \\\"New\\\" or Status == \\\"Active\\\"\\n| where Severity == \\\"High\\\"\\n| summarize count()\\n\\n\\n\\n\",\"size\":4,\"title\":\"High\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Description\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"60%\"}},{\"columnMatch\":\"name\",\"formatter\":0,\"formatOptions\":{\"customColumnWidthSetting\":\"5%\"}},{\"columnMatch\":\"severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"Critical\",\"representation\":\"critical\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Major\",\"representation\":\"2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"text\":\"{0}{1}\"}],\"customColumnWidthSetting\":\"5\"}},{\"columnMatch\":\"message\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"70%\"}}]},\"tileSettings\":{\"titleContent\":{\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"min\":0,\"palette\":\"redBright\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"showBorder\":false,\"size\":\"auto\"}},\"customWidth\":\"25\",\"name\":\"query - 10\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\n| where Status == \\\"New\\\" or Status == \\\"Active\\\"\\n| where Severity == \\\"Medium\\\"\\n| summarize count()\\n\\n\\n\\n\",\"size\":4,\"title\":\"Medium \",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Description\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"60%\"}},{\"columnMatch\":\"name\",\"formatter\":0,\"formatOptions\":{\"customColumnWidthSetting\":\"5%\"}},{\"columnMatch\":\"severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"Critical\",\"representation\":\"critical\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Major\",\"representation\":\"2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"text\":\"{0}{1}\"}],\"customColumnWidthSetting\":\"5\"}},{\"columnMatch\":\"message\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"70%\"}}]},\"tileSettings\":{\"titleContent\":{\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"min\":0,\"palette\":\"orange\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"showBorder\":false,\"size\":\"auto\"}},\"customWidth\":\"25\",\"name\":\"query - 10 - Copy\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\n| where Status == \\\"New\\\" or Status == \\\"Active\\\"\\n| where Severity == \\\"Low\\\"\\n| summarize count()\\n\\n\\n\\n\",\"size\":4,\"title\":\"Low\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Description\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"60%\"}},{\"columnMatch\":\"name\",\"formatter\":0,\"formatOptions\":{\"customColumnWidthSetting\":\"5%\"}},{\"columnMatch\":\"severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"Critical\",\"representation\":\"critical\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Major\",\"representation\":\"2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"text\":\"{0}{1}\"}],\"customColumnWidthSetting\":\"5\"}},{\"columnMatch\":\"message\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"70%\"}}]},\"tileSettings\":{\"titleContent\":{\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"min\":0,\"palette\":\"yellow\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"showBorder\":false,\"size\":\"auto\"}},\"customWidth\":\"25\",\"name\":\"query - 10 - Copy - Copy\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\n| where Status == \\\"New\\\" or Status == \\\"Active\\\"\\n| where dayofyear(TimeGenerated) == dayofyear(now())\\n| summarize count()\\n\\n\\n\",\"size\":4,\"title\":\"New Today\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Description\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"60%\"}},{\"columnMatch\":\"name\",\"formatter\":0,\"formatOptions\":{\"customColumnWidthSetting\":\"5%\"}},{\"columnMatch\":\"severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"Critical\",\"representation\":\"critical\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Major\",\"representation\":\"2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"text\":\"{0}{1}\"}],\"customColumnWidthSetting\":\"5\"}},{\"columnMatch\":\"message\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"CellDetails\",\"linkIsContextBlade\":true,\"customColumnWidthSetting\":\"70%\"}}]},\"tileSettings\":{\"titleContent\":{\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"min\":0,\"palette\":\"blueDark\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"showBorder\":false,\"size\":\"auto\"}},\"customWidth\":\"25\",\"name\":\"query - 10\"}]},\"customWidth\":\"50\",\"name\":\"Incidents\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| summarize arg_max(LastModifiedTime,*) by IncidentNumber\\r\\n| where Status == \\\"Closed\\\"\\r\\n| extend TimeToRespond = (CreatedTime - FirstActivityTime)/1h \\r\\n| extend TimeToResolve = (ClosedTime - CreatedTime)/1h\\r\\n| extend AssignedAnalyst = tostring(Owner.assignedTo)\\r\\n| extend [\\\"MITRE ATT&CK Tactics\\\"] = tostring(parse_json(tostring(AdditionalData.tactics))[0])\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| project IncidentName=Title, IncidentNumber, Severity, IncidentUrl, [\\\"MITRE ATT&CK Tactics\\\"], AssignedAnalyst, Classification, ClassificationComment, ClassificationReason, Description, TimeToRespond, TimeToResolve, IncidentStartTime=CreatedTime, IncidentClosedTime=ClosedTime, IncidentBlade\\r\\n| sort by IncidentClosedTime desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Closure Reports\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"IncidentName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"TimeToRespond\",\"formatter\":0,\"numberFormat\":{\"unit\":27,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"TimeToResolve\",\"formatter\":0,\"numberFormat\":{\"unit\":27,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"name\":\"query - 9 - Copy\"}]},\"conditionalVisibility\":{\"parameterName\":\"isIncidentVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Incident Response Plan and Incident Handling\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Inventory](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDeveloping, documenting, and maintaining a current inventory of all systems, networks, and components so that only authorized endpoints are given access, and unauthorized and un-managed endpoints are found and prevented from gaining access.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure Resource Graph](https://azure.microsoft.com/features/resource-graph/)<br>\\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n🔷 [DeviceRegistryEvents](https://docs.microsoft.com/azure/azure-monitor/reference/tables/deviceregistryevents) ✳️ [Microsoft Defender for Endpoint](https://www.microsoft.com/microsoft-365/security/endpoint-defender)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Explore and Manage Your Resources With Asset Inventory](https://docs.microsoft.com/azure/security-center/asset-inventory) <br>\\r\\n💡 [View Installed Software](https://docs.microsoft.com/azure/automation/automation-tutorial-installed-software#view-installed-software)<br>\\r\\n💡 [What is Azure Resource Graph?](https://docs.microsoft.com/azure/governance/resource-graph/overview)<br> \\r\\n\\t\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Resource Graph Explorer](https://portal.azure.com/#blade/HubsExtension/ArgQueryBlade) <br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.AC, PR.DS, PR.IP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000},\"value\":\"Implemented\"},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"04JUL76\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"Asset Inventory Implemented, Plan of Action & Milestones Documented, System Security Plan (SSP) Updated\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| extend Azure_Inventory=location\\r\\n| extend M365_Inventory=strcat(\\\"https://security.microsoft.com/machines\\\")\\r\\n| project AssetID=id,AssetType=type, Azure_Inventory, M365_Inventory\\r\\n| sort by AssetType desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Asset Inventory\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Azure_Inventory\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Azure Inventory >>\",\"bladeOpenContext\":{\"bladeName\":\"InventoryBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"\",\"source\":\"static\",\"value\":\"25\"}]}}},{\"columnMatch\":\"M365_Inventory\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"M365 Inventory >>\"}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"where type contains \\\"microsoft\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| summarize count() by location\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Assets by Location\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"piechart\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"location\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Globe\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"Computer\",\"formatter\":16,\"formatOptions\":{\"showIcon\":true}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| project id,type,location,resourceGroup\\r\\n| summarize count() by type\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Asset Count by Type\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"type\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"ResourceFlat\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"Computer\",\"formatter\":16,\"formatOptions\":{\"showIcon\":true}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 8\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| summarize count() by ResourceDisplayName\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Application Inventory & Access\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"DeviceRegistryEvents \\r\\n| summarize arg_max(TimeGenerated, *) by InitiatingProcessFileName, DeviceName\\r\\n| summarize count() by InitiatingProcessFileName\\r\\n| where InitiatingProcessFileName <> \\\"\\\"\\r\\n| sort by count_ desc\\r\\n\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Software Inventory by Initiating Process\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3 - Copy\"}]},\"conditionalVisibility\":{\"parameterName\":\"isInventoryVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Inventory\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Least Privilege](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDesigning the security architecture such that each entity is granted the minimum system resources and authorizations that the entity needs to perform its function.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [IdentityInfo](https://docs.microsoft.com/azure/azure-monitor/reference/tables/identityinfo) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n🔷 [AzureActivity](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azureactivity) ✳️ [Azure Monitor]( https://azure.microsoft.com/services/monitor/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Administrator roles by admin task in Microsoft Entra ID](https://docs.microsoft.com/azure/active-directory/roles/delegate-by-task)<br>\\r\\n💡 [Overview of role-based access control in Microsoft Entra ID](https://docs.microsoft.com/azure/active-directory/roles/custom-overview)<br>\\r\\n💡 [Microsoft Entra ID Sign-In Activity](https://docs.microsoft.com/azure/active-directory/reports-monitoring/concept-all-sign-ins)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.AC, PR.IP, PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"identity\\\" or RecommendationDisplayName contains \\\"privilege\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let LastObserved = SigninLogs\\r\\n| where ResultType == 0\\r\\n| summarize arg_max(TimeGenerated, *) by UserPrincipalName\\r\\n| project UserPrincipalName, LastSignIn=TimeGenerated;\\r\\nSigninLogs\\r\\n| extend UserProfile = strcat(\\\"https://portal.azure.com/#blade/Microsoft_AAD_IAM/UserDetailsMenuBlade/Profile/userId/\\\", UserId)\\r\\n| where ResultType == 0\\r\\n| summarize count() by UserPrincipalName, UserProfile, UserId\\r\\n| join (LastObserved) on UserPrincipalName\\r\\n| project UserPrincipalName, SignInCount=count_, UserProfile, LastSignIn, UserId\\r\\n| sort by SignInCount desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Valid Accounts\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"SignInCount\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"UserProfile\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"AAD User Profile >>\",\"bladeOpenContext\":{\"bladeName\":\"UserDetailsMenuBlade\",\"extensionName\":\"Microsoft_AAD_IAM\",\"bladeParameters\":[{\"name\":\"userId\",\"source\":\"column\",\"value\":\"UserId\"}]}}},{\"columnMatch\":\"UserId\",\"formatter\":5},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}}],\"filter\":true},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"customWidth\":\"50\",\"name\":\"query - 9\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"IdentityInfo\\r\\n| extend GroupMemberships = strcat(GroupMembership)\\r\\n| extend AssignedRoles_ = strcat(AssignedRoles)\\r\\n| extend UserPrincipalName = MailAddress\\r\\n| where MailAddress <> \\\"\\\"\\r\\n| distinct UserPrincipalName, GroupMemberships, AssignedRoles_\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Assigned Roles & Group Memberships\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"User\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Activities\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 4\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isLeastVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Least Privilege\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Secure Administration](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nPerforming administrative tasks in a secure manner, using secure protocols.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [AuditLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/auditlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation\\r\\n💡 [Delegate Administration in Microsoft Entra ID](https://docs.microsoft.com/azure/active-directory/roles/concept-delegation)<br>\\r\\n💡 [Start Using Privileged Identity Management](https://docs.microsoft.com/azure/active-directory/privileged-identity-management/pim-getting-started#)<br> \\r\\n💡 [Apply Azure security baselines to machines](https://docs.microsoft.com/azure/defender-for-cloud/apply-security-baseline)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Privileged Identity Management](https://portal.azure.com/#blade/Microsoft_Azure_PIMCommon/CommonMenuBlade/quickStart) <br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.MA](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"admin\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"admin\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"admin\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"admin\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AuditLogs\\r\\n| where OperationName contains \\\"PIM\\\"\\r\\n| extend InitiatedBy = tostring(parse_json(tostring(InitiatedBy.user)).userPrincipalName)\\r\\n| distinct OperationName, Identity, AADOperationType, InitiatedBy, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Privileged Identity Management\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"OperationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Identity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"InitiatedBy\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"PersonWithFriend\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"\"}},{\"columnMatch\":\"ComplianceDomain\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_thresholds_InitiatedBy_3\",\"sortOrder\":2}]},\"sortBy\":[{\"itemKey\":\"$gen_thresholds_InitiatedBy_3\",\"sortOrder\":2}],\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"customWidth\":\"50\",\"name\":\"query - 9\"}]},\"conditionalVisibility\":{\"parameterName\":\"isSecureVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Secure Administration\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Strong Authentication](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nVerifying the identity of users, endpoints, or other entities through rigorous means (e.g. multi-factor authentication) before granting access.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Plan an Azure AD Multi-Factor Authentication Deployment](https://docs.microsoft.com/azure/active-directory/authentication/howto)<br>\\r\\n💡 [How it works: Azure AD Multi-Factor Authentication](https://docs.microsoft.com/azure/active-directory/authentication/concept-mfa-howitworks)<br>\\r\\n💡 [Remediate recommendations in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/security-center-remediate-recommendations)<br>\\r\\n💡 [SecretManagement and Accessing Linux VMs in Azure](https://techcommunity.microsoft.com/t5/itops-talk-blog/secretmanagement-and-accessing-linux-vms-in-azure/ba-p/2278735)<br>\\r\\n💡 [Eliminate Password-Based Attacks on Azure Linux VMs](https://techcommunity.microsoft.com/t5/azure-security-center/eliminate-password-based-attacks-on-azure-linux-vms/ba-p/2271139)<br>\\r\\n💡 [Quickstart: Create a Key Vault Using the Azure Portal](https://techcommunity.microsoft.com/t5/itops-talk-blog/secretmanagement-and-accessing-linux-vms-in-azure/ba-p/2278735)<br>\\r\\n\\t\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Key Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"authentication\\\" or RecommendationDisplayName contains \\\"JIT\\\" or RecommendationDisplayName contains \\\"password\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"authentication\\\" or Description contains \\\"password\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"authentication\\\" or Description contains \\\"password\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"authentication\\\" or Description contains \\\"password\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where Title contains \\\"auth\\\" or Title contains \\\"password\\\" or Title contains \\\"login\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Authentication Attacks\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isStrongVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\" Strong Authentication\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Time Synchronization](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCoordinating clocks on all systems (e.g. servers, workstations, network endpoints) to enable accurate comparison of timestamps between systems.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityBaseline](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Time Sync for Windows VMs in Azure](https://docs.microsoft.com/azure/virtual-machines/windows/time-sync)<br>\\r\\n💡 [Apply Azure security baselines to machines](https://docs.microsoft.com/azure/defender-for-cloud/apply-security-baseline)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Portal](https://portal.azure.com/) <br>\\r\\n🔀 [Virtual Machines](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Compute%2FVirtualMachines) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.IP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Time Synchronization\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"time\\\" or Description contains \\\"sync\\\" or Description contains \\\"ntp\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"time\\\" or Description contains \\\"sync\\\" or Description contains \\\"ntp\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"time\\\" or Description contains \\\"sync\\\" or Description contains \\\"ntp\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| where Description !contains \\\"runtime\\\"\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isTimeVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Time Synchronization\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Vulnerability Management](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nProactively working to discover vulnerabilities, including the use of both active and passive means of discovery, and taking action to mitigate discovered vulnerabilities.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) 🔷 [SecurityBaseline](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n💡 [Secure Score in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/secure-score-security-controls)<br>\\r\\n💡 [Microsoft Defender for Cloud's Integrated Vulnerability Assessment Solution for Azure and Hybrid Machine](https://docs.microsoft.com/azure/security-center/built-in-vulnerability-assessment)<br>\\r\\n💡 [Threat and Vulnerability Management Walk-Through](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/next-gen-threat-and-vuln-mgt)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Microsoft 365 Defender: Threat & Vulnerability Management](https://security.microsoft.com/tvm_dashboard)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.RA, PR.IP, DE.AE, DE.CM, DE.DP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"vuln\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityBaseline\\r\\n| where CceId <> \\\"\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by ResourceId, CceId\\r\\n|project CceId, RuleSeverity, Description, ResourceId\\r\\n|limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Vulnerability Management\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"CceId\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Defense Evasion\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RuleSeverity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Resource\",\"formatter\":13,\"formatOptions\":{\"linkTarget\":\"Resource\",\"showIcon\":true}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 4\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityBaseline\\r\\n| where CceId <> \\\"\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by Resource, CceId\\r\\n| summarize count() by ResourceId\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Vulnerability Count by Asset\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Resource\",\"formatter\":13,\"formatOptions\":{\"linkTarget\":\"Resource\",\"showIcon\":true}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"CceId\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Defense Evasion\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RuleSeverity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 4\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isVulnerabilityVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Vulnerability Management\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Patch Management](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nIdentifying, acquiring, installing, and verifying patches for products and systems.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Update Management Overview](https://docs.microsoft.com/azure/automation/update-management/overview)<br>\\r\\n💡 [Enable Update Management From the Azure Portal](https://docs.microsoft.com/azure/automation/update-management/enable-from-portal)<br>\\r\\n💡 [Handling Planned Maintenance Notifications Using the Azure Portal](https://docs.microsoft.com/azure/virtual-machines/maintenance-notifications-portal)<br>\\r\\n💡 [Managing Platform Updates with Maintenance Control](https://docs.microsoft.com/azure/virtual-machines/maintenance-control?toc=/azure/virtual-machines/linux/toc.json&bc=/azure/virtual-machines/linux/breadcrumb/toc.json)<br>\\r\\n💡 [Scheduling Maintenance Updates with Maintenance Control and Azure Functions](https://github.com/Azure/azure-docs-powershell-samples/tree/master/maintenance-auto-scheduler)<br>\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Automation Accounts](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Automation%2FAutomationAccounts) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br> \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.IP, PR.MA](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"update\\\" or RecommendationDisplayName contains \\\"upgrade\\\" or RecommendationDisplayName contains \\\"version\\\" or RecommendationDisplayName contains \\\"patch\\\" or RecommendationDisplayName contains \\\"java\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isPatchVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Patch Management\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Auditing and Accounting](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCapturing business records, including logs and other telemetry, and making them available for auditing and accounting as required. Design of the auditing system should take insider threat into consideration, including separation of duties violation tracking, such that insider abuse or misuse can be detected.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Usage](https://docs.microsoft.com/azure/azure-monitor/reference/tables/usage) ✳️ [Azure Monitor]( https://azure.microsoft.com/services/monitor/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Create Diagnostic Settings to Send Platform Logs and Metrics to Different Destinations](https://docs.microsoft.com/azure/azure-monitor/platform/diagnostic-settings)<br>\\r\\n💡 [Tutorial: Grant a User Access to Azure Resources Using the Azure Portal](https://docs.microsoft.com/azure/role-based-access-control/quickstart-assign-role-user-portal)<br>\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n💡 [Auditing Microsoft Sentinel Activities](https://techcommunity.microsoft.com/t5/azure-sentinel/auditing-azure-sentinel-activities/ba-p/1718328)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br> \\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br> \\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br> \\r\\n\\r\\n### NIST CSF Mapping\\r\\n[ID.SC, PR.AC, PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"audit\\\" or RecommendationDisplayName contains \\\"account\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"audit\\\" or Description contains \\\"log\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"audit\\\" or Description contains \\\"log\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"audit\\\" or Description contains \\\"log\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"Usage\\r\\n| summarize count() by DataType\\r\\n| sort by count_ desc\\r\\n| limit 100\",\"size\":0,\"showAnalytics\":true,\"title\":\"Log Events by Type\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"gridSettings\":{\"filter\":true},\"tileSettings\":{\"showBorder\":false,\"titleContent\":{\"columnMatch\":\"DataType\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"count_\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"maximumSignificantDigits\":3,\"maximumFractionDigits\":2}}},\"rowLimit\":100}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAuditingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Auditing and Accounting\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Resilience](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nEnsuring that systems, services, and protections maintain acceptable performance under adverse conditions.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) 🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure DDoS Protection]( https://azure.microsoft.com/services/ddos-protection/) <br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [DDoS Protection Plans](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FddosProtectionPlans) <br>\\r\\n🔀 [Availability Sets](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Compute%2FavailabilitySets) <br>\\r\\n🔀 [Load Balancing](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers)<br> \\r\\n🔀 [Virtual Machine Scale Sets](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Compute%2FvirtualMachineScaleSets) <br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Azure DDoS Protection Standard Overview](https://docs.microsoft.com/azure/ddos-protection/ddos-protection-overview)<br>\\r\\n💡 [Building Solutions for High Availability Using Availability Zones](https://docs.microsoft.com/azure/architecture/high-availability/building-solutions-for-high-availability)<br> \\r\\n💡 [Azure Infrastructure Availability](https://docs.microsoft.com/azure/security/fundamentals/infrastructure-availability)<br> \\r\\n💡 [What is Azure Load Balancer?](https://docs.microsoft.com/azure/load-balancer/load-balancer-overview)<br>\\r\\n💡 [What are virtual machine scale sets?](https://docs.microsoft.com/azure/virtual-machine-scale-sets/overview)<br> \\r\\n\\r\\n### NIST CSF Mapping\\r\\n[ID.BE, PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"balance\\\" or RecommendationDisplayName contains \\\"denial\\\" or RecommendationDisplayName contains \\\"recover\\\" or RecommendationDisplayName contains \\\"back\\\" or RecommendationDisplayName contains \\\"scale\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"SourceIPLocation\",\"longitude\":\"SourceIPLocation\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\"}]}}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"dos\\\"or type contains \\\"balance\\\" or type contains \\\"recover\\\" or type contains \\\"back\\\" or type contains \\\"scale\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Resilience Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"DDoSMitigationReports\\\"\\r\\n| sort by TimeGenerated desc\\r\\n| extend TopAttackVector = tostring(parse_json(AttackVectors_s)[0]) \\r\\n| extend Total_packets_ = tostring(parse_json(TrafficOverview_s).Total_packets) \\r\\n| extend Total_packets_dropped_ = todouble(parse_json(TrafficOverview_s).Total_packets_dropped)\\r\\n| extend TotalPackets =todouble(Total_packets_)\\r\\n| where TotalPackets > 0\\r\\n| where TopAttackVector <> \\\"\\\"\\r\\n| project TopAttackVector, TotalPackets, TotalPacketsDropped = Total_packets_dropped_ , ResourceId , SourceIP=IPAddress, Resource, TimeGenerated\\r\\n| sort by TotalPacketsDropped desc\\r\\n| limit 100\\r\\n\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Denial of Service Attacks Observed\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"exportedParameters\":[{\"fieldName\":\"IPAddress\",\"parameterName\":\"IPAddress\",\"parameterType\":1},{\"fieldName\":\"ResourceId\",\"parameterName\":\"ResourceId\",\"parameterType\":1,\"defaultValue\":\"ResourceId\"},{\"fieldName\":\"Resource\",\"parameterName\":\"AttackReport\",\"parameterType\":1,\"defaultValue\":\"/\"}],\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"TopAttackVector\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"TotalPackets\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"TotalPacketsDropped\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"Resource\",\"formatter\":5},{\"columnMatch\":\"Total_packets_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"Total_packets_dropped_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"IPAddress\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"}},\"subtitleContent\":{\"columnMatch\":\"TopAttackVector\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Resource\"},\"rightContent\":{\"columnMatch\":\"TimeGenerated\"},\"showBorder\":true,\"size\":\"auto\"}},\"customWidth\":\"50\",\"name\":\"query - 4\"}]},\"conditionalVisibility\":{\"parameterName\":\"isResilienceVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Resilience\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Enterprise Threat Intelligence](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nObtaining threat intelligence from private and government sources and implementing mitigation for the identified risks.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [ThreatIntelligenceIndicator](https://docs.microsoft.com/azure/azure-monitor/reference/tables/threatintelligenceindicator) 🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) 🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityalert) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/)\\r\\n\\r\\n### Implementation \\r\\n💡 [Connect Data from Threat Intelligence Providers](https://docs.microsoft.com/azure/sentinel/connect-threat-intelligence)<br>\\r\\n💡 [Microsoft Security Intelligence Portal](https://www.microsoft.com/wdsi)<br>\\r\\n💡 [Microsoft Graph Security tiIndicators API](https://docs.microsoft.com/graph/api/resources/tiindicator)<br>\\r\\n💡 [MSTIC Jupyter and Python Security Tools](https://github.com/Microsoft/msticpy)<br>\\r\\n💡 [Use Jupyter Notebook to Hunt for Security Threats](https://docs.microsoft.com/azure/sentinel/connect-threat-intelligence)<br>\\r\\n\\t\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender Security Intelligence Portal](https://microsoft.com/wdsi)<br>\\r\\n🔀 [MSTICpy](https://github.com/Microsoft/msticpy) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.RA, DE.AE, DE.CM, DE.DP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"ThreatIntelligenceIndicator\\r\\n| summarize arg_max(TimeGenerated, *) by IndicatorId\\r\\n| summarize CountOfIndicators = count() by SourceSystem\\r\\n| order by CountOfIndicators desc \\r\\n| render barchart kind=unstacked\",\"size\":0,\"showAnalytics\":true,\"title\":\"Cyber Threat Intelligence Indicator Counts\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where Description contains \\\"intel\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Threat Intelligence\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where Tactics <> \\\"\\\"\\r\\n| where Tactics <> \\\"Unknown\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by SystemAlertId\\r\\n| summarize count() by Tactics\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Alerts by MITRE ATT&CK Tactics Observed\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Tactics\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Defense Evasion\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}},{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3 - Copy\"}]},\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Enterprise Threat Intelligence\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Situational Awareness](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMaintaining effective awareness, both current and historical, across all components.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityalert) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Get Visibility Into Alerts](https://docs.microsoft.com/azure/sentinel/quickstart-get-visibility)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, ID.RA, PR.DS, PR.IP, DE.AE, DE.CM, DE.DP, RS.CO](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where isnotempty(ProviderName)\\r\\n| summarize count() by ProductName\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Alerts By Product\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"uninitialized\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where isnotempty(ProviderName)\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by ProductName\\r\\n| render timechart \\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Alerts Over Time\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"uninitialized\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isSituationalVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Situational Awareness\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Dynamic Threat Discovery](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nUsing dynamic approaches (e.g. heuristics, baselining, etc.) to discover new malicious activity\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [BehaviorAnalytics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/behavioranalytics) 🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Advanced Multistage Attack Detection in Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/fusion)<br>\\r\\n💡 [Enable User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/enable-entity-behavior-analytics)<br>\\r\\n💡 [Heuristic Detections in Microsoft Defender for Cloud](https://azure.microsoft.com/blog/heuristic-dns-detections-in-azure-security-center/)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.RA, DE.AE, DE.CM, DE.DP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"defender\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let AnomalousSigninActivity = BehaviorAnalytics\\r\\n | where ActionType == \\\"Sign-in\\\"\\r\\n | where (UsersInsights.NewAccount == True or UsersInsights.DormantAccount == True) and (\\r\\n ActivityInsights.FirstTimeUserAccessedResource == True and ActivityInsights.ResourceUncommonlyAccessedAmongPeers == True\\r\\n or ActivityInsights.FirstTimeUserUsedApp == True and ActivityInsights.AppUncommonlyUsedAmongPeers == False)\\r\\n | join (\\r\\n SigninLogs | where Status.errorCode == 0 or Status.errorCode == 0 and RiskDetail != \\\"none\\\"\\r\\n )\\r\\n on $left.SourceRecordId == $right._ItemId\\r\\n | extend UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName)\\r\\n | extend AnomalyName = \\\"Anomalous Successful Logon\\\",\\r\\n Tactic = \\\"Persistence\\\",\\r\\n Technique = \\\"Valid Accounts\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Successful Sign-in with one or more of the following indications: sign by new or recently dormant accounts and sign in with resource for the first time (while none of their peers did) or to an app for the first time (while none of their peers did) or performed by a user with Risk indication from AAD\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, ResourceDisplayName, AppDisplayName, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet critical = dynamic(['9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3', 'c4e39bd9-1100-46d3-8c65-fb160da0071f', '158c047a-c907-4556-b7ef-446551a6b5f7', '62e90394-69f5-4237-9190-012177145e10', 'd29b2b05-8046-44ba-8758-1e26182fcf32', '729827e3-9c14-49f7-bb1b-9608f156bbb8', '966707d0-3269-4727-9be2-8c3a10f19b9d', '194ae4cb-b126-40b2-bd5b-6091b380977d', 'fe930be7-5e62-47db-91af-98c3a49a38b1']);\\r\\nlet high = dynamic(['cf1c38e5-3621-4004-a7cb-879624dced7c', '7495fdc4-34c4-4d15-a289-98788ce399fd', 'aaf43236-0c0d-4d5f-883a-6955382ac081', '3edaf663-341e-4475-9f94-5c398ef6c070', '7698a772-787b-4ac8-901f-60d6b08affd2', 'b1be1c3e-b65d-4f19-8427-f6fa0d97feb9', '9f06204d-73c1-4d4c-880a-6edb90606fd8', '29232cdf-9323-42fd-ade2-1d097af3e4de', 'be2f45a1-457d-42af-a067-6ec1fa63bc45', '7be44c8a-adaf-4e2a-84d6-ab2649e08a13', 'e8611ab8-c189-46e8-94e1-60213ab1f814']);//\\r\\nlet AnomalousRoleAssignment = AuditLogs\\r\\n | where TimeGenerated > ago(28d)\\r\\n | where OperationName == \\\"Add member to role\\\"\\r\\n | mv-expand TargetResources\\r\\n | extend RoleId = tostring(TargetResources.modifiedProperties[0].newValue)\\r\\n | where isnotempty(RoleId) and RoleId in (critical, high)\\r\\n | extend RoleName = tostring(TargetResources.modifiedProperties[1].newValue)\\r\\n | where isnotempty(RoleName)\\r\\n | extend TargetId = tostring(TargetResources.id)\\r\\n | extend Target = tostring(TargetResources.userPrincipalName)\\r\\n | join kind=inner (\\r\\n BehaviorAnalytics\\r\\n | where ActionType == \\\"Add member to role\\\"\\r\\n | where UsersInsights.BlastRadius == \\\"High\\\" or ActivityInsights.FirstTimeUserPerformedAction == true\\r\\n )\\r\\n on $left._ItemId == $right.SourceRecordId\\r\\n | extend AnomalyName = \\\"Anomalous Role Assignment\\\",\\r\\n Tactic = \\\"Persistence\\\",\\r\\n Technique = \\\"Account Manipulation\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may manipulate accounts to maintain access to victim systems. These actions include adding new accounts to high privileged groups. Dragonfly 2.0, for example, added newly created accounts to the administrators group to maintain elevated access. The query below generates an output of all high Blast Radius users performing Add member to privileged role, or ones that add users for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"TargetUser\\\"]=Target, RoleName, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; let LogOns=materialize(\\r\\n BehaviorAnalytics\\r\\n | where ActivityType == \\\"LogOn\\\");\\r\\nlet AnomalousResourceAccess = LogOns\\r\\n | where ActionType == \\\"ResourceAccess\\\"\\r\\n | where ActivityInsights.FirstTimeUserLoggedOnToDevice == true\\r\\n | extend AnomalyName = \\\"Anomalous Resource Access\\\",\\r\\n Tactic = \\\"Lateral Movement\\\",\\r\\n Technique = \\\"\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversary may be trying to move through the environment. APT29 and APT32, for example, has used PtH & PtT techniques to lateral move around the network. The query below generates an output of all users performing an resource access (4624:3) to devices for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet AnomalousRDPActivity = LogOns\\r\\n | where ActionType == \\\"RemoteInteractiveLogon\\\"\\r\\n | where ActivityInsights.FirstTimeUserLoggedOnToDevice == true\\r\\n | extend AnomalyName = \\\"Anomalous RDP Activity\\\",\\r\\n Tactic = \\\"Lateral Movement\\\",\\r\\n Technique = \\\"\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may use Valid Accounts to log into a computer using the Remote Desktop Protocol (RDP). The adversary may then perform actions as the logged-on user. FIN10, for example, has used RDP to move laterally to systems in the victim environment. The query below generates an output of all users performing a remote interactive logon (4624:10) to a device for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet AnomalousLogintoDevices = LogOns\\r\\n | where ActionType == \\\"InteractiveLogon\\\"\\r\\n | where ActivityInsights.FirstTimeUserLoggedOnToDevice == true\\r\\n | where UsersInsights.DormantAccount == true or DevicesInsights.LocalAdmin == true\\r\\n | extend AnomalyName = \\\"Anomalous Login To Devices\\\",\\r\\n Tactic = \\\"Privilege Escalation\\\",\\r\\n Technique = \\\"Valid Accounts\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may steal the credentials of a specific user or service account using Credential Access techniques or capture credentials earlier in their reconnaissance process through social engineering for means of gaining Initial Access. APT33, for example, has used valid accounts for initial access and privilege escalation. The query below generates an output of all administrator users performing an interactive logon (4624:2) to a device for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet AnomalousPasswordReset = BehaviorAnalytics\\r\\n | where ActionType == \\\"Reset user password\\\"\\r\\n | where ActivityInsights.FirstTimeUserPerformedAction == \\\"True\\\"\\r\\n | join (\\r\\n AuditLogs\\r\\n | where OperationName == \\\"Reset user password\\\"\\r\\n )\\r\\n on $left.SourceRecordId == $right._ItemId\\r\\n | mv-expand TargetResources\\r\\n | extend Target = iff(tostring(TargetResources.userPrincipalName) contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(TargetResources.userPrincipalName, \\\"#\\\")[0])), TargetResources.userPrincipalName), tostring(TargetResources.userPrincipalName)\\r\\n | extend UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName)\\r\\n | extend AnomalyName = \\\"Anomalous Password Reset\\\",\\r\\n Tactic = \\\"Impact\\\",\\r\\n Technique = \\\"Account Access Removal\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may interrupt availability of system and network resources by inhibiting access to accounts utilized by legitimate users. Accounts may be deleted, locked, or manipulated (ex: changed credentials) to remove access to accounts. LockerGoga, for example, has been observed changing account passwords and logging off current users. The query below generates an output of all users performing Reset user password for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"TargetUser\\\"]=Target, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority\\r\\n | sort by TimeGenerated desc;\\r\\nlet AnomalousGeoLocationLogon = BehaviorAnalytics\\r\\n | where ActionType == \\\"Sign-in\\\"\\r\\n | where ActivityInsights.FirstTimeUserConnectedFromCountry == True and (ActivityInsights.FirstTimeConnectionFromCountryObservedInTenant == True or ActivityInsights.CountryUncommonlyConnectedFromAmongPeers == True)\\r\\n | join (\\r\\n SigninLogs\\r\\n )\\r\\n on $left.SourceRecordId == $right._ItemId\\r\\n | extend UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName)\\r\\n | extend AnomalyName = \\\"Anomalous Successful Logon\\\",\\r\\n Tactic = \\\"Initial Access\\\",\\r\\n Technique = \\\"Valid Accounts\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may steal the credentials of a specific user or service account using Credential Access techniques or capture credentials earlier in their reconnaissance process through social engineering for means of gaining Initial Access. APT33, for example, has used valid accounts for initial access. The query below generates an output of successful Sign-in performed by a user from a new geo location he has never connected from before, and none of his peers as well.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, ResourceDisplayName, AppDisplayName, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet AnomalousFailedLogon = BehaviorAnalytics\\r\\n | where ActivityType == \\\"LogOn\\\"\\r\\n | where UsersInsights.BlastRadius == \\\"High\\\"\\r\\n | join (\\r\\n SigninLogs \\r\\n | where Status.errorCode == 50126\\r\\n )\\r\\n on $left.SourceRecordId == $right._ItemId\\r\\n | extend UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName)\\r\\n | extend AnomalyName = \\\"Anomalous Failed Logon\\\",\\r\\n Tactic = \\\"Credential Access\\\",\\r\\n Technique = \\\"Brute Force\\\",\\r\\n SubTechnique = \\\"Password Guessing\\\",\\r\\n Description = \\\"Adversaries with no prior knowledge of legitimate credentials within the system or environment may guess passwords to attempt access to accounts. Emotet, for example, has been observed using a hard coded list of passwords to brute force user accounts. The query below generates an output of all users with 'High' BlastRadius that perform failed Sign-in:Invalid username or password.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"Evidence\\\"]=ActivityInsights, ResourceDisplayName, AppDisplayName, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; \\r\\nlet AnomalousAADAccountManipulation = AuditLogs\\r\\n | where OperationName == \\\"Update user\\\"\\r\\n | mv-expand AdditionalDetails\\r\\n | where AdditionalDetails.key == \\\"UserPrincipalName\\\"\\r\\n | mv-expand TargetResources\\r\\n | extend RoleId = tostring(TargetResources.modifiedProperties[0].newValue)\\r\\n | where isnotempty(RoleId) and RoleId in (critical, high)\\r\\n | extend RoleName = tostring(TargetResources.modifiedProperties[1].newValue)\\r\\n | where isnotempty(RoleName)\\r\\n | extend TargetId = tostring(TargetResources.id)\\r\\n | extend Target = iff(tostring(TargetResources.userPrincipalName) contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(TargetResources.userPrincipalName, \\\"#\\\")[0])), TargetResources.userPrincipalName), tostring(TargetResources.userPrincipalName)\\r\\n | join kind=inner ( \\r\\n BehaviorAnalytics\\r\\n | where ActionType == \\\"Update user\\\"\\r\\n | where UsersInsights.BlastRadius == \\\"High\\\" or ActivityInsights.FirstTimeUserPerformedAction == true\\r\\n )\\r\\n on $left._ItemId == $right.SourceRecordId\\r\\n | extend UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName) \\r\\n | extend AnomalyName = \\\"Anomalous Account Manipulation\\\",\\r\\n Tactic = \\\"Persistence\\\",\\r\\n Technique = \\\"Account Manipulation\\\",\\r\\n SubTechnique = \\\"\\\",\\r\\n Description = \\\"Adversaries may manipulate accounts to maintain access to victim systems. These actions include adding new accounts to high privileged groups. Dragonfly 2.0, for example, added newly created accounts to the administrators group to maintain elevated access. The query below generates an output of all high Blast Radius users performing 'Update user' (name change) to privileged role, or ones that changed users for the first time.\\\"\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"TargetUser\\\"]=Target, RoleName, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority; let AnomalousAADAccountCreation = BehaviorAnalytics\\r\\n | where ActionType == \\\"Add user\\\"\\r\\n | where ActivityInsights.FirstTimeUserPerformedAction == True or ActivityInsights.FirstTimeActionPerformedInTenant == True or ActivityInsights.ActionUncommonlyPerformedAmongPeers == true\\r\\n | join(\\r\\n AuditLogs\\r\\n | where OperationName == \\\"Add user\\\"\\r\\n )\\r\\n on $left.SourceRecordId == $right._ItemId\\r\\n | mv-expand TargetResources\\r\\n | extend Target = iff(tostring(TargetResources.userPrincipalName) contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(TargetResources.userPrincipalName, \\\"#\\\")[0])), TargetResources.userPrincipalName), tostring(TargetResources.userPrincipalName)\\r\\n | extend DisplayName = tostring(UsersInsights.AccountDisplayName),\\r\\n UserPrincipalName = iff(UserPrincipalName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserPrincipalName),\\r\\n UserName = iff(UserName contains \\\"#EXT#\\\", replace(\\\"_\\\", \\\"@\\\", tostring(split(UserPrincipalName, \\\"#\\\")[0])), UserName)\\r\\n | extend AnomalyName = \\\"Anomalous Account Creation\\\",\\r\\n Tactic = \\\"Persistence\\\",\\r\\n Technique = \\\"Create Account\\\",\\r\\n SubTechnique = \\\"Cloud Account\\\",\\r\\n Description = \\\"Adversaries may create a cloud account to maintain access to victim systems. With a sufficient level of access, such accounts may be used to establish secondary credentialed access that does not require persistent remote access tools to be deployed on the system. The query below generates an output of all the users performing user creation for the first time and the target users that were created.\\\"\\t\\r\\n | project TimeGenerated, AnomalyName, Tactic, Technique, SubTechnique, Description, UserName, UserPrincipalName, UsersInsights, ActivityType, ActionType, [\\\"TargetUser\\\"]=Target, [\\\"Evidence\\\"]=ActivityInsights, SourceIPAddress, SourceIPLocation, SourceDevice, DevicesInsights, [\\\"Anomaly Score\\\"]=InvestigationPriority\\r\\n | sort by TimeGenerated desc;\\r\\nlet AnomalyTable = union kind=outer AnomalousSigninActivity, AnomalousRoleAssignment, AnomalousResourceAccess, AnomalousRDPActivity, AnomalousPasswordReset, AnomalousLogintoDevices, AnomalousGeoLocationLogon, AnomalousAADAccountManipulation, AnomalousAADAccountCreation, AnomalousFailedLogon;\\r\\nlet TopUsersByAnomalies = AnomalyTable\\r\\n | summarize hint.strategy = shuffle AnomalyCount=count() by UserName, UserPrincipalName, tostring(UsersInsights.OnPremSid), tostring(UsersInsights.AccountObjectId)\\r\\n | project Name=tolower(UserName), UPN=tolower(UserPrincipalName), AadUserId=UsersInsights_AccountObjectId, Sid=UsersInsights_OnPremSid, AnomalyCount\\r\\n | sort by AnomalyCount desc;\\r\\nlet TopUsersByIncidents = SecurityIncident\\r\\n | summarize hint.strategy = shuffle arg_max(LastModifiedTime, *) by IncidentNumber\\r\\n | where Status == \\\"New\\\" or Status == \\\"Active\\\"\\r\\n | mv-expand AlertIds\\r\\n | extend AlertId = tostring(AlertIds)\\r\\n | join kind= innerunique ( \\r\\n SecurityAlert \\r\\n )\\r\\n on $left.AlertId == $right.SystemAlertId\\r\\n | summarize hint.strategy = shuffle arg_max(TimeGenerated, *), NumberOfUpdates = count() by SystemAlertId\\r\\n | mv-expand todynamic(Entities)\\r\\n | where Entities[\\\"Type\\\"] =~ \\\"account\\\"\\r\\n | extend Name = tostring(tolower(Entities[\\\"Name\\\"])), NTDomain = tostring(Entities[\\\"NTDomain\\\"]), UPNSuffix = tostring(Entities[\\\"UPNSuffix\\\"]), AadUserId = tostring(Entities[\\\"AadUserId\\\"]), AadTenantId = tostring(Entities[\\\"AadTenantId\\\"]), \\r\\n Sid = tostring(Entities[\\\"Sid\\\"]), IsDomainJoined = tobool(Entities[\\\"IsDomainJoined\\\"]), Host = tostring(Entities[\\\"Host\\\"])\\r\\n | extend UPN = iff(Name != \\\"\\\" and UPNSuffix != \\\"\\\", strcat(Name, \\\"@\\\", UPNSuffix), \\\"\\\")\\r\\n | union TopUsersByAnomalies\\r\\n | extend \\r\\n AadPivot = iff(isempty(AadUserId), iff(isempty(Sid), Name, Sid), AadUserId),\\r\\n SidPivot = iff(isempty(Sid), iff(isempty(AadUserId), Name, AadUserId), Sid),\\r\\n UPNExists = iff(isempty(UPN), false, true),\\r\\n NameExists = iff(isempty(Name), false, true),\\r\\n SidExists = iff(isempty(Sid), false, true),\\r\\n AADExists = iff(isempty(AadUserId), false, true)\\r\\n | summarize hint.strategy = shuffle IncidentCount=dcount(IncidentNumber, 4), AlertCount=dcountif(AlertId, isnotempty(AlertId), 4), AnomalyCount=sum(AnomalyCount), any(Title, Severity, Status, StartTime, IncidentNumber, IncidentUrl, Owner), UPNAnchor=anyif(UPN, UPNExists == true), NameAnchor=anyif(Name, NameExists == true), AadAnchor=anyif(AadUserId, AADExists == true), SidAnchor=anyif(Sid, SidExists == true), any(SidPivot) by AadPivot\\r\\n | summarize hint.strategy = shuffle IncidentCount=sum(IncidentCount), AlertCount=sum(AlertCount), AnomalyCount=sum(AnomalyCount), UPNAnchor=anyif(UPNAnchor, isempty(UPNAnchor) == false), NameAnchor=anyif(NameAnchor, isempty(NameAnchor) == false), AadAnchor=anyif(AadAnchor, isempty(AadAnchor) == false), SidAnchor=anyif(SidAnchor, isempty(SidAnchor) == false), any(any_Title, any_Severity, any_StartTime, any_IncidentNumber, any_IncidentUrl) by any_SidPivot\\r\\n | summarize hint.strategy = shuffle IncidentCount=sum(IncidentCount), AlertCount=sum(AlertCount), AnomalyCount=sum(AnomalyCount), UPNAnchor=anyif(UPNAnchor, isempty(UPNAnchor) == false), AadAnchor=anyif(AadAnchor, isempty(AadAnchor) == false), SidAnchor=anyif(SidAnchor, isempty(SidAnchor) == false), any(any_any_Title, any_any_Severity, any_any_StartTime, any_any_IncidentNumber, any_any_IncidentUrl) by NameAnchor\\r\\n | project [\\\"UserName\\\"]=NameAnchor, IncidentCount, AlertCount, AnomalyCount, [\\\"AadUserId\\\"]=AadAnchor, [\\\"OnPremSid\\\"]=SidAnchor, [\\\"UserPrincipalName\\\"]=UPNAnchor;\\r\\nTopUsersByIncidents\\r\\n| where UserPrincipalName !contains \\\"[\\\"\\r\\n| where UserPrincipalName <> \\\"\\\"\\r\\n| project UserPrincipalName, IncidentCount, AlertCount, AnomalyCount\\r\\n| sort by AlertCount desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"User Entity Behavior Analytics Alerts\",\"noDataMessage\":\"There are no results within the selected thresholds (time, workspace, subscription). See Enable User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel for respective UEBA configurations (https://docs.microsoft.com/azure/sentinel/enable-entity-behavior-analytics)\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"AlertCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"orange\"}},{\"columnMatch\":\"AnomalyCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"yellow\"}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"SourceIPLocation\",\"longitude\":\"SourceIPLocation\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\"}]}}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 1\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"fusion\\\" or Title contains \\\"dynamic\\\" or Title contains \\\"anomal\\\" or Title contains \\\"behavior\\\" or Title contains \\\"learning\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Dynamic Threat Discovery\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDynamicVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Dynamic Threat Discovery\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Policy Enforcement Parity](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nConsistently applying security protections and other policies, independent of the communication mechanism, forwarding path, or endpoints used.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [What is Azure Policy?](https://docs.microsoft.com/azure/governance/policy/overview)<br>\\r\\n💡 [Review your security recommendations](https://docs.microsoft.com/azure/defender-for-cloud/review-security-recommendations)<br>\\r\\n💡 [Apply Azure security baselines to machines](https://docs.microsoft.com/azure/defender-for-cloud/apply-security-baseline)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Policy](https://portal.azure.com/#blade/Microsoft_Azure_Policy/PolicyMenuBlade/Overview) <Br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS, PR.IP, PR.MA](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isPolicyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Policy Enforcement Parity\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Effective Use of Shared Services](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nEmploying shared services, where applicable, that can be individually tailored, measured to independently validate service conformance, and offer effective protections for tenants against malicious actors, both external as well as internal to the service provider.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Get Started with Azure Lighthouse](https://azure.microsoft.com/services/azure-lighthouse/)<br>\\r\\n💡 [Customer Lockbox for Microsoft Azure](https://docs.microsoft.com/azure/security/fundamentals/customer-lockbox-overview)<br>\\r\\n💡 [What are External Identities in Microsoft Entra ID?](https://docs.microsoft.com/azure/active-directory/external-identities/compare-with-b2c)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Lighthouse](https://portal.azure.com/#blade/Microsoft_Azure_CustomerHub/LighthouseBlade) <br>\\r\\n🔀 [Customer Lockbox for Microsoft Azure](https://portal.azure.com/#blade/Microsoft_Azure_Lockbox/LockboxMenu/Overview) <br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, ID.GV, ID.RM, ID.SC, PR.AT, RS.CO](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"guest\\\" or RecommendationDisplayName contains \\\"shared\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let LastObserved = SigninLogs\\r\\n| where ResultType == 0\\r\\n| where UserType == \\\"Guest\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by UserPrincipalName\\r\\n| project UserPrincipalName, UserType, LastSignIn=TimeGenerated;\\r\\nSigninLogs\\r\\n| extend UserProfile = strcat(\\\"https://portal.azure.com/#blade/Microsoft_AAD_IAM/UserDetailsMenuBlade/Profile/userId/\\\", UserId)\\r\\n| where ResultType == 0\\r\\n| summarize count() by UserPrincipalName, UserProfile, UserId\\r\\n| join (LastObserved) on UserPrincipalName\\r\\n| project UserPrincipalName, UserType, SignInCount=count_, UserProfile, LastSignIn, UserId\\r\\n| sort by SignInCount desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Guest Accounts\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"SignInCount\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"UserProfile\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"AAD User Profile >>\",\"bladeOpenContext\":{\"bladeName\":\"UserDetailsMenuBlade\",\"extensionName\":\"Microsoft_AAD_IAM\",\"bladeParameters\":[{\"name\":\"userId\",\"source\":\"column\",\"value\":\"UserId\"}]}}},{\"columnMatch\":\"UserId\",\"formatter\":5},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}}],\"filter\":true},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"customWidth\":\"50\",\"name\":\"query - 9\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"shared\\\" or Description contains \\\"guest\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"shared\\\" or Description contains \\\"guest\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"shared\\\" or Description contains \\\"guest\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| where Description !contains \\\"not shared\\\"\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isEffectiveVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Effective Use of Shared Services\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Integrated Desktop, Mobile, and Remote Policies](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDefining polices such that they apply to a given agency entity no matter its location.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [What is Conditional Access?](https://docs.microsoft.com/azure/active-directory/conditional-access/overview)<br>\\r\\n💡 [What are Common Ways to Use Conditional Access with Intune?](https://docs.microsoft.com/mem/intune/protect/conditional-access-intune-common-ways-use)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)<br>\\r\\n🔀 [Microsoft Endpoint Manager Admin Center](https://devicemanagement.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.AC, PR.DS, PR.IP, PR.MA](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| extend DeviceOS = tostring(DeviceDetail.operatingSystem)\\r\\n| summarize count() by DeviceOS\\r\\n| where DeviceOS <> \\\"\\\"\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Policy Application by Operating System\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ConditionalAccessPolicy\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9 - Copy\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| where ResultType == 0\",\"size\":0,\"showAnalytics\":true,\"title\":\"Sign-Ins By Location\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"map\",\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"Location\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"greenRed\"}}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| mv-expand ConditionalAccessPolicies\\r\\n| extend ConditionalAccessPolicy = tostring(ConditionalAccessPolicies.displayName)\\r\\n| summarize count() by ConditionalAccessPolicy\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Conditional Access Policies\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ConditionalAccessPolicy\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isIntegratedVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Integrated Desktop, Mobile, and Remote Policies\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isUniversalSecurityCapabilitiesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UniversalSecurityCapabilities\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Files](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nFile-based protections including anti-malware, malicious code removal, content disarm & reconstruction, and detonation chambers.\\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Files Capabilities Overview\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 106\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Anti-Malware\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Malware\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Content Disarm & Reconstruction\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Content\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Detonation Chamber\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Detonation\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Data Loss Prevention\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isMalwareVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Malware\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isContentVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Content\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"1f176b0f-1f2f-4e12-afb0-3f10c834ef24\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDetonationVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Detonation\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b17f2902-5d29-45b2-8712-bff5b7dd1487\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"793ffbca-13bc-4fac-9535-048cbd9efc54\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Anti-Malware](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAnti-malware protections detect the presence of malicious code and facilitate its quarantine or removal.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityalert) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/)\\r\\n ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/azure-defender/)\\r\\n✳️ [Microsoft Defender for Endpoint](https://www.microsoft.com/microsoft-365/security/endpoint-defender)<br> ✳️ [Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender) ✳️ [Microsoft Defender for Identity](https://www.microsoft.com/microsoft-365/security/identity-defender) ✳️ [Microsoft Defender for Cloud Apps](https://www.microsoft.com/microsoft-365/enterprise-mobility-security/cloud-app-security)\\r\\n\\r\\n### Implementation\\r\\n💡 [Microsoft Antimalware Extension for Windows](https://docs.microsoft.com/azure/virtual-machines/extensions/iaas-antimalware-windows)<br>\\r\\n💡 [Microsoft Antimalware for Azure Cloud Services and Virtual Machines](https://docs.microsoft.com/azure/security/fundamentals/antimalware)<br>\\r\\n💡 [Microsoft Defender for Cloud Apps: Malware Detection](https://docs.microsoft.com/cloud-app-security/anomaly-detection-policy#malware-detection)<br>\\r\\n💡 [Microsoft Defender for Endpoint](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/microsoft-defender-advanced-threat-protection)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Microsoft Defender for Identity](https://portal.atp.azure.com/) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft Defender for Cloud Apps](https://portal.cloudappsecurity.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS, PR.PT, DE.CM, DE.DP, RS.MI](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"endpoint protection\\\" or RecommendationDisplayName contains \\\"malware\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where Description contains \\\"malware\\\" or Title contains \\\"malware\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Malware\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where AlertName contains \\\"mal\\\"\\r\\n| summarize count() by ProductName\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Malware Detected by Product\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Defense Evasion\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isMalwareVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Anti-Malware\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Content Disarm & Reconstruction](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nContent disarm and reconstruction technology detects the presence of unapproved active content and facilitates its removal.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n🔷 [EmailAttachmentInfo](https://docs.microsoft.com/azure/azure-monitor/reference/tables/emailattachmentinfo) ✳️ [Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender)\\r\\n\\r\\n### Implementation \\r\\n💡 [Setup Safe Attachments Policies in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/set-up-atp-safe-attachments-policies)<br>\\r\\n💡 [Threat and Vulnerability Management](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/next-gen-threat-and-vuln-mgt)<br>\\r\\n💡 [Microsoft Defender Application Guard overview](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-application-guard/md-app-guard-overview)<br>\\r\\n💡 [Create and deploy an Exploit Guard policy](https://docs.microsoft.com/mem/configmgr/protect/deploy-use/create-deploy-exploit-guard-policy)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft Endpoint Manager Admin Center](https://endpoint.microsoft.com/#home)<br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM, DE.DP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where Description contains \\\"exploit\\\" or Title contains \\\"exploit\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Exploits\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"EmailAttachmentInfo\\r\\n| extend Detection = strcat(DetectionMethods)\\r\\n| where ThreatTypes <> \\\"\\\"\\r\\n| project RecipientEmailAddress, FileName, ThreatTypes, ThreatNames, Detection, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Safe Attachments: Attachment Mitigation\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isContentVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Content Disarm & Reconstruction\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Detonation Chamber](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDetonation chambers facilitate the detection of malicious code through the use of protected and isolated execution environments to analyze the files.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n🔷 [EmailEvents](https://docs.microsoft.com/azure/azure-monitor/reference/tables/emailevents) ✳️ [Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Submit File for Deep Analysis](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/respond-file-alerts#submit-files-for-deep-analysis)<br>\\r\\n💡 [Using the Built-in URL Detonation in Microsoft Sentinel](https://techcommunity.microsoft.com/t5/azure-sentinel/using-the-new-built-in-url-detonation-in-azure-sentinel/ba-p/996229)<br>\\r\\n💡 [Safe Links in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/atp-safe-links)<br>\\r\\n💡 [Safe Attachments in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/atp-safe-attachments)<br>\\r\\n💡 [Microsoft Defender Application Guard overview](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-application-guard/md-app-guard-overview)<br>\\r\\n💡 [Create and deploy an Exploit Guard policy](https://docs.microsoft.com/mem/configmgr/protect/deploy-use/create-deploy-exploit-guard-policy)<br>\\r\\n\\r\\n### Microsoft Portals \\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft Endpoint Manager Admin Center](https://endpoint.microsoft.com/#home)<br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[DE.CM, DE.DP, RS.AN, RS.MI](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where Description contains \\\"detonation\\\" or Title contains \\\"detonation\\\" or Description contains \\\"sand\\\" or Title contains \\\"sand\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Detonation\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"EmailEvents\\r\\n| where DetectionMethods <>\\\"\\\"\\r\\n| project RecipientEmailAddress, DeliveryAction, DeliveryLocation, EmailDirection, EmailAction, DetectionMethods, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Email Detonation: SafeLinks, SafeAttachments, SafeFiles\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"DeliveryAction\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"EmailDirection\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"Outbound\",\"representation\":\"right\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"left\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"EmailAction\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"DetectionMethods\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isDetonationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Detonation Chamber\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Loss Prevention](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData loss prevention technologies detect instances of the exfiltration, either malicious or accidental, of agency data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [InformationProtectionLogs_CL](https://docs.microsoft.com/azure/information-protection/audit-logs) ✳️ [Azure Information Protection](https://azure.microsoft.com/services/information-protection/)<br>\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityalert) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender) ✳️ [Microsoft Defender for Endpoint]( https://www.microsoft.com/microsoft-365/security/endpoint-defender) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [How to Configure a Label for Rights Management Protection](https://docs.microsoft.com/azure/information-protection/configure-policy-protection)<br>\\r\\n💡 [Hunt for Threats with Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/hunting)<br>\\r\\n💡 [Learn about Microsoft 365 Endpoint Data Loss Prevention](https://docs.microsoft.com/microsoft-365/compliance/endpoint-dlp-learn-about)<br>\\r\\n💡 [Configure and View Alerts for DLP Polices](https://docs.microsoft.com/microsoft-365/compliance/dlp-configure-view-alerts-policies)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Information Protection](https://portal.azure.com/#blade/Microsoft_Azure_InformationProtection/DataClassGroupEditBlade/quickstartBlade) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br> \\r\\n🔀 [Office 365 Security & Compliance Center](https://protection.office.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Description contains \\\"data\\\" or Title contains \\\"data\\\" or Description contains \\\"loss\\\" or Title contains \\\"loss\\\" or Description contains \\\"exfil\\\" or Title contains \\\"exfil\\\" or Tactics contains \\\"exfil\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Data Loss\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| project UserId_s, LabelName_s, Operation_s, Activity_s, IPv4_s, ProtectionOwner_s, ApplicationName_s, ProcessName_s, Platform_s, ContentId_g, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Scan/Monitor for Sensitive Data with Azure Information Protection\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserId_s\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"red\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"orange\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"yellow\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"blue\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"uninitialized\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Alert >\"}},{\"columnMatch\":\"UPN\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Incident >\"},\"numberFormat\":{\"unit\":0,\"options\":{\"style\":\"decimal\"}}},{\"columnMatch\":\"count_\",\"formatter\":8,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"city_\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blue\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"state_\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\",\"text\":\"{0}{1}\"}]}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"SourceIPLocation\",\"longitude\":\"SourceIPLocation\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\"}]}}},\"customWidth\":\"50\",\"name\":\"query - 2\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| extend UserPrincipalName = UserId_s_s\\r\\n| where LabelName_s <> \\\"\\\"\\r\\n| join (SigninLogs) on UserPrincipalName\\r\\n| extend City = tostring(LocationDetails.city)\\r\\n| extend State = tostring(LocationDetails.state)\\r\\n| extend Country_Region = tostring(LocationDetails.countryOrRegion)\\r\\n\",\"size\":3,\"showAnalytics\":true,\"title\":\"Sensitive Data Access by Geolocation\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"map\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"warning\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"UncommonActionVolume\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"UncommonAction\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"}},{\"columnMatch\":\"FirstTimeUserAction\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"FirstTimeDeviceLogon\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellow\"}},{\"columnMatch\":\"IncidentCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"AlertCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"orange\"}},{\"columnMatch\":\"AnomalyCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"yellow\"}}]},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"yellow\"}]}}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 12\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDataVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Loss Prevention\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isFilesVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"FilesGroup\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Email](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nEmail-based protections including anti-phishing, anti-spam, authenticated received chain, data loss prevention, DMARC for incoming/outgoing mail, email encryption, and malicious URL protections.\\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Email Capabilities Help\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 107\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Anti-Phishing Protections\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Phishing\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Anti-Spam Protections\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Spam\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Authenticated Received Chain\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Authenticated\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Data Loss Prevention\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DMARC for Incoming Email\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Incoming\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isPhishingVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Phishing\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isSpamVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Spam\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"5e162b71-5dff-4440-8bd9-111c1ec62efb\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAuthenticatedVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Authenticated\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"37272499-cf34-4fd3-8f26-5929ea74e783\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"2086488a-60de-43a5-a31f-0ae0eca9abd3\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIncomingVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Incoming\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"e35e9dbc-8e1d-4749-9fe3-6e1b7cc19f2c\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DMARC for Outgoing Email\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Outgoing\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Encryption for Email Transmission\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Encryption\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Malicious URL Protections\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Malicious\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"URL Click-Through Protection\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Url\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8 - Copy\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"2477e9e4-bcad-49d6-a4b6-df6672debb7b\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isOutgoingVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Outgoing\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEncryptionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Encryption\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"1fa8afad-de60-4eb0-8a40-a43bde323bdb\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isMaliciousVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Malicious\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"125bc4a9-0a88-4bef-80c9-2707fa0e5f74\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isUrlVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Url\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"e62d359a-891b-4663-9384-b7891d8dc461\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors - Copy\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Anti-Phishing Protections](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAnti-phishing protections detect instances of phishing and prevent users from accessing them.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Anti-Phishing Protection in Microsoft 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/anti-phishing-protection)<br>\\r\\n💡 [Configure Anti-Phishing Policies in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/configure-atp-anti-phishing-policies)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AT, PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"email\\\" or Title contains \\\"phish\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Phishing\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isPhishingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Anti-Phishing Protections\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Anti-SPAM Protections](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAnti-SPAM protections detect and quarantine instances of SPAM.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [EmailEvents](https://docs.microsoft.com/azure/azure-monitor/reference/tables/emailevents) ✳️ [Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n\\r\\n### Microsoft Reference \\r\\n💡 [Anti-Spam protection in Exchange Online Protection](https://docs.microsoft.com/microsoft-365/security/office-365-security/anti-spam-protection)<br>\\r\\n💡 [Configure Anti-Spam Policies in Exchange Online Protection](https://docs.microsoft.com/microsoft-365/security/office-365-security/configure-your-spam-filter-policies)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"EmailEvents\\r\\n| extend Spam = tostring(parse_json(ConfidenceLevel).Spam)\\r\\n| where Spam <> \\\"Skipped\\\"\\r\\n| where Spam <> \\\"Not spam\\\"\\r\\n| where Spam <> \\\"\\\"\\r\\n| project Spam, RecipientEmailAddress, DeliveryAction, EmailDirection, ConfidenceLevel, DetectionMethods, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Spam Email Actions\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Spam\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Mail\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isSpamVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Anti-SPAM Protections\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Authenticated Received Chain](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAuthenticated Received Chain allows for an intermediary, like a mailing list or forwarding service, to sign its own authentication of the original email, allowing downstream entities to accept the intermediary’s authentication even if the email was changed.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityevent) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [How Microsoft 365 Utilizes Authenticated Received Chain (ARC)](https://docs.microsoft.com/microsoft-365/security/office-365-security/use-dmarc-to-validate-email#how-microsoft-365-utilizes-authenticated-received-chain-arc)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where ProviderName == \\\"OATP\\\"\\r\\n| where Entities contains \\\"Fail\\\"\\r\\n| project AlertName, AlertLink, ProductName, Entities, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Alerts for DMARC, SPF, DKIM Validations\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Alert >>\"}},{\"columnMatch\":\"Spam\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Mail\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_thresholds_AlertName_0\",\"sortOrder\":1}]},\"sortBy\":[{\"itemKey\":\"$gen_thresholds_AlertName_0\",\"sortOrder\":1}]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAuthenticatedVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Authenticated Received Chain\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Loss Prevention](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData loss prevention technologies detect instances of the exfiltration, either malicious or accidental, of agency data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Microsoft References \\r\\n💡 [How to Configure a Label for Rights Management Protection](https://docs.microsoft.com/azure/information-protection/configure-policy-protection)<br>\\r\\n💡 [Configure and View Alerts for DLP Polices](https://docs.microsoft.com/microsoft-365/compliance/dlp-configure-view-alerts-policies)<br>\\r\\n💡 [How DLP Works Between the Security & Compliance Center and Exchange Admin Centers](https://docs.microsoft.com/microsoft-365/compliance/how-dlp-works-between-admin-centers)<br>\\r\\n💡 [Email Entity Page](https://docs.microsoft.com/microsoft-365/security/office-365-security/mdo-email-entity-page)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Information Protection](https://portal.azure.com/#blade/Microsoft_Azure_InformationProtection/DataClassGroupEditBlade/quickstartBlade)<br> \\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Tactics contains \\\"exfil\\\"\\r\\n| where Title contains \\\"email\\\" or Title contains \\\"phish\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Email Data Loss\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDataVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Loss Prevention\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DMARC for Incoming Email](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDMARC protections authenticate incoming email according to the DMARC email authentication protocol defined in RFC 7489.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityevent) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Use DMARC to Validate Email](https://docs.microsoft.com/microsoft-365/security/office-365-security/use-dmarc-to-validate-email)<br>\\r\\n💡 [How Microsoft 365 Handles Inbound Emails that Fail DMARC](https://docs.microsoft.com/microsoft-365/security/office-365-security/use-dmarc-to-validate-email#how-microsoft-365-handles-inbound-email-that-fails-dmarc)<Br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, PR.IP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where ProviderName == \\\"OATP\\\"\\r\\n| where Entities contains \\\"Fail\\\" and Entities contains \\\"inbound\\\"\\r\\n| project AlertName, AlertLink, ProductName, Entities, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Inbound DMARC Failures\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Alert >>\"}},{\"columnMatch\":\"Spam\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Mail\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isIncomingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DMARC for Incoming Email\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DMARC for Outgoing Email](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDMARC protections facilitate the authentication of outgoing email by signing the emails and ensuring that external parties may validate the email signatures. The DMARC email authentication protocol is defined in RFC7489.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityevent) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Use DMARC to Validate Email](https://docs.microsoft.com/microsoft-365/security/office-365-security/use-dmarc-to-validate-email)<br>\\r\\n💡 [How Microsoft 365 Handles Inbound Emails that Fail DMARC](https://docs.microsoft.com/microsoft-365/security/office-365-security/use-dmarc-to-validate-email#how-microsoft-365-handles-inbound-email-that-fails-dmarc)<Br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, PR.IP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityAlert\\r\\n| where ProviderName == \\\"OATP\\\"\\r\\n| where Entities contains \\\"Fail\\\" and Entities contains \\\"outbound\\\"\\r\\n| project AlertName, AlertLink, ProductName, Entities, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Outbound DMARC Failures\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Alert >>\"}},{\"columnMatch\":\"Spam\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Mail\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isOutgoingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DMARC for Outgoing Email\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Encryption for Email Transmission](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nEmail services are configured to use encrypted connections, when possible, for communications between clients and other email servers.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Email Encryption](https://docs.microsoft.com/microsoft-365/compliance/ome)<br>\\r\\n💡 [How Exchange Online Uses TLS to Secure Email Connections](https://docs.microsoft.com/microsoft-365/compliance/exchange-online-uses-tls-to-secure-email-connections)<br>\\r\\n💡 [Define Mail Flow Rules to Encrypt Email Messages](https://docs.microsoft.com/microsoft-365/compliance/define-mail-flow-rules-to-encrypt-email)<br>\\r\\n💡 [Setup New Message Encryption Capabilities](https://docs.microsoft.com/microsoft-365/compliance/set-up-new-message-encryption-capabilities)<br>\\r\\n💡 [Define Mail Flow Rules to Encrypt Email Messages](https://docs.microsoft.com/microsoft-365/compliance/define-mail-flow-rules-to-encrypt-email)<br>\\r\\n💡 [Manage Office 365 Message Encryption](https://docs.microsoft.com/microsoft-365/compliance/manage-office-365-message-encryption)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/)<br> 🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br> 🔀[Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"encrypt\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information.\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isEncryptionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Encryption for Email Transmission\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Malicious URL Protections](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMalicious URL protections detect malicious URLs in emails and prevent users from accessing them.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [EmailEvents](https://docs.microsoft.com/azure/azure-monitor/reference/tables/emailevents) ✳️ [Microsoft Defender for Office 365](https://www.microsoft.com/microsoft-365/security/office-365-defender)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Safe Links in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/atp-safe-links)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"EmailEvents\\r\\n| where DetectionMethods contains \\\"url\\\"\\r\\n| join (EmailUrlInfo) on NetworkMessageId\\r\\n| project RecipientEmailAddress, DeliveryAction, Url, UrlDomain, EmailDirection, ConfidenceLevel, DetectionMethods, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"SafeLinks Email Protections\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecipientEmailAddress\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"DeliveryAction\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Url\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Spam\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Mail\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ThreatTypes\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isMaliciousVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Malicious URL Protections\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [URL Click-Through Protection](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nURL click-through protections ensure that when a URL from an email is clicked, the requester is directed to a protection that verifies the security of the URL destination before permitting access.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Safe Links in Microsoft Defender for Office 365](https://docs.microsoft.com/microsoft-365/security/office-365-security/atp-safe-links)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"url\\\" or Title contains \\\"url\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Urls\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isUrlVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"URL Click-Through Protection\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isEmailVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Email Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Web](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nWeb-based protections including break/inspect, active content mitigation, certificate blacklisting/consensus, content filtering, authenticated proxy, data loss prevention, DNS-over-HTTPS filtering, RFC compliance enforcement, domain category filtering, domain reputation filtering, bandwidth control, malicious content filtering, and access control.\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Web Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 108\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Break and Inspect\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Break\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Active Content Mitigation\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Active\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Certificate Denylisting\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Certificate\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Content Filtering\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Content\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Authenticated Proxy\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Authenticated\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Data Loss Prevention\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DNS-over-HTTPS Filtering\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"DNS\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a30d01d0-38f1-4a91-9cf6-cdb181d676b5\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isBreakVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Break\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isActiveVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Active\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b2b0b9d3-128b-4ec7-a1e8-287df84633da\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isCertificateVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Certificate\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"508474da-365f-43db-9c42-4331e8648144\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isContentVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Content\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"68f6fab3-9f4c-4ea8-ac17-064809f6740e\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAuthenticatedVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Authenticated\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"a539291a-2744-47ef-9558-f15986ecf508\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"bd2ce9fe-9e44-4bcf-9f00-83a04c86e456\"},{\"id\":\"5cb17a08-31fb-4eee-87d8-abef7ecbb7e2\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDNSVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"DNS\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"RFC Compliance Enforcement\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"RFC\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Domain Category Filtering\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Category\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Domain Reputation Filter\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Reputation\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Bandwidth Control\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Bandwidth\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Malicious Content Filtering\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Malicious\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Access Control\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Access\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8 - Copy\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"0114faf6-043c-452c-9249-34899d8965a1\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isRFCVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"RFC\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isCategoryVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Category\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"35f239a8-a4dc-4e7f-8b70-dd4c876151db\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isReputationVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Reputation\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"57218915-069e-4559-94ff-29144252c397\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isBandwidthVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Bandwidth\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"d77f49a8-0e58-46c3-b705-5a61736b41ea\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isMaliciousVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Malicious\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"a11bbfd4-4c45-4527-b1d2-6cab517590cb\"},{\"id\":\"a1bdb4f4-7f9d-48f8-8deb-e979a7e203a6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAccessVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Access\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters - Copy\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Break and Inspect](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nBreak-and-Inspect systems, or encryption proxies, terminate encrypted traffic, logging or performing policy enforcement against the plaintext, and re-encrypting the traffic, if applicable, before transmitting to the final destination.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure Firewall Premium](https://azure.microsoft.com/services/azure-firewall/) ✳️ [Network Watcher](https://azure.microsoft.com/services/network-watcher/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Firewall Premium Features](https://docs.microsoft.com/azure/firewall/premium-features) <br>\\r\\n💡 [Inspect Traffic with Azure Firewall](https://docs.microsoft.com/azure/private-link/inspect-traffic-with-azure-firewall) <br>\\r\\n💡 [Tutorial: Deploy and Configure Azure Firewall Using the Azure Portal](https://docs.microsoft.com/azure/firewall/tutorial-firewall-deploy-portal) <br>\\r\\n💡 [Create an Azure Network Watcher instance](https://docs.microsoft.com/azure/network-watcher/network-watcher-create) <br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies) <br>\\r\\n🔀 [Network Watcher](https://portal.azure.com/#blade/Microsoft_Azure_Network/NetworkWatcherMenuBlade/overview) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"protected by Azure Firewall\\\" or RecommendationDisplayName contains \\\"watcher\\\" or RecommendationDisplayName contains \\\"proxy\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"azurefirewalls\\\" or type contains \\\"firewallpolicies\\\" or type contains \\\"networkwatchers\\\" or type contains \\\"webapplicationfirewall\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Break & Inspect Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"}]},\"conditionalVisibility\":{\"parameterName\":\"isBreakVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Break and Inspect\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Active Content Mitigation](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nActive content mitigation protections detect the presence of unapproved active content and facilitate its removal.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) 🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Web Application Firewall](https://azure.microsoft.com/services/web-application-firewall/)\\r\\n\\r\\n\\r\\n### Implementation \\r\\n💡[What is Azure Web Application Firewall on Azure Application Gateway?](https://docs.microsoft.com/azure/web-application-firewall/ag/ag-overview)<br>\\r\\n💡[Azure Web Application Firewall on Azure Front Door](https://docs.microsoft.com/azure/web-application-firewall/afds/afds-overview)<br>\\r\\n💡[Connect data from Microsoft 365 Defender to Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/connect-microsoft-365-defender?tabs=MDE)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Web Application Firewall Policies](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"endpoint protection\\\" or RecommendationDisplayName contains \\\"Web Application Firewall\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"webapplicationfirewall\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Active Content Mitigation Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FakeData = (datatable (Message: string, ruleName_s: string, clientIp_s: string, clientIP_s: string, action_s: string, transactionId_s: string, trackingReference_s: string) [\\\"\\\", \\\"\\\", \\\"\\\", \\\"\\\", \\\"\\\", \\\"\\\", \\\"\\\"]);\\r\\nFakeData\\r\\n| union AzureDiagnostics\\r\\n| where (ResourceType == \\\"APPLICATIONGATEWAYS\\\" or ResourceType == \\\"FRONTDOORS\\\" or ResourceType == \\\"CDNWEBAPPLICATIONFIREWALLPOLICIES\\\") and (\\\"Application Gateway\\\" == \\\"All\\\" or (ResourceType == \\\"APPLICATIONGATEWAYS\\\" and \\\"Application Gateway\\\" contains \\\"application gateway\\\") or (ResourceType == \\\"FRONTDOORS\\\" and \\\"Application Gateway\\\" contains \\\"azure front door\\\") or (ResourceType == \\\"CDNWEBAPPLICATIONFIREWALLPOLICIES\\\" and \\\"Application Gateway\\\" contains \\\"cdn\\\")) and (\\\"SOC-NS-AG-WAFV2 - 1129440\\\" == \\\"All\\\" or Resource in ('SOC-NS-AG-WAFV2'))\\r\\n| where Category == \\\"FrontdoorWebApplicationFirewallLog\\\" or OperationName == \\\"ApplicationGatewayFirewall\\\" or Category == \\\"WebApplicationFirewallLogs\\\"\\r\\n| extend Action = iif(action_s == \\\"Blocked\\\", Action = \\\"Block\\\", action_s)\\r\\n| extend Action = iif(Action == \\\"Detected\\\", Action = \\\"Log\\\", Action)\\r\\n| where '*' == Action or '*' == \\\"*\\\" \\r\\n| where '*' == requestUri_s or '*' == \\\"*\\\"\\r\\n| extend Rule = strcat(ruleName_s, Message), ClientIP = strcat(clientIp_s, clientIP_s)\\r\\n| extend Rule= iif(Rule contains \\\"Mandatory rule. Cannot be disabled.\\\", strcat_array(split(Rule, \\\"Mandatory rule. Cannot be disabled. Inbound \\\", 1), \\\"\\\"), Rule) // Removes initial component for mandatory rule \\r\\n| extend Rule = iif(Rule contains \\\"Total Inbound Score\\\", strcat_array(array_concat(split(Rule, \\\" - SQLI=\\\", 0), parse_json('[\\\") -\\\"]'), split(Rule, \\\"):\\\", 1)), \\\"\\\"), Rule) // Removes smaller information if more info is available for anomaly score\\r\\n| summarize count() by Rule\\r\\n| top 50 by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Azure WAF Events\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Rule\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"warning\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redDark\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isActiveVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Active Content Mitigation\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Certificate Denylisting](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCertificate denylisting protections prevent communication with entities that use a set of known bad certificates.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) 🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation\\r\\n💡 [Certificates Used by Azure Firewall Premium](https://docs.microsoft.com/azure/firewall/premium-certificates)<br>\\r\\n💡 [Tutorial: Deploy and Configure Azure Firewall Using the Azure Portal](https://docs.microsoft.com/azure/firewall/tutorial-firewall-deploy-portal)<br>\\r\\n💡 [Quickstart: Create a Key Vault using the Azure Portal](https://docs.microsoft.com/azure/key-vault/general/quick-create-portal)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)<br>\\r\\n🔀 [Key Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"certificate\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"cert\\\" \\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"cert\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"cert\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isCertificateVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Certificate Denylisting\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Content Filtering](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nContent filtering protections detect the presence of unapproved content and facilitate its removal or denial of access.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall](https://azure.microsoft.com/services/azure-firewall/)\\r\\n\\r\\n### Implementation\\r\\n💡 [Azure Firewall Web Categories](https://docs.microsoft.com/azure/firewall/web-categories)<br>\\r\\n💡 [Tutorial: Deploy and Configure Azure Firewall Using the Azure Portal](https://docs.microsoft.com/azure/firewall/tutorial-firewall-deploy-portal)<br>\\r\\n💡 [Web Content Filtering](https://docs.microsoft.com/microsoft-365/security/defender-endpoint/web-content-filtering)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewalls](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls)<br>\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)<br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM, DE.DP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let materializedData =\\r\\n materialize(\\r\\n AzureDiagnostics\\r\\n | where Category == \\\"AzureFirewallApplicationRule\\\"\\r\\n | project msg_s, Resource, TimeGenerated);\\r\\nunion\\r\\n (\\r\\n materializedData\\r\\n | where msg_s has \\\"Web Category:\\\" and msg_s has \\\". Url\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Url:\\\" Url \\\". Action: \\\" Action \\\". Rule Collection:\\\" RuleCollection \\\". Rule:\\\" Rule \\\". Web Category:\\\" WebCategory\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s has \\\". Url\\\"\\r\\n and msg_s has \\\". No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Url:\\\" Url \\\". Action: \\\" Action \\\". No rule matched\\\" *\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s has \\\". No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". No rule matched\\\" *\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s has \\\"Web Category:\\\" and msg_s !has \\\". Url\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Rule Collection:\\\" RuleCollection \\\". Rule:\\\" Rule \\\". Web Category:\\\" WebCategory\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\" Reason: \\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". \\\" RuleCollection \\\". \\\" Rule\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\"TLS extension was missing\\\"\\r\\n | where msg_s has \\\" Reason:\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\". Action: \\\" Action \\\". Reason: \\\" Rule \\\".\\\"\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"TLS extension was missing\\\"\\r\\n and msg_s !has \\\"No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Rule Collection: \\\" RuleCollection \\\". Rule: \\\" Rule\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\" Reason: \\\"\\r\\n | where msg_s has \\\"Rule Collection Group\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Policy:\\\" Policy \\\". Rule Collection Group:\\\" RuleCollectionGroup \\\". Rule Collection: \\\" RuleCollection \\\". Rule: \\\" Rule\\r\\n )\\r\\n| summarize Count = count(), last_log = datetime_diff(\\\"second\\\", now(), max(TimeGenerated)) by RuleCollection, Rule, WebCategory\",\"size\":1,\"showAnalytics\":true,\"title\":\"Azure Firewall: Content Enforcement\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Count\",\"formatter\":8,\"formatOptions\":{\"palette\":\"whiteBlack\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"useGrouping\":false,\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"last_log\",\"formatter\":8,\"formatOptions\":{\"palette\":\"greenRed\"},\"numberFormat\":{\"unit\":24,\"options\":{\"style\":\"decimal\",\"useGrouping\":false}}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"$gen_heatmap_last_log_4\",\"sortOrder\":1}]},\"sortBy\":[{\"itemKey\":\"$gen_heatmap_last_log_4\",\"sortOrder\":1}]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 36\"}]},\"conditionalVisibility\":{\"parameterName\":\"isContentVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Content Filtering\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Authenticated Proxy](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAuthenticated proxies require entities to authenticate with the proxy before making use of it, enabling user, group, and location-aware security controls.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Plan an Azure AD Application Proxy Deployment](https://docs.microsoft.com/azure/active-directory/manage-apps/application-proxy-deployment-plan)<br>\\r\\n💡 [Configure Real-Time Application Access Monitoring with Microsoft Defender for Cloud Apps and Microsoft Entra ID](https://docs.microsoft.com/azure/active-directory/manage-apps/application-proxy-integrate-with-microsoft-cloud-application-security)<br>\\r\\n💡 [Protect Apps with Microsoft Defender for Cloud Apps Conditional Access App Control](https://docs.microsoft.com/cloud-app-security/proxy-intro-aad)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Defender for Cloud Apps](https://portal.cloudappsecurity.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| mv-expand ConditionalAccessPolicies\\r\\n| extend ConditionalAccessPolicy = tostring(ConditionalAccessPolicies.displayName)\\r\\n| summarize count() by ConditionalAccessPolicy\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Conditional Access Policies\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ConditionalAccessPolicy\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"pending\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAuthenticatedVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Authenticated Proxy\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Loss Prevention](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData loss prevention technologies detect instances of the exfiltration, either malicious or accidental, of agency data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Microsoft Defender for Cloud Apps: File Policies](https://docs.microsoft.com/cloud-app-security/data-protection-policies)<br>\\r\\n💡 [Content Inspection for Protected Files](https://docs.microsoft.com/cloud-app-security/content-inspection)<br>\\r\\n💡 [How to Configure a Label for Rights Management Protection](https://docs.microsoft.com/azure/information-protection/configure-policy-protection)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Microsoft Defender for Identity Portal](https://portal.atp.azure.com/) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft Defender for Cloud Apps](https://portal.cloudappsecurity.com/) <br>\\r\\n🔀 [Office 365 Security & Compliance Center](https://protection.office.com/) <br>\\r\\n🔀 [Azure Information Protection](https://portal.azure.com/#blade/Microsoft_Azure_InformationProtection/DataClassGroupEditBlade/quickstartBlade) \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Tactics contains \\\"exfil\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Data Exfiltration\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isDataVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Loss Prevention_W\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DNS-over-HTTPS Filtering](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDNS-over-HTTPS filtering prevents entities from using the DNS-over-HTTPS protocol, possibly evading DNS-based protections.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Microsoft Defender for DNS](https://docs.microsoft.com/azure/defender-for-cloud/defender-for-dns-introduction)<br>\\r\\n💡 [Azure Firewall DNS settings](https://docs.microsoft.com/azure/firewall/dns-settings)<br>\\r\\n💡 [Web Content Filtering](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/web-content-filtering)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud: Workload Protections](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/26)<br>\\r\\n🔀 [Azure Firewall](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"dns\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNS-over-HTTPS Filtering\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [RFC Compliance Enforcement](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nRFC compliant enforcement technologies ensure that traffic complies with protocol definitions.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Web Application Firewall]( https://azure.microsoft.com/services/web-application-firewall/) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n\\r\\n### Implementation\\r\\n💡[What is Azure Web Application Firewall on Azure Application Gateway?](https://docs.microsoft.com/azure/web-application-firewall/ag/ag-overview)<br>\\r\\n💡[Tutorial: Create an Application Gateway with a Web Application Firewall using the Azure Portal](https://docs.microsoft.com/azure/web-application-firewall/ag/application-gateway-web-application-firewall-portal)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Web Application Firewall Policies](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers) <br> \\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics \\r\\n| where Category == \\\"ApplicationGatewayFirewallLog\\\"\\r\\n| where details_file_s contains \\\"rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf\\\"\\r\\n| summarize count() by ResourceId, Message\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Web Protocol Enforcement Alerts\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isRFCVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"RFC Compliance Enforcement\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Domain Category Filtering](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDomain category filtering technologies allow for classes of domains (e.g. banking, medical) to receive a different set of security protections.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Firewall: Web Categories](https://docs.microsoft.com/azure/firewall/premium-deploy#web-categories-testing) <br> \\r\\n💡 [Use FQDN Filtering in Network Rules](https://docs.microsoft.com/azure/firewall/fqdn-filtering-network-rules) <br> \\r\\n💡 [Azure Firewall Premium Features](https://docs.microsoft.com/azure/firewall/premium-features) <br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewalls](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls)<br> \\r\\n🔀 [Firewall Manager](https://portal.azure.com/#blade/Microsoft_Azure_HybridNetworking/FirewallManagerMenuBlade/firewallManagerOverview) <br>\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)\\t<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.IP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let materializedData =\\r\\n materialize(\\r\\n AzureDiagnostics\\r\\n | where Category == \\\"AzureFirewallApplicationRule\\\"\\r\\n | project msg_s, Resource, TimeGenerated);\\r\\nunion\\r\\n (\\r\\n materializedData\\r\\n | where msg_s has \\\"Web Category:\\\" and msg_s has \\\". Url\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Url:\\\" Url \\\". Action: \\\" Action \\\". Rule Collection:\\\" RuleCollection \\\". Rule:\\\" Rule \\\". Web Category:\\\" WebCategory\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s has \\\". Url\\\"\\r\\n and msg_s has \\\". No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Url:\\\" Url \\\". Action: \\\" Action \\\". No rule matched\\\" *\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s has \\\". No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". No rule matched\\\" *\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s has \\\"Web Category:\\\" and msg_s !has \\\". Url\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Rule Collection:\\\" RuleCollection \\\". Rule:\\\" Rule \\\". Web Category:\\\" WebCategory\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\" Reason: \\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". \\\" RuleCollection \\\". \\\" Rule\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\"TLS extension was missing\\\"\\r\\n | where msg_s has \\\" Reason:\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\". Action: \\\" Action \\\". Reason: \\\" Rule \\\".\\\"\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"TLS extension was missing\\\"\\r\\n and msg_s !has \\\"No rule matched\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Rule Collection: \\\" RuleCollection \\\". Rule: \\\" Rule\\r\\n ),\\r\\n (\\r\\n materializedData\\r\\n | where msg_s !has \\\"Web Category:\\\"\\r\\n and msg_s !has \\\". Url\\\"\\r\\n and msg_s !has \\\"Rule Collection\\\"\\r\\n and msg_s !has \\\" Reason: \\\"\\r\\n | where msg_s has \\\"Rule Collection Group\\\"\\r\\n | parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". Policy:\\\" Policy \\\". Rule Collection Group:\\\" RuleCollectionGroup \\\". Rule Collection: \\\" RuleCollection \\\". Rule: \\\" Rule\\r\\n )\\r\\n| where Action == \\\"Deny\\\"\\r\\n| where '*' == SourceIP or '*' == \\\"*\\\" \\r\\n| summarize count() by FQDN\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Domain & Category Filtering\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"FQDN\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Diagnostics\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isCategoryVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Domain Category Filtering\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Domain Reputation Filter](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDomain reputation filtering protections are a form of domain denylisting based on a domain’s reputation, as defined by either the agency or an external entity.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Firewall Threat Intelligence-Based Filtering](https://docs.microsoft.com/azure/firewall/threat-intel)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewalls](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls) <br>\\r\\n🔀 [Firewall Manager](https://portal.azure.com/#blade/Microsoft_Azure_HybridNetworking/FirewallManagerMenuBlade/firewallManagerOverview) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let materializedData =\\r\\nmaterialize(\\r\\nAzureDiagnostics\\r\\n| where Category == \\\"AzureFirewallNetworkRule\\\"\\r\\n| where OperationName == \\\"AzureFirewallThreatIntelLog\\\"\\r\\n| where msg_s <> \\\" request from to . Action: . ThreatIntel: \\\"\\r\\n| project msg_s, Resource, TimeGenerated,ResourceId , ResourceGroup , SubscriptionId);\\r\\nunion\\r\\n(\\r\\nmaterializedData\\r\\n| where msg_s has \\\"Url\\\"\\r\\n| parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Url: \\\" Url \\\". Action: \\\" Action \\\". ThreatIntel: \\\" ThreatIntelMsg\\r\\n),\\r\\n(\\r\\nmaterializedData\\r\\n| where msg_s !has \\\"Url\\\"\\r\\n| parse msg_s with Protocol \\\" request from \\\" SourceIP \\\":\\\" SourcePort \\\" to \\\" FQDN \\\":\\\" DestinationPort \\\". Action: \\\" Action \\\". ThreatIntel: \\\" ThreatIntelMsg\\r\\n)\\r\\n| summarize by ThreatIntelMsg, Url, FQDN, Action, Protocol, SourceIP, SourcePort, DestinationPort, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Azure Firewall: Threat Intelligence URL Blocks\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Url\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Diagnostics\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Action\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"4\",\"text\":\"{0}{1}\"}]}}],\"filter\":true,\"sortBy\":[{\"itemKey\":\"FQDN\",\"sortOrder\":1}]},\"sortBy\":[{\"itemKey\":\"FQDN\",\"sortOrder\":1}]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isReputationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Domain Reputation Filter\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Bandwidth Control](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nBandwidth control technologies allow for limiting the amount of bandwidth used by different classes of domains.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [Metrics](https://docs.microsoft.com/azure/azure-monitor/essentials/data-platform-metrics) ✳️ [Azure Firewall](https://azure.microsoft.com/services/azure-firewall/)\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Monitor Metrics Overview](https://docs.microsoft.com/azure/azure-monitor/essentials/data-platform-metrics)<br>\\r\\n💡 [Monitor Azure Firewall Logs and Metrics](https://docs.microsoft.com/azure/firewall/firewall-diagnostics) \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewalls](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls) <br>\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"Bandwidth Control\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"40\",\"name\":\"Control Smartcard\"},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"5084e141-6c56-4d7f-bd8a-09f7ef9af1bc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"Resource\",\"label\":\"Azure Firewalls\",\"type\":5,\"isRequired\":true,\"multiSelect\":true,\"quote\":\"'\",\"delimiter\":\",\",\"query\":\"where type =~ 'Microsoft.Network/azureFirewalls'\\r\\n| project id, name\",\"crossComponentResources\":[\"{Workspace}\"],\"typeSettings\":{\"additionalResourceOptions\":[\"value::all\"]},\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"value\":[\"value::all\"]}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"20\",\"name\":\"parameters - 1\"},{\"type\":10,\"content\":{\"chartId\":\"workbook76864ed5-dd34-42d0-ae35-f3db9f9e8f15\",\"version\":\"MetricsItem/2.0\",\"size\":0,\"chartType\":2,\"resourceType\":\"microsoft.network/azurefirewalls\",\"metricScope\":0,\"resourceParameter\":\"Resource\",\"resourceIds\":[\"{Resource}\"],\"timeContextFromParameter\":\"TimeRange\",\"timeContext\":{\"durationMs\":604800000},\"metrics\":[{\"namespace\":\"microsoft.network/azurefirewalls\",\"metric\":\"microsoft.network/azurefirewalls--Throughput\",\"aggregation\":4,\"columnName\":\"All Firewall Throughput Average\"}],\"title\":\"Average Throughput of Firewall Traffic\",\"gridSettings\":{\"rowLimit\":10000}},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"metric - 25\"}]},\"conditionalVisibility\":{\"parameterName\":\"isBandwidthVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Bandwidth Control\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Malicious Content Filtering](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMalicious content filtering protections detect the presence of malicious content and facilitate its removal.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) ✳️ [Azure Web Application Firewall](https://azure.microsoft.com/services/web-application-firewall/)\\r\\n\\r\\n### Implementation \\r\\n💡 [Microsoft Defender for Cloud's enhanced security features](https://docs.microsoft.com/azure/defender-for-cloud/enhanced-security-features-overview)<br>\\r\\n💡 [What is Azure Web Application Firewall on Azure Application Gateway?](https://docs.microsoft.com/azure/web-application-firewall/ag/ag-overview)<br>\\r\\n💡 [Azure Web Application Firewall on Azure Front Door](https://docs.microsoft.com/azure/web-application-firewall/afds/afds-overview)<br>\\r\\n💡 [Azure Firewall Premium Features](https://docs.microsoft.com/azure/firewall/premium-features) <br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)<br>\\r\\n🔀 [Web Application Firewall Policies](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS, PR.PT, PR.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"firewall\\\" or RecommendationDisplayName contains \\\"defender\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"mal\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Malicious Content\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let materializedData =\\r\\nmaterialize(\\r\\nAzureDiagnostics\\r\\n| where ResourceType == \\\"AZUREFIREWALLS\\\"\\r\\n| project Category, ResourceType, OperationName);\\r\\nunion\\r\\n(\\r\\nmaterializedData\\r\\n | where OperationName == \\\"AzureFirewallIDSLog\\\"\\r\\n | summarize Volume=count() by OperationName\\r\\n | project Category=OperationName, Volume\\r\\n),\\r\\n(\\r\\nmaterializedData\\r\\n | where OperationName == \\\"AzureFirewallThreatIntelLog\\\"\\r\\n | summarize Volume=count() by OperationName\\r\\n | project Category=OperationName, Volume\\r\\n),\\r\\n(\\r\\nmaterializedData\\r\\n | where OperationName <> \\\"AzureFirewallThreatIntelLog\\\"\\r\\n | where OperationName <> \\\"AzureFirewallIDSLog\\\"\\r\\n | summarize Volume=count() by Category\\r\\n)\\r\\n| sort by Volume desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Web Protections by Rule Category\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"noDataMessageStyle\":4,\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"exportFieldName\":\"Category\",\"exportParameterName\":\"SelectedCategory\",\"exportDefaultValue\":\"*\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Volume\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true},\"tileSettings\":{\"showBorder\":false,\"titleContent\":{\"columnMatch\":\"Category\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Volume\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"maximumSignificantDigits\":3,\"maximumFractionDigits\":2}}}}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 2\"}]},\"conditionalVisibility\":{\"parameterName\":\"isMaliciousVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Malicious Content Filtering\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Access Control](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAccess control technologies allow an agency to define policies limiting what actions may be performed by connected users and entities.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Overview of Role-Based Access Control in Microsoft Entra ID](https://docs.microsoft.com/azure/active-directory/roles/custom-overview)<br>\\r\\n💡 [What is Azure AD Privileged Identity Management?](https://docs.microsoft.com/azure/active-directory/privileged-identity-management/pim-configure)<br>\\r\\n💡 [Secure Your Management Ports With Just-In-Time Access](https://docs.microsoft.com/azure/active-directory/privileged-identity-management/pim-configure)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Privileged Identity Management](https://portal.azure.com/#blade/Microsoft_Azure_PIMCommon/CommonMenuBlade/quickStart) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"Just\\\" or RecommendationDisplayName contains \\\"privilege\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAccessVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Access Control\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isWebVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Web Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Networking](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nNetwork-based protections including network access controls, IP denylisting, host containment, network segmentation, and microsegmentation. \\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Networking Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 109\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Access Control\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Access\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"IP Denylisting\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"IP\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Host Containment\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Host\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Network Segmentation\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Network\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Microsegmentation\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Micro\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAccessVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Access\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIPVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"IP\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"50ab20f8-9e71-4938-a67c-fc3cddda9d3e\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isHostVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Host\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"297ab54c-7fb4-4d69-b331-d06b5848b0c2\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isNetworkVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Network\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"4c49d950-1bd2-45c1-8a98-4f17abff2088\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isMicroVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Micro\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"cf2d16a5-def7-4887-87ff-188258574464\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Access Control](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAccess control protections prevent the ingest, egress, or transiting of unauthorized network traffic.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n✳️ [Virtual Network](https://azure.microsoft.com/services/virtual-network/)\\r\\n✳️ [Azure Web Application Firewall](https://azure.microsoft.com/services/web-application-firewall/)\\r\\n\\r\\n### Implementation \\r\\n💡 [Security Recommendations in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/security-center-recommendations)<br>\\r\\n💡 [Network Security Groups](https://docs.microsoft.com/azure/virtual-network/network-security-groups-overview)<br>\\r\\n💡 [Tutorial: Deploy and Configure Azure Firewall Using the Azure Portal](https://docs.microsoft.com/azure/firewall/tutorial-firewall-deploy-portal)<br>\\r\\n💡 [Tutorial: Create an Application Gateway with a Web Application Firewall using the Azure Portal](https://docs.microsoft.com/azure/web-application-firewall/ag/application-gateway-web-application-firewall-portal)<br>\\r\\n💡 [Tutorial: Create and Manage a VPN Gateway using Azure Portal]( https://docs.microsoft.com/azure/vpn-gateway/tutorial-create-gateway-portal)<br>\\r\\n💡 [What is Azure ExpressRoute?](https://docs.microsoft.com/azure/expressroute/expressroute-introduction)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br> 🔀 [Network Security Groups](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FNetworkSecurityGroups)<br> 🔀 [Firewalls](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FazureFirewalls) <br>🔀 [Web Application Firewall Policies](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers) <br>🔀 [Virtual Network Gateways](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FvirtualNetworkGateways)<br> 🔀 [ExpressRoute Circuits](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FexpressRouteCircuits) \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.IP, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"network access\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"network\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Networking Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics\\r\\n| where OperationName == \\\"NetworkSecurityGroupEvents\\\"\\r\\n| extend NetworkMap=strcat(\\\"NetworkMap\\\")\\r\\n| summarize count() by ruleName_s, NetworkMap\\r\\n| project NetworkSecurityGroupRule=ruleName_s, FlowCount=count_, NetworkMap\\r\\n| sort by FlowCount desc \",\"size\":0,\"showAnalytics\":true,\"title\":\"Network Map & Flow Counts\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"NetworkSecurityGroupRule\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Lateral_Movement\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"FlowCount\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"NetworkMap\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Network Map >>\",\"bladeOpenContext\":{\"bladeName\":\"NetworkMapBlade\",\"extensionName\":\"Microsoft_Azure_Security_R3\"}}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 4\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAccessVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Access Control\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [IP Denylisting](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nIP denylisting protections prevent the ingest or transiting of traffic received from or destined to a denylisted IP address.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [ThreatIntelligenceIndicator](https://docs.microsoft.com/azure/azure-monitor/reference/tables/threatintelligenceindicator) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/)<br>\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Connect Data from Threat Intelligence Providers](https://docs.microsoft.com/azure/sentinel/connect-threat-intelligence)<br>\\r\\n💡 [Azure Firewall Threat Intelligence Configuration](https://docs.microsoft.com/azure/firewall-Manager/threat-intelligence-settings)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Firewall Manager](https://portal.azure.com/#blade/Microsoft_Azure_HybridNetworking/FirewallManagerMenuBlade/firewallManagerOverview) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"ThreatIntelligenceIndicator\\r\\n| extend IndicatorType = iif(isnotempty(EmailSourceIpAddress) or isnotempty(NetworkDestinationIP) or isnotempty(NetworkIP) or isnotempty(NetworkSourceIP) or isnotempty(NetworkCidrBlock), \\\"IP\\\",\\r\\n\\t iff(isnotempty(Url), \\\"URL\\\",\\r\\n\\t iff(isnotempty(EmailRecipient) or isnotempty(EmailSenderAddress), \\\"Email\\\",\\r\\n\\t iff(isnotempty(FileHashValue), \\\"File\\\",\\r\\n\\t iff(isnotempty(DomainName) or isnotempty(EmailSourceDomain), \\\"Domain\\\",\\r\\n\\t \\\"Other\\\")))))\\r\\n| where IndicatorType == \\\"IP\\\"\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by IndicatorType\\r\\n| render areachart\",\"size\":0,\"showAnalytics\":true,\"title\":\"Microsoft Sentinel: Threat Intelligence IP Indicators Ingested\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"VMConnection\\r\\n| extend NetworkSourceIP=RemoteIp\\r\\n| where NetworkSourceIP <> \\\"\\\"\\r\\n| extend FirewallManager=strcat(\\\"FirewallManager\\\")\\r\\n| join (ThreatIntelligenceIndicator) on NetworkSourceIP\\r\\n| extend Indicator = strcat(NetworkSourceIP, FileHashValue, NetworkIP, NetworkDestinationIP, Url, EmailSourceIpAddress, EmailSenderAddress, DomainName)\\r\\n| extend Source=SourceSystem1\\r\\n| summarize count () by ThreatType, Action, Indicator, Direction, _ResourceId, FirewallManager, RemoteCountry, RemoteIp, Source\\r\\n| sort by count_ desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Threat Intelligence: IP Denylisting\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"table\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"ThreatType\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"FirewallManager\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Go to Firewall Manager >>\",\"bladeOpenContext\":{\"bladeName\":\"FirewallManagerMenuBlade\",\"extensionName\":\"Microsoft_Azure_HybridNetworking\"}}},{\"columnMatch\":\"RemoteCountry\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Globe\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Source\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"View\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"RiskIQ_Lookup\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"RiskIQ Lookup >\"}},{\"columnMatch\":\"VirusTotalURL\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"VirusTotal Lookup >\"}}],\"filter\":true},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"RemoteCountry\",\"latitude\":\"RemoteLatitude\",\"longitude\":\"RemoteLongitude\",\"sizeSettings\":\"RemoteCountry\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"RemoteCountry\",\"legendMetric\":\"RemoteCountry\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"RemoteIp\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"redBright\"}]}}},\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Threat Intelligence: IP Denylisting\"}]},\"conditionalVisibility\":{\"parameterName\":\"isIPVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"IP Denylisting\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Host Containment](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nHost containment protections enable a network to revoke or quarantine a host’s access to the network.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Security Orchestration, Automation, and Response (SOAR) in Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/automation-in-azure-sentinel)<br>\\r\\n💡 [How to Isolate an Azure VM Using Microsoft Defender for Cloud’s Workflow Automation](https://techcommunity.microsoft.com/t5/azure-security-center/how-to-isolate-an-azure-vm-using-azure-security-center-s/ba-p/1250985)<br>\\r\\n💡 [Isolate Endpoints from the Network](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/respond-machine-alerts#isolate-endpoints-from-the-network)<br>\\r\\n\\r\\n### Microsoft Portals \\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.IP, PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"logic\\\"\\r\\n| where id contains \\\"block\\\" or id contains \\\"isolate\\\" or id contains \\\"lock\\\" or id contains \\\"revoke\\\" or id contains \\\"quarantine\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Containment Automations Configured\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isHostVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Host Containment\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Network Segmentation](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nNetwork segmentation separates a given network into subnetworks, facilitating security controls between the subnetworks, and decreasing the attack surface of the network.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Virtual Network](https://azure.microsoft.com/services/virtual-network/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Implement Network Segmentation Patterns on Azure](https://docs.microsoft.com/azure/architecture/framework/security/design-network-segmentation)<br>\\r\\n💡 [What is Azure Virtual Network?](https://docs.microsoft.com/azure/virtual-network/virtual-networks-overview)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Virtual Networks](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworks) <br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"segment\\\" or RecommendationDisplayName contains \\\"network security group\\\" or RecommendationDisplayName contains \\\"subnet\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"networksecuritygroups\\\" or type contains \\\"virtualnetworks\\\" or type contains \\\"tables\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Network Segmentation Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isNetworkVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Network Segmentation\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Microsegmentation](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMicrosegmentation divides the network, either physically or virtually, according to the communication needs of application and data workflows, facilitating security controls to protect the data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Virtual Network](https://azure.microsoft.com/services/virtual-network/)\\r\\n✳️ [Application Gateway](https://azure.microsoft.com/services/application-gateway/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Network Security & Containment](https://docs.microsoft.com/azure/virtual-network/virtual-networks-overview)<br>\\r\\n💡 [What is Azure Virtual Network?](https://docs.microsoft.com/azure/virtual-network/virtual-networks-overview)<br>\\r\\n💡 [Implement network segmentation patterns on Azure](https://docs.microsoft.com/azure/architecture/framework/security/design-network-segmentation)<br>\\r\\n💡 [Application Security Groups](https://docs.microsoft.com/azure/virtual-network/application-security-groups)<br>\\r\\n💡 [Tutorial: Filter Network Traffic with a Network Security Group using the Azure portal](https://docs.microsoft.com/azure/virtual-network/tutorial-filter-network-traffic)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Application Security Groups](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworks) <br>\\r\\n🔀 [Network Security Groups](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FNetworkSecurityGroups) <br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.DS, PR.IP, PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"application gateway\\\" or RecommendationDisplayName contains \\\"security group\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"applicationgateway\\\" or type contains \\\"securitygroup\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Microsegementation Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isMicroVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Microsegmentation\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isNetworkingVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Networking Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Resiliency](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nResiliency measures including DDoS protections, elastic expansion, and regional delivery.\\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Resiliency Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 110\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DDoS Protections\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"DDoS\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Elastic Expansion\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Elastic\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Regional Delivery\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Regional\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDDoSVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"DDoS\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isElasticVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Elastic\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"c6997d7f-b3e5-431c-b747-ea5a75b533e0\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isRegionalVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Regional\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"250d293f-5d5f-4944-8cd4-5ec0183b9053\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DDoS Protections](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDDoS protections mitigate the effects of distributed denial of service attacks.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) 🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure DDoS Protection]( https://azure.microsoft.com/services/ddos-protection/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure DDoS Protection Standard Overview](https://docs.microsoft.com/azure/ddos-protection/ddos-protection-overview)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [DDoS Protection Plans](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FddosProtectionPlans) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"dos\\\" or Title contains \\\"denial\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: DDoS\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"Resources\\r\\n| where type contains \\\"microsoft.network/ddosprotectionplans\\\"\\r\\n| extend RG = substring(id, 0, indexof(id, '/providers'))\\r\\n| extend virtualNetworks = properties.virtualNetworks\\r\\n| mvexpand bagexpansion=array virtualNetworks\\r\\n| extend VNETid = virtualNetworks.id\\r\\n| project-away kind, managedBy, sku, plan, identity, zones, extendedLocation, name, tenantId, properties, tags, virtualNetworks, resourceGroup\",\"size\":0,\"showAnalytics\":true,\"title\":\"DDoS Protection Plans\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Subscription}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"type\",\"formatter\":16,\"formatOptions\":{\"showIcon\":true}},{\"columnMatch\":\"location\",\"formatter\":17},{\"columnMatch\":\"subscriptionId\",\"formatter\":15,\"formatOptions\":{\"showIcon\":true}},{\"columnMatch\":\"VNETid\",\"formatter\":13,\"formatOptions\":{\"showIcon\":true}}],\"filter\":true,\"labelSettings\":[{\"columnId\":\"id\",\"label\":\"Name\"},{\"columnId\":\"type\",\"label\":\"Type\"},{\"columnId\":\"location\",\"label\":\"Region\"},{\"columnId\":\"subscriptionId\",\"label\":\"Subscription\"},{\"columnId\":\"VNETid\",\"label\":\"Virtual Networks\"}]}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DDoSPlans\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"DDoSMitigationReports\\\"\\r\\n| sort by TimeGenerated desc\\r\\n| extend TopAttackVector = tostring(parse_json(AttackVectors_s)[0]) \\r\\n| extend Total_packets_ = tostring(parse_json(TrafficOverview_s).Total_packets) \\r\\n| extend Total_packets_dropped_ = todouble(parse_json(TrafficOverview_s).Total_packets_dropped)\\r\\n| extend TotalPackets =todouble(Total_packets_)\\r\\n| where TotalPackets > 0\\r\\n| where TopAttackVector <> \\\"\\\"\\r\\n| project TopAttackVector, TotalPackets, TotalPacketsDropped = Total_packets_dropped_ , ResourceId , SourceIP=IPAddress, Resource, TimeGenerated\\r\\n| sort by TotalPacketsDropped desc\\r\\n| limit 100\\r\\n\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"DDoS Mitigation Activity\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"exportedParameters\":[{\"fieldName\":\"IPAddress\",\"parameterName\":\"IPAddress\",\"parameterType\":1},{\"fieldName\":\"ResourceId\",\"parameterName\":\"ResourceId\",\"parameterType\":1,\"defaultValue\":\"ResourceId\"},{\"fieldName\":\"Resource\",\"parameterName\":\"AttackReport\",\"parameterType\":1,\"defaultValue\":\"/\"}],\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"TopAttackVector\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"TotalPackets\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"TotalPacketsDropped\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"Resource\",\"formatter\":5},{\"columnMatch\":\"Total_packets_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}},{\"columnMatch\":\"Total_packets_dropped_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumSignificantDigits\":4}}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"IPAddress\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"}},\"subtitleContent\":{\"columnMatch\":\"TopAttackVector\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Resource\"},\"rightContent\":{\"columnMatch\":\"TimeGenerated\"},\"showBorder\":true,\"size\":\"auto\"}},\"customWidth\":\"50\",\"name\":\"query - 4\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDDoSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DDoS Protections\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Elastic Expansion](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nElastic expansion enables agencies to dynamically expand the resources available for services as conditions require.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure Virtual Machine Scale Sets](https://azure.microsoft.com/services/virtual-machine-scale-sets/) ✳️ [Traffic Manager]( https://azure.microsoft.com/services/traffic-manager/) ✳️ [Load Balancer]( https://azure.microsoft.com/services/load-balancer/) ✳️ [Azure Availability Zones]( https://azure.microsoft.com/global-infrastructure/availability-zones/)\\r\\n\\r\\n### Implementation \\r\\n💡 [What are Virtual Machine Scale Sets?](https://docs.microsoft.com/azure/virtual-machine-scale-sets/overview) <br>\\r\\n💡 [Elastic Pools Help You Manage and Scale Multiple Databases in Azure SQL Database](https://www.cisa.gov/trusted-internet-connections)<br>\\r\\n💡 [What is Azure Load Balancer?](https://docs.microsoft.com/azure/load-balancer/load-balancer-overview)<br>\\r\\n💡 [What is Traffic Manager?](https://docs.microsoft.com/azure/traffic-Manager/traffic-Manager-overview)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Virtual Machine Scale Sets](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Compute%2FvirtualMachineScaleSets)<br> 🔀 [Azure SQL](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Sql%2Fazuresql)<br> 🔀 [Load Balancer](https://portal.azure.com/#blade/Microsoft_Azure_Network/LoadBalancingHubMenuBlade/loadBalancers)<br> 🔀 [Traffic Manager Profiles](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2Ftrafficmanagerprofiles)<br> 🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"load\\\" or Description contains \\\"scale\\\" or Description contains \\\"front\\\" or Description contains \\\"traffic manager\\\" or Description contains \\\"pool\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":12531600000,\"endTime\":\"2022-02-23T15:45:00Z\"},\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"scale\\\" or type contains \\\"traffic\\\" or type contains \\\"load\\\" or type contains \\\"balance\\\" or type contains \\\"pool\\\" or type contains \\\"set\\\" or type contains \\\"manager\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Elastic Expansion Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isElasticVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Elastic Expansion\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Regional Delivery](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nRegional delivery technologies enable the deployment of agency services across geographically diverse locations.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter)\\r\\n\\r\\n### Implementation \\r\\n💡 [Building Solutions for High Availability Using Availability Zones](https://docs.microsoft.com/azure/architecture/high-availability/building-solutions-for-high-availability)<br> \\r\\n💡 [Azure Infrastructure Availability](https://docs.microsoft.com/azure/security/fundamentals/infrastructure-availability) <br>\\r\\n💡 [Data residency in Azure](https://azure.microsoft.com/global-infrastructure/data-residency/#overview) <br>\\r\\n💡 [Regions and availability zones](https://docs.microsoft.com/azure/availability-zones/az-overview) <br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Availability Sets](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Compute%2FavailabilitySets) <br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.AC, PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"disaster\\\" or RecommendationDisplayName contains \\\"region\\\" or RecommendationDisplayName contains \\\"redundant\\\" or RecommendationDisplayName contains \\\"geo\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":12531600000,\"endTime\":\"2022-02-23T15:45:00Z\"},\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| where ResultType == 0\",\"size\":0,\"showAnalytics\":true,\"title\":\"Sign-Ins By Location\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":0},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"map\",\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"Location\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"greenRed\"}}},\"customWidth\":\"50\",\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| project id,type,location,resourceGroup\\r\\n| summarize count() by location\\r\\n| sort by count_ desc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Assets by Location\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"location\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Globe\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isRegionalVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Regional Delivery\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isResiliencyVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Resiliency Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DNS](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nDNS measures including DNS blackholing, DNSSEC for clients, and DNSSEC for domains. \\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNS Capability Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 111\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DNS Sinkholing\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Sink\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DNSSEC for Agency Clients\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Clients\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"DNSSEC for Agency Domains\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Domains\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isSinkVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Sink\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"aaf5f338-70e7-4910-8b24-0256c3e819ab\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isClientsVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Clients\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDomainsVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Domains\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b454a300-8718-4f34-a5e9-722b582dc95d\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DNS Sinkholing](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDNS sinkholing protections are a form of denylisting that protect clients from accessing malicious domains by responding to DNS queries for those domains.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Azure DNS](https://azure.microsoft.com/services/dns/) \\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [What is Azure DNS?](https://docs.microsoft.com/azure/dns/dns-overview)<br>\\r\\n💡 [How to protect DNS zones and records](https://docs.microsoft.com/azure/dns/dns-protect-zones-recordsets)<br>\\r\\n💡 [Microsoft Defender for DNS](https://docs.microsoft.com/azure/defender-for-cloud/defender-for-dns-introduction)<br>\\r\\n💡 [Azure Firewall DNS settings](https://docs.microsoft.com/azure/firewall/dns-settings)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [DNS Zones](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FdnsZones)<br> 🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies)<br>🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"domain\\\" or type contains \\\"dns\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"DNS Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"dns\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: DNS\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isSinkVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNS Sinkholing\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DNSSEC for Agency Clients](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDNSSEC protections ensure that domain name lookups from agency clients, whether for internal or external domains, are validated.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityBaselines](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securitybaseline) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/) \\r\\n\\r\\n### Implementation \\r\\n💡 [Enabling Central Visibility For DNS Using Azure Firewall Custom DNS and DNS Proxy](https://techcommunity.microsoft.com/t5/azure-network-security/enabling-central-visibility-for-dns-using-azure-firewall-custom/ba-p/2156331)<br>\\r\\n💡 [DANE Support](https://docs.microsoft.com/windows-server/networking/dns/what-s-new-in-dns-server#dane-support)<br>\\r\\n💡 [Support of DANE and DNSSEC in Office 365 Exchange Online](https://techcommunity.microsoft.com/t5/exchange-team-blog/support-of-dane-and-dnssec-in-office-365-exchange-online/ba-p/1275494)<br>\\r\\n💡 [Apply Azure security baselines to machines](https://docs.microsoft.com/azure/defender-for-cloud/apply-security-baseline)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [DNS zones](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FdnsZones)<br>\\r\\n🔀 [Firewall Manager](https://portal.azure.com/#blade/Microsoft_Azure_HybridNetworking/FirewallManagerMenuBlade/firewallManagerOverview) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let FailedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"dns\\\"\\r\\n| where AnalyzeResult == \\\"Failed\\\"\\r\\n| summarize FailedAssets = makelist(Computer) by Description;\\r\\nlet PassedAssets=SecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"dns\\\"\\r\\n| where AnalyzeResult == \\\"Passed\\\"\\r\\n| summarize PassedAssets = makelist(Computer) by Description;\\r\\nSecurityBaseline\\r\\n| summarize arg_max(TimeGenerated, *) by _ResourceId, Description\\r\\n| where Description contains \\\"dns\\\"\\r\\n| summarize\\r\\n Failed = countif(AnalyzeResult == \\\"Failed\\\"),\\r\\n Passed = countif(AnalyzeResult == \\\"Passed\\\"),\\r\\n Total = countif(AnalyzeResult == \\\"Failed\\\" or AnalyzeResult == \\\"Passed\\\")\\r\\n by Description\\r\\n| extend PassedControls = (Passed / todouble(Total)) * 100\\r\\n| join kind=fullouter(FailedAssets) on Description\\r\\n| join kind=fullouter(PassedAssets) on Description\\r\\n| project Description, Total, PassedControls, Passed, Failed, PassedAssets, FailedAssets\\r\\n| sort by Total, Passed desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Security Baselines\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationDisplayName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2}}},{\"columnMatch\":\"ControlNumber\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"AllServices\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"RecommendationState\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"!=\",\"thresholdValue\":\"Healthy\",\"representation\":\"3\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"success\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"AzureFirewallDnsProxy\\\"\\r\\n| parse msg_s with \\\"DNS Request: \\\" ClientIP \\\":\\\" ClientPort \\\" - \\\" QueryID \\\" \\\" Request_Type \\\" \\\" Request_Class \\\" \\\" Request_Name \\\". \\\" Request_Protocol \\\" \\\" Request_Size \\\" \\\" EDNSO_DO \\\" \\\" EDNS0_Buffersize \\\" \\\" Responce_Code \\\" \\\" Responce_Flags \\\" \\\" Responce_Size \\\" \\\" Response_Duration\\r\\n| project-away msg_s\\r\\n| summarize by TimeGenerated, ResourceId, ClientIP, ClientPort, QueryID, Request_Type, Request_Class, Request_Name, Request_Protocol, Request_Size, EDNSO_DO, EDNS0_Buffersize, Responce_Code, Responce_Flags, Responce_Size, Response_Duration, SubscriptionId\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by Request_Type\\r\\n| render areachart \",\"size\":0,\"showAnalytics\":true,\"title\":\"Azure Firewall: DNS Proxy Actions over Time\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":604800000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 2\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isClientsVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNSSEC for Agency Clients\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [DNSSEC for Agency Domains](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDNSSEC protections ensure that all agency domain names are secured using DNSSEC, enabling external entities to validate their resolution the domain names.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [What is Azure DNS?](https://docs.microsoft.com/azure/dns/dns-overview)<br>\\r\\n💡 [Security Recommendations in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/security-center-recommendations)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [DNS Zones](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FdnsZones) <br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"dns\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":12531600000,\"endTime\":\"2022-02-23T15:45:00Z\"},\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isDomainsVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNSSEC for Agency Domains\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isDNSVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"DNS Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Intrusion Detection](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nIntrusion Detection measures including endpoint detection & response, intrusion protection systems, adaptive access control, deception platforms, and certificate transparency log monitoring.\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Intrusion Detection Capability Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 112\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Endpoint Detection and Response\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Endpoint\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Intrusion Protection Systems (IPS)\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Intrusion\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Adaptive Access Control\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Adaptive\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Deception Platforms\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Deception\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Certificate Transparency Log Monitoring\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Certificate\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEndpointVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Endpoint\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIntrusionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Intrusion\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"f683c8d4-894a-4863-a2c6-03d36d6d7819\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAdaptiveVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Adaptive\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"27dcffa8-43ca-4d68-b69d-11dbd33dcbcb\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDeceptionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Deception\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b4f96879-69b4-45b3-b6a6-384a91e9569c\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isCertificateVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Certificate\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"51c9fd25-2fa3-4cca-bc9f-bf8b5d0a0e07\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Endpoint Detection and Response](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nEndpoint detection and response tools combine endpoint and network event data to aid in the detection of malicious activity.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Overview of Endpoint Detection and Response](https://docs.microsoft.com/windows/security/threat-protection/microsoft-defender-atp/overview-endpoint-detection-response)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/)<br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[DE.AE, DE.CM, RS.AN](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"endpoint protection\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":12531600000,\"endTime\":\"2022-02-23T15:45:00Z\"},\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| where AdditionalData contains \\\"Microsoft Defender for Endpoint\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Endpoint Detection & Response\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isEndpointVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Endpoint Detection and Response\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Intrusion Protection Systems (IPS)](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nIntrusion protection systems detect malicious activity, attempt to stop the activity, and report the activity.\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Firewall Premium: IPS](https://docs.microsoft.com/azure/firewall/premium-features#idps)<br>\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [AzureDiagnostics](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azurediagnostics) 🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter ✳️ [Azure Firewall]( https://azure.microsoft.com/services/azure-firewall/)\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Firewall Policies](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FfirewallPolicies) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[DE.AE, DE.CM, DE.DP, RS.AN](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"IPS\\\" or Title contains \\\"IDS\\\" or Title contains \\\"intrusion\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Intrusion Protection System\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureDiagnostics\\r\\n| where Category == \\\"AzureFirewallNetworkRule\\\"\\r\\n| where OperationName == \\\"AzureFirewallIDSLog\\\"\\r\\n| parse msg_s with * \\\"TCP request from \\\" Source \\\" to \\\" Destination \\\". Action: \\\" ActionTaken \\\". Rule: \\\" IDPSSig \\\". IDS: \\\" IDSMessage \\\". Priority: \\\" Priority \\\". Classification: \\\" Classification\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by OperationName\\r\\n| render areachart \",\"size\":0,\"showAnalytics\":true,\"title\":\"Azure Firewall: IDPS Alerts over Time\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"]},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"microsoft.network/firewallpolicies\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"IPS Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"}]},\"conditionalVisibility\":{\"parameterName\":\"isIntrusionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Intrusion Protection Systems (IPS)\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Adaptive Access Control](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAdaptive access control technologies factor in additional context, like security risk, operational needs, and other heuristics, when evaluating access control decisions.\\r\\n\\r\\n### Microsoft Reference \\r\\n💡 [What is Conditional Access?](https://docs.microsoft.com/azure/active-directory/conditional-access/overview)<br>\\r\\n💡 [Use adaptive application controls to reduce your machines' attack surfaces](https://docs.microsoft.com/Azure/defender-for-cloud/adaptive-application-controls)<br>\\r\\n💡 [Improve your network security posture with adaptive network hardening](https://docs.microsoft.com/Azure/defender-for-cloud/adaptive-application-controls)<br>\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud: Workload Protections](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/26)<br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"adaptive\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Continuous Log Export to this workspace for SecurityRecommendations is enabled. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":12531600000,\"endTime\":\"2022-02-23T15:45:00Z\"},\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let data = SigninLogs\\r\\n | where AppDisplayName in ('*') or '*' in ('*')\\r\\n | where UserDisplayName in ('*') or '*' in ('*')\\r\\n | extend CAStatus = case(ConditionalAccessStatus == \\\"success\\\", \\\"Successful\\\",\\r\\n ConditionalAccessStatus == \\\"failure\\\", \\\"Failed\\\", \\r\\n ConditionalAccessStatus == \\\"notApplied\\\", \\\"Not applied\\\", \\r\\n isempty(ConditionalAccessStatus), \\\"Not applied\\\", \\r\\n \\\"Disabled\\\")\\r\\n | mvexpand ConditionalAccessPolicies\\r\\n | extend CAGrantControlName = tostring(ConditionalAccessPolicies.enforcedGrantControls[0])\\r\\n | extend CAGrantControl = case(CAGrantControlName contains \\\"MFA\\\", \\\"Require MFA\\\", \\r\\n CAGrantControlName contains \\\"Terms of Use\\\", \\\"Require Terms of Use\\\", \\r\\n CAGrantControlName contains \\\"Privacy\\\", \\\"Require Privacy Statement\\\", \\r\\n CAGrantControlName contains \\\"endpoint\\\", \\\"Require endpoint Compliant\\\", \\r\\n CAGrantControlName contains \\\"Azure AD Joined\\\", \\\"Require Hybird Azure AD Joined endpoint\\\", \\r\\n CAGrantControlName contains \\\"Apps\\\", \\\"Require Approved Apps\\\",\\r\\n \\\"Other\\\");\\r\\ndata\\r\\n| summarize Count = dcount(Id) by CAStatus\\r\\n| join kind = inner (data\\r\\n | make-series Trend = dcount(Id) default = 0 on TimeGenerated in range(ago(14d), now(), 6h) by CAStatus\\r\\n )\\r\\n on CAStatus\\r\\n| project-away CAStatus1, TimeGenerated\\r\\n| order by Count desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Conditional Access Status\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"tiles\",\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"CAStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"blue\"}},\"showBorder\":false}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3 - Copy\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isAdaptiveVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Adaptive Access Control\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Deception Platforms](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nDeception platform technologies provide decoy environments, from individual machines to entire networks, that can be used to deflect attacks away from the operational systems supporting agency missions/business functions.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) ✳️ [Key Vault](https://azure.microsoft.com/services/key-vault/)<br> \\r\\n\\r\\n### Microsoft Reference \\r\\n💡 [Microsoft Sentinel Deception Solution](https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/what-s-new-microsoft-sentinel-deception-solution/ba-p/2904945)<br>\\r\\n💡 [Deploy and monitor Azure Key Vault honeytokens with Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/monitor-key-vault-honeytokens?tabs=deploy-at-scale)<br>\\r\\n💡 [Manage Sensitive or Honeytoken Accounts](https://docs.microsoft.com/defender-for-identity/manage-sensitive-honeytoken-accounts)<br>\\r\\n\\r\\n### Microsoft Portal\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n🔀 [Microsoft Defender for Identity](https://portal.atp.azure.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, DE.AE, RS.AN](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where id contains \\\"deception\\\" or id contains \\\"honey\\\" or id contains \\\"HTDK\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Deception Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Title contains \\\"honeytoken\\\" or Title contains \\\"deception\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Deception\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"honey\\\" or RecommendationDisplayName contains \\\"deception\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isDeceptionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Deception Platforms\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Certificate Transparency Log Monitoring](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCertificate transparency log monitoring allows agencies to discover when new certificates are issued for agency domains.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Key Vault](https://azure.microsoft.com/services/key-vault/) <br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Get Started with Key Vault Certificates](https://docs.microsoft.com/azure/key-vault/certificates/certificate-scenarios)<br>\\r\\n💡 [Security Recommendations in Microsoft Defender for Cloud](https://docs.microsoft.com/azure/security-center/security-center-recommendations)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Key Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"cert\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"key\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Key Vault Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Description contains \\\"certificate\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Certificates\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isCertificateVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Certificate Transparency Log Monitoring\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isIntrusionDetectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Intrusion Detection Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Enterprise](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nEnterprise-based controls including security orchestration automation & response, shadow IT detection, and virtual private networks. \"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Enterprise Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 113\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Security Orchestration, Automation, and Response\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"SOAR\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Shadow IT Detection\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Shadow\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Virtual Private Network (VPN)\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"VPN\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"6a82c6f2-dde9-45d9-acf4-23e96b5b2647\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isSOARVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"SOAR\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isShadowVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Shadow\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"750b4451-0f5d-4e58-95c2-c4b4c8991335\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isVPNVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"VPN\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"a2f3d34f-7824-4733-bddc-00efb62da0f2\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Security Orchestration, Automation, and Response (SOAR)](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nSecurity Orchestration, Automation, and Response (SOAR) tools define, prioritize, and automate the response to security incidents.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n🔷 [AzureActivity](https://docs.microsoft.com/azure/azure-monitor/reference/tables/azureactivity) ✳️ [Azure Logic Apps](https://azure.microsoft.com/services/logic-apps/) <br>\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Tutorial: Setup Automated Threat Responses in Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/tutorial-respond-threats-playbook)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[DE.AE, DE.CM, DE.DP, RS.CO, RS.AN, RC.RP](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type == \\\"microsoft.logic/workflows\\\"\\r\\n| extend Connection = parse_json(properties)[\\\"parameters\\\"][\\\"$connections\\\"][\\\"value\\\"]\\r\\n| where Connection has \\\"managedApis/azuresentinel\\\"\\r\\n| project id, type, resourceGroup\",\"size\":0,\"showAnalytics\":true,\"title\":\"SOAR Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3 - Copy\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"playbook\\\" or RecommendationDisplayName contains \\\"automation\\\" or RecommendationDisplayName contains \\\"logic\\\" or RecommendationDisplayName contains \\\"notification\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"AzureActivity\\r\\n| where OperationNameValue startswith \\\"Microsoft.Logic\\\"\\r\\n| where ActivityStatusValue == \\\"Success\\\" or ActivityStatusValue == \\\"Succeeded\\\"\\r\\n| extend scope_ = tostring(Authorization_d.scope)\\r\\n| parse-where scope_ with * 'workflows/' PlaybookName '/' *\\r\\n| where PlaybookName contains \\\"notify\\\" or PlaybookName contains \\\"email\\\" or PlaybookName contains \\\"teams\\\" or PlaybookName contains \\\"ticket\\\" or PlaybookName contains \\\"post\\\"\\r\\n| make-series count() default=0 on TimeGenerated from {TimeRange:start} to {TimeRange:end} step 1d by PlaybookName\\r\\n| render timechart \",\"size\":0,\"showAnnotations\":true,\"showAnalytics\":true,\"title\":\"Notification SOAR Playbooks (Triggered over Time)\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"]},\"customWidth\":\"50\",\"name\":\"query - 3\"}]},\"conditionalVisibility\":{\"parameterName\":\"isSOARVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Security Orchestration, Automation, and Response (SOAR)\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Shadow IT Detection](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nShadow IT detection systems detect the presence of unauthorized software and systems in use by an agency.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Tutorial: Discover and Manage Shadow IT in Your Network](https://docs.microsoft.com/cloud-app-security/tutorial-shadow-it)<br>\\r\\n💡 [Review Your Security Recommendations](https://docs.microsoft.com/azure/security-center/security-center-recommendations)<br>\\r\\n💡 [Endpoint Discovery - Navigating Your Way Through Unmanaged Devices](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/endpoint-discovery-navigating-your-way-through-unmanaged-devices/ba-p/2248909)<br>\\r\\n💡 [Device Discovery Overview](https://docs.microsoft.com/microsoft-365/security/defender-endpoint/device-discovery)<br>\\r\\n💡 [Welcome to Microsoft Defender for IoT](https://docs.microsoft.com/azure/defender-for-iot/overview)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud Apps](https://portal.cloudappsecurity.com/) <br>\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0)<br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br>\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft Defender for IoT](https://portal.azure.com/#blade/Microsoft_Azure_IoT_Defender/IoTDefenderDashboard/Getting_Started)<br> \\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.IP, PR.MA, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Description contains \\\"shadow\\\" or Description contains \\\"unauth\\\" or Description contains \\\"rogue\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Shadow IT\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"safe\\\" or RecommendationDisplayName contains \\\"authorized\\\" or RecommendationDisplayName contains \\\"endpoint protection\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| extend Azure_Inventory=location\\r\\n| extend M365_Inventory=strcat(\\\"https://security.microsoft.com/machines\\\")\\r\\n| project AssetID=id,AssetType=type, Azure_Inventory, M365_Inventory\\r\\n| sort by AssetType desc\\r\\n| limit 2500\",\"size\":0,\"showAnalytics\":true,\"title\":\"Review Asset Inventory\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Azure_Inventory\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Azure Inventory >>\",\"bladeOpenContext\":{\"bladeName\":\"InventoryBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"\",\"source\":\"static\",\"value\":\"25\"}]}}},{\"columnMatch\":\"M365_Inventory\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"M365 Inventory >>\"}}],\"rowLimit\":2500,\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 1\"}]},\"conditionalVisibility\":{\"parameterName\":\"isShadowVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Shadow IT Detection\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Virtual Private Network (VPN)](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nVirtual private network (VPN) solutions provide a secure communications mechanism between networks that may traverse across unprotected or public networks.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [Resources](https://docs.microsoft.com/azure/governance/resource-graph/samples/starter) ✳️ [VPN Gateway]( https://azure.microsoft.com/services/vpn-gateway/)<br>\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [What is VPN Gateway?](https://docs.microsoft.com/azure/vpn-gateway/vpn-gateway-about-vpngateways)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Virtual Network Gateways](https://portal.azure.com/#blade/HubsExtension/BrowseResourceBlade/resourceType/Microsoft.Network%2FvirtualNetworkGateways)<br>\\r\\n🔀 [Microsoft Defender for Cloud: Recommendations](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.DS, PR.IP, PR.MA, PR.PT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"private\\\" or RecommendationDisplayName contains \\\"vpn\\\" or RecommendationDisplayName contains \\\"network gateway\\\" or RecommendationDisplayName contains \\\"express\\\" or RecommendationDisplayName contains \\\"VPC\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"resources\\r\\n| where type contains \\\"gate\\\" or type contains \\\"bastion\\\" or type contains \\\"route\\\" or type contains \\\"privateend\\\"\\r\\n| project id,type,location,resourceGroup\\r\\n| order by location asc\",\"size\":0,\"showAnalytics\":true,\"title\":\"VPN Assets\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"showExportToExcel\":true,\"queryType\":1,\"resourceType\":\"microsoft.resourcegraph/resources\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 1\"}]},\"conditionalVisibility\":{\"parameterName\":\"isVPNVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Virtual Private Network (VPN)\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isEnterpriseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Enterprise Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Unified Communications & Collaboration](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nUCC measures including identity verification, encrypted communications, connection terminations, and data loss prevention. \\r\\n\"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Unified Communications & Collaboration Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 114\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"UCC Identity Verification\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Identity\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"UCC Encrypted Communication\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Encrypted\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"UCC Connection Termination\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Connection\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"UCC Data Loss Prevention\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"a206a547-329b-4003-8832-c16daacca6c6\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isIdentityVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Identity\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isEncryptedVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Encrypted\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"9b640df5-5ec5-41bc-8e78-086304ed742a\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isConnectionVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Connection\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"893f0857-1ccf-4c35-8432-abe89d1fcf15\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"767d26fb-524c-448c-9240-40f069a8db45\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [UCC Identity Verification](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nIdentity verification ensures that access to the virtual meeting is limited to appropriate individuals. Waiting room features, where the meeting host authorizes vetted individuals to join the meeting can also be utilized.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Security and Microsoft Teams](https://docs.microsoft.com/microsoftteams/teams-security-guide)<br>\\r\\n💡 [Identity Models and Authentication for Microsoft Teams](https://docs.microsoft.com/microsoftteams/identify-models-authentication)<br>\\r\\n💡 [Microsoft Sentinel and Microsoft Teams](https://docs.microsoft.com/microsoftteams/teams-sentinel-guide)<br>\\r\\n💡 [Microsoft Teams Meeting Attendance Report](https://docs.microsoft.com/microsoftteams/teams-analytics-and-reports/meeting-attendance-report)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/)<br>\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let LastObserved = SigninLogs\\r\\n| where ResultType == 0\\r\\n| summarize arg_max(TimeGenerated, *) by UserPrincipalName\\r\\n| project UserPrincipalName, LastSignIn=TimeGenerated;\\r\\nSigninLogs\\r\\n| extend UserProfile = strcat(\\\"https://portal.azure.com/#blade/Microsoft_AAD_IAM/UserDetailsMenuBlade/Profile/userId/\\\", UserId)\\r\\n| where AppDisplayName has_any (\\\"teams\\\", \\\"webex\\\", \\\"slack\\\", \\\"zoom\\\", \\\"meet\\\", \\\"chat\\\", \\\"goto\\\")\\r\\n| where ResultType == 0\\r\\n| summarize count() by UserPrincipalName, UserProfile, UserId, AppDisplayName\\r\\n| join (LastObserved) on UserPrincipalName\\r\\n| project UserPrincipalName, AppDisplayName, SignInCount=count_, UserProfile, LastSignIn, UserId\\r\\n| sort by SignInCount desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"UCC Authentications\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"SignInCount\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"UserProfile\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"AAD User Profile >>\",\"bladeOpenContext\":{\"bladeName\":\"UserDetailsMenuBlade\",\"extensionName\":\"Microsoft_AAD_IAM\",\"bladeParameters\":[{\"name\":\"userId\",\"source\":\"column\",\"value\":\"UserId\"}]}}},{\"columnMatch\":\"UserId\",\"formatter\":5},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}}],\"filter\":true},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"customWidth\":\"50\",\"name\":\"query - 9\"}]},\"conditionalVisibility\":{\"parameterName\":\"isIdentityVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UCC Identity Verification\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [UCC Encrypted Communication](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nCommunication between virtual meeting participants and any data exchanged is encrypted at rest and in transit. Some UCC offerings support end-to-end encryption, where encryption is performed on the clients and can only be decrypted by the other authenticated participants and cannot be decrypted by the UCC vendor.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [OfficeActivity](https://docs.microsoft.com/azure/azure-monitor/reference/tables/officeactivity) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender)<br> \\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityrecommendation) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [Security and Microsoft Teams](https://docs.microsoft.com/microsoftteams/teams-security-guide)<br>\\r\\n💡 [Microsoft Sentinel and Microsoft Teams](https://docs.microsoft.com/microsoftteams/teams-sentinel-guide)<br>\\r\\n💡 [Trustworthy by Default](https://docs.microsoft.com/microsoftteams/teams-security-guide#trustworthy-by-default)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Admin Center](https://admin.microsoft.com/)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.PT, PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"OfficeActivity\\r\\n| where RecordType == \\\"MicrosoftTeams\\\"\\r\\n| extend TeamsMembers = strcat(Members)\\r\\n| distinct Operation, UserId, TeamsMembers, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Microsoft Teams Logs\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Operation\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"UserId\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName contains \\\"web apps\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isEncryptedVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UCC Encrypted Communication\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [UCC Connection Termination](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMechanisms that ensure the meeting host can positively control participation. These can include inactivity timeouts, on-demand prompts, unique access codes for each meeting, host participant eviction, and even meeting duration limits.\\r\\n\\r\\n### Implementation \\r\\n💡 [Manage Meeting Policies in Teams](https://docs.microsoft.com/microsoftteams/meeting-policies-in-teams)<br>\\r\\n💡 [Manage Microsoft Teams Rooms](https://docs.microsoft.com/microsoftteams/rooms/rooms-manage)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Teams Admin Center](https://admin.teams.microsoft.com/)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.IP, PR.AT](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":1,\"content\":{\"json\":\"### ✳️ [Leverage Microsoft Teams for UCC Connection Termination Controls via Meeting Policies](https://docs.microsoft.com/microsoftteams/meeting-policies-in-teams?WT.mc_id=Portal-fx)\\r\\n \\r\\n\"},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isConnectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UCC Connection Termination\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [UCC Data Loss Prevention](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nMechanisms for controlling the sharing of information between UCC participants, intentional or incidental. This may be integrated into additional agency data loss prevention technologies and can include keyword matching, attachment file type or existence prohibitions, attachment size limitations, or even audio/visual filters.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [InformationProtectionLogs_CL](https://docs.microsoft.com/azure/information-protection/audit-logs) ✳️ [Azure Information Protection](https://azure.microsoft.com/services/information-protection/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Data Loss Prevention and Microsoft Teams](https://docs.microsoft.com/microsoft-365/compliance/dlp-microsoft-teams)<br>\\r\\n💡[Communication Compliance in Microsoft 365](https://docs.microsoft.com/microsoft-365/compliance/communication-compliance-solution-overview)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft 365 Defender](https://security.microsoft.com/) <br>\\r\\n🔀 [Microsoft 365 Compliance Center](https://compliance.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 2\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| summarize count() by ApplicationName_s, LabelName_s\\r\\n| sort by count_ desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Sensitive Data Actions by Application\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContext\":{\"durationMs\":2592000000},\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"orange\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 2\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDataVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UCC Data Loss Prevention\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isUnifiedCommunicationsCollaborationVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"UCC Group\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Protection](https://www.cisa.gov/trusted-internet-connections)\\r\\n---\\r\\nData protection measures including access control, protections for data at rest, protections for data in transit, data loss prevention, and data access & use telemetry. \"},\"customWidth\":\"40\",\"conditionalVisibility\":{\"parameterName\":\"isDataProtectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Protection Capabilities Guide\"},{\"type\":1,\"content\":{\"json\":\"\"},\"customWidth\":\"60\",\"conditionalVisibility\":{\"parameterName\":\"isDataProtectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"text - 115\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"{\\\"version\\\":\\\"1.0.0\\\",\\\"content\\\":\\\"[\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Access Control\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Access\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Protections for Data at Rest\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Rest\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Protections for Data in Transit\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Transit\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Data Loss Prevention\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Data\\\\\\\" },\\\\r\\\\n\\\\t{ \\\\\\\"Control\\\\\\\": \\\\\\\"Data Access and Use Telemetry\\\\\\\", \\\\\\\"tab\\\\\\\": \\\\\\\"Use\\\\\\\" }\\\\r\\\\n]\\\"}\\r\\n\",\"size\":3,\"exportMultipleValues\":true,\"exportedParameters\":[{\"fieldName\":\"tab\",\"parameterName\":\"Tab\",\"parameterType\":1}],\"queryType\":8,\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"tab\",\"formatter\":5}]}},\"customWidth\":\"40\",\"name\":\"query - 8\",\"styleSettings\":{\"showBorder\":true}},{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"6a82c6f2-dde9-45d9-acf4-23e96b5b2647\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"isAccessVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Access\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isRestVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Rest\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"b91d3f98-d0d1-4e31-a63c-d949e61ec08b\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isTransitVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Transit\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"a34338fa-6463-4b8f-866f-2d79396eceb7\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isDataVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Data\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"9a520097-2a54-41dd-bf84-7ca039dd1939\"},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"isUseVisible\",\"type\":1,\"isHiddenWhenLocked\":true,\"criteriaData\":[{\"criteriaContext\":{\"leftOperand\":\"Tab\",\"operator\":\"contains\",\"rightValType\":\"static\",\"rightVal\":\"Use\",\"resultValType\":\"static\",\"resultVal\":\"true\"}},{\"criteriaContext\":{\"operator\":\"Default\",\"rightValType\":\"param\",\"resultValType\":\"static\",\"resultVal\":\"false\"}}],\"timeContext\":{\"durationMs\":86400000},\"id\":\"22c31b63-743c-4b33-924e-26a70aa0fefb\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"customWidth\":\"10\",\"name\":\"Hidden Parameters Selectors\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Access Control](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nAccess control technologies allow an agency to define policies concerning the allowable activities of users and entities to data and resources.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br> \\r\\n\\r\\n### Implementation \\r\\n💡 [How Access Management in Azure AD works](https://docs.microsoft.com/azure/active-directory/fundamentals/active-directory-manage-groups#how-access-management-in-azure-ad-works)<br> \\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview)<br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.AC, PR.IP, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let LastObserved = SigninLogs\\r\\n| where ResultType == 0\\r\\n| summarize arg_max(TimeGenerated, *) by UserPrincipalName\\r\\n| project UserPrincipalName, LastSignIn=TimeGenerated;\\r\\nSigninLogs\\r\\n| extend UserProfile = strcat(\\\"https://portal.azure.com/#blade/Microsoft_AAD_IAM/UserDetailsMenuBlade/Profile/userId/\\\", UserId)\\r\\n| where ResultType == 0\\r\\n| summarize count() by UserPrincipalName, UserProfile, UserId, AppDisplayName\\r\\n| join (LastObserved) on UserPrincipalName\\r\\n| project UserPrincipalName, AppDisplayName, SignInCount=count_, UserProfile, LastSignIn, UserId\\r\\n| sort by SignInCount desc\\r\\n| limit 2500\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"User Access by Application\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"SignInCount\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"UserProfile\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"AAD User Profile >>\",\"bladeOpenContext\":{\"bladeName\":\"UserDetailsMenuBlade\",\"extensionName\":\"Microsoft_AAD_IAM\",\"bladeParameters\":[{\"name\":\"userId\",\"source\":\"column\",\"value\":\"UserId\"}]}}},{\"columnMatch\":\"UserId\",\"formatter\":5},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellowOrangeRed\"}}],\"rowLimit\":2500,\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"OperationName\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Runs\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"maximumSignificantDigits\":3,\"maximumFractionDigits\":2}}},\"secondaryContent\":{\"columnMatch\":\"TrendList\",\"formatter\":9,\"formatOptions\":{\"palette\":\"blue\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":100,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"}}},\"customWidth\":\"50\",\"name\":\"query - 9\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SigninLogs\\r\\n| where ResultType == 0\\r\\n| where Location <> \\\"\\\"\\r\\n| extend latitude_ = tostring(parse_json(tostring(LocationDetails.geoCoordinates)).latitude)\\r\\n| extend longitude_ = tostring(parse_json(tostring(LocationDetails.geoCoordinates)).longitude)\\r\\n| extend city_ = tostring(LocationDetails.city)\\r\\n\\r\\n\",\"size\":3,\"showAnalytics\":true,\"title\":\"User Sign-Ins by Geolocation\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore This Control Further\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"map\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Caller\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}]},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"OperationName\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Runs\",\"formatter\":12,\"formatOptions\":{\"palette\":\"auto\"},\"numberFormat\":{\"unit\":17,\"options\":{\"maximumSignificantDigits\":3,\"maximumFractionDigits\":2}}},\"secondaryContent\":{\"columnMatch\":\"TrendList\",\"formatter\":9,\"formatOptions\":{\"palette\":\"blue\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"LatLong\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"city_\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"city_\",\"numberOfMetrics\":10,\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"state_\",\"colorAggregation\":\"Count\",\"type\":\"heatmap\",\"heatmapPalette\":\"coldHot\"},\"numberFormatSettings\":{\"unit\":0,\"options\":{\"style\":\"decimal\"}}}},\"conditionalVisibility\":{\"parameterName\":\"isDataProtectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"showPin\":false,\"name\":\"query - 4\"}]},\"conditionalVisibility\":{\"parameterName\":\"isAccessVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Access Control\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Protections for Data at Rest](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData protection at rest aims to secure data stored on any endpoint or storage medium.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Data Encryption at Rest](https://docs.microsoft.com/azure/security/fundamentals/encryption-atrest)<br>\\r\\n💡 [About Azure Key Vault](https://docs.microsoft.com/azure/key-vault/general/overview)<br>\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Key Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName has_any(\\\"encrypt\\\", \\\"storage\\\", \\\"database\\\", \\\"databases\\\", \\\"SQL\\\", \\\"disk\\\", \\\"disks\\\")\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isRestVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Protections for Data at Rest\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Protections for Data in Transit](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData protection in transit, or data in motion, aims to secure data that is actively moving from one location to another, such as across the internet or through a private enterprise network.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [SecurityRecommendation](https://docs.microsoft.com/azure/security-center/continuous-export?tabs=azure-portal#what-data-types-can-be-exported) ✳️ [Microsoft Defender for Cloud](https://azure.microsoft.com/services/security-center/)<br>\\r\\n\\r\\n### Implementation \\r\\n💡 [Azure Data Encryption in Transit](https://docs.microsoft.com/azure/security/fundamentals/encryption-overview#encryption-of-data-in-transit)<br>\\r\\n💡 [About Azure Key Vault](https://docs.microsoft.com/azure/key-vault/general/overview)<br>\\r\\n💡 [Use Microsoft Defender for Cloud Recommendations to Enhance Security](https://docs.microsoft.com/azure/security-center/security-center-using-recommendations)<br>\\r\\n💡 [Encryption for Data in Transit](https://docs.microsoft.com/compliance/assurance/assurance-encryption-in-transit)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Defender for Cloud](https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0) <br>\\r\\n🔀 [Key Vaults](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.KeyVault%2Fvaults) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"let CustomView = SecurityRecommendation | summarize arg_max(TimeGenerated,*) by RecommendationName| project RecommendationName, RecommendationLink | parse RecommendationLink with * '/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/' assessmentKey '/' *;\\r\\nSecurityRecommendation\\r\\n| where RecommendationDisplayName has_any(\\\"http\\\", \\\"https\\\", \\\"TLS\\\", \\\"transfer\\\", \\\"transit\\\", \\\"Secure Socket\\\", \\\"SSH\\\", \\\"just\\\", \\\"FTP\\\", \\\"server-side\\\")\\r\\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\\r\\n| summarize Failed = countif(RecommendationState == \\\"Unhealthy\\\"), Passed = countif(RecommendationState == \\\"Healthy\\\"), Total = countif(RecommendationState == \\\"Unhealthy\\\" or RecommendationState == \\\"Healthy\\\") by RecommendationName\\r\\n| extend PassedControls = (Passed/todouble(Total))*100\\r\\n| join (CustomView) on RecommendationName\\r\\n| project RecommendationName, Total, PassedControls, Passed, Failed, RecommendationLink, assessmentKey\\r\\n| where Total > 0\\r\\n| sort by Total, Passed desc\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Recommendations \",\"noDataMessage\":\"Confirm Microsoft Defender for Cloud: Regulatory Compliance Initiative for NIST SP 800-53 R4 is enabled with Microsoft Defender for Cloud Continous Log Export to this workspace. See Getting Started steps in the help tab above for more information\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"RecommendationName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Gear\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Total\",\"formatter\":22,\"formatOptions\":{\"compositeBarSettings\":{\"labelText\":\"\",\"columnSettings\":[{\"columnName\":\"Passed\",\"color\":\"green\"},{\"columnName\":\"Failed\",\"color\":\"redBright\"}]}}},{\"columnMatch\":\"PassedControls\",\"formatter\":0,\"numberFormat\":{\"unit\":1,\"options\":{\"style\":\"decimal\",\"useGrouping\":true,\"maximumFractionDigits\":2}}},{\"columnMatch\":\"RecommendationLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Remediate >>\",\"bladeOpenContext\":{\"bladeName\":\"RecommendationsBlade\",\"extensionName\":\"Microsoft_Azure_Security\",\"bladeParameters\":[{\"name\":\"assessmentKey\",\"source\":\"column\",\"value\":\"assessmentKey\"}]}}},{\"columnMatch\":\"assessmentKey\",\"formatter\":5},{\"columnMatch\":\"Family\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ControlFamily\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Persistence\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"coldHot\"}}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 9\",\"styleSettings\":{\"maxWidth\":\"50\"}}]},\"conditionalVisibility\":{\"parameterName\":\"isTransitVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Protections for Data in Transit\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Loss Prevention](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nData loss prevention technologies detect instances of the exfiltration, either malicious or accidental, of agency data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [InformationProtectionLogs_CL](https://docs.microsoft.com/azure/information-protection/audit-logs) ✳️ [Azure Information Protection](https://azure.microsoft.com/services/information-protection/)<br>\\r\\n🔷 [SecurityIncident](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityincident) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) <br> \\r\\n🔷 [SecurityAlert](https://docs.microsoft.com/azure/azure-monitor/reference/tables/securityalert) ✳️ [Microsoft Sentinel](https://azure.microsoft.com/services/azure-sentinel/) ✳️ [Microsoft Defender for Office 365]( https://www.microsoft.com/microsoft-365/security/office-365-defender) ✳️ [Microsoft Defender for Endpoint]( https://www.microsoft.com/microsoft-365/security/endpoint-defender) <br>\\r\\n\\r\\n### Implementation \\r\\n💡 [How to Configure a Label for Rights Management Protection](https://docs.microsoft.com/azure/information-protection/configure-policy-protection)<br>\\r\\n💡 [Hunt for Threats with Microsoft Sentinel](https://docs.microsoft.com/azure/sentinel/hunting)<br>\\r\\n💡 [Learn about Microsoft 365 Endpoint Data Loss Prevention](https://docs.microsoft.com/microsoft-365/compliance/endpoint-dlp-learn-about)<br>\\r\\n💡 [Configure and View Alerts for DLP Polices](https://docs.microsoft.com/microsoft-365/compliance/dlp-configure-view-alerts-policies)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Azure Information Protection](https://portal.azure.com/#blade/Microsoft_Azure_InformationProtection/DataClassGroupEditBlade/quickstartBlade) <br>\\r\\n🔀 [Microsoft Sentinel](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/microsoft.securityinsightsarg%2Fsentinel)<br> \\r\\n🔀 [Office 365 Security & Compliance Center](https://protection.office.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[PR.DS](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"SecurityIncident\\r\\n| extend Tactics = tostring(parse_json(tostring(AdditionalData.tactics)))\\r\\n| where Description contains \\\"data\\\" or Title contains \\\"data\\\" or Description contains \\\"loss\\\" or Title contains \\\"loss\\\" or Description contains \\\"exfil\\\" or Title contains \\\"exfil\\\" or Tactics contains \\\"exfil\\\"\\r\\n| summarize arg_max(TimeGenerated, *) by IncidentNumber\\r\\n| parse IncidentUrl with * '/#asset/Microsoft_Azure_Security_Insights/Incident' IncidentBlade\\r\\n| extend SeverityRank=iff(Severity == \\\"High\\\", 3, iff(Severity == \\\"Medium\\\", 2, iff(Severity == \\\"Low\\\", 1, iff(Severity == \\\"Informational\\\", 0, 0))))\\r\\n| sort by SeverityRank, TimeGenerated desc\\r\\n| project ['Incident Name']=Title, IncidentNumber, Severity, IncidentUrl, FirstActivityTime, IncidentBlade\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Security Incidents: Data Loss\",\"noDataMessage\":\"No Incidents Observed For This Technique Within These Thresholds\",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"Incident Name\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Alert\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"Sev0\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"Sev1\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"Sev2\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"Sev3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"OpenBlade\",\"linkLabel\":\"Incident >>\",\"bladeOpenContext\":{\"bladeName\":\"CaseBlade\",\"extensionName\":\"Microsoft_Azure_Security_Insights\",\"bladeParameters\":[{\"name\":\"id\",\"source\":\"column\",\"value\":\"IncidentBlade\"}]}}},{\"columnMatch\":\"IncidentBlade\",\"formatter\":5}],\"filter\":true}},\"customWidth\":\"50\",\"name\":\"query - 3\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| project UserId_s, LabelName_s, Operation_s, Activity_s, IPv4_s, ProtectionOwner_s, ApplicationName_s, ProcessName_s, Platform_s, ContentId_g, TimeGenerated\\r\\n| sort by TimeGenerated desc\\r\\n| limit 250\\r\\n\",\"size\":0,\"showAnalytics\":true,\"title\":\"Scan/Monitor for Sensitive Data with Azure Information Protection\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserId_s\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"3\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"Severity\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"==\",\"thresholdValue\":\"High\",\"representation\":\"red\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Medium\",\"representation\":\"orange\",\"text\":\"{0}{1}\"},{\"operator\":\"==\",\"thresholdValue\":\"Low\",\"representation\":\"yellow\",\"text\":\"{0}{1}\"},{\"operator\":\"Default\",\"representation\":\"blue\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"ProductName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"uninitialized\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"AlertLink\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Alert >\"}},{\"columnMatch\":\"UPN\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"2\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"IncidentUrl\",\"formatter\":7,\"formatOptions\":{\"linkTarget\":\"Url\",\"linkLabel\":\"Go to Incident >\"},\"numberFormat\":{\"unit\":0,\"options\":{\"style\":\"decimal\"}}},{\"columnMatch\":\"count_\",\"formatter\":8,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"city_\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blue\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"state_\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"colors\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\",\"text\":\"{0}{1}\"}]}}],\"filter\":true},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"SourceIPLocation\",\"longitude\":\"SourceIPLocation\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"blueDark\"}]}}},\"customWidth\":\"50\",\"name\":\"query - 2\"}]},\"conditionalVisibility\":{\"parameterName\":\"isDataVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Loss Prevention\",\"styleSettings\":{\"showBorder\":true}},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":1,\"content\":{\"json\":\"# [Data Access and Use Telemetry](https://www.cisa.gov/publication/tic-30-core-guidance-documents)\\r\\nIdentify agency sensitive data stored, processed, or transmitted, including those located at a service provider. Enforce detailed logging for access or changes to sensitive data.\\r\\n\\r\\n### Recommended Logs\\r\\n🔷 [InformationProtectionLogs_CL](https://docs.microsoft.com/azure/information-protection/audit-logs) ✳️ [Azure Information Protection](https://azure.microsoft.com/services/information-protection/)<br> \\r\\n🔷 [SigninLogs](https://docs.microsoft.com/azure/azure-monitor/reference/tables/signinlogs) ✳️ [Microsoft Entra ID](https://azure.microsoft.com/services/active-directory/)<br>\\r\\n\\r\\n### Microsoft Reference \\r\\n💡 [What is Azure Information Protection?](https://docs.microsoft.com/azure/information-protection/what-is-information-protection)<br>\\r\\n💡 [Tutorial: Discovering Your Sensitive Content with the Azure Information Protection (AIP) scanner](https://docs.microsoft.com/azure/information-protection/tutorial-scan-networks-and-content)<br>\\r\\n💡 [Quickstart: Deploying the Azure Information Protection (AIP) Unified Labeling Client](https://docs.microsoft.com/azure/information-protection/quickstart-deploy-client)<br>\\r\\n💡 [Azure Information Protection (AIP) Labeling, Classification, and Protection](https://docs.microsoft.com/azure/information-protection/aip-classification-and-protection)<br>\\r\\n💡 [Overview of Data Loss Prevention](https://docs.microsoft.com/microsoft-365/compliance/data-loss-prevention-policies)<br>\\r\\n\\r\\n### Microsoft Portals\\r\\n🔀 [Microsoft Entra ID](https://portal.azure.com#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview) <br>\\r\\n🔀 [Azure Information Protection](https://portal.azure.com/#blade/Microsoft_Azure_InformationProtection/DataClassGroupEditBlade/quickstartBlade)<br> \\r\\n🔀 [Microsoft 365 Compliance Center](https://compliance.microsoft.com/) <br>\\r\\n\\r\\n### NIST Cybersecurity Framework Mapping\\r\\n[ID.AM, PR.AC, PR.DS, PR.PT, DE.AE, DE.CM](https://www.nist.gov/cyberframework)\\r\\n\\r\\n### Control Assessment\"},\"name\":\"text - 3\"},{\"type\":12,\"content\":{\"version\":\"NotebookGroup/1.0\",\"groupType\":\"editable\",\"items\":[{\"type\":9,\"content\":{\"version\":\"KqlParameterItem/1.0\",\"parameters\":[{\"id\":\"52668f65-b44a-4e14-82d8-c87410e7e5dc\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationStatus\",\"label\":\"Status\",\"type\":2,\"typeSettings\":{\"showDefault\":false},\"jsonData\":\"[\\r\\n {\\\"value\\\": \\\"Not Implemented\\\", \\\"label\\\": \\\"Not Implemented\\\", \\\"selected\\\":true},\\r\\n {\\\"value\\\": \\\"Implemented\\\", \\\"label\\\": \\\"Implemented\\\"},\\r\\n {\\\"value\\\": \\\"Alternate Implementation\\\", \\\"label\\\": \\\"Alternate Implementation\\\"},\\r\\n {\\\"value\\\": \\\"Planned\\\", \\\"label\\\": \\\"Planned\\\"},\\r\\n {\\\"value\\\": \\\"Out of Scope\\\", \\\"label\\\": \\\"Out of Scope\\\"}\\r\\n]\",\"timeContext\":{\"durationMs\":86400000}},{\"id\":\"578b8620-30b9-4b92-abc6-997998bc8156\",\"version\":\"KqlParameterItem/1.0\",\"name\":\"ImplementationDate\",\"label\":\"Date\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000}},{\"version\":\"KqlParameterItem/1.0\",\"name\":\"Notes\",\"type\":1,\"value\":\"\",\"timeContext\":{\"durationMs\":86400000},\"id\":\"7bd0d384-d3c3-4c77-9dae-d75e823edfcf\"}],\"style\":\"pills\",\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\"},\"name\":\"Status\"},{\"type\":1,\"content\":{\"json\":\"### Notes <br>\\r\\n{Notes}\"},\"name\":\"text - 1\"}]},\"name\":\"group - 2\"}]},\"customWidth\":\"50\",\"name\":\"Control Smartcard\"},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| summarize count() by UserId_s, LabelName_s, ApplicationName_s_s, Operation_s_s, Platform_s_s, Activity_s_s, IPv4_s_s\\r\\n| sort by count_ desc\\r\\n| limit 250\",\"size\":0,\"showAnalytics\":true,\"title\":\"Data Access and Use Telemetry\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserId_s\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"Person\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"count_\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}}],\"filter\":true}},\"customWidth\":\"50\",\"conditionalVisibility\":{\"parameterName\":\"isDataProtectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"query - 3\",\"styleSettings\":{\"maxWidth\":\"50\"}},{\"type\":3,\"content\":{\"version\":\"KqlItem/1.0\",\"query\":\"InformationProtectionLogs_CL\\r\\n| extend UserPrincipalName = UserId_s_s\\r\\n| where LabelName_s <> \\\"\\\"\\r\\n| join (SigninLogs) on UserPrincipalName\\r\\n| extend City = tostring(LocationDetails.city)\\r\\n| extend State = tostring(LocationDetails.state)\\r\\n| extend Country_Region = tostring(LocationDetails.countryOrRegion)\\r\\n\",\"size\":3,\"showAnalytics\":true,\"title\":\"Sensitive Data Access by Geolocation\",\"noDataMessage\":\"An Empty Panel Provides Opportunity To Explore Further and Implement Hardening. Controls: Confirm Licensing, Availability, and Health of Respective Offerings. Logging: Confirm Log Source is Onboarded to the Log Analytics Workspace. Time: Adjust the Time Parameter for a Larger Data-Set. \",\"timeContextFromParameter\":\"TimeRange\",\"showExportToExcel\":true,\"queryType\":0,\"resourceType\":\"microsoft.operationalinsights/workspaces\",\"crossComponentResources\":[\"{Workspace}\"],\"visualization\":\"map\",\"gridSettings\":{\"formatters\":[{\"columnMatch\":\"UserPrincipalName\",\"formatter\":18,\"formatOptions\":{\"thresholdsOptions\":\"icons\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"warning\",\"text\":\"{0}{1}\"}]}},{\"columnMatch\":\"UncommonActionVolume\",\"formatter\":4,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"UncommonAction\",\"formatter\":4,\"formatOptions\":{\"palette\":\"green\"}},{\"columnMatch\":\"FirstTimeUserAction\",\"formatter\":4,\"formatOptions\":{\"palette\":\"blue\"}},{\"columnMatch\":\"FirstTimeDeviceLogon\",\"formatter\":4,\"formatOptions\":{\"palette\":\"yellow\"}},{\"columnMatch\":\"IncidentCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"redBright\"}},{\"columnMatch\":\"AlertCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"orange\"}},{\"columnMatch\":\"AnomalyCount\",\"formatter\":8,\"formatOptions\":{\"palette\":\"yellow\"}}]},\"tileSettings\":{\"titleContent\":{\"columnMatch\":\"SigninStatus\",\"formatter\":1},\"leftContent\":{\"columnMatch\":\"Count\",\"formatter\":12,\"formatOptions\":{\"palette\":\"blue\"},\"numberFormat\":{\"unit\":17,\"options\":{\"style\":\"decimal\",\"maximumFractionDigits\":2,\"maximumSignificantDigits\":3}}},\"secondaryContent\":{\"columnMatch\":\"Trend\",\"formatter\":9,\"formatOptions\":{\"palette\":\"green\"}},\"showBorder\":false},\"mapSettings\":{\"locInfo\":\"CountryRegion\",\"locInfoColumn\":\"Location\",\"latitude\":\"latitude_\",\"longitude\":\"longitude_\",\"sizeSettings\":\"Location\",\"sizeAggregation\":\"Count\",\"labelSettings\":\"city_\",\"legendMetric\":\"Location\",\"legendAggregation\":\"Count\",\"itemColorSettings\":{\"nodeColorField\":\"Location\",\"colorAggregation\":\"Count\",\"type\":\"thresholds\",\"thresholdsGrid\":[{\"operator\":\"Default\",\"representation\":\"yellow\"}]}}},\"name\":\"query - 12\"}]},\"conditionalVisibility\":{\"parameterName\":\"isUseVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Access and Use Telemetry\",\"styleSettings\":{\"showBorder\":true}}]},\"conditionalVisibility\":{\"parameterName\":\"isDataProtectionVisible\",\"comparison\":\"isEqualTo\",\"value\":\"true\"},\"name\":\"Data Protection Group\"}],\"fromTemplateId\":\"sentinel-ZeroTrust(TIC3.0)\",\"$schema\":\"https://github.com/Microsoft/Application-Insights-Workbooks/blob/master/schema/workbook.json\"}\r\n",
|
||
"version": "1.0",
|
||
"sourceId": "[variables('workspaceResourceId')]",
|
||
"category": "sentinel"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/metadata",
|
||
"apiVersion": "2022-01-01-preview",
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat('Workbook-', last(split(variables('workbookId1'),'/'))))]",
|
||
"properties": {
|
||
"description": "@{workbookKey=ZeroTrust(TIC3.0)Workbook; logoFileName=Azure_Sentinel.svg; description=Sets the time name for analysis; dataTypesDependencies=System.Object[]; dataConnectorsDependencies=System.Object[]; previewImagesFileNames=System.Object[]; version=1.0.0; title=ZeroTrust(TIC3.0); templateRelativePath=ZeroTrustTIC3.json; subtitle=; provider=Microsoft}.description",
|
||
"parentId": "[variables('workbookId1')]",
|
||
"contentId": "[variables('_workbookContentId1')]",
|
||
"kind": "Workbook",
|
||
"version": "[variables('workbookVersion1')]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
},
|
||
"dependencies": {
|
||
"operator": "AND",
|
||
"criteria": [
|
||
{
|
||
"contentId": "SecurityRecommendation",
|
||
"kind": "DataType"
|
||
}
|
||
]
|
||
}
|
||
}
|
||
}
|
||
]
|
||
},
|
||
"packageKind": "Solution",
|
||
"packageVersion": "[variables('_solutionVersion')]",
|
||
"packageName": "[variables('_solutionName')]",
|
||
"packageId": "[variables('_solutionId')]",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"contentId": "[variables('_workbookContentId1')]",
|
||
"contentKind": "Workbook",
|
||
"displayName": "[parameters('workbook1-name')]",
|
||
"contentProductId": "[variables('_workbookcontentProductId1')]",
|
||
"id": "[variables('_workbookcontentProductId1')]",
|
||
"version": "[variables('workbookVersion1')]"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentTemplates",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"name": "[variables('analyticRuleObject1').analyticRuleTemplateSpecName1]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"dependsOn": [
|
||
"[extensionResourceId(resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspace')), 'Microsoft.SecurityInsights/contentPackages', variables('_solutionId'))]"
|
||
],
|
||
"properties": {
|
||
"description": "Zero_Trust_TIC3.0_ControlAssessmentPostureChange_AnalyticalRules Analytics Rule with template version 3.0.1",
|
||
"mainTemplate": {
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "[variables('analyticRuleObject1').analyticRuleVersion1]",
|
||
"parameters": {},
|
||
"variables": {},
|
||
"resources": [
|
||
{
|
||
"type": "Microsoft.SecurityInsights/AlertRuleTemplates",
|
||
"name": "[variables('analyticRuleObject1')._analyticRulecontentId1]",
|
||
"apiVersion": "2022-04-01-preview",
|
||
"kind": "Scheduled",
|
||
"location": "[parameters('workspace-location')]",
|
||
"properties": {
|
||
"description": "Zero Trust(TIC3.0) Control Assessments have Deviated from Configured Threshold Baselines",
|
||
"displayName": "ZeroTrust(TIC3.0) Control Assessment Posture Change",
|
||
"enabled": false,
|
||
"query": "SecurityRecommendation\n| where RecommendationDisplayName <> \"\"\n| extend ControlFamily=iff(RecommendationDisplayName has_any(\"email\"), \"Email\",\n iff(RecommendationDisplayName has_any(\"apps\", \"teams\", \"meeting\", \"call\"), \"Unified Communications & Collaboration\",\n iff(RecommendationDisplayName has_any(\"dns\", \"domain\"), \"DNS\",\n iff(RecommendationDisplayName has_any(\"endpoint protection\", \"malware\", \"file\", \"files\", \"IaaSAntimalware\"), \"Files\",\n iff(RecommendationDisplayName has_any(\"Security Center\", \"defender\", \"adaptive\", \"HoneyTokens\", \"honey\", \"deception\", \"intrusion\", \"incident\", \"incidents\"), \"Intrusion Detection\",\n iff(RecommendationDisplayName has_any(\"firewall\", \"watcher\", \"proxy\", \"certificate\", \"url\", \"web\"), \"Web\",\n iff(RecommendationDisplayName has_any(\"network\", \"segment\", \"network security groups\", \"subnet\", \"application gateway\", \"security groups\", \"IP forwarding\", \"port\", \"ports\", \"networks\"), \"Networking\",\n iff(RecommendationDisplayName has_any(\"backup\", \"denial\", \"DDoS\", \"load\", \"scale\", \"front\", \"traffic manager\", \"pool\", \"disaster\", \"region\", \"redundant\", \"geo\"), \"Resiliency\",\n iff(RecommendationDisplayName has_any(\"encrypt\", \"rest\", \"transit\", \"data\", \"http\", \"https\", \"TLS\", \"transfer\", \"transit\", \"Secure Socket\", \"SSH\", \"just\", \"FTP\", \"server-side\", \"storage\", \"database\", \"databases\", \"SQL\", \"disk\", \"disks\"), \"Data Protection\",\n iff(RecommendationDisplayName has_any(\"private\", \"vpn\", \"automation\", \"playbook\", \"logic\", \"notification\", \"authorized\", \"safe\", \"network gateway\", \"express\", \"VPC\"), \"Enterprise\",\n iff(RecommendationDisplayName has_any(\"recover\", \"log\", \"configured\", \"configuration\", \"identity\", \"privilege\", \"admin\", \"authentication\", \"JIT\", \"just\", \"password\", \"time\", \"sync\", \"vulnerability\", \"Vulnerabilities\", \"updates\", \"update\", \"upgrade\", \"audit\", \"account\", \"guest\", \"shared\", \"access\", \"machines\", \"rights\", \"VM\", \"key\", \"keys\", \"IAM\", \"EC2\", \"GuardDuty\", \"logs\", \"CloudTrail\", \"MFA\", \"External accounts\", \"accounts\", \"config\", \"credentials\", \"privileged\", \"owner\", \"owners\", \"login\", \"logon\", \"virtual machine\", \"container\", \"containers\", \"Kubernetes\"), \"Universal Security Capabilities\", \"Other\")))))))))))\n| summarize arg_max(TimeGenerated, *) by AssessedResourceId, RecommendationDisplayName\n| summarize\n Failed=countif(RecommendationState == \"Unhealthy\"),\n Passed=countif(RecommendationState == \"Healthy\"),\n Total=countif(RecommendationState == \"Unhealthy\" or RecommendationState == \"Healthy\")\n by ControlFamily\n| extend PassedControlsPercentage = (Passed / todouble(Total)) * 100\n| extend RemediationLink = strcat('https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5')\n| extend URLCustomEntity = RemediationLink\n| project ControlFamily, Total, PassedControlsPercentage, Passed, Failed, RemediationLink, URLCustomEntity\n| where PassedControlsPercentage < 70 //Adjust PassedRatePercentage Thresholds within Organizational Needs\n| sort by PassedControlsPercentage asc\n",
|
||
"queryFrequency": "P7D",
|
||
"queryPeriod": "P7D",
|
||
"severity": "Medium",
|
||
"suppressionDuration": "PT1H",
|
||
"suppressionEnabled": false,
|
||
"triggerOperator": "GreaterThan",
|
||
"triggerThreshold": 0,
|
||
"status": "Available",
|
||
"requiredDataConnectors": [],
|
||
"tactics": [
|
||
"Discovery"
|
||
],
|
||
"techniques": [
|
||
"T1082"
|
||
],
|
||
"entityMappings": [
|
||
{
|
||
"entityType": "URL",
|
||
"fieldMappings": [
|
||
{
|
||
"columnName": "URLCustomEntity",
|
||
"identifier": "Url"
|
||
}
|
||
]
|
||
}
|
||
]
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/metadata",
|
||
"apiVersion": "2022-01-01-preview",
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat('AnalyticsRule-', last(split(variables('analyticRuleObject1').analyticRuleId1,'/'))))]",
|
||
"properties": {
|
||
"description": "ZeroTrust(TIC3.0) Analytics Rule 1",
|
||
"parentId": "[variables('analyticRuleObject1').analyticRuleId1]",
|
||
"contentId": "[variables('analyticRuleObject1')._analyticRulecontentId1]",
|
||
"kind": "AnalyticsRule",
|
||
"version": "[variables('analyticRuleObject1').analyticRuleVersion1]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
}
|
||
}
|
||
}
|
||
]
|
||
},
|
||
"packageKind": "Solution",
|
||
"packageVersion": "[variables('_solutionVersion')]",
|
||
"packageName": "[variables('_solutionName')]",
|
||
"packageId": "[variables('_solutionId')]",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"contentId": "[variables('analyticRuleObject1')._analyticRulecontentId1]",
|
||
"contentKind": "AnalyticsRule",
|
||
"displayName": "ZeroTrust(TIC3.0) Control Assessment Posture Change",
|
||
"contentProductId": "[variables('analyticRuleObject1')._analyticRulecontentProductId1]",
|
||
"id": "[variables('analyticRuleObject1')._analyticRulecontentProductId1]",
|
||
"version": "[variables('analyticRuleObject1').analyticRuleVersion1]"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentTemplates",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"name": "[variables('playbookTemplateSpecName1')]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"dependsOn": [
|
||
"[extensionResourceId(resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspace')), 'Microsoft.SecurityInsights/contentPackages', variables('_solutionId'))]"
|
||
],
|
||
"properties": {
|
||
"description": "Notify-GovernanceComplianceTeam-ZeroTrust Playbook with template version 3.0.1",
|
||
"mainTemplate": {
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "[variables('playbookVersion1')]",
|
||
"parameters": {
|
||
"PlaybookName": {
|
||
"defaultValue": "Notify-GovernanceComplianceTeam-ZeroTrust",
|
||
"type": "string"
|
||
},
|
||
"Email": {
|
||
"defaultValue": "GovernanceComplianceTeam@example.com",
|
||
"type": "string"
|
||
},
|
||
"TeamschannelId": {
|
||
"defaultValue": "GovernanceComplianceTeam",
|
||
"type": "string"
|
||
},
|
||
"TeamsgroupId": {
|
||
"defaultValue": "GovernanceComplianceTeam",
|
||
"type": "string"
|
||
}
|
||
},
|
||
"variables": {
|
||
"teamsConnectionName": "[[concat('teams-', parameters('PlaybookName'))]",
|
||
"azuresentinelConnectionName": "[[concat('azuresentinel-', parameters('PlaybookName'))]",
|
||
"office365ConnectionName": "[[concat('office365-', parameters('PlaybookName'))]",
|
||
"connection-2": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"_connection-2": "[[variables('connection-2')]",
|
||
"connection-3": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/office365')]",
|
||
"_connection-3": "[[variables('connection-3')]",
|
||
"connection-4": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/teams')]",
|
||
"_connection-4": "[[variables('connection-4')]",
|
||
"workspace-location-inline": "[concat('[resourceGroup().locatio', 'n]')]",
|
||
"workspace-name": "[parameters('workspace')]",
|
||
"workspaceResourceId": "[[resourceId('microsoft.OperationalInsights/Workspaces', variables('workspace-name'))]"
|
||
},
|
||
"resources": [
|
||
{
|
||
"properties": {
|
||
"provisioningState": "Succeeded",
|
||
"state": "Enabled",
|
||
"definition": {
|
||
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
|
||
"contentVersion": "1.0.0.0",
|
||
"parameters": {
|
||
"$connections": {
|
||
"type": "Object"
|
||
}
|
||
},
|
||
"triggers": {
|
||
"When_Azure_Sentinel_incident_creation_rule_was_triggered": {
|
||
"type": "ApiConnectionWebhook",
|
||
"inputs": {
|
||
"body": {
|
||
"callback_url": "@{listCallbackUrl()}"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['azuresentinel']['connectionId']"
|
||
}
|
||
},
|
||
"path": "/incident-creation"
|
||
}
|
||
}
|
||
},
|
||
"actions": {
|
||
"For_each": {
|
||
"foreach": "@triggerBody()?['object']?['properties']?['Alerts']",
|
||
"actions": {
|
||
"Post_message_in_a_chat_or_channel": {
|
||
"type": "ApiConnection",
|
||
"inputs": {
|
||
"body": {
|
||
"messageBody": "<p>Governance & Compliance Team,<br>\n<br>\nThe security posture of a workload has changed per the alerting details below:<br>\n<br>\nSeverity of Alert: @{items('For_each')?['properties']?['severity']}<br>\n<br>\n<u><strong>Microsoft Sentinel Incident</strong></u><br>\nTItle: @{triggerBody()?['object']?['properties']?['title']}<br>\nStatus: @{triggerBody()?['object']?['properties']?['status']}<br>\nNumber: @{triggerBody()?['object']?['properties']?['incidentNumber']}<br>\nCreated Time (UTC): @{triggerBody()?['object']?['properties']?['createdTimeUtc']}<br>\nIncident Link: @{triggerBody()?['object']?['properties']?['incidentUrl']}<br>\n<br>\n<u><strong>Alert Details</strong></u><br>\nAlert Display Name: @{items('For_each')?['properties']?['alertDisplayName']}<br>\nAlert Type: @{items('For_each')?['properties']?['alertType']}<br>\nSubscription ID: @{triggerBody()?['workspaceInfo']?['SubscriptionId']}<br>\nProvider Alert ID: @{items('For_each')?['properties']?['providerAlertId']}<br>\nAlert Link: @{items('For_each')?['properties']?['alertLink']}</p>",
|
||
"recipient": {
|
||
"channelId": "[[parameters('TeamschannelId')]",
|
||
"groupId": "[[parameters('TeamsgroupId')]"
|
||
}
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['teams']['connectionId']"
|
||
}
|
||
},
|
||
"method": "post",
|
||
"path": "/beta/teams/conversation/message/poster/Flow bot/location/@{encodeURIComponent('Channel')}"
|
||
}
|
||
},
|
||
"Send_an_email_(V2)_2": {
|
||
"runAfter": {
|
||
"Post_message_in_a_chat_or_channel": [
|
||
"Succeeded"
|
||
]
|
||
},
|
||
"type": "ApiConnection",
|
||
"inputs": {
|
||
"body": {
|
||
"Body": "<p>Governance & Compliance Team,<br>\n<br>\nThe security posture of a workload has changed per the alerting details below:<br>\n<br>\n<br>\n<u><strong>Microsoft Sentinel Incident</strong></u><br>\nTItle: @{triggerBody()?['object']?['properties']?['title']}<br>\nStatus: @{triggerBody()?['object']?['properties']?['status']}<br>\nNumber: @{triggerBody()?['object']?['properties']?['incidentNumber']}<br>\nIncident Severity: @{triggerBody()?['object']?['properties']?['severity']}<br>\nCreated Time (UTC): @{triggerBody()?['object']?['properties']?['createdTimeUtc']}<br>\nIncident Link: @{triggerBody()?['object']?['properties']?['incidentUrl']}<br>\n<br>\n<u><strong>Alert Details</strong></u><br>\nAlert Display Name: @{items('For_each')?['properties']?['alertDisplayName']}<br>\nAlert Product Name: @{items('For_each')?['properties']?['productName']}<br>\nAlert Severity: @{items('For_each')?['properties']?['severity']}<br>\nAlert Type: @{items('For_each')?['properties']?['alertType']}<br>\nSubscription ID: @{triggerBody()?['workspaceInfo']?['SubscriptionId']}<br>\nProvider Alert ID: @{items('For_each')?['properties']?['providerAlertId']}<br>\nAlert Link: @{items('For_each')?['properties']?['alertLink']}</p>",
|
||
"Subject": "ZeroTrust(TIC3.0): Security Posture Change Alert",
|
||
"To": "[[parameters('Email')]"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['office365']['connectionId']"
|
||
}
|
||
},
|
||
"method": "post",
|
||
"path": "/v2/Mail"
|
||
}
|
||
}
|
||
},
|
||
"type": "Foreach"
|
||
}
|
||
}
|
||
},
|
||
"parameters": {
|
||
"$connections": {
|
||
"value": {
|
||
"azuresentinel": {
|
||
"connectionName": "[[variables('azuresentinelConnectionName')]",
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('azuresentinelConnectionName'))]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"connectionProperties": {
|
||
"authentication": {
|
||
"type": "ManagedServiceIdentity"
|
||
}
|
||
}
|
||
},
|
||
"office365": {
|
||
"connectionName": "[[variables('office365ConnectionName')]",
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('office365ConnectionName'))]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/office365')]"
|
||
},
|
||
"teams": {
|
||
"connectionName": "[[variables('teamsConnectionName')]",
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('teamsConnectionName'))]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/teams')]"
|
||
}
|
||
}
|
||
}
|
||
}
|
||
},
|
||
"name": "[[parameters('PlaybookName')]",
|
||
"type": "Microsoft.Logic/workflows",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"tags": {
|
||
"hidden-SentinelTemplateName": "Notify-GovernanceComplianceTeam",
|
||
"hidden-SentinelTemplateVersion": "1.0",
|
||
"hidden-SentinelWorkspaceId": "[[variables('workspaceResourceId')]"
|
||
},
|
||
"identity": {
|
||
"type": "SystemAssigned"
|
||
},
|
||
"apiVersion": "2017-07-01",
|
||
"dependsOn": [
|
||
"[[resourceId('Microsoft.Web/connections', variables('azuresentinelConnectionName'))]",
|
||
"[[resourceId('Microsoft.Web/connections', variables('office365ConnectionName'))]",
|
||
"[[resourceId('Microsoft.Web/connections', variables('teamsConnectionName'))]"
|
||
]
|
||
},
|
||
{
|
||
"name": "[[variables('azuresentinelConnectionName')]",
|
||
"properties": {
|
||
"parameterValueType": "Alternative",
|
||
"displayName": "[[variables('azuresentinelConnectionName')]",
|
||
"api": {
|
||
"id": "[[variables('_connection-2')]"
|
||
}
|
||
},
|
||
"type": "Microsoft.Web/connections",
|
||
"kind": "V1",
|
||
"apiVersion": "2016-06-01",
|
||
"location": "[[variables('workspace-location-inline')]"
|
||
},
|
||
{
|
||
"name": "[[variables('office365ConnectionName')]",
|
||
"properties": {
|
||
"displayName": "[[variables('office365ConnectionName')]",
|
||
"api": {
|
||
"id": "[[variables('_connection-3')]"
|
||
}
|
||
},
|
||
"type": "Microsoft.Web/connections",
|
||
"kind": "V1",
|
||
"apiVersion": "2016-06-01",
|
||
"location": "[[variables('workspace-location-inline')]"
|
||
},
|
||
{
|
||
"name": "[[variables('teamsConnectionName')]",
|
||
"properties": {
|
||
"displayName": "[[variables('teamsConnectionName')]",
|
||
"api": {
|
||
"id": "[[variables('_connection-4')]"
|
||
}
|
||
},
|
||
"type": "Microsoft.Web/connections",
|
||
"kind": "V1",
|
||
"apiVersion": "2016-06-01",
|
||
"location": "[[variables('workspace-location-inline')]"
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/metadata",
|
||
"apiVersion": "2022-01-01-preview",
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat('Playbook-', last(split(variables('playbookId1'),'/'))))]",
|
||
"properties": {
|
||
"parentId": "[variables('playbookId1')]",
|
||
"contentId": "[variables('_playbookContentId1')]",
|
||
"kind": "Playbook",
|
||
"version": "[variables('playbookVersion1')]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
}
|
||
}
|
||
}
|
||
],
|
||
"metadata": {
|
||
"title": "Notify-GovernanceComplianceTeam",
|
||
"description": "This Security Orchestration, Automation, & Response (SOAR) capability is designed for configuration with the solution's analytics rules. When analytics rules trigger this automation notifies the governance compliance team of respective details via Teams chat and exchange email. This automation reduces requirements to manually monitor the workbook or analytics rules while increasing response times.",
|
||
"lastUpdateTime": "2022-08-05T00:00:00Z",
|
||
"releaseNotes": [
|
||
{
|
||
"version": "1.0.0",
|
||
"title": "Notify-GovernanceComplianceTeam",
|
||
"notes": [
|
||
"Initial version"
|
||
]
|
||
}
|
||
]
|
||
}
|
||
},
|
||
"packageKind": "Solution",
|
||
"packageVersion": "[variables('_solutionVersion')]",
|
||
"packageName": "[variables('_solutionName')]",
|
||
"packageId": "[variables('_solutionId')]",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"contentId": "[variables('_playbookContentId1')]",
|
||
"contentKind": "Playbook",
|
||
"displayName": "Notify-GovernanceComplianceTeam-ZeroTrust",
|
||
"contentProductId": "[variables('_playbookcontentProductId1')]",
|
||
"id": "[variables('_playbookcontentProductId1')]",
|
||
"version": "[variables('playbookVersion1')]"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentTemplates",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"name": "[variables('playbookTemplateSpecName2')]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"dependsOn": [
|
||
"[extensionResourceId(resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspace')), 'Microsoft.SecurityInsights/contentPackages', variables('_solutionId'))]"
|
||
],
|
||
"properties": {
|
||
"description": "Create-AzureDevOpsTask-ZeroTrust Playbook with template version 3.0.1",
|
||
"mainTemplate": {
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "[variables('playbookVersion2')]",
|
||
"parameters": {
|
||
"PlaybookName": {
|
||
"defaultValue": "Create-AzureDevOpsTask-ZeroTrust",
|
||
"type": "string"
|
||
}
|
||
},
|
||
"variables": {
|
||
"AzureSentinelConnectionName": "[[concat('azuresentinel-', parameters('PlaybookName'))]",
|
||
"AzureDevOpsConnectionName": "[[concat('azuredevops-', parameters('PlaybookName'))]",
|
||
"connection-1": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"_connection-1": "[[variables('connection-1')]",
|
||
"connection-2": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/visualstudioteamservices')]",
|
||
"_connection-2": "[[variables('connection-2')]",
|
||
"workspace-location-inline": "[concat('[resourceGroup().locatio', 'n]')]",
|
||
"workspace-name": "[parameters('workspace')]",
|
||
"workspaceResourceId": "[[resourceId('microsoft.OperationalInsights/Workspaces', variables('workspace-name'))]"
|
||
},
|
||
"resources": [
|
||
{
|
||
"type": "Microsoft.Web/connections",
|
||
"apiVersion": "2016-06-01",
|
||
"name": "[[variables('AzureSentinelConnectionName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"kind": "V1",
|
||
"properties": {
|
||
"displayName": "[[variables('AzureSentinelConnectionName')]",
|
||
"parameterValueType": "Alternative",
|
||
"api": {
|
||
"id": "[[variables('_connection-1')]"
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.Web/connections",
|
||
"apiVersion": "2016-06-01",
|
||
"name": "[[variables('AzureDevOpsConnectionName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"properties": {
|
||
"displayName": "[[variables('AzureDevOpsConnectionName')]",
|
||
"api": {
|
||
"id": "[[variables('_connection-2')]"
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.Logic/workflows",
|
||
"apiVersion": "2017-07-01",
|
||
"name": "[[parameters('PlaybookName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"tags": {
|
||
"hidden-SentinelTemplateName": "Create-AzureDevOpsTask",
|
||
"hidden-SentinelTemplateVersion": "1.0",
|
||
"hidden-SentinelWorkspaceId": "[[variables('workspaceResourceId')]"
|
||
},
|
||
"identity": {
|
||
"type": "SystemAssigned"
|
||
},
|
||
"dependsOn": [
|
||
"[[resourceId('Microsoft.Web/connections', variables('AzureSentinelConnectionName'))]",
|
||
"[[resourceId('Microsoft.Web/connections', variables('AzureDevOpsConnectionName'))]"
|
||
],
|
||
"properties": {
|
||
"state": "Enabled",
|
||
"definition": {
|
||
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
|
||
"actions": {
|
||
"Add_comment_to_incident_(V3)": {
|
||
"inputs": {
|
||
"body": {
|
||
"incidentArmId": "@triggerBody()?['object']?['id']",
|
||
"message": "<p>Azure DevOps Task created: @{body('Create_a_work_item')?['url']}</p>"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['azuresentinel']['connectionId']"
|
||
}
|
||
},
|
||
"method": "post",
|
||
"path": "/Incidents/Comment"
|
||
},
|
||
"runAfter": {
|
||
"Create_a_work_item": [
|
||
"Succeeded"
|
||
]
|
||
},
|
||
"type": "ApiConnection"
|
||
},
|
||
"Create_a_work_item": {
|
||
"inputs": {
|
||
"body": {
|
||
"description": "Incident Description: @{triggerBody()?['object']?['properties']?['description']}\nIncident Severity: @{triggerBody()?['object']?['properties']?['severity']}\nIncident URL: @{triggerBody()?['object']?['properties']?['incidentUrl']}\n",
|
||
"title": "New Microsoft Sentinel Incident: @{triggerBody()?['object']?['properties']?['title']}"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['visualstudioteamservices']['connectionId']"
|
||
}
|
||
},
|
||
"method": "patch",
|
||
"path": "/@{encodeURIComponent('test')}/_apis/wit/workitems/$@{encodeURIComponent('Task')}",
|
||
"queries": {
|
||
"account": "test"
|
||
}
|
||
},
|
||
"type": "ApiConnection"
|
||
}
|
||
},
|
||
"contentVersion": "1.0.0.0",
|
||
"parameters": {
|
||
"$connections": {
|
||
"type": "Object"
|
||
}
|
||
},
|
||
"triggers": {
|
||
"When_Azure_Sentinel_incident_creation_rule_was_triggered": {
|
||
"inputs": {
|
||
"body": {
|
||
"callback_url": "@{listCallbackUrl()}"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['azuresentinel']['connectionId']"
|
||
}
|
||
},
|
||
"path": "/incident-creation"
|
||
},
|
||
"type": "ApiConnectionWebhook"
|
||
}
|
||
}
|
||
},
|
||
"parameters": {
|
||
"$connections": {
|
||
"value": {
|
||
"azuresentinel": {
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('AzureSentinelConnectionName'))]",
|
||
"connectionName": "[[variables('AzureSentinelConnectionName')]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"connectionProperties": {
|
||
"authentication": {
|
||
"type": "ManagedServiceIdentity"
|
||
}
|
||
}
|
||
},
|
||
"visualstudioteamservices": {
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('AzureDevOpsConnectionName'))]",
|
||
"connectionName": "[[variables('AzureDevOpsConnectionName')]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/visualstudioteamservices')]"
|
||
}
|
||
}
|
||
}
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/metadata",
|
||
"apiVersion": "2022-01-01-preview",
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat('Playbook-', last(split(variables('playbookId2'),'/'))))]",
|
||
"properties": {
|
||
"parentId": "[variables('playbookId2')]",
|
||
"contentId": "[variables('_playbookContentId2')]",
|
||
"kind": "Playbook",
|
||
"version": "[variables('playbookVersion2')]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
}
|
||
}
|
||
}
|
||
],
|
||
"metadata": {
|
||
"title": "Create-AzureDevOpsTask",
|
||
"description": "This playbook will create the Azure DevOps task filled with the Microsoft Sentinel incident details.",
|
||
"lastUpdateTime": "2022-08-05T00:00:00Z",
|
||
"tags": [
|
||
"Sync"
|
||
],
|
||
"releaseNotes": [
|
||
{
|
||
"version": "1.0.0",
|
||
"title": "Create Azure DevOps Task",
|
||
"notes": [
|
||
"Initial version"
|
||
]
|
||
}
|
||
]
|
||
}
|
||
},
|
||
"packageKind": "Solution",
|
||
"packageVersion": "[variables('_solutionVersion')]",
|
||
"packageName": "[variables('_solutionName')]",
|
||
"packageId": "[variables('_solutionId')]",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"contentId": "[variables('_playbookContentId2')]",
|
||
"contentKind": "Playbook",
|
||
"displayName": "Create-AzureDevOpsTask-ZeroTrust",
|
||
"contentProductId": "[variables('_playbookcontentProductId2')]",
|
||
"id": "[variables('_playbookcontentProductId2')]",
|
||
"version": "[variables('playbookVersion2')]"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentTemplates",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"name": "[variables('playbookTemplateSpecName3')]",
|
||
"location": "[parameters('workspace-location')]",
|
||
"dependsOn": [
|
||
"[extensionResourceId(resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspace')), 'Microsoft.SecurityInsights/contentPackages', variables('_solutionId'))]"
|
||
],
|
||
"properties": {
|
||
"description": "CreateJiraIssue-ZeroTrust Playbook with template version 3.0.1",
|
||
"mainTemplate": {
|
||
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
|
||
"contentVersion": "[variables('playbookVersion3')]",
|
||
"parameters": {
|
||
"PlaybookName": {
|
||
"defaultValue": "CreateJiraIssue-ZeroTrust",
|
||
"type": "string",
|
||
"metadata": {
|
||
"description": "Incident trigger"
|
||
}
|
||
}
|
||
},
|
||
"variables": {
|
||
"AzureSentinelConnectionName": "[[concat('azuresentinel-', parameters('PlaybookName'))]",
|
||
"JiraConnectionName": "[[concat('jira-', parameters('PlaybookName'))]",
|
||
"connection-1": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"_connection-1": "[[variables('connection-1')]",
|
||
"connection-2": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/jira')]",
|
||
"_connection-2": "[[variables('connection-2')]",
|
||
"workspace-location-inline": "[concat('[resourceGroup().locatio', 'n]')]",
|
||
"workspace-name": "[parameters('workspace')]",
|
||
"workspaceResourceId": "[[resourceId('microsoft.OperationalInsights/Workspaces', variables('workspace-name'))]"
|
||
},
|
||
"resources": [
|
||
{
|
||
"type": "Microsoft.Web/connections",
|
||
"apiVersion": "2016-06-01",
|
||
"name": "[[variables('AzureSentinelConnectionName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"properties": {
|
||
"displayName": "[[variables('AzureSentinelConnectionName')]",
|
||
"parameterValueType": "Alternative",
|
||
"api": {
|
||
"id": "[[variables('_connection-1')]"
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.Web/connections",
|
||
"apiVersion": "2016-06-01",
|
||
"name": "[[variables('jiraConnectionName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"properties": {
|
||
"displayName": "[[variables('jiraConnectionName')]",
|
||
"api": {
|
||
"id": "[[variables('_connection-2')]"
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.Logic/workflows",
|
||
"apiVersion": "2017-07-01",
|
||
"name": "[[parameters('PlaybookName')]",
|
||
"location": "[[variables('workspace-location-inline')]",
|
||
"tags": {
|
||
"hidden-SentinelTemplateName": "CreateJiraIssue-Incident",
|
||
"hidden-SentinelTemplateVersion": "1.0",
|
||
"hidden-SentinelWorkspaceId": "[[variables('workspaceResourceId')]"
|
||
},
|
||
"identity": {
|
||
"type": "SystemAssigned"
|
||
},
|
||
"dependsOn": [
|
||
"[[resourceId('Microsoft.Web/connections', variables('AzureSentinelConnectionName'))]",
|
||
"[[resourceId('Microsoft.Web/connections', variables('JiraConnectionName'))]"
|
||
],
|
||
"properties": {
|
||
"state": "Enabled",
|
||
"definition": {
|
||
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
|
||
"contentVersion": "1.0.0.0",
|
||
"parameters": {
|
||
"$connections": {
|
||
"type": "Object"
|
||
}
|
||
},
|
||
"triggers": {
|
||
"When_Azure_Sentinel_incident_creation_rule_was_triggered": {
|
||
"type": "ApiConnectionWebhook",
|
||
"inputs": {
|
||
"body": {
|
||
"callback_url": "@{listCallbackUrl()}"
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['azuresentinel']['connectionId']"
|
||
}
|
||
},
|
||
"path": "/incident-creation"
|
||
}
|
||
}
|
||
},
|
||
"actions": {
|
||
"Create_a_new_issue": {
|
||
"type": "ApiConnection",
|
||
"inputs": {
|
||
"body": {
|
||
"fields": {
|
||
"description": "Incident description: @{triggerBody()?['object']?['properties']?['description']};\nSeverity: @{triggerBody()?['object']?['properties']?['severity']};\nIncident URL: @{triggerBody()?['object']?['properties']?['incidentUrl']}",
|
||
"issuetype": {
|
||
"id": "10007"
|
||
},
|
||
"summary": "@triggerBody()?['object']?['properties']?['title']"
|
||
}
|
||
},
|
||
"host": {
|
||
"connection": {
|
||
"name": "@parameters('$connections')['Jira']['connectionId']"
|
||
}
|
||
},
|
||
"method": "post",
|
||
"path": "/issue",
|
||
"queries": {
|
||
"projectKey": "SOC"
|
||
}
|
||
}
|
||
}
|
||
}
|
||
},
|
||
"parameters": {
|
||
"$connections": {
|
||
"value": {
|
||
"azuresentinel": {
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('AzureSentinelConnectionName'))]",
|
||
"connectionName": "[[variables('AzureSentinelConnectionName')]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/azuresentinel')]",
|
||
"connectionProperties": {
|
||
"authentication": {
|
||
"type": "ManagedServiceIdentity"
|
||
}
|
||
}
|
||
},
|
||
"Jira": {
|
||
"connectionId": "[[resourceId('Microsoft.Web/connections', variables('jiraConnectionName'))]",
|
||
"connectionName": "[[variables('jiraConnectionName')]",
|
||
"id": "[[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Web/locations/', variables('workspace-location-inline'), '/managedApis/jira')]"
|
||
}
|
||
}
|
||
}
|
||
}
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/metadata",
|
||
"apiVersion": "2022-01-01-preview",
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/',concat('Playbook-', last(split(variables('playbookId3'),'/'))))]",
|
||
"properties": {
|
||
"parentId": "[variables('playbookId3')]",
|
||
"contentId": "[variables('_playbookContentId3')]",
|
||
"kind": "Playbook",
|
||
"version": "[variables('playbookVersion3')]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
}
|
||
}
|
||
}
|
||
],
|
||
"metadata": {
|
||
"title": "Create Jira Issue",
|
||
"description": "This playbook will open a Jira Issue when a new incident is opened in Microsoft Sentinel.",
|
||
"prerequisites": [
|
||
"1. Jira instance (ex. xyz.atlassian.net)",
|
||
"2. Jira API",
|
||
"3. Username."
|
||
],
|
||
"lastUpdateTime": "2022-08-05T00:00:00Z",
|
||
"tags": [
|
||
"Sync"
|
||
],
|
||
"releaseNotes": [
|
||
{
|
||
"version": "1.0.0",
|
||
"title": "Create Jira Issue",
|
||
"notes": [
|
||
"Initial version"
|
||
]
|
||
}
|
||
]
|
||
}
|
||
},
|
||
"packageKind": "Solution",
|
||
"packageVersion": "[variables('_solutionVersion')]",
|
||
"packageName": "[variables('_solutionName')]",
|
||
"packageId": "[variables('_solutionId')]",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"contentId": "[variables('_playbookContentId3')]",
|
||
"contentKind": "Playbook",
|
||
"displayName": "CreateJiraIssue-ZeroTrust",
|
||
"contentProductId": "[variables('_playbookcontentProductId3')]",
|
||
"id": "[variables('_playbookcontentProductId3')]",
|
||
"version": "[variables('playbookVersion3')]"
|
||
}
|
||
},
|
||
{
|
||
"type": "Microsoft.OperationalInsights/workspaces/providers/contentPackages",
|
||
"apiVersion": "2023-04-01-preview",
|
||
"location": "[parameters('workspace-location')]",
|
||
"properties": {
|
||
"version": "3.0.1",
|
||
"kind": "Solution",
|
||
"contentSchemaVersion": "3.0.0",
|
||
"displayName": "ZeroTrust(TIC3.0)",
|
||
"publisherDisplayName": "Microsoft Sentinel, Microsoft Corporation",
|
||
"descriptionHtml": "<p><strong>Note:</strong> <em>There may be <a href=\"https://aka.ms/sentinelsolutionsknownissues\">known issues</a> pertaining to this Solution, please refer to them before installing.</em></p>\n<p>The Microsoft Sentinel Zero Trust (TIC 3.0) solution provides a mechanism for viewing log queries aligned to Zero Trust and Trusted Internet Connections models across the Microsoft and partner ecosystem. This solution enables governance and compliance teams to design, build, monitor, and respond to Zero Trust (TIC 3.0) requirements across 25+ Microsoft and 3rd party products. The solution includes the new Zero Trust (TIC 3.0) Workbook, (1) Analytics Rule, and (3) Playbooks. While only Microsoft Sentinel and Microsoft Defender for Cloud are required to get started, the solution is enhanced with numerous Microsoft offerings. This Solution enables Security Architects, Engineers, SecOps Analysts, Managers, and IT Pros to gain situational awareness visibility for the security posture of cloud, multi-cloud, hybrid, and on-premise workloads. For more information, see 💡<a href=\"https://www.microsoft.com/en-in/security/business/zero-trust?rtc=1\">Microsoft Zero Trust Model</a> 💡<a href=\"https://www.cisa.gov/tic\">Trusted Internet Connections: Core Guidance Documents</a></p>\n<p>Microsoft Sentinel Solutions provide a consolidated way to acquire Microsoft Sentinel content like data connectors, workbooks, analytics, and automations in your workspace with a single deployment step.</p>\n<p><strong>Workbooks:</strong> 1, <strong>Analytic Rules:</strong> 1, <strong>Playbooks:</strong> 3</p>\n<p><a href=\"https://aka.ms/azuresentinel\">Learn more about Microsoft Sentinel</a> | <a href=\"https://aka.ms/azuresentinelsolutionsdoc\">Learn more about Solutions</a></p>\n",
|
||
"contentKind": "Solution",
|
||
"contentProductId": "[variables('_solutioncontentProductId')]",
|
||
"id": "[variables('_solutioncontentProductId')]",
|
||
"icon": "<img src=\"https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Workbooks/Images/Logos/Azure_Sentinel.svg\" width=\"75px\" height=\"75px\">",
|
||
"contentId": "[variables('_solutionId')]",
|
||
"parentId": "[variables('_solutionId')]",
|
||
"source": {
|
||
"kind": "Solution",
|
||
"name": "ZeroTrust(TIC3.0)",
|
||
"sourceId": "[variables('_solutionId')]"
|
||
},
|
||
"author": {
|
||
"name": "Microsoft",
|
||
"email": "[variables('_email')]"
|
||
},
|
||
"support": {
|
||
"name": "Microsoft Corporation",
|
||
"email": "support@microsoft.com",
|
||
"tier": "Microsoft",
|
||
"link": "https://support.microsoft.com"
|
||
},
|
||
"dependencies": {
|
||
"operator": "AND",
|
||
"criteria": [
|
||
{
|
||
"kind": "Workbook",
|
||
"contentId": "[variables('_workbookContentId1')]",
|
||
"version": "[variables('workbookVersion1')]"
|
||
},
|
||
{
|
||
"kind": "AnalyticsRule",
|
||
"contentId": "[variables('analyticRuleObject1')._analyticRulecontentId1]",
|
||
"version": "[variables('analyticRuleObject1').analyticRuleVersion1]"
|
||
},
|
||
{
|
||
"kind": "Playbook",
|
||
"contentId": "[variables('_Notify_GovernanceComplianceTeam-ZeroTrust')]",
|
||
"version": "[variables('playbookVersion1')]"
|
||
},
|
||
{
|
||
"kind": "Playbook",
|
||
"contentId": "[variables('_Open_DevOpsTaskRecommendation-ZeroTrust')]",
|
||
"version": "[variables('playbookVersion2')]"
|
||
},
|
||
{
|
||
"kind": "Playbook",
|
||
"contentId": "[variables('_Open_JIRATicketRecommendation-ZeroTrust')]",
|
||
"version": "[variables('playbookVersion3')]"
|
||
}
|
||
]
|
||
},
|
||
"firstPublishDate": "2021-10-20",
|
||
"providers": [
|
||
"Microsoft"
|
||
],
|
||
"categories": {
|
||
"domains": [
|
||
"Identity",
|
||
"Security - Others",
|
||
"Compliance",
|
||
"Security - Automation (SOAR)"
|
||
]
|
||
}
|
||
},
|
||
"name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/', variables('_solutionId'))]"
|
||
}
|
||
],
|
||
"outputs": {}
|
||
}
|