зеркало из https://github.com/Azure/acs-engine.git
* Remove trailing whitespaces in parts/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in pkg/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in examples/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in docs/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in test/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in extensions/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in .circleci/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in jenkins/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> * Remove trailing whitespaces in scripts/ Signed-off-by: Sylvain Rabot <s.rabot@lectra.com> |
||
|---|---|---|
| .. | ||
| README.md | ||
| dcos.json | ||
README.md
Private Registry Support
ACS can deploy credentials to private registries to agent nodes DC/OS clusters.
The credentials are specified in the orchestrator profile in the apimodel:
"properties": {
"orchestratorProfile": {
"orchestratorType": "DCOS",
"dcosConfig" : {
"Registry" : "",
"RegistryUser" : "",
"RegistryPassword" : ""
}
},
The agent provisioning process will then create a tar archive containing a docker config as documented at: Using a Private Docker Registry
Example
Let's provision a DC/OS cluster with credentials to an Azure Container Registry deployed to every agent node.
-
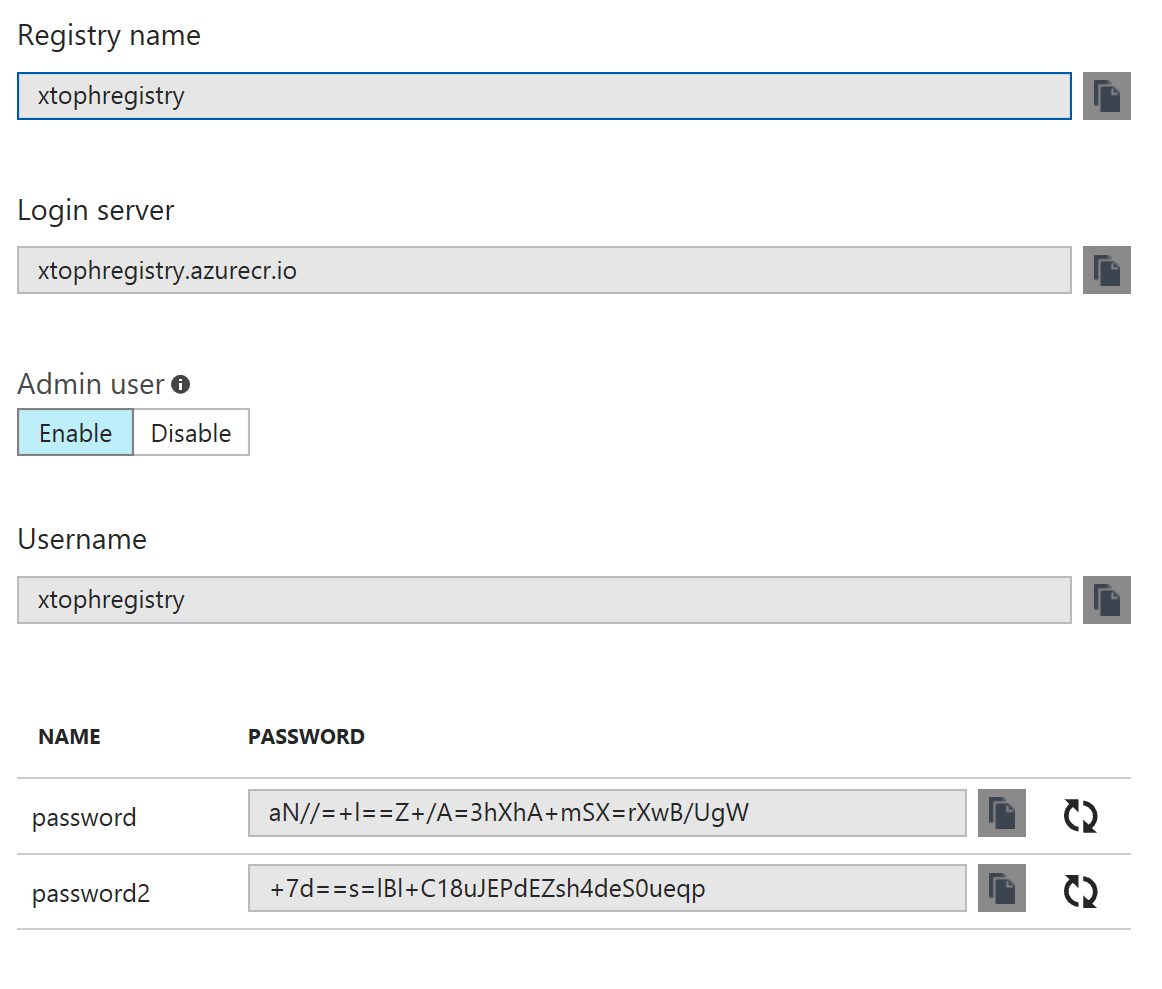
Enable Admin Access and note the registry credentials
-
Clone acs-engine and start the container with the dev environment.
-
Edit the API model to include the credentials
"properties": {
"orchestratorProfile": {
"orchestratorType": "DCOS",
"registry" : "xtophregistry.azurecr.io",
"registryUser" : "xtophregistry",
"registryPassword" : "aN//=+l==Z+/A=3hXhA+mSX=rXwB/UgW"
},
- Run acs-engine to create ARM templates
./acs-engine generate examples/dcos-private-registry/dcos.json
- Deploy the cluster
az group create -l eastus -n cluster-rg
az group deployment create -g cluster-rg --template-file _output/dcoscluster/azuredeploy.json --parameters @_output/dcoscluster/azuredeploy.parameters.json
-
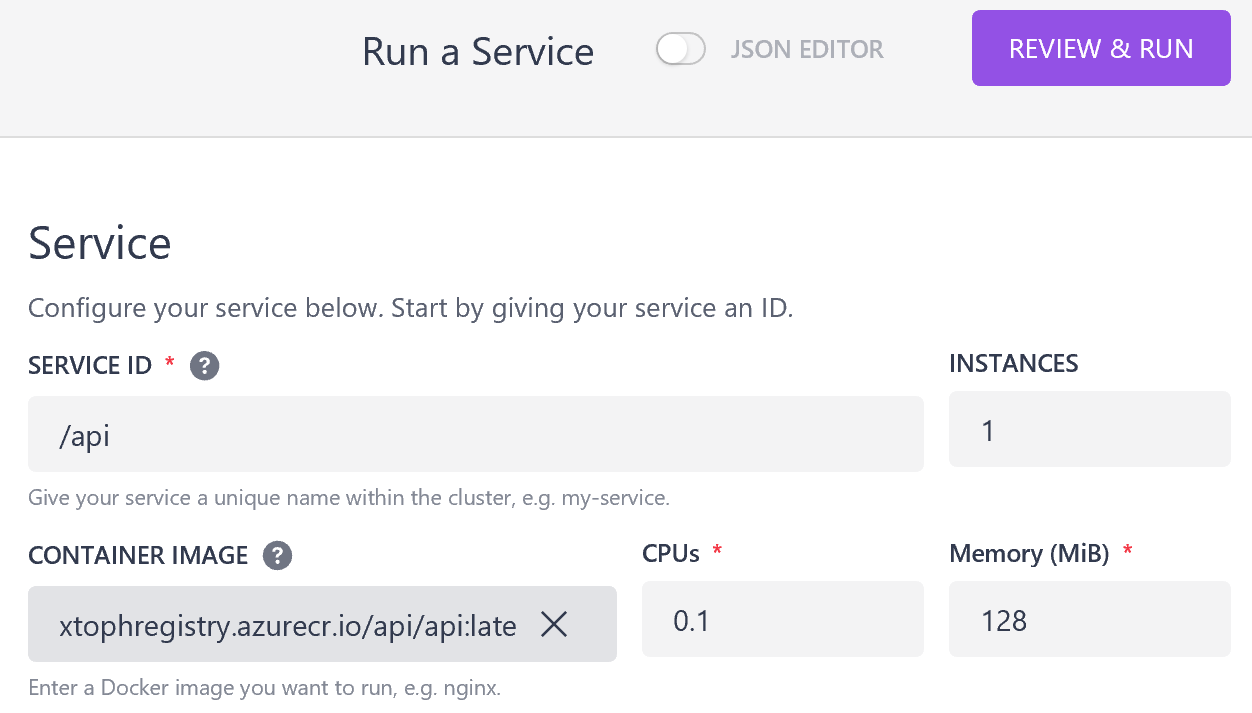
Create a Service to deploy a container from the ACR
-
Add the credential path on the agent using the JSON editor

-
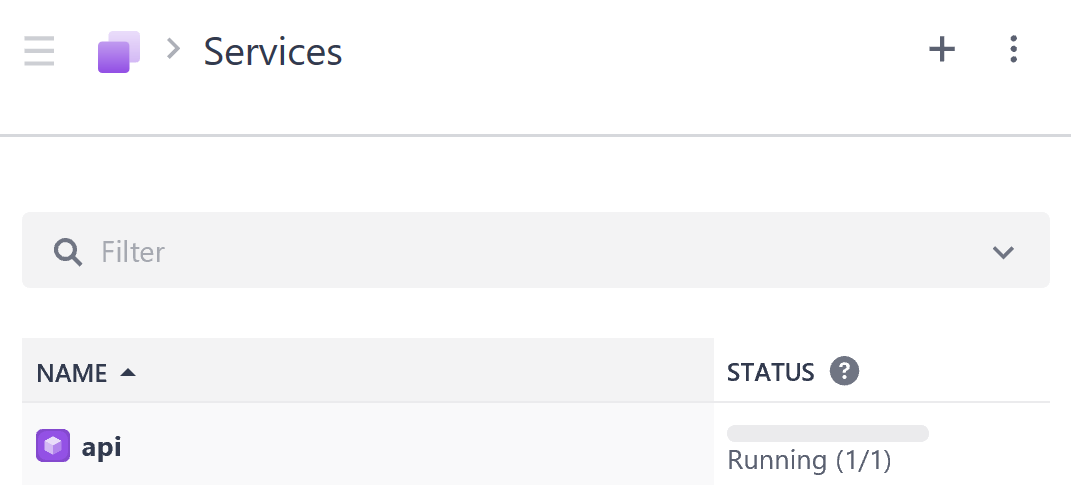
See the Service running
-
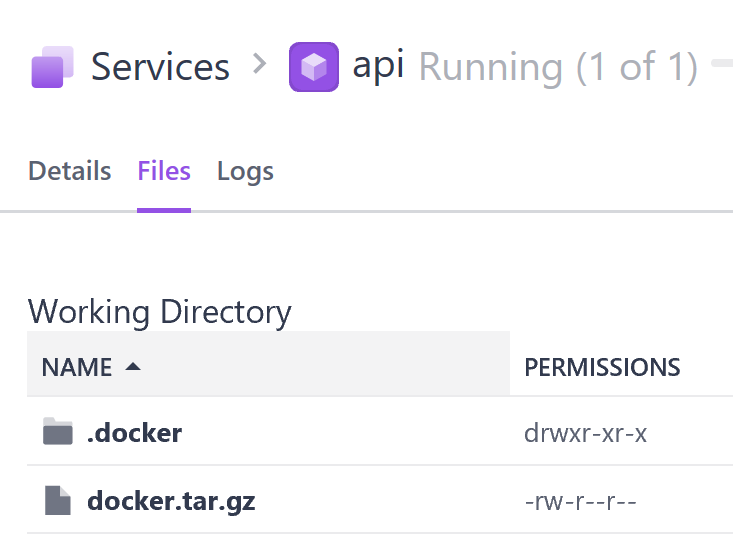
Check the credential deployment
Limitations
- The API model currenlty only supports credentials to a single registry.
- Not tested with Kubernetes clusters
- Credentials have to be updated on each node