|
|
||
|---|---|---|
| .. | ||
| images | ||
| README.md | ||
README.md
Troubleshooting
New-AzRoleAssignment (Failed)
Symptoms
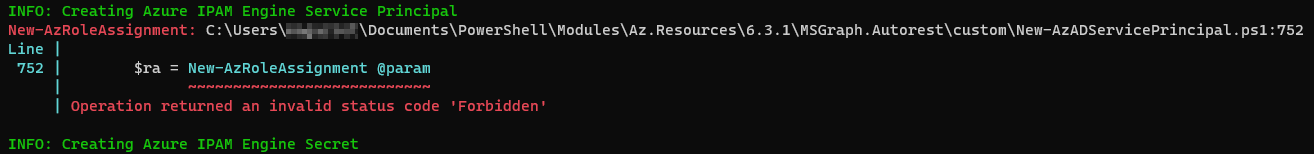
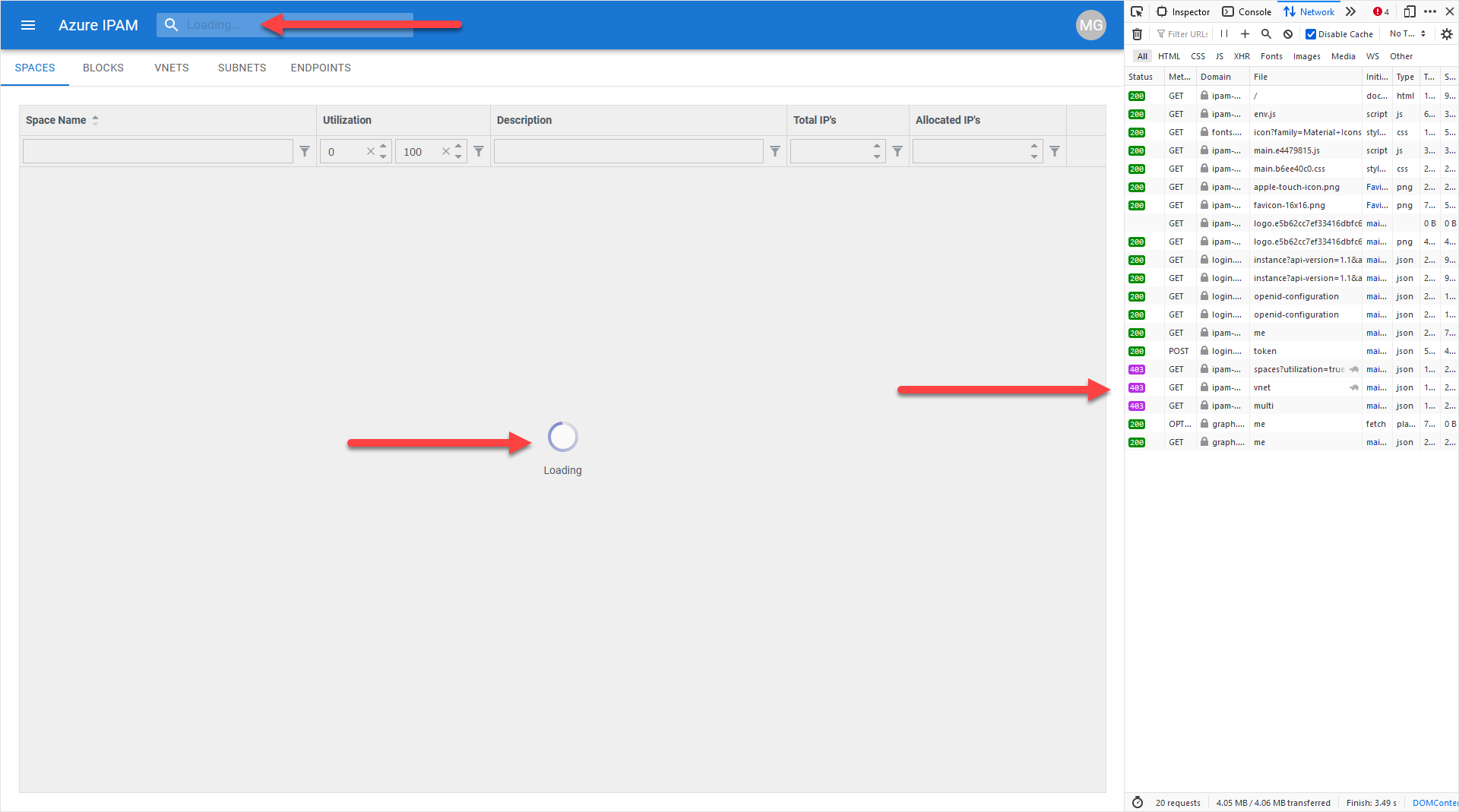
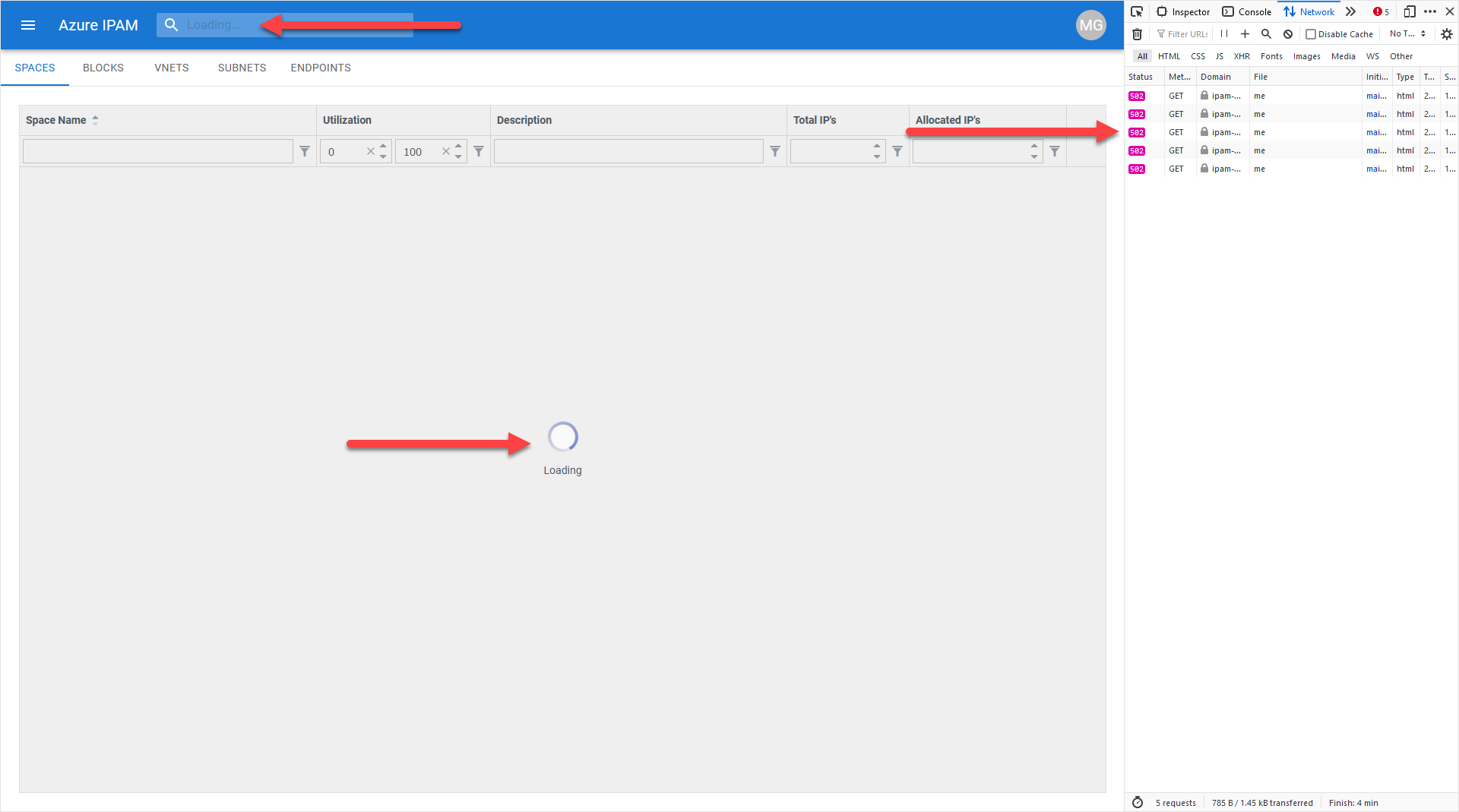
During the deployment of Azure IPAM, you see an error similar to the following:
HTTP 502 responses are visible for the "spaces/vnet/multi" calls in the Developer Tools networking view.
- An error in the Application Log for the App Service stating that the Access is denied to the requested resource. The user might not have enough permission.
Verify
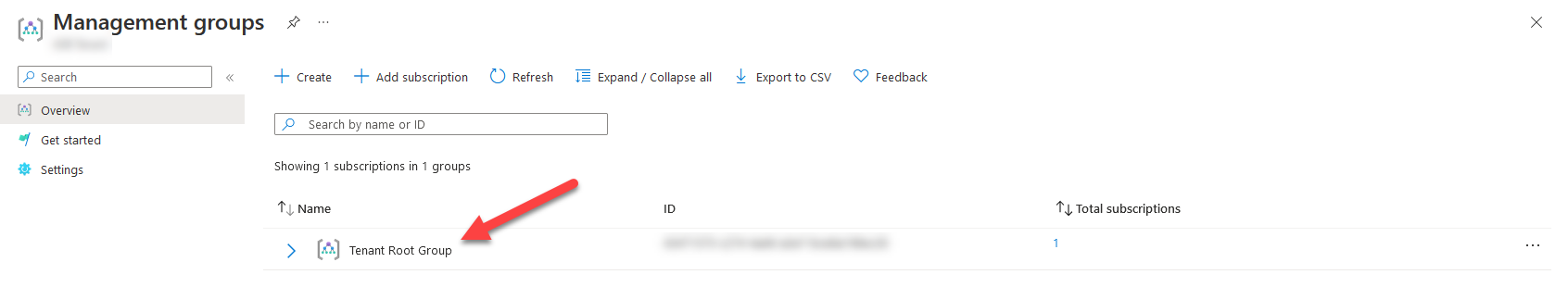
You can check to see if you have the necessary permissions on the Tenant Root Group in the Azure Portal by navigating to Management Groups
If you cannot click on the Tenant Root Group, then you likely don't have access to the Tenant Root Group at all.
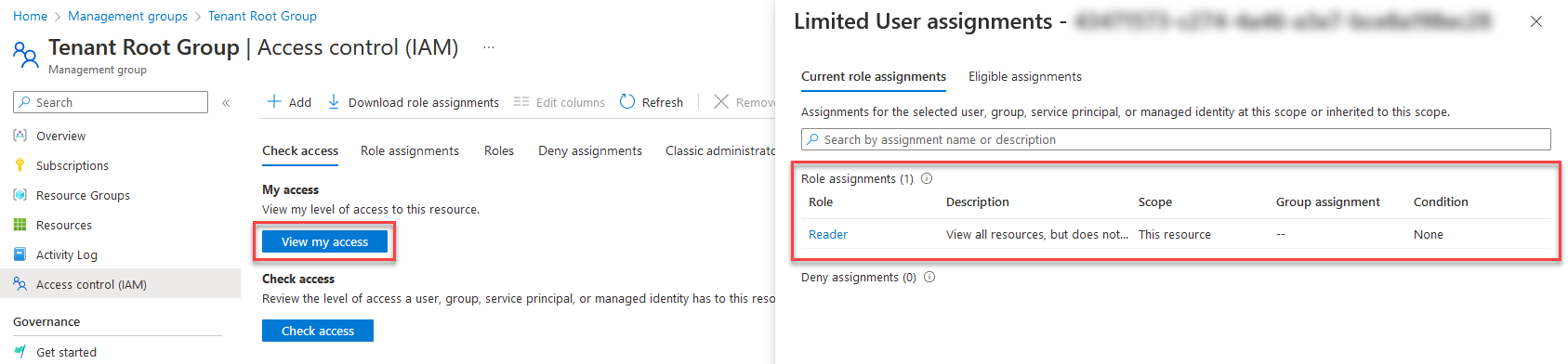
Once you select the Tenant Root Group, under Access Control (IAM) you can click on View my access to see what RBAC permissions your currently logged in user has.
You can see from the above image, this user only has the Reader role, which isn't sufficient to deploy the Azure IPAM solution.
Resolve
Contact your Azure Administrator (or equivalent) to request a role which has Microsoft.Authorization/roleAssignments/write at the Tenant Root Group level.
This role could be one of the following:
- Owner
- User Access Administrator
- Custom Role with allow permissions of
Microsoft.Authorization/roleAssignments/write
Notes
You can read more about the requirements for deploying Azure IPAM in the Prerequisites section of the deployment guide.
New-MgOauth2PermissionGrant (Failed)
Symptoms
During the deployment of Azure IPAM, you see an error similar to the following:
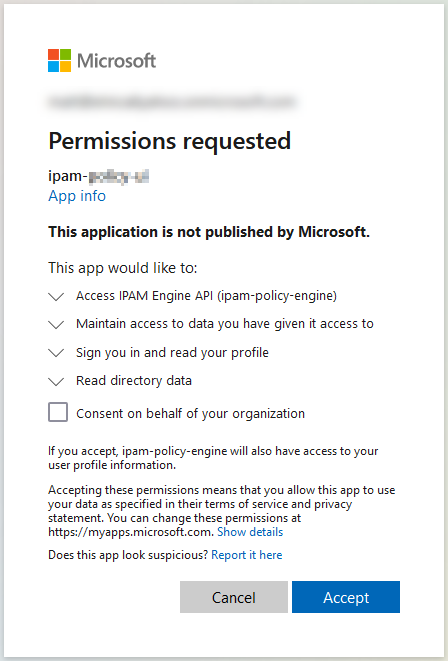
When authenticating to Azure IPAM for the first time, you are presented with a Permissions Requested screen.
Verify
The role of Global Administrator is required to deploy the Azure IPAM solution. This role is needed to grant admin consent for the API permissions used by the Azure IPAM App Registrations.
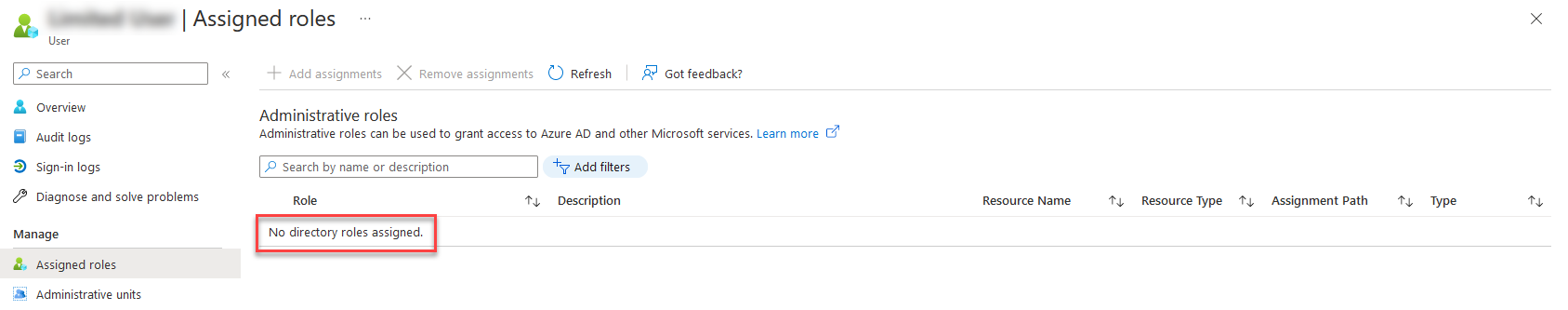
Navigate to your user in Azure Active Directory and check your current Role Assignments.
You can see from the image above that the Global Administrator role is not present.
Resolve
Contact your Azure Active Directory Administrator (or equivalent) to request the Global Administrator role.
Alternatively, if your organization (like many) has separate groups whom manage Azure Active Directory permissions and Azure infrastructure, you can leverage the two-step deployment method for Azure IPAM where a member of the Global Administrators can deploy the required App Registrations, then pass the generated Parameters file to the Azure Infrastructure team to complete the deployment.
Here are the steps from the Deployment section:
Notes
You can read more about the requirements for deploying Azure IPAM in the Prerequisites section of the deployment guide.
DisableKeyBasedMetadataWriteAccess (Cosmos DB)
Symptoms
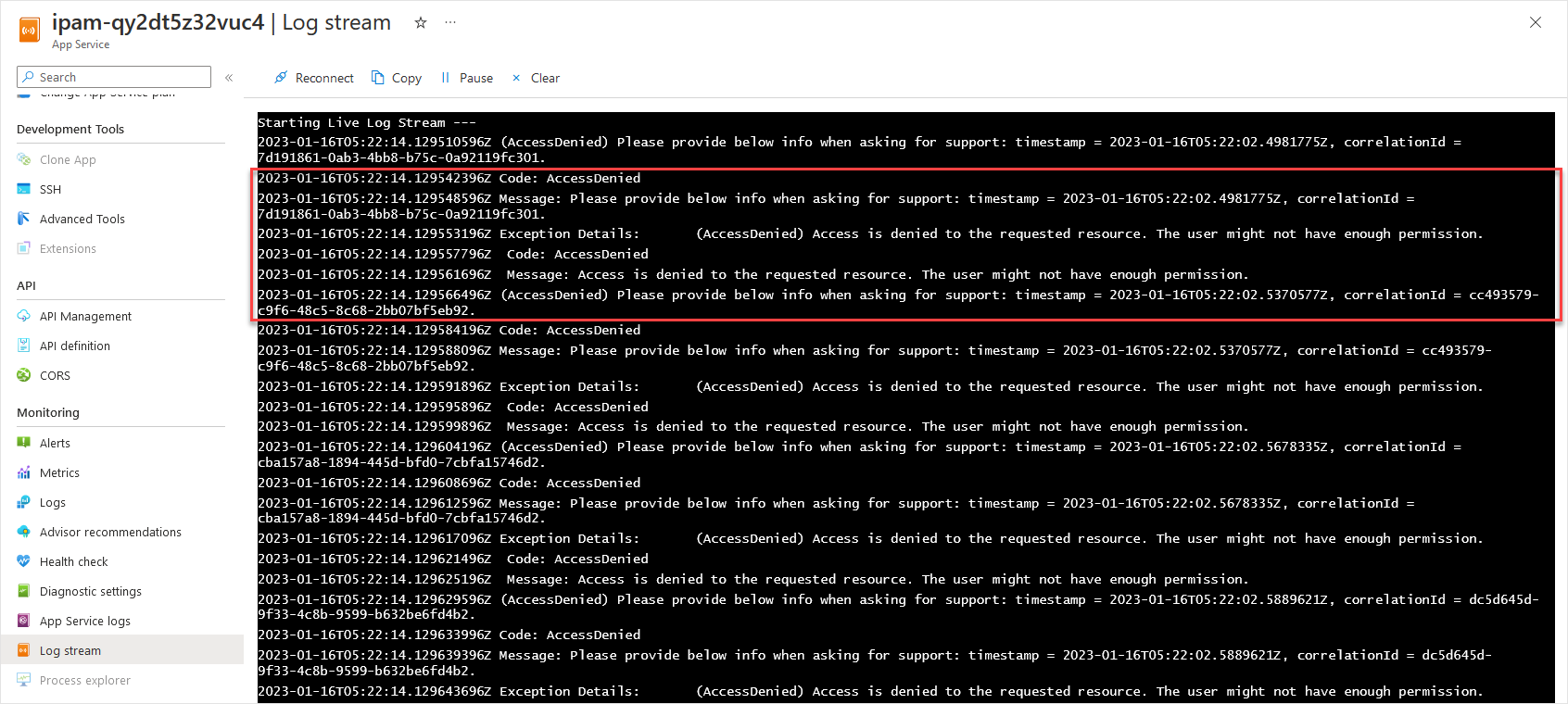
- Spaces, Blocks, Virtual Networks, Subnets, and Endpoints fail to load
- HTTP 502 responses are visible for the "me" call in the Developer Tools networking view
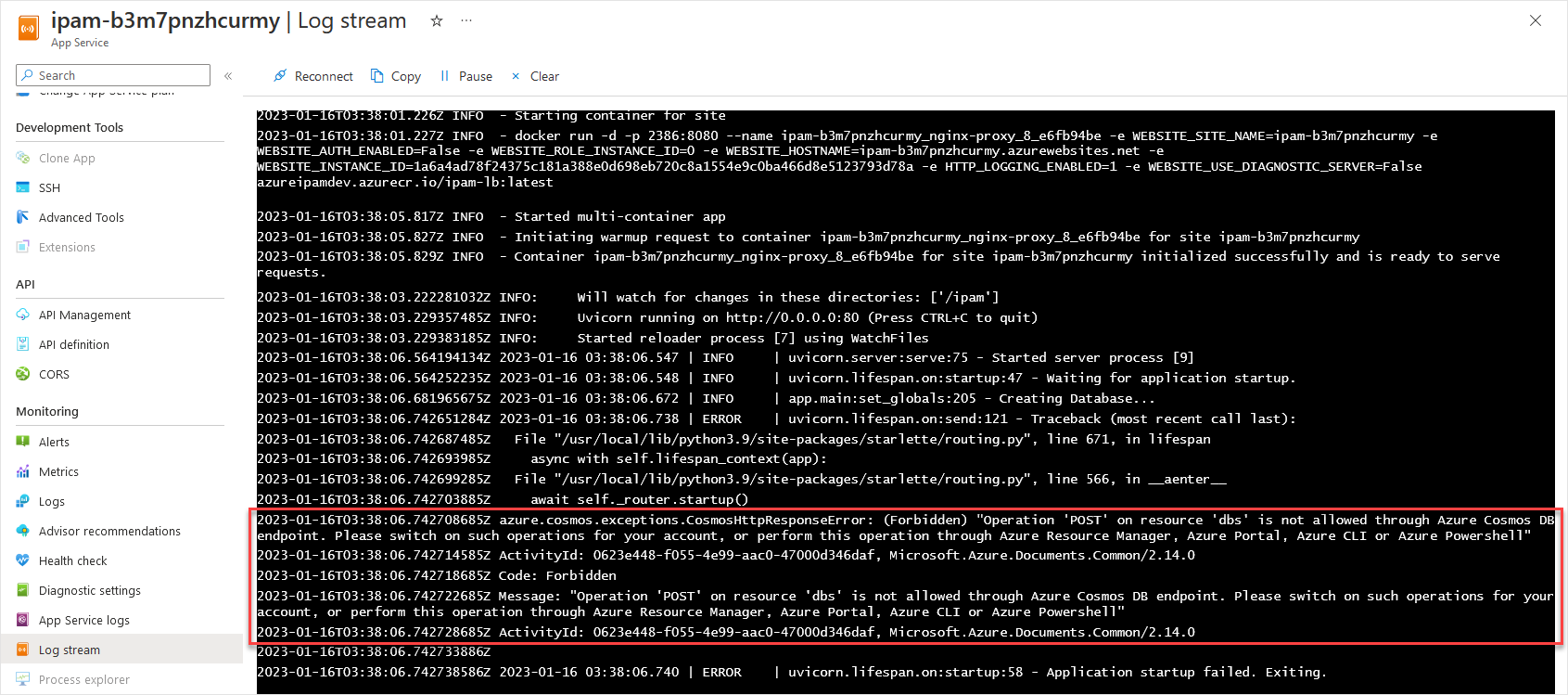
- An error in the Application Log for the App Service stating that the Operation...is not allow through the Azure Cosmos DB endpoint.
Verify
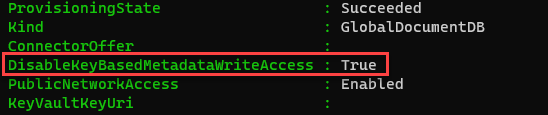
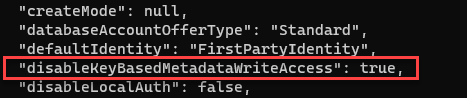
You can check to see if the flag DisableKeyBasedMetadataWriteAccess is set on your Cosmos DB resource by running one of the following commands:
Azure PowerShell
Get-AzCosmosDBAccount -ResourceGroupName <ResourceGroupName> -Name <CosmosDBAccountName>
Azure CLI
az cosmosdb show --resource-group <ResourceGroupName> --name <CosmosDBAccountName>
Resolve
Set the DisableKeyBasedMetadataWriteAccess flag to false using one of the following commands:
Azure PowerShell
Update-AzCosmosDBAccount -ResourceGroupName <ResourceGroupName> -Name <CosmosDBAccountName> -DisableKeyBasedMetadataWriteAccess $false
Azure CLI
az cosmosdb update --resource-group <ResourceGroupName> --name <CosmosDBAccountName> --disable-key-based-metadata-write-access false
Notes
This flag may have been set by Azure Policy. You can find more details about this policy here under Azure Cosmos DB key based metadata write access should be disabled. You may need to contact your policy administrator to request an exception for Azure IPAM.
Additionally this issue only applies to legacy deployments of Azure IPAM (prior to v3.0.0) as the latest versions use SQL role-based access control to read/write data from Cosmos DB.