* Link to mission lz edge * Update Software Bill of Materials (SBOM) * Added "Hub" to ASH * Update Software Bill of Materials (SBOM) Co-authored-by: Microsoft.VisualStudio.Services.TFS <> |
||
|---|---|---|
| .azure-devops | ||
| .devcontainer | ||
| .github | ||
| .vscode | ||
| _manifest | ||
| docs | ||
| src | ||
| .gitattributes | ||
| .gitignore | ||
| CODE_OF_CONDUCT.md | ||
| CONTRIBUTING.md | ||
| LICENSE | ||
| NOTICE | ||
| README.md | ||
| SECURITY.md | ||
| SUPPORT.md | ||
README.md
Mission LZ
Mission Landing Zone is a highly opinionated Infrastructure-as-Code (IaC) template which IT oversight organizations can use to create a cloud management system to deploy Azure environments for their workloads and teams.
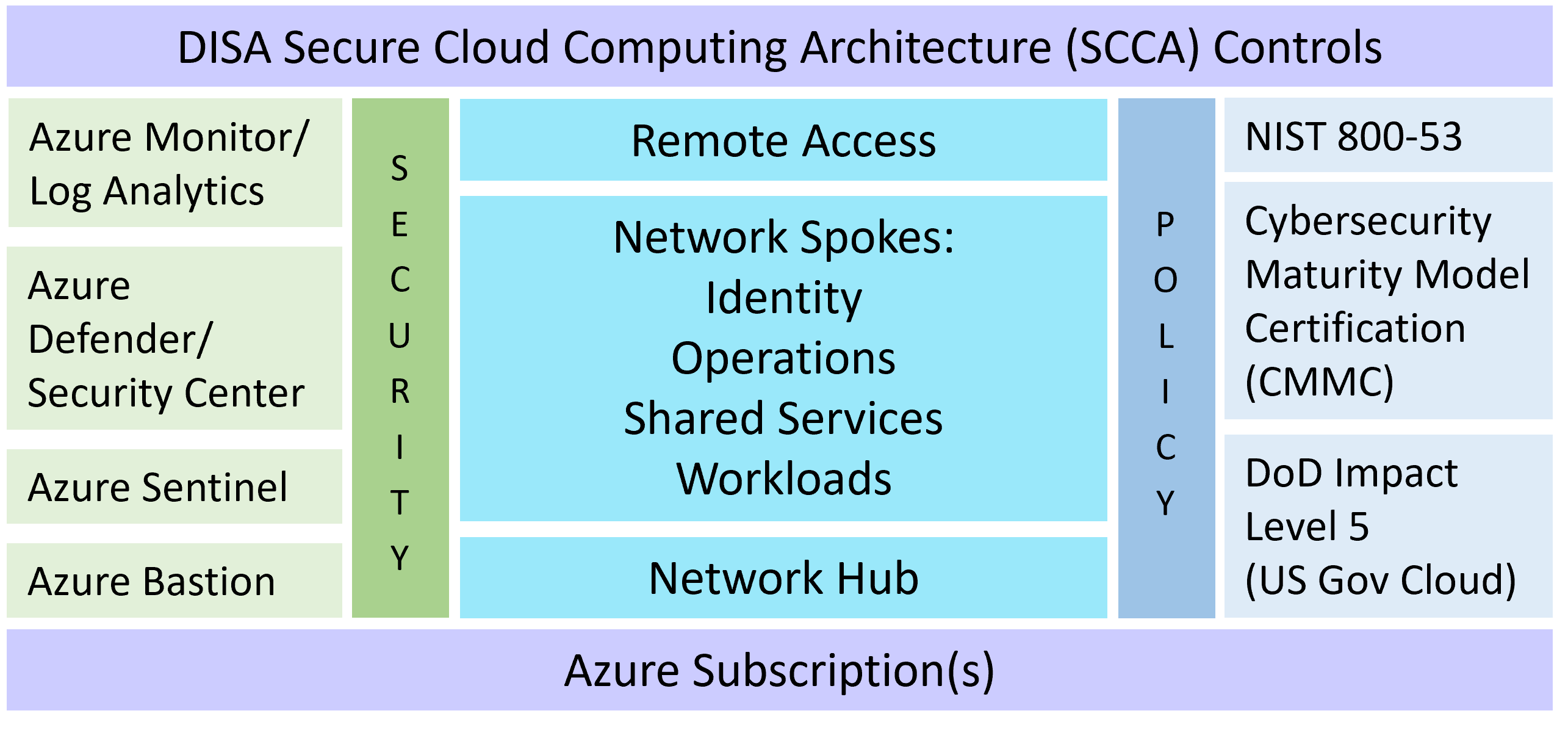
Mission Landing Zone addresses a narrowly scoped, specific need for a Secure Cloud Computing Architecture (SCCA) compliant hub and spoke infrastructure.
- Designed for US Government mission customers
- Implements SCCA controls following Microsoft's SACA implementation guidance
- Deployable in Azure commercial, Azure Government, Azure Government Secret, and Azure Government Top Secret clouds
- A simple solution with low configuration and narrow scope
- Written as Bicep and Terraform templates
Mission Landing Zone is the right solution when:
- A simple, secure, and scalable hub and spoke infrastructure is needed.
- A central IT team is administering cloud resources on behalf of other teams and workloads.
- There is a need to implement SCCA.
- Hosting any workload requiring a secure environment, for example: data warehousing, AI/ML, and containerized applications.
Design goals include:
- A simple, minimal set of code that is easy to configure
- Good defaults that allow experimentation and testing in a single subscription
- Deployment via command line or with a user interface
- 100% Azure PaaS products
Our intent is to enable IT Admins to use this software to:
- Test and evaluate the landing zone using a single Azure subscription
- Develop a known good configuration that can be used for production with multiple Azure subscriptions
- Customize the deployment configuration to suit specific needs
- Deploy multiple customer workloads in production
What is a Landing Zone?
A landing zone is networking infrastructure configured to provide a secure environment for hosting workloads.
Quickstart
You can deploy Mission Landing Zone from the Azure Portal or by executing an Azure CLI command.
You must have Owner RBAC permissions to the subscription(s) you deploy Mission Landing Zone into.
Deploy from the Azure Portal
- Deploy Mission Landing Zone into
AzureCloudorAzureUsGovernmentfrom the Azure Portal:Azure Commercial Azure Government
- After a successful deployment, see our examples directory for how to extend the capabilities of Mission Landing Zone.
Deploy using the Azure CLI
-
Clone the repository and change directory to the root of the repository:
git clone https://github.com/Azure/missionlz.git cd missionlz -
Deploy Mission Landing Zone with the
az deployment sub createcommand. For a quickstart, we suggest a test deployment into the current AZ CLI subscription setting these parameters:--name: (optional) The deployment name, which is visible in the Azure Portal under Subscription/Deployments.--location: (required) The Azure region to store the deployment metadata.--template-file: (required) The file path to themlz.biceptemplate.--parameters resourcePrefix=<value>: (required) TheresourcePrefixBicep parameter is used to generate names for your resources. It is the only required parameter in the Bicep file. You can set it to any alphanumeric value (without whitespace) that is between 3-10 characters. You can omit this parameter and theaz deployment sub createcommand will prompt you to enter a value.
Here's an example:
az deployment sub create \ --name myMlzDeployment \ --location eastus \ --template-file ./src/bicep/mlz.bicep \ --parameters resourcePrefix="myMlz" -
After a successful deployment, see our examples directory for how to extend the capabilities of Mission Landing Zone.
Don't have Azure CLI? Here's how to get started with Azure Cloud Shell in your browser: https://docs.microsoft.com/en-us/azure/cloud-shell/overview
For more detailed deployment instructions, see our deployment guides for Bicep and Terraform.
Scope
Mission LZ has the following scope:
- Hub and spoke networking intended to comply with SCCA controls
- Predefined spokes for identity, operations, shared services, and workloads
- Ability to create multiple, isolated workloads or team subscriptions
- Remote access
- Compatibility with SCCA compliance (and other compliance frameworks)
- Security using standard Azure tools with sensible defaults
- Azure Policy initiatives
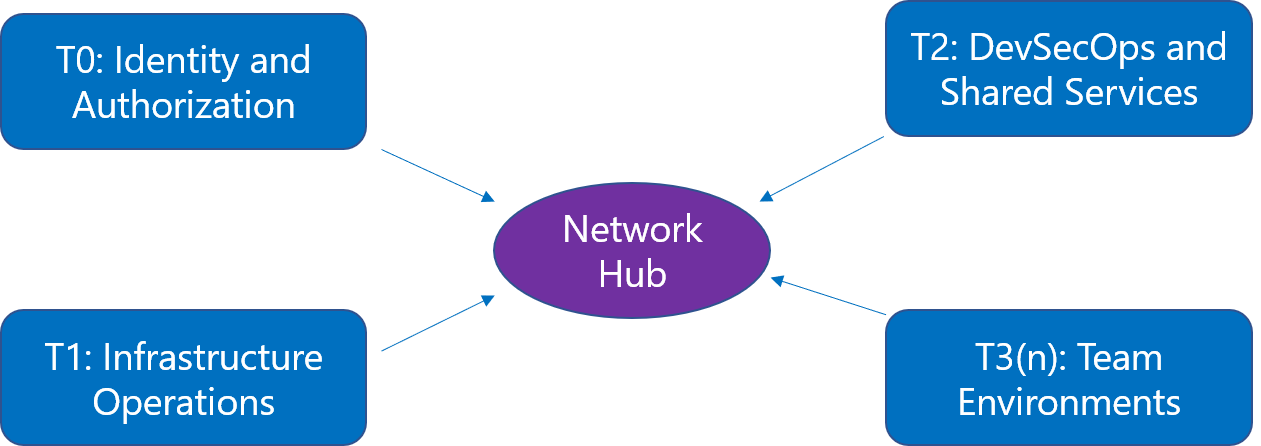
Networking
Networking is set up in a hub and spoke design, separated by tiers: T0 (Identity and Authorization), T1 (Infrastructure Operations), T2 (DevSecOps and Shared Services), and multiple T3s (Workloads). Access control can be configured to allow separation of duties between all tiers.
Subscriptions
Most customers will deploy each tier to a separate Azure subscription, but multiple subscriptions are not required. A single subscription deployment is good for a testing and evaluation, or possibly a small IT Admin team.
Firewall
All network traffic is directed through the firewall residing in the Network Hub resource group. The firewall is configured as the default route for all the T0 (Identity and Authorization) through T3 (workload/team environments) resource groups as follows:
| Name | Address prefix | Next hop type | Next hop IP address |
|---|---|---|---|
| default_route | 0.0.0.0/0 | Virtual Appliance | 10.0.100.4 |
The default firewall configured for MLZ is Azure Firewall Premium.
Presently, there are two firewall rules configured to ensure access to the Azure Portal and to facilitate interactive logon via PowerShell and Azure CLI, all other traffic is restricted by default. Below are the collection of rules configured for Azure Commercial and Azure Government clouds:
| Rule Collection Priority | Rule Collection Name | Rule name | Source | Port | Protocol |
|---|---|---|---|---|---|
| 100 | AllowAzureCloud | AzureCloud | * | * | Any |
| 110 | AzureAuth | msftauth | * | Https:443 | aadcdn.msftauth.net, aadcdn.msauth.net |
To deploy Mission LZ using Azure Stack Hub and an F5 BIG-IP Virtual Edition instead of Azure Firewall Premium, there is an alternate repository with instructions found here.
Getting Started
See the Deployment Guide for Bicep and the Deployment Guide for Terraform in the docs folder.
Product Roadmap
See the Projects page for the release timeline and feature areas.
Here's a summary of what Mission Landing Zone deploys of as of December 2021:

Contributing
This project welcomes contributions and suggestions. See our Contributing Guide for details.
Feedback, Support, and How to Contact Us
Please see the Support and Feedback Guide. To report a security issue please see our security guidance.
Trademarks
This project may contain trademarks or logos for projects, products, or services. Authorized use of Microsoft trademarks or logos is subject to and must follow Microsoft's Trademark & Brand Guidelines. Use of Microsoft trademarks or logos in modified versions of this project must not cause confusion or imply Microsoft sponsorship. Any use of third-party trademarks or logos are subject to those third-party's policies.
Nightly Build Status
| Deployment Type | Azure Cloud | Azure Government |
|---|---|---|
| Bicep | ||
| Terraform |