README links to context file docu (#16)
Multiple users complained that contexts and context files are not discussed or explained. These are outside the scope of this project.
This commit is contained in:
Родитель
4c3aa1225a
Коммит
9104c2dd53
|
|
@ -22,6 +22,8 @@ After installing the scanner from the Azure DevOps Marketplace, you will need to
|
|||
|
||||
- By default, the task will run a baseline scan.
|
||||
|
||||
- Custom configuration for ZAP may be provided through a "context file". This is ZAP functionality, and [is documented by the official project team](https://www.zaproxy.org/docs/desktop/start/features/contexts/).
|
||||
|
||||
#### Baseline Scan Notes
|
||||
|
||||
> The baseline scan will spider the target for 1 minute and then wait for the passive scanning to complete. This makes for a relatively short-running scan that doesn't perform any attacks.
|
||||
|
|
@ -38,6 +40,8 @@ After installing the scanner from the Azure DevOps Marketplace, you will need to
|
|||
|
||||
> - By default, the scan will be performed without much effort at scoping for tech, excluded URL endpoints, etc.., but you can provide a context file for a more focused scan. The context file is useful to take full advantage of the baseline scans minute of crawling or, to narrow the scope of a full-scan in aggressive mode to keep the duration as short as possible. To accomplish this, check the "Provide Context File" box and provide the path to a context file in your source repository relative to the build copy of the source. 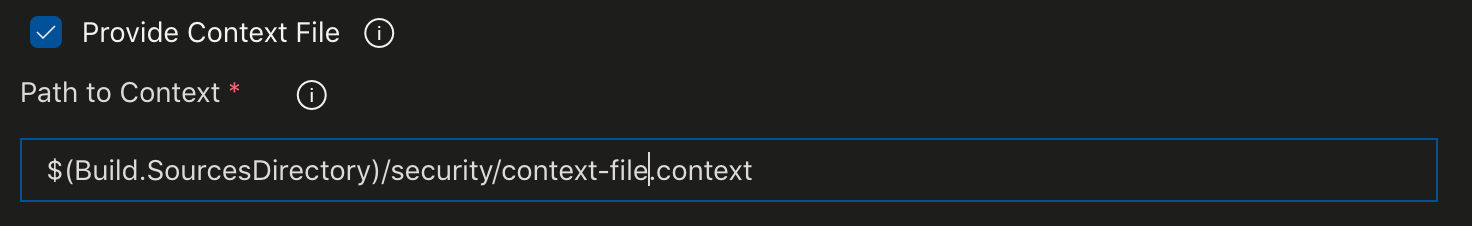
|
||||
|
||||
- ZAP contexts and context files are not within the scope of our documentation. [Please refer to ZAP's official documentation, here.](https://www.zaproxy.org/docs/desktop/start/features/contexts/)
|
||||
|
||||
- Finally, provide an optional port number for custom ports. By default, the scan will be interested in port 80 on the target system.
|
||||
|
||||
### Reporting Options
|
||||
|
|
|
|||
Загрузка…
Ссылка в новой задаче