зеркало из https://github.com/microsoft/DevSkim.git
Родитель
9c5a19ab8f
Коммит
e5c187dc1c
|
|
@ -1,33 +1,35 @@
|
|||
# README
|
||||
# DevSkim
|
||||
|
||||
DevSkim is a framework of IDE plugins and Language analyzers that provide inline security analysis in the dev environment as the developer writes code. It is designed to work with multiple IDEs (VS, VS Code, etc.), and has a flexible rule model that supports multiple programming languages. The idea is to give the developer notification as they are introducing a security vulnerability in order to fix the issue at the point of introduction, and to help build awareness for the developer.
|
||||
DevSkim is a framework of IDE extensions and language analyzers that provide inline security analysis in the dev environment as the developer writes code. It has a flexible rule model that supports multiple programming languages. The goal is to notify the developer as they are introducing a security vulnerability in order to fix the issue at the point of introduction, and to help build awareness for the developer.
|
||||
|
||||
## PUBLIC PREVIEW
|
||||
## Features
|
||||
|
||||
DevSkim is currently in public preview. We're looking forward to working with the community to improve both the scanning engines and rules over the next few months, and welcome your feedback and contributions! You can find us at https://github.com/Microsoft/DevSkim
|
||||
* Built-in rules, and support for writing custom rules
|
||||
* IntelliSense error "squiggly lines" for identified security issues
|
||||
* Information and guidance provided for identified security issues
|
||||
* Optional suppression of unwanted findings
|
||||
* Broad language support including: C, C++, C#, Cobol, Go, Java, Javascript/Typescript, Python, and [more](https://github.com/Microsoft/DevSkim/wiki/Supported-Languages).
|
||||
|
||||
## Usage
|
||||
|
||||
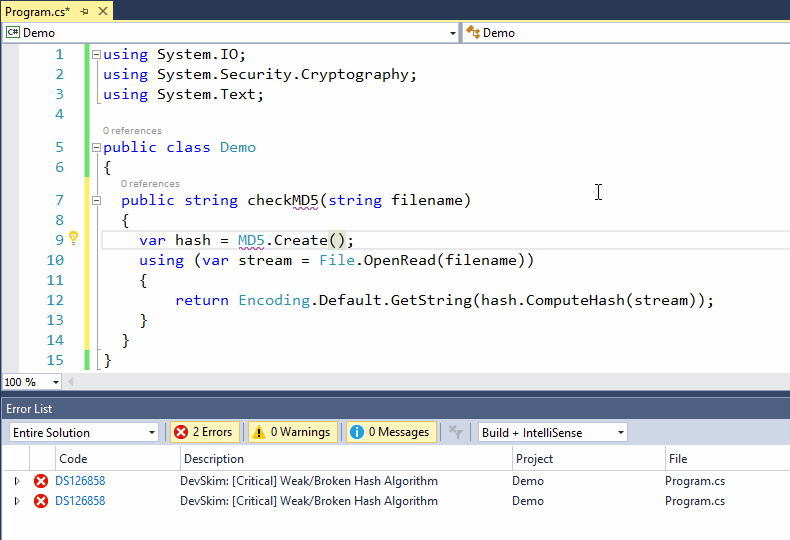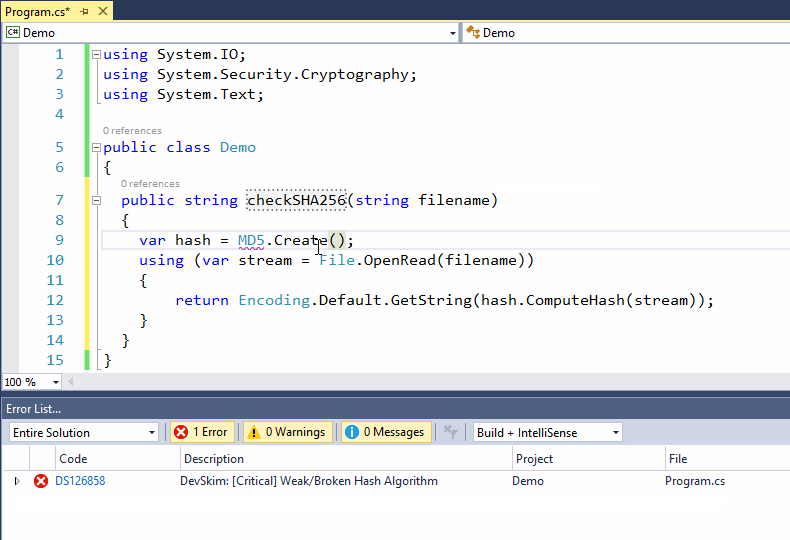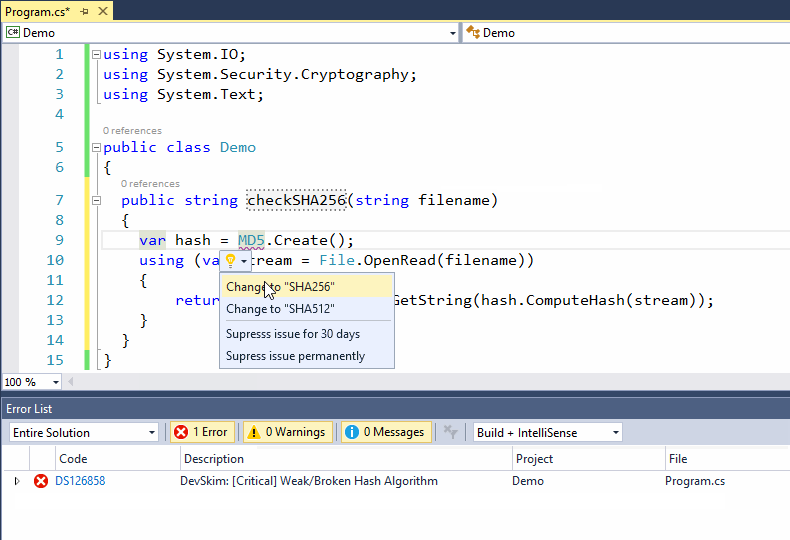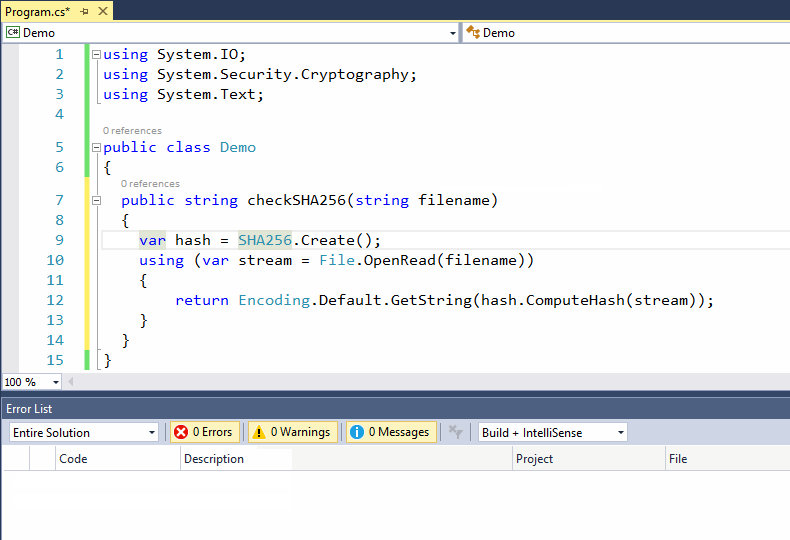
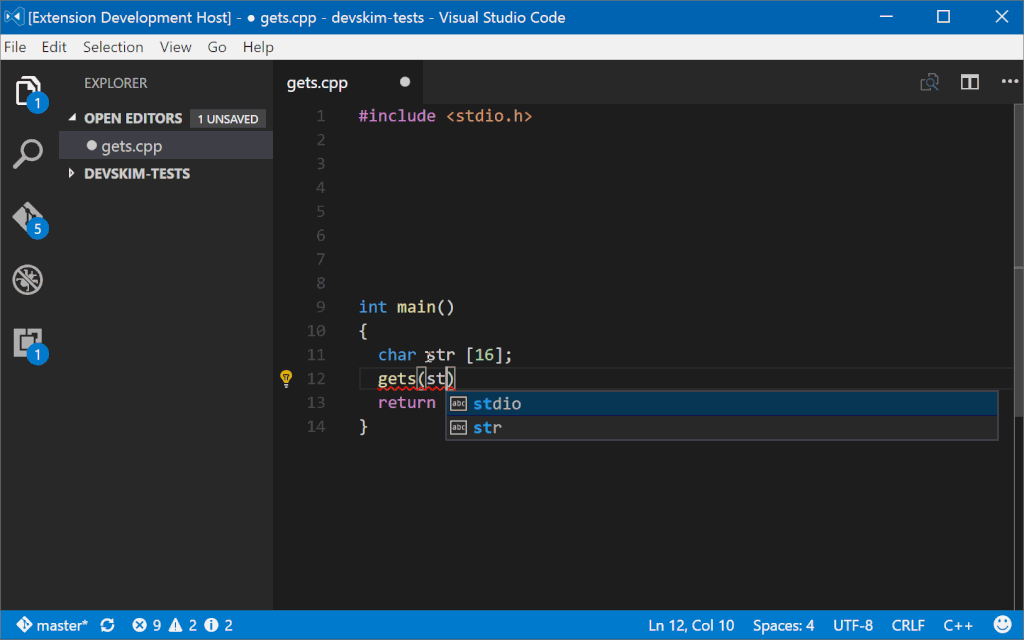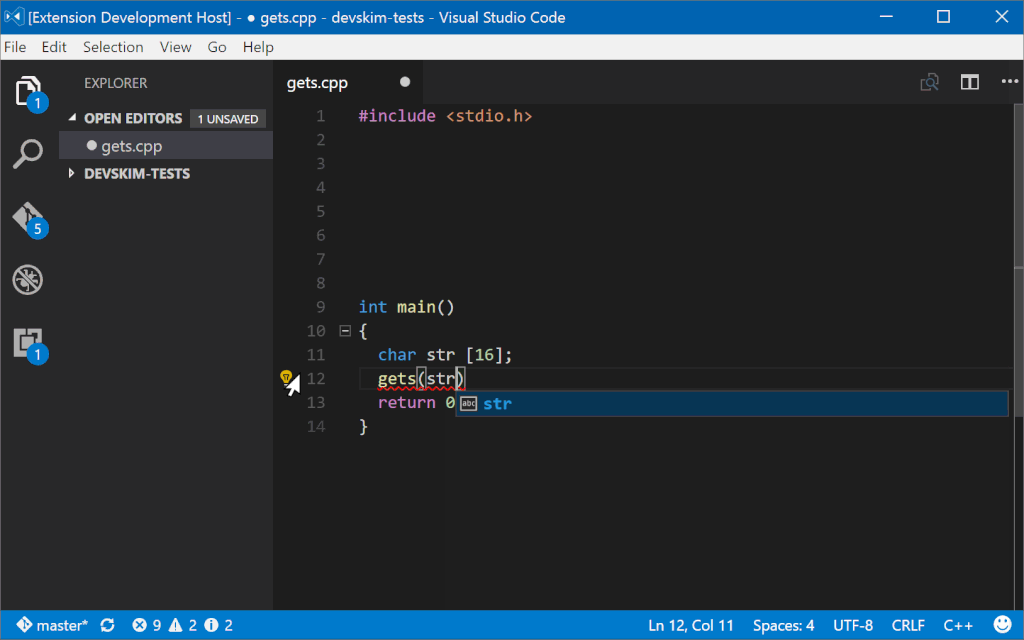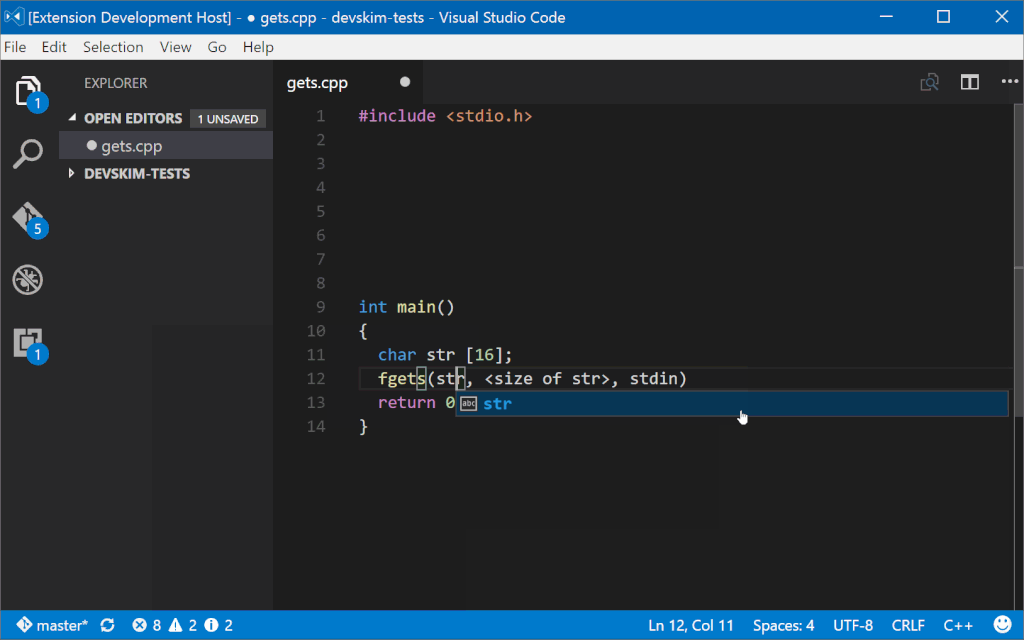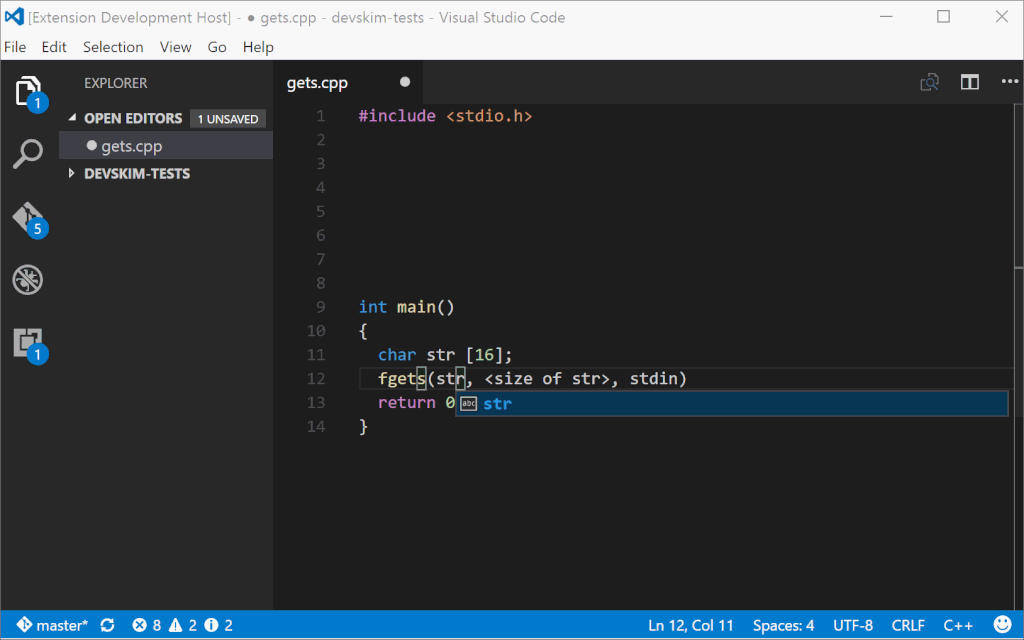
As a developer codes DevSkim will flag certain security issues and call attention to them with errors or warnings (depending on a very generalized estimation of the severity). Mousing over the issue will show a description of the problem and how to address it, and a link to more information. For some issues, one or more safe alternitives are available in the lightbulb menu so that the issue can be fixed with a couple mouse clicks. For issues where the alternitive has different parameters than the unsafe API that is called out, guidance for the parameters will be inserted in the form of \<some guidance info\> (example, when DevSkim turns gets() into fgets() it adds \<size of firstparamname\> to cue a user that they need to provide the size of the buffer).
|
||||
As a developer writes code, DevSkim will flag identified security issues and call attention to them with errors or warnings. Mousing over the issue will show a description of the problem and how to address it, with a link to more information. For some issues, one or more safe alternatives are available in the lightbulb menu so that the issue can be fixed automatically. For issues where the alternative has different parameters than the unsafe API that is called out, guidance for the parameters will be inserted in the form of \<some guidance info\>. For example, when DevSkim turns gets() into fgets() it adds \<size of firstparamname\> to inform a user that they need to provide the size of the buffer.
|
||||
|
||||

|
||||
|
||||
|
||||
### Suppressions
|
||||
|
||||
DevSkim has built in the ability to suppress any of its warnings, either permanently, or for a period of time. The permanent Suppressions are for scenarios where, for whatever reason, the flagged code shouldn't be changed. Timed Suppressions are for scenarios where the code should change, but the developer doesn't want to change it right now. In both cases, DevSkim will insert a comment after the code to notify it (and anyone reviewing the code) that the usage should be ignored, and in the case of timed suppressions, when DevSkim should alert of the usage again. Users can add additional comments after the suppression to describe why the issue is being suppressed.
|
||||
DevSkim has built-in ability to suppress any of its warnings, either permanently, or for a period of time. Permanent suppressions are for scenarios where, for whatever reason, the flagged code should not be changed. Timed suppressions are for scenarios where the code should change, but the developer does not want to change it immediately. In both cases, DevSkim will insert a comment after the code to notify it (and anyone reviewing the code) that the usage should be ignored, and in the case of timed suppressions, when DevSkim should alert again. Users can add additional comments after the suppression to describe why the issue is being suppressed.
|
||||
|
||||
For timed suppressions, the default period is 30 days, but this can be adjusted in the settings file.
|
||||
|
||||
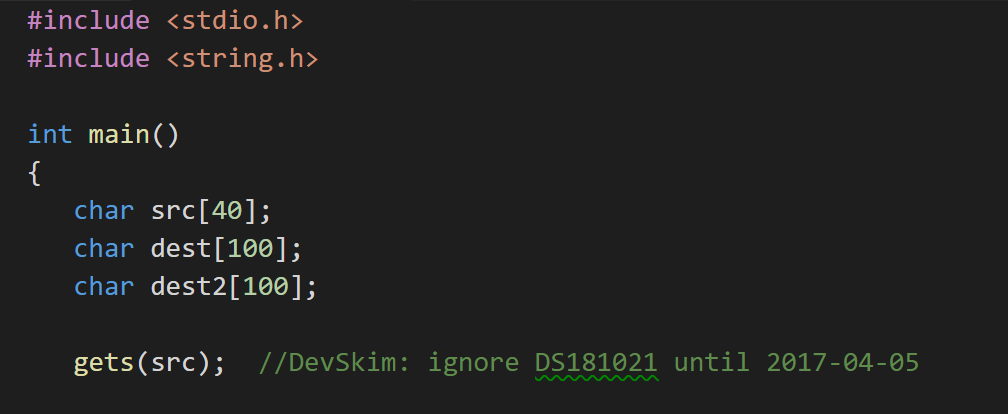
Suppressions can be accessed from the lightbulb menu. Once a suppression is added, DevSkim will highlight the issue number that identifies the check being suppressed (the gets() example above is issue number DS181021 for example), and mousing over will provide details. This will let other contributors to a project know what was suppressed, so that they aren't confused by the comment
|
||||
Suppressions can be accessed from the lightbulb menu. Once a suppression is added, DevSkim will highlight the issue number that identifies the check being suppressed (the gets() example above is issue number DS181021 for example), and mousing over will provide details. This will let other contributors to a project know what was suppressed, and reduce confusion about the comment.
|
||||
|
||||

|
||||
|
||||
|
||||
## Rules
|
||||
|
||||
## Programming Language Support
|
||||
|
||||
DevSkim takes an approach that is programming language agnostic. At this stage, it primarily finds issues via regular expression, so rules can be written for just about any programming language. Out of the box DevSkim can find dangerous crypto usage in most programming languages and has regular expressions for language specific issues for C/C++, Java, C#, JavaScript, PHP, and a number of other languages. We are growing our built in ruleset regularly, but we have also tried to make it very easy for people to write their own rules. All it requires is a passable knowledge of regular expressions and json. Details can be found [on our Github wiki](https://github.com/Microsoft/DevSkim/wiki/Writing-Rules)
|
||||
DevSkim takes an approach that is programming language agnostic. It primarily finds issues via regular expression, so rules can be written for just about any programming language. Out of the box, DevSkim can find dangerous crypto usage in most programming languages, and also includes rules for a range of language specific issues. The built-in ruleset is growing regularly, and it is very easy for users to write their own rules. For more information, see [Writing Rules](https://github.com/Microsoft/DevSkim/wiki/Writing-Rules).
|
||||
|
||||
## Thank You
|
||||
|
||||
Thanks for trying DevSkim. Its a work in progress. If you find issues please
|
||||
[report them on Github](https://github.com/Microsoft/DevSkim) and feel free to contribute!
|
||||
Thanks for trying DevSkim! If you find issues, please [report them on GitHub](https://github.com/Microsoft/DevSkim) and feel free to contribute!
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@
|
|||
<GeneratePackageOnBuild>false</GeneratePackageOnBuild>
|
||||
<PackageLicenseFile>LICENSE.txt</PackageLicenseFile>
|
||||
<copyright>© Microsoft Corporation. All rights reserved.</copyright>
|
||||
<Description>DevSkim is a framework and language analyzer that provides inline security analysis.</Description>
|
||||
<Description>DevSkim is a framework and language analyzer that provides inline security analysis. This is a library package. For the Dotnet Tool package, see Microsoft.CST.DevSkim.CLI.</Description>
|
||||
<PackageIcon>devskim-icon-128.png</PackageIcon>
|
||||
<PackageProjectUrl>https://github.com/Microsoft/DevSkim</PackageProjectUrl>
|
||||
<LangVersion>8.0</LangVersion>
|
||||
|
|
|
|||
|
|
@ -5,7 +5,6 @@
|
|||
.vscode
|
||||
.gitignore
|
||||
node_modules
|
||||
readme-gallery.md
|
||||
tsconfig.json
|
||||
|
||||
client/node_modules
|
||||
|
|
|
|||
|
|
@ -0,0 +1,35 @@
|
|||
# DevSkim
|
||||
|
||||
DevSkim is a framework of IDE extensions and language analyzers that provide inline security analysis in the dev environment as the developer writes code. It has a flexible rule model that supports multiple programming languages. The goal is to notify the developer as they are introducing a security vulnerability in order to fix the issue at the point of introduction, and to help build awareness for the developer.
|
||||
|
||||
## Features
|
||||
|
||||
* Built-in rules, and support for writing custom rules
|
||||
* IntelliSense error "squiggly lines" for identified security issues
|
||||
* Information and guidance provided for identified security issues
|
||||
* Optional suppression of unwanted findings
|
||||
* Broad language support including: C, C++, C#, Cobol, Go, Java, Javascript/Typescript, Python, and [more](https://github.com/Microsoft/DevSkim/wiki/Supported-Languages).
|
||||
|
||||
## Usage
|
||||
|
||||
As a developer writes code, DevSkim will flag identified security issues and call attention to them with errors or warnings. Mousing over the issue will show a description of the problem and how to address it, with a link to more information. For some issues, one or more safe alternatives are available in the lightbulb menu so that the issue can be fixed automatically. For issues where the alternative has different parameters than the unsafe API that is called out, guidance for the parameters will be inserted in the form of \<some guidance info\>. For example, when DevSkim turns gets() into fgets() it adds \<size of firstparamname\> to inform a user that they need to provide the size of the buffer.
|
||||
|
||||
|
||||
|
||||
### Suppressions
|
||||
|
||||
DevSkim has built-in ability to suppress any of its warnings, either permanently, or for a period of time. Permanent suppressions are for scenarios where, for whatever reason, the flagged code should not be changed. Timed suppressions are for scenarios where the code should change, but the developer does not want to change it immediately. In both cases, DevSkim will insert a comment after the code to notify it (and anyone reviewing the code) that the usage should be ignored, and in the case of timed suppressions, when DevSkim should alert again. Users can add additional comments after the suppression to describe why the issue is being suppressed.
|
||||
|
||||
For timed suppressions, the default period is 30 days, but this can be adjusted in the settings file.
|
||||
|
||||
Suppressions can be accessed from the lightbulb menu. Once a suppression is added, DevSkim will highlight the issue number that identifies the check being suppressed (the gets() example above is issue number DS181021 for example), and mousing over will provide details. This will let other contributors to a project know what was suppressed, and reduce confusion about the comment.
|
||||
|
||||
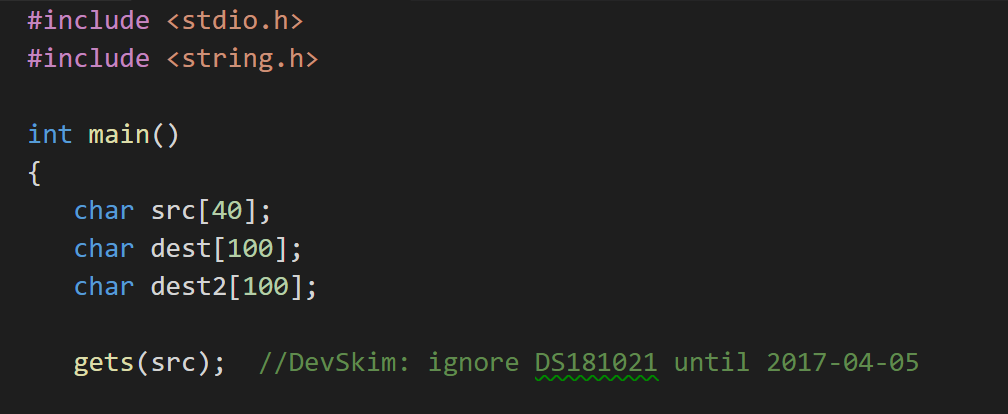
|
||||
|
||||
## Rules
|
||||
|
||||
DevSkim takes an approach that is programming language agnostic. It primarily finds issues via regular expression, so rules can be written for just about any programming language. Out of the box, DevSkim can find dangerous crypto usage in most programming languages, and also includes rules for a range of language specific issues. The built-in ruleset is growing regularly, and it is very easy for users to write their own rules. For more information, see [Writing Rules](https://github.com/Microsoft/DevSkim/wiki/Writing-Rules).
|
||||
|
||||
## Thank You
|
||||
|
||||
Thanks for trying DevSkim! If you find issues, please [report them on GitHub](https://github.com/Microsoft/DevSkim) and feel free to contribute!
|
||||
|
|
@ -1,40 +0,0 @@
|
|||
# README
|
||||
|
||||
DevSkim is a framework of IDE plugins and Language analyzers that provide inline security analysis in the dev environment as the developer writes code. It is designed to work with multiple IDEs (VS, VS Code, Sublime Text, etc.), and has a flexible rule model that supports multiple programming languages. The idea is to give the developer notification as they are introducing a security vulnerability in order to fix the issue at the point of introduction, and to help build awareness for the developer.
|
||||
|
||||
## PUBLIC PREVIEW
|
||||
|
||||
DevSkim is currently in public preview. We're looking forward to working with the community to improve both the scanning engines and rules over the next few months, and welcome your feedback and contributions! You can find us at https://github.com/Microsoft/DevSkim
|
||||
|
||||
## Usage
|
||||
|
||||
As a developer codes DevSkim will flag certain security issues and call attention to them with errors or warnings (depending on a very generalized estimation of the severity). Mousing over the issue will show a description of the problem and how to address it, and a link to more information. For some issues, one or more safe alternitives are available in the lightbulb menu so that the issue can be fixed with a couple mouse clicks. For issues where the alternitive has different parameters than the unsafe API that is called out, guidance for the parameters will be inserted in the form of \<some guidance info\> (example, when DevSkim turns gets() into fgets() it adds \<size of firstparamname\> to cue a user that they need to provide the size of the buffer).
|
||||
|
||||

|
||||
|
||||
### Suppressions
|
||||
|
||||
DevSkim has built in the ability to suppress any of its warnings, either permanently, or for a period of time. The permanent Suppressions are for scenarios where, for whatever reason, the flagged code shouldn't be changed. Timed Suppressions are for scenarios where the code should change, but the developer doesn't want to change it right now. In both cases, DevSkim will insert a comment after the code to notify it (and anyone reviewing the code) that the usage should be ignored, and in the case of timed suppressions, when DevSkim should alert of the usage again. Users can add additional comments after the suppression to describe why the issue is being suppressed.
|
||||
|
||||
For timed suppressions, the default period is 30 days, but this can be adjusted in the settings file.
|
||||
|
||||
Suppressions can be accessed from the lightbulb menu. Once a suppression is added, DevSkim will highlight the issue number that identifies the check being suppressed (the gets() example above is issue number DS181021 for example), and mousing over will provide details. This will let other contributors to a project know what was suppressed, so that they aren't confused by the comment
|
||||
|
||||

|
||||
|
||||
### Code Reviews
|
||||
|
||||
Most of DevSkim's rules are meant to be used by all developers, flagging programming practices that are generally bad for security. For example, the hashing function SHA-1 is broken, so generally should never be used. There are some scenarios where the security relevence is not as clear cut. For example, many dynamic languages support some form of eval() to create code on the fly. If an
|
||||
attacker can get their data into the eval function, they can get their own code created, but if there isn't a clear path for an attacker to manipulate the contents of eval() it is probably ok. For scenarios such as this, DevSkim is conservative and by default won't alert to the usage. However, if the user turns on the Manual Review rules in settings they will start seeing issues that take a bit of analysis to determine whether the usage is safe or dangerous. The intent is to make manual security code reviews a bit easier, by calling attention to *potentially* dangerous code. When the reviewer deems the code safe they can click on the lightbulb menu and mark it as reviewed. Similar to suppressions, DevSkim will no longer flag that usage, but will highlight the issue number in its comment so that other people seeing the comment can understand what was reviewed.
|
||||
|
||||
There is also a DevSkim setting to set the reviewer name (person's name, or github handle, etc.). If set, DevSkim will mark that the code was reviewed by that specific person.
|
||||
|
||||

|
||||
|
||||
## Programming Language Support
|
||||
|
||||
DevSkim takes an approach that is programming language agnostic. At this stage, it primarily finds issues via regular expression, so rules can be written for just about any programming language. Out of the box DevSkim can find dangerous crypto usage in most programming languages and has regular expressions for language specific issues for C/C++, Java, C#, JavaScript, PHP, and a number of other languages. We are growing our built in ruleset regularly, but we have also tried to make it very easy for people to write their own rules. All it requires is a passable knowledge of regular expressions and json. Details can be found [on our Github wiki](https://github.com/Microsoft/DevSkim/wiki/Writing-Rules)
|
||||
|
||||
## Thank You
|
||||
|
||||
Thanks for trying DevSkim. Its a work in progress. If you find issues please [report them on Github](https://github.com/Microsoft/DevSkim) and feel free to contribute!
|
||||
Загрузка…
Ссылка в новой задаче