зеркало из https://github.com/microsoft/SmartDump.git
Update README.md
This commit is contained in:
Родитель
02957ae624
Коммит
fc458b9174
17
README.md
17
README.md
|
|
@ -158,7 +158,6 @@ The following are several sample commands that uses the tool with Kudu debug con
|
|||
|
||||
|
||||
|
||||
|
||||
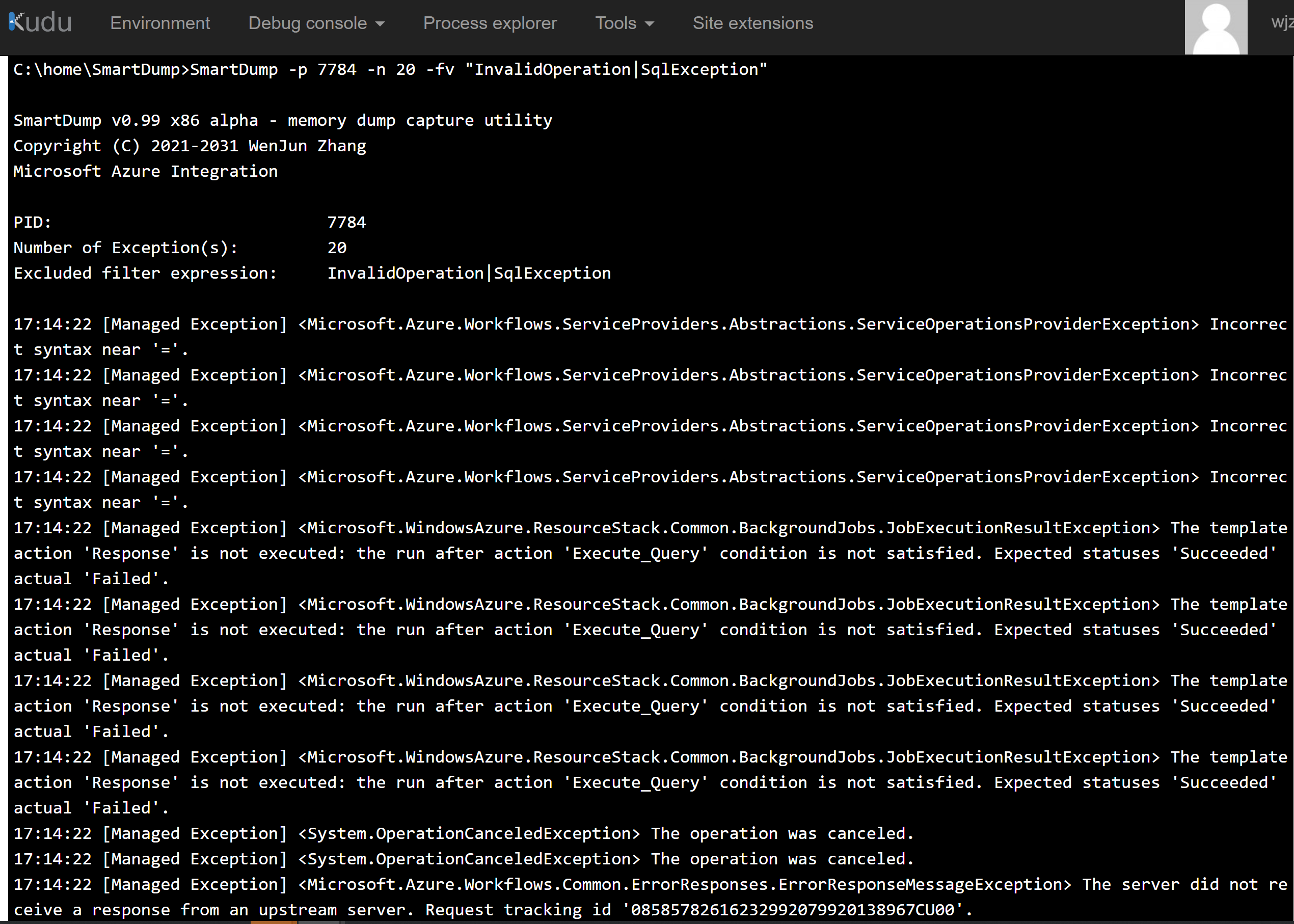
6) Collect dump based on specified address of breakpoint.
|
||||
|
||||

|
||||
|
|
@ -184,6 +183,22 @@ The following are several sample commands that uses the tool with Kudu debug con
|
|||
|
||||

|
||||
|
||||
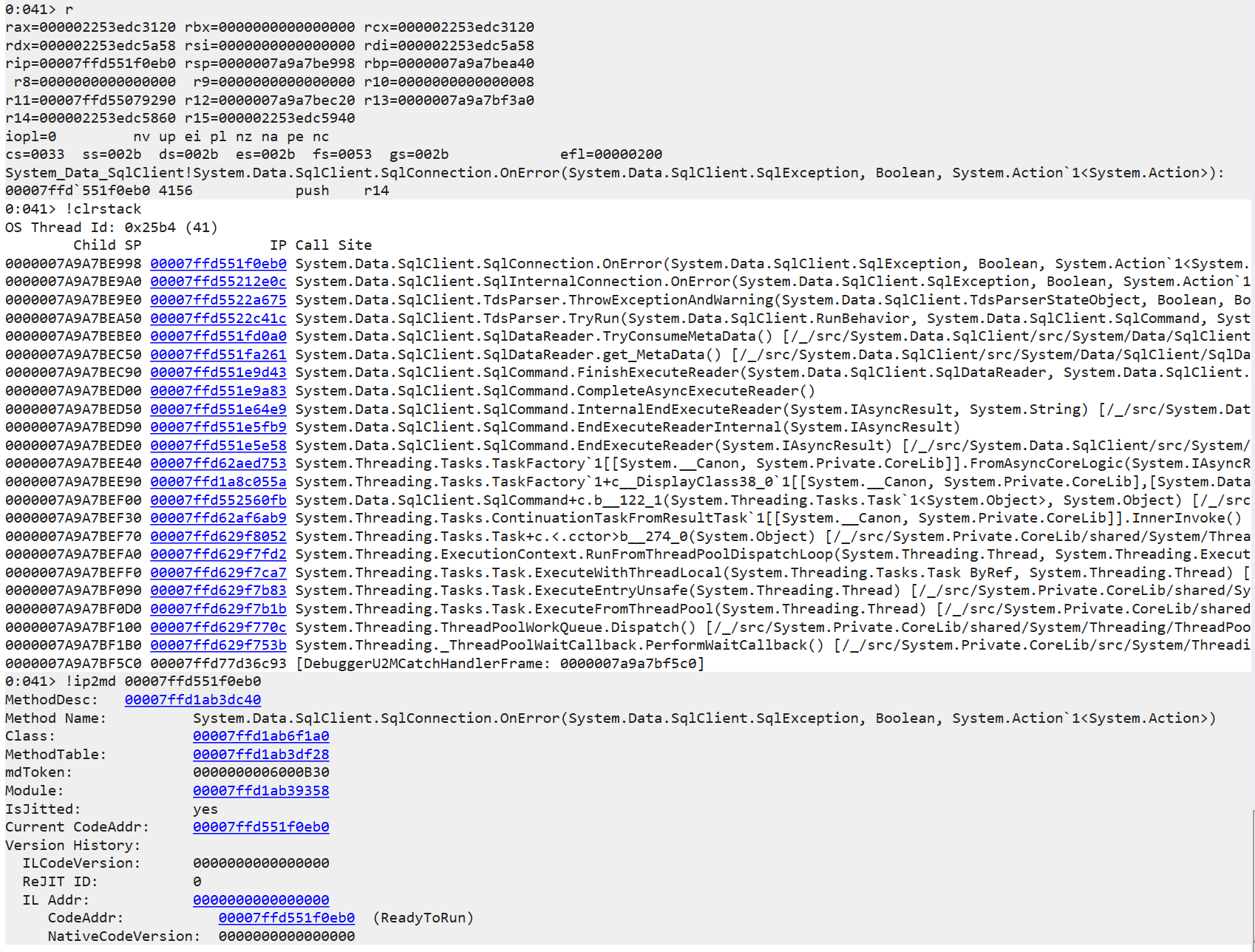
11) Display verbose output to list frames of managed callstack. Then we can utilize addresses from its output to set breakpoint with -a option.
|
||||
For example, a code entry address of a function can be used to dump its corresponding interested call:
|
||||
|
||||
SmartDump.exe -p 4567 -n 20 -v
|
||||
|
||||
The frame output indicates the entry code address of the first managed call that threw the exception is 0x00007ffd`551f0eb0.
|
||||
|
||||

|
||||
|
||||
So we use address: 00007ffd`551f0eb0 as breakpoint to capture dump with -a option:
|
||||
|
||||

|
||||
|
||||
As we can see, 00007ffd`551f0eb0 is just the entry address of function: System.Data.SqlClient.SqlConnection.OnError
|
||||
|
||||
|
||||
|
||||
# Project
|
||||
|
||||
|
|
|
|||
Загрузка…
Ссылка в новой задаче