* Run e2e integration tests after deployment * Add stage name * build * Take from vars, bump * rebase * Change path * retest Co-authored-by: sharon <sharon.hart@microsoft.com> |
||
|---|---|---|
| .github | ||
| .pipelines/templates | ||
| docs | ||
| e2e-tests | ||
| presidio-analyzer | ||
| presidio-anonymizer | ||
| presidio-image-anonymizer | ||
| .gitignore | ||
| .pre-commit-config.yaml | ||
| CONTRIBUTING.md | ||
| LICENSE | ||
| NOTICE | ||
| README.MD | ||
| SECURITY.MD | ||
| VERSION | ||
| azure-pipelines-ci.yml | ||
| azure-pipelines.yml | ||
| docker-compose.yml | ||
README.MD
Presidio - Data Protection and Anonymization API
Context aware, pluggable and customizable PII anonymization service for text and images.
What is Presidio
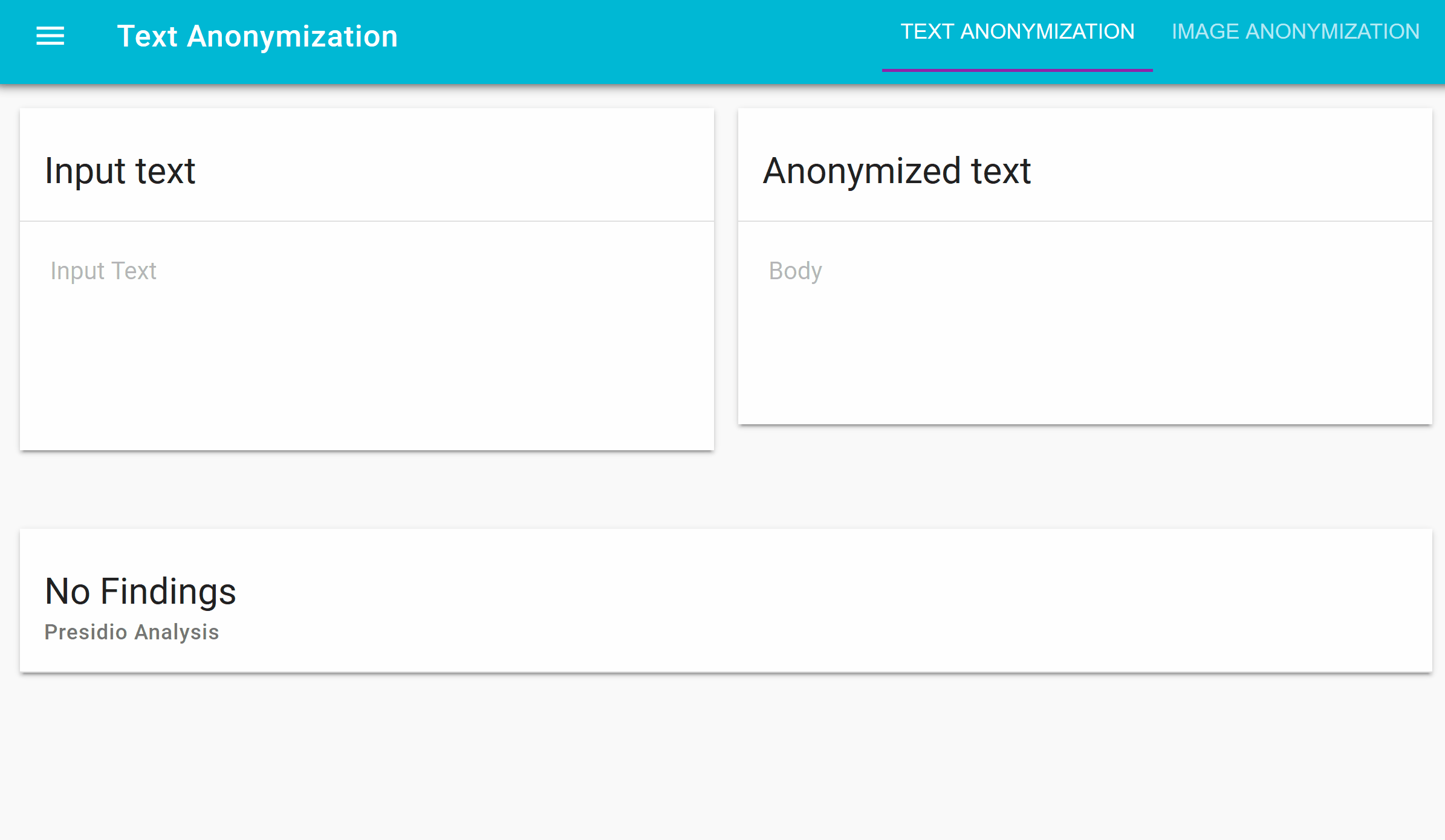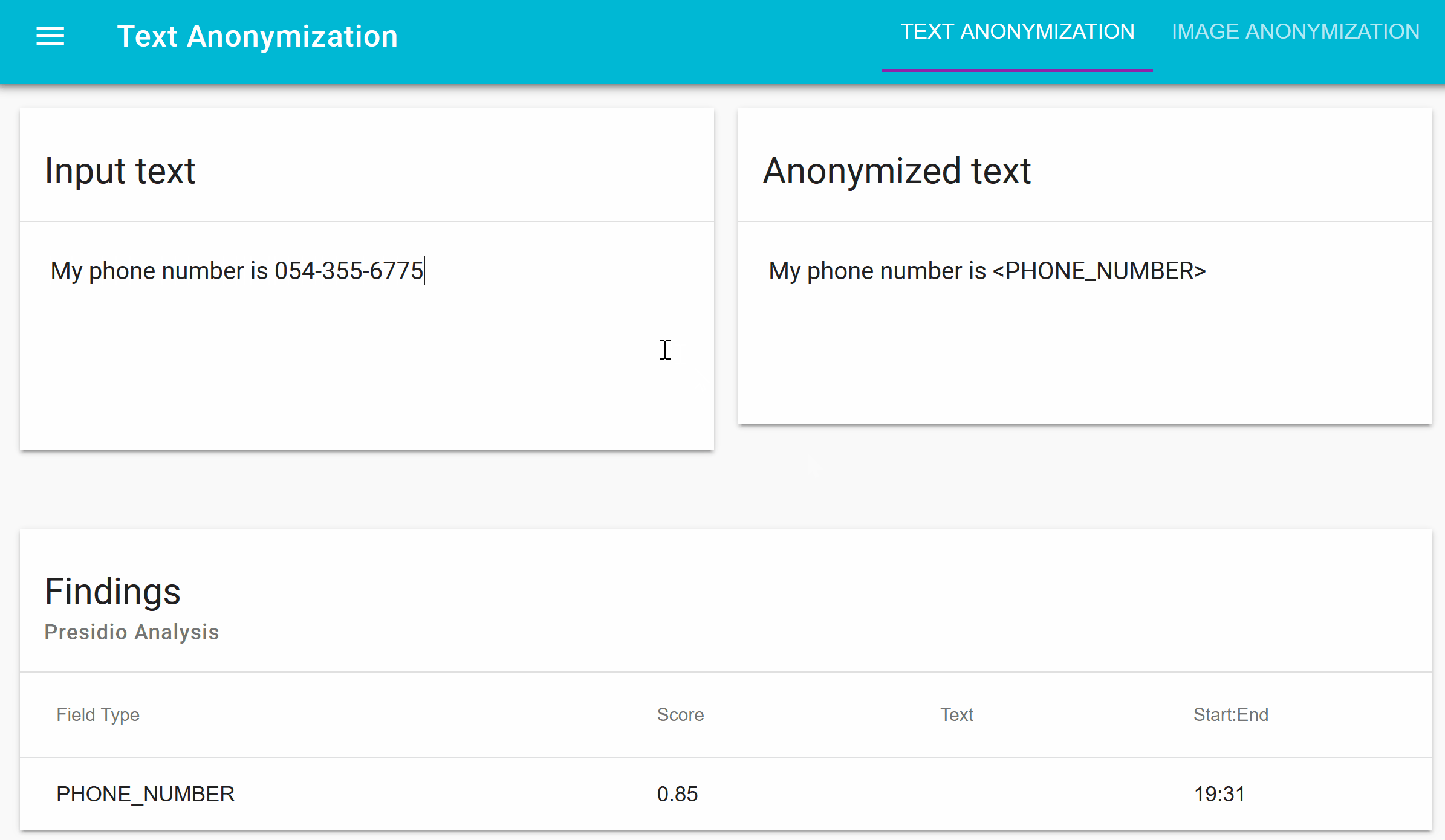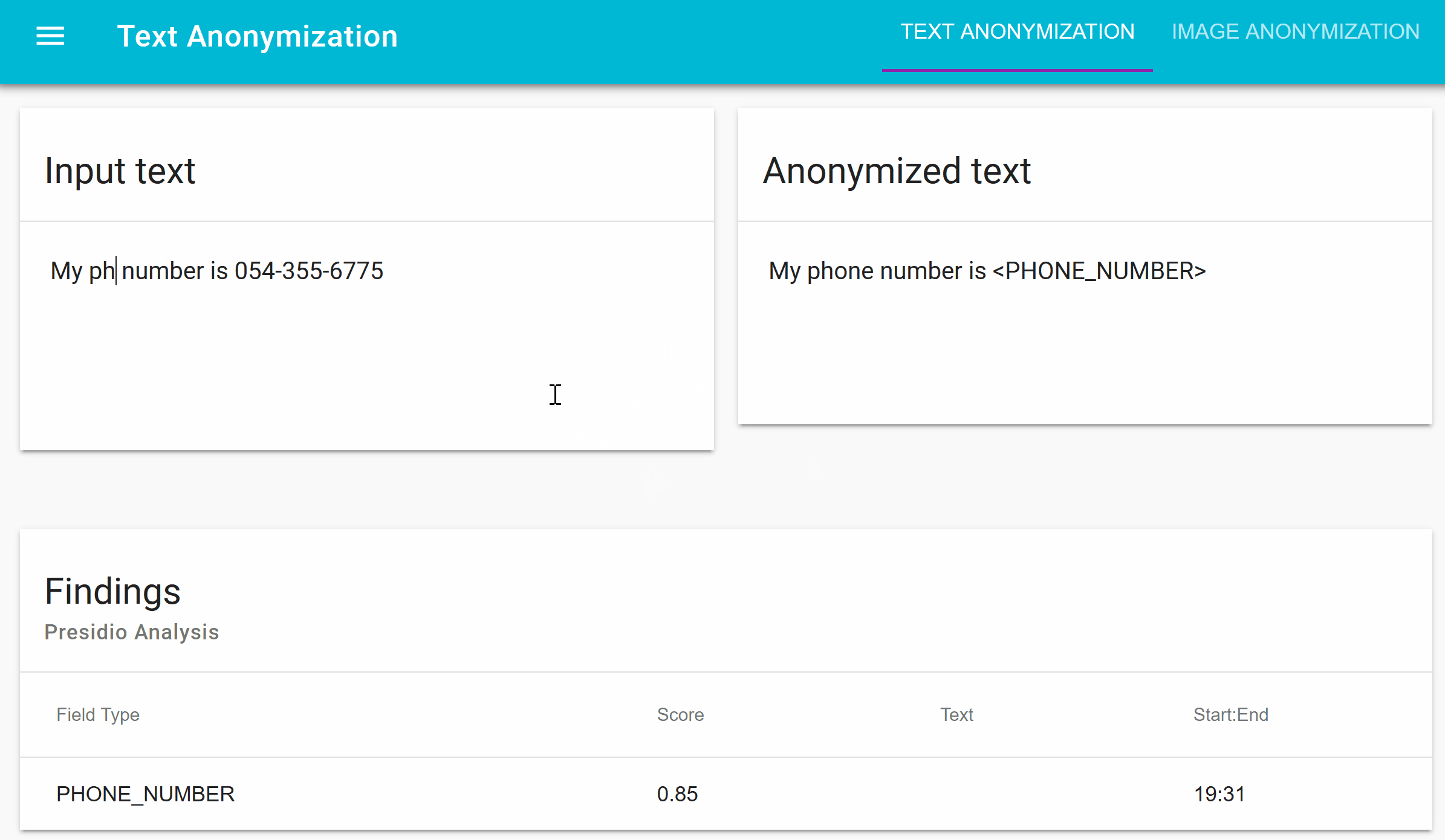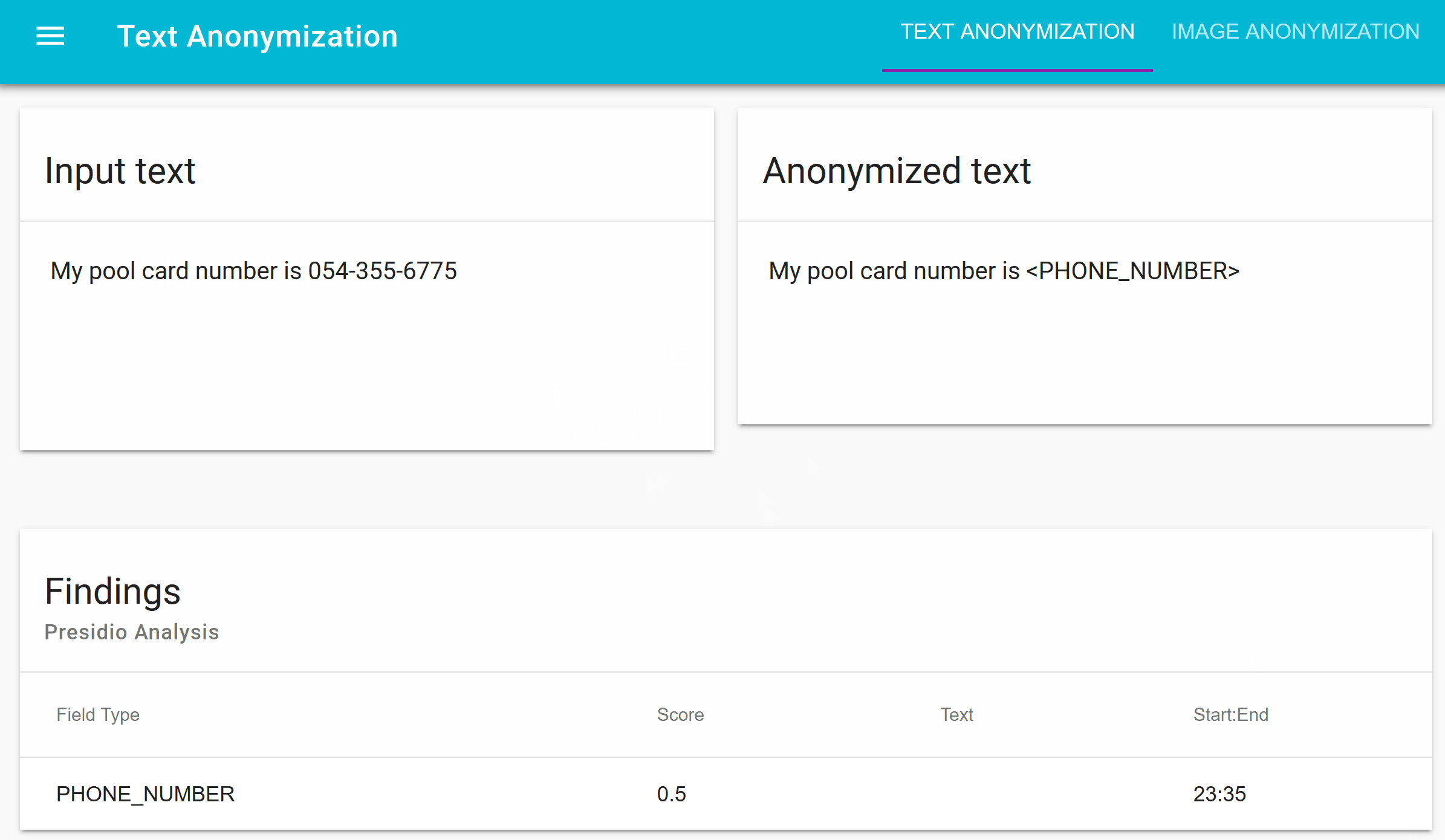
Presidio (Origin from Latin praesidium ‘protection, garrison’) helps to ensure sensitive data is properly managed and governed. It provides fast identification and anonymization modules for private entities in text such as credit card numbers, names, locations, social security numbers, bitcoin wallets, US phone numbers, financial data and more.
Goals
- Allow organizations to preserve privacy in a simpler way by democratizing de-identification technologies and introducing transparency in decisions.
- Embrace extensibility and customizability to a specific business need.
- Facilitate both fully automated and semi-automated PII de-identification flows on multiple platforms.
Main features
- Predefined or custom PII recognizers leveraging Named Entity Recognition, regular expressions, rule based logic and checksum with relevant context in multiple languages.
- Options for connecting to external PII detection models.
- Multiple usage options, from Python or PySpark workloads through Docker to Kubernetes.
- Customizability in PII identification and anonymization.
- Module for redacting PII text in images.
⚠️ Presidio can help identify sensitive/PII data in un/structured text. However, because Presidio is using trained ML models, there is no guarantee that Presidio will find all sensitive information. Consequently, additional systems and protections should be employed.
Demo
Try Presidio with your own data
Installing Presidio
Running Presidio
- Running Presidio via code
- Running Presidio as an HTTP service
- Setting up a development environment
- Perform PII identification using presidio-analyzer
- Perform PII anonymization using presidio-anonymizer
- Perform PII identification and anonymization in images using presidio-image-anonymizer
- Example deployments
Support
- Before you submit an issue, please go over the documentation. For general discussions, please use the Github repo's discussion board.
- If you have a usage question, found a bug or have a suggestion for improvement, please file a Github issue.
- For other matters, please email presidio@microsoft.com.
Contributing
For details on contributing to this repository, see the contributing guide.
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit https://cla.microsoft.com.
When you submit a pull request, a CLA-bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., label, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.