2014-02-11 21:39:17 +04:00
|
|
|
MIG: Mozilla InvestiGator
|
|
|
|
|
=========================
|
2013-12-05 20:27:03 +04:00
|
|
|
|
2014-11-03 05:52:22 +03:00
|
|
|
**Note: MIG is under heavy development. The code is unstable, and non-backward compatible changes are still in progress. Be warned.**
|
|
|
|
|
|
2014-06-29 20:58:45 +04:00
|
|
|
MIG is OpSec's platform for investigative surgery of remote endpoints.
|
|
|
|
|
|
|
|
|
|
MIG is composed of agents installed on all systems of an infrastructure. The
|
|
|
|
|
agents can be queried in real-time using a messenging protocol implemented in
|
|
|
|
|
the MIG Scheduler. MIG has an API, a database, RabbitMQ relays and a console
|
|
|
|
|
client. It allows investigators to send actions to pools of agents, and check
|
2014-02-07 20:40:39 +04:00
|
|
|
for indicator of compromision, verify the state of a configuration, block an
|
2014-06-29 20:58:45 +04:00
|
|
|
account, create a firewall rule, update a blacklist and so on.
|
2013-12-05 20:27:03 +04:00
|
|
|
|
2014-04-02 01:49:35 +04:00
|
|
|

|
|
|
|
|
|
2014-02-07 20:40:39 +04:00
|
|
|
For example: an investigator launches an action to search for an apache module
|
|
|
|
|
that matches a given md5 value. MIG will register the action, find all the
|
2014-06-29 20:58:45 +04:00
|
|
|
relevant targets and send commands to each target agent with the detail of the
|
|
|
|
|
action. Each agent then individually runs the action using built-in modules,
|
|
|
|
|
and sends the results back to the MIG platform.
|
2014-02-07 20:40:39 +04:00
|
|
|
|
|
|
|
|
Agents are designed to be lightweight, secure, and easy to deploy. All
|
|
|
|
|
parameters are built into the agent at compile time, include the list of
|
|
|
|
|
investigator's public keys. The agent binary is statically compiled for a target
|
2014-06-29 20:58:45 +04:00
|
|
|
platform and can be shipped without any external dependency. Deploying an agent
|
|
|
|
|
is as easy as `wget -O /sbin/mig-agent https://fileserver/mig-agent && /sbin/mig-agent`
|
2014-02-07 20:40:39 +04:00
|
|
|
|
|
|
|
|
MIG is designed to be fast, and asynchronous. It uses AMQP to distribute actions
|
|
|
|
|
to endpoints, and relies on Go channels to prevent components from blocking.
|
|
|
|
|
Running actions and commands are stored on disk cache, and don't rely on running
|
|
|
|
|
processes for reliability.
|
|
|
|
|
|
|
|
|
|
Speed is a strong requirement. Most actions will only take a few hundreds
|
|
|
|
|
milliseconds to run. Larger ones, for example when looking for a hash in a large
|
2014-06-29 20:58:45 +04:00
|
|
|
directory, should run in less than a minute or two.
|
|
|
|
|
|
|
|
|
|
Privacy and security are paramount. Agents never send raw data back to the
|
|
|
|
|
platform, but only reply to questions instead. All actions are signed by GPG
|
|
|
|
|
keys that are not stored in the platform, thus preventing a compromision from
|
|
|
|
|
taking over the entire infrastructure.
|
2014-02-07 20:40:39 +04:00
|
|
|
|
2014-10-11 23:04:35 +04:00
|
|
|
Discussion
|
|
|
|
|
----------
|
|
|
|
|
Join **#mig** on [irc.mozilla.org](https://wiki.mozilla.org/IRC)
|
2014-02-11 21:07:51 +04:00
|
|
|
|
2014-07-26 00:02:53 +04:00
|
|
|
Video presentation
|
|
|
|
|
------------------
|
|
|
|
|
|
|
|
|
|
Check out this 10 minutes video for a more general presentation and a demo of
|
|
|
|
|
the console interface.
|
|
|
|
|
|
|
|
|
|
[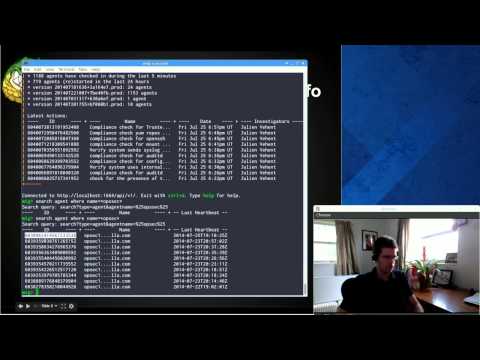](http://www.youtube.com/watch?v=wJwj5YB6FFA)
|
2014-02-11 21:07:51 +04:00
|
|
|
|
2014-02-07 20:40:39 +04:00
|
|
|
Goals
|
|
|
|
|
-----
|
|
|
|
|
|
|
|
|
|
* Query a pool of endpoints to verify the presence of a specific indicators
|
|
|
|
|
(similar to IOC, but we use a different format)
|
|
|
|
|
* Provide response mechanisms to lock down compromised endpoints
|
2014-06-29 20:58:45 +04:00
|
|
|
* Periodically verify endpoint's compliance with the security requirements
|
2014-02-07 20:40:39 +04:00
|
|
|
|
|
|
|
|
Features
|
|
|
|
|
--------
|
|
|
|
|
* Provide strong authentication of investigators
|
|
|
|
|
* Actions must have a valid GPG signature, each investigator has a different
|
|
|
|
|
key, for tracking.
|
|
|
|
|
* Provide a way to inspect remote systems for indicators of compromise (IOC).
|
|
|
|
|
At the moment, this is limited to :
|
|
|
|
|
* file by name
|
|
|
|
|
* file content by regex
|
|
|
|
|
* file hashes: md5, sha1, sha256, sha384, sha512, sha3_224,sha3_256,
|
|
|
|
|
sha3_384, sha3_512
|
2014-06-29 20:58:45 +04:00
|
|
|
* connected IPs
|
2014-02-07 20:40:39 +04:00
|
|
|
* Protect data security, investigate without intruding:
|
|
|
|
|
* Raw data must not be readily available to investigators
|
|
|
|
|
|
2014-06-29 20:58:45 +04:00
|
|
|
In the work:
|
2014-02-07 20:40:39 +04:00
|
|
|
* More agent modules
|
|
|
|
|
* low level devices (memory, file system blocks, network cards)
|
2014-06-29 20:58:45 +04:00
|
|
|
* firewall rules (read & write)
|
|
|
|
|
* network sniffer
|
|
|
|
|
* accounts creation & destruction
|
2014-02-07 20:40:39 +04:00
|
|
|
* lots more ...
|
|
|
|
|
* Provide response mechanisms, including:
|
|
|
|
|
* dynamic firewall rules additions & removal
|
|
|
|
|
* system password changes
|
|
|
|
|
* process execution (execve) & destruction (kill)
|
|
|
|
|
* Input/Output IOCs, Yara, ... through the API
|
|
|
|
|
* Output results in standard format for alerting
|
2014-06-29 20:58:45 +04:00
|
|
|
* Investigation console
|
|
|
|
|
|
2014-07-25 08:01:10 +04:00
|
|
|
[](https://www.youtube.com/watch?v=3MeN0cN79L4)
|
2014-02-07 20:40:39 +04:00
|
|
|
|
|
|
|
|
Documentation
|
|
|
|
|
-------------
|
|
|
|
|
All documentation is available in the 'doc' directory.
|
2014-07-25 06:11:59 +04:00
|
|
|
* [Concepts & Internal Components](doc/concepts.rst)
|
|
|
|
|
* [Installation & Configuration](doc/configuration.rst)
|
2014-05-22 22:20:24 +04:00
|
|
|
|
|
|
|
|
Bug & Issue tracker
|
|
|
|
|
-------------------
|
|
|
|
|
We use Bugzilla to track the work on MIG.
|
|
|
|
|
* List open bugs: [Bugzilla MIG](https://bugzilla.mozilla.org/showdependencytree.cgi?id=896480&hide_resolved=1)
|
|
|
|
|
* Create a new bug: [Bugzilla OpSec](https://bugzilla.mozilla.org/enter_bug.cgi?product=mozilla.org&component=Security%20Assurance%3A%20Operations)
|
|
|
|
|
|