Use Workload identity federation with the AzOps
Introduction
GitHub Actions and Azure Pipelines can make use of OpenID Connect (OIDC) for secure deployments to Azure, which uses short-lived tokens that are automatically rotated for each deployment. In the context of AzOps, this means we can allow the AzOps pipeline Service Principal/User-assigned managed identity to access Azure Resource Manager and Azure AD with federated credentials, eliminating the need to create/handle secrets.
This wiki explains how this feature can be used and configured with AzOps.
Configure
Before you start to configure the workload federation feature in Azure AD and changing the GitHub Actions or Azure DevOps Pipelines, ensure that you have followed the instructions at https://github.com/azure/azops/wiki/prerequisites and have your Service Principal/User-assigned managed identity ready with appropriate RBAC permissions.
GitHub
Important: For this feature to work with the current implementation of Workload identities, we take a dependency on Environments for GitHub Actions. Environments are only available in public repositories for free. Access to environments in private repositories requires GitHub Enterprise.
How to setup GitHub Actions with workload identity federation:
Note: The starter GitHub pipelines in AzOps-Accelerator have been updated to support federated credentials. Consider performing an update using the update pipeline.
-
Validate that you have the latest version (post february 2023) of sharedSteps/action.yml, pull.yml, push.yml, redeploy.yml and validate.yml.
-
Uncomment the line with environment definition in pull.yml, push.yml, redeploy.yml and validate.yml. Change the environment name to reflect your environment names.
environment: prod # Environment if using Federated Credentials (https://github.com/azure/azops/wiki/oidc) -
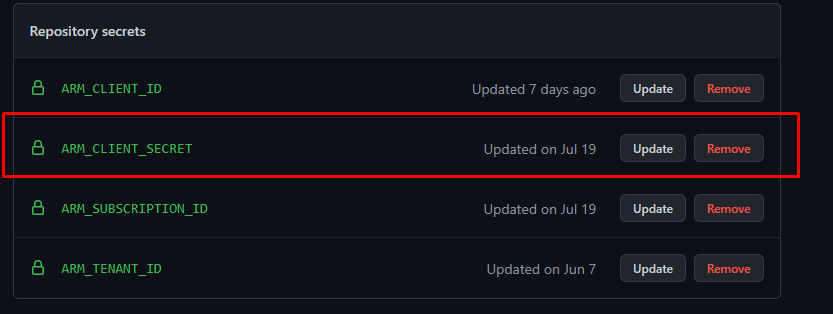
Remove all references to
ARM_CLIENT_SECRETfrom the repository/environment secrets. IfARM_CLIENT_SECRETexists, the pipeline will try to connect with the secret instead. -
Test the Pull, Push and Validate pipelines to ensure authentication works with federated credential.
Azure Pipelines
How to setup Azure DevOps Pipelines with workload identity federation:
Note: The starter Azure Pipelines in AzOps-Accelerator have been updated to support federated credentials. Consider performing an update using the update pipeline.
-
Validate that you have the latest version (post october 2023) of templates/sharedSteps.yml and templates/vars.yml.
-
Remove the
ARM_CLIENT_SECRETvariable from thecredentialsvariable group. IfARM_CLIENT_SECRETexists, the pipeline will try to connect with the secret instead. -
Test the Pull, Push and Validate pipelines to ensure authentication works with federated credential.
Resources
Read more about the functionality in the official docs below:
Navigation
Getting started
Documentation
- Settings
- Updates
- Steps
- Deployments
- Resources Deletion Feature
- Feeds
- Self-hosted agents/runners
- Roadmap
- Troubleshooting
- FAQ