24 KiB

Illusive Active Defense Sentinel Solution
Instructions for configuring, running, and using the Illusive Active Defense Sentinel solution.
Table of Contents
- Executive summary
- Basic requirements
- Workflow
- Locate the Sentinel workspace
- Azure application setup
- Generate an Illusive API key
- Configure Illusive to send logs to a Linux-based syslog server
- Deploy solution package or deploy playbooks
- Configure the Illusive analytic rule
- Access and view the playbook
Executive summary
Configure Sentinel and load custom playbooks to have Illusive open Sentinel incidents, populate them with Illusive-based information, and automate incident response.
This solution contains the following components:
-
Incident Enrichment playbook – leverages Sentinel analytic rules to discover Illusive-based alerts and report the associated data and forensics as Sentinel incident sets.
Use this playbook to enrich Sentinel security incidents originating from Illusive with Illusive incident and forensics information. Illusive continues to enrich relevant Sentinel incidents as new events are detected. This is done using the Illusive API resource. -
Incident Response playbook – leverages CrowdStrike or Microsoft Defender for Endpoint integration to automate incident response when specified Illusive incidents are discovered.
Use this playbook to quickly stop or slow down ransomware attacks and critical incidents detected by Illusive in your organization. Upon detection, Sentinel is instructed to use the triggering process information reported by Illusive remove or kill the process. If the triggering process cannot be killed, Sentinel is instructed to isolate the host. These capabilities are available for organizations with CrowdStrike Falcon or Microsoft Defender for Endpoint. -
Analytic Rule - Trigger a Sentinel alert upon detecting an Illusive event and create a Sentinel incident. The Sentinel incident will correspond to the Illusive incident and will include all subsequent associated Illusive events. The Illusive solution playbooks require the analytic rule to operate.
Basic requirements (set up in advance)
To use the Illusive Active Defense solution, you must have the following:
- An Azure AD subscription with a configured Sentinel workspace
- An Illusive ADS (deceptions) license
- A Linux-based syslog server. To set up the syslog server, see these instructions from Microsoft. Then, go to Data connectors, find and select the CEF connector
Workflow
- Locate the Sentinel workspace
- Azure application setup
- Generate an Illusive API key
- Configure Illusive to send logs to a Linux-based syslog server
- Configure and deploy playbooks
- Configure the Illusive analytic rule
Locate the Sentinel workspace
The workspace name, as well as the Subscription and resource group it belongs to are required later on during this configuration.
Steps to locate the Sentinel Workspace name, subscription, and resource group:
- In the Azure portal, go to Azure Sentinel.
- Type "Azure Sentinel" in the Search bar, or click on the Azure Sentinel icon.
- On the Azure Sentinel page, in the list, find the workspace where you want to create the playbook and its associated API connection.

- Make a note of the workspace Name, resource group, and Subscription. You will need these during playbook deployment.
Azure application setup
The Illusive solution playbooks run with an Azure application with the required API permissions.
This procedure sets out the general registration and configuration requirements that apply to both the Incident Enrichment and Incident Response playbooks.
Register an Azure app
-
If you have access to multiple tenants, in the top menu, use the Directory + subscription filter to select the tenant in which you want to register the application.

-
Search for and select Azure Active Directory.
-
Under Manage, select App registrations>New registration.The Register an application page appears.
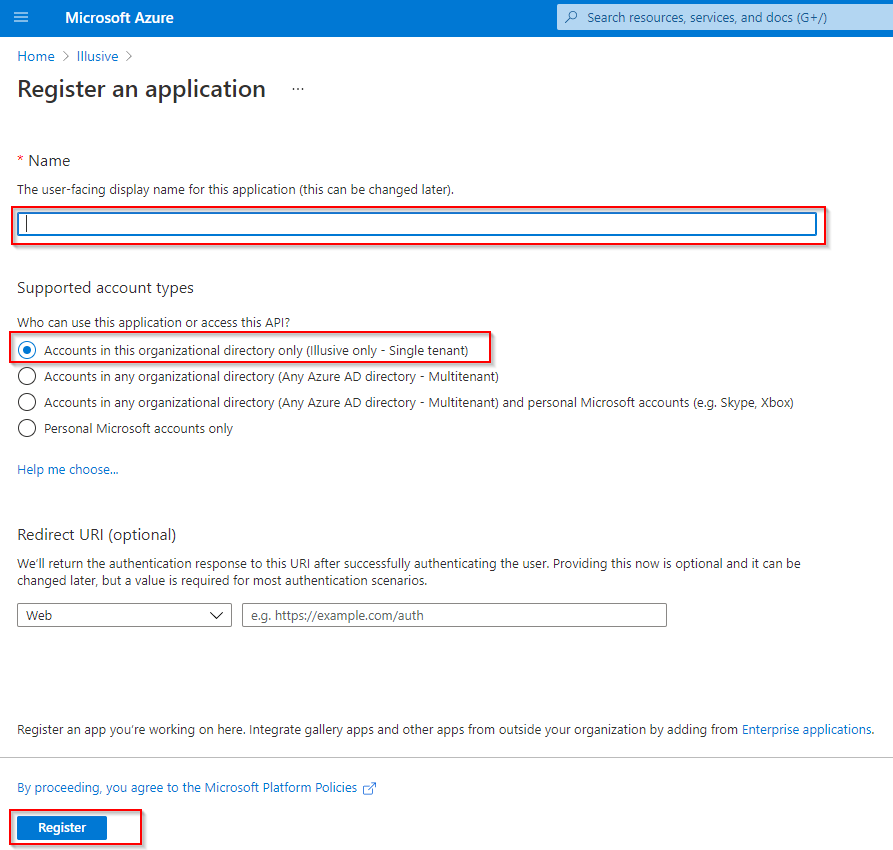
-
Specify a Name for your application.
Conform to company naming conventions. Do not use “illusive” or any other word that might reveal the existence of Illusive in the environment.
-
Under Supported account types, select Accounts in this organizational directory only.
-
To complete the initial app registration, click Register.
Collect app information
You need the Application (client) ID and the Directory (tenant) ID to configure Illusive solution playbooks.
-
Go to the created application’s Overview page.
-
Copy and save the Application (client) ID and the Directory (tenant) ID. You need this information to configure the Illusive playbooks.
Generate and save a Client Secret
You need specify a secret Value to configure Illusive solution playbooks.
- Click Certificates & Secrets.
- Click New Client Secret.
- Add a Description for the Client Secret.
- Select an Expiry date for the Client Secret (recommended 6 months).
- Click Add.
- Copy and save the secret Value. You need this information to configure Illusive playbooks.
Add the User Impersonation API permission
The user_impersonation permission is used to read Azure Sentinel incidents.
Additional API permissions are required for the Incident Response playbook. These are specified in the Incident Response playbook deployment instructions.
- From the Azure console, find the Azure app you created to run the Illusive Sentinel Solution.
- Go to API Permissions.
- Click Add a permission.
- Under Microsoft APIs, select Azure Service Management.
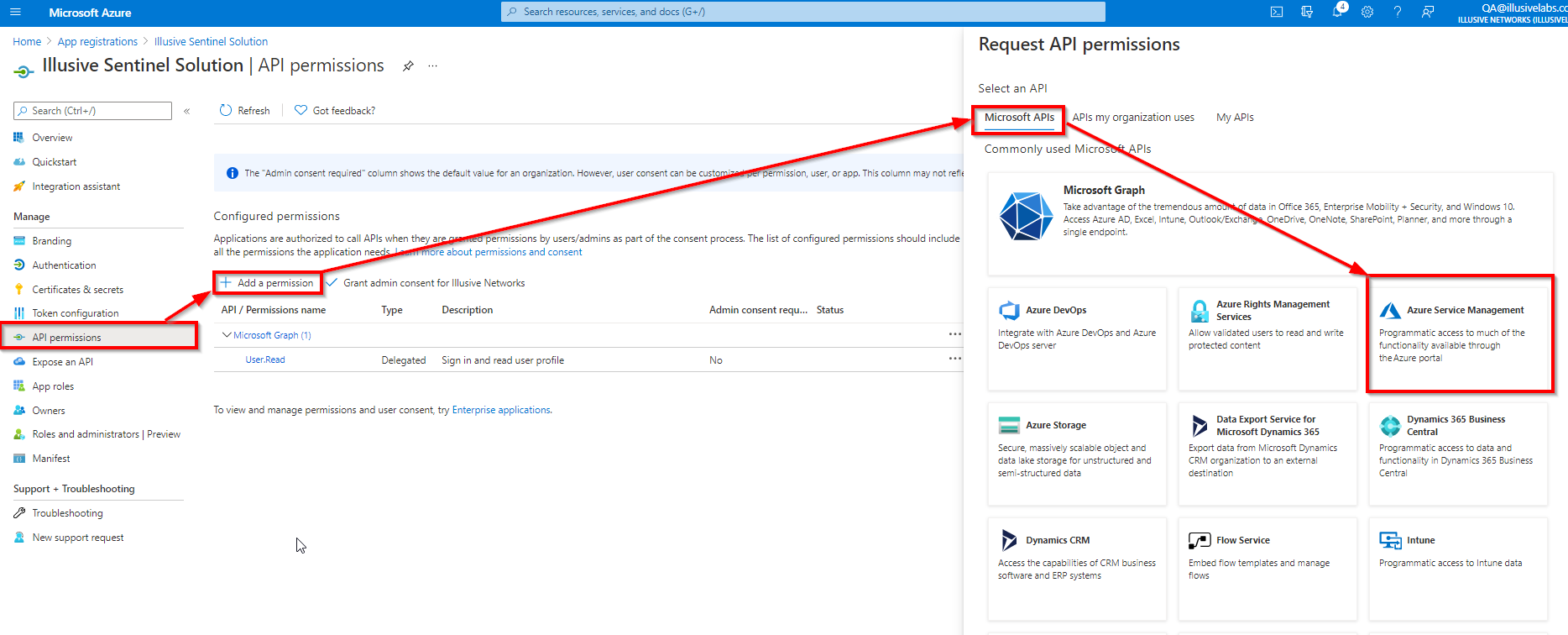
- Select Delegated permissions, check user_impersonation, and click Add permissions.

- Click Grant admin consent for Default Directory and click Yes.

- Verify admin consent has been granted. This step is important, even if the admin consent status is green. Only a Global Admin can approve admin consent requests.
- Go to Enterprise>Admin Consent requests.
- Go to My pending and verify that this permission is not pending.
Generate an Illusive API key
You need the Illusive REST API URL and an Illusive API key to configure Illusive solution playbooks.
-
In the Illusive Console, navigate to Settings>General>API Keys.
-
Enter values in the following fields:
Field Description and values Description Specify description of key.
- All Permissions
- Create Event Read
- Monitoring DataPermissions Select the permission: Restrict SourceIP Limit the API key to be used only from the specified source IP address. (optional) -
Click Add API key. The API Key is created and added to the list of keys shown.
-
Copy the header containing the key to a text file and save it securely. The key is valid for one year to access the REST API on this Management Server only.
-
To get the Illusive API URL, click REST API Documentation. This opens the Swagger API page. Copy the URL from the browser address bar.
Configure Illusive to send logs to a Linux-based syslog server
Configure Illusive to automatically send Illusive activity logs and event messages to a Linux based Syslog server. Every Syslog message also contains an Illusive incident ID. Sentinel will consume this information and trigger the Illusive solution playbooks.
If you haven't yet configured the syslog server, see these instructions from Microsoft. Then, go to Data connectors and find and select the Common event format connector.
- In the Illusive Console, navigate to Settings>Reporting and scroll down to Syslog Servers.

- In the Host Name server field, supply the server IP address or host name.
- In the Port field, supply the Syslog server’s communication port. (Default 514)
- From the Protocol dropdown menu, select TCP.
Recommendation: For high reliability, select the TCP protocol. - From the Audit messages drop-down menu, select one of the following (either option is okay; this integration only requires the event messages):
Option Description Send audit messages to server Sends Illusive event and audit messages to your Syslog server Don’t send audit messages to server Sends only Illusive event messages and system health data to your Syslog server - Click Add.
Deploy solution package or deploy playbooks
There are several paths for deploying the Illusive Sentinel solution.
- Deploy the complete solution package. Continue with Deploy the solution package below.
- Deploy just the Incident Enrichment playbook, go to Incident Enrichment Playbook.
- Deploy just the Incident Response playbook, go to Incident Response Playbook.
Deploy the solution package
- Before deploying the Illusive solution package, download the mainTemplate.json from the GitHub repository using this link.
- The playbook should be deployed under the same resource group, subscription, and workspace as the Azure app.
- The Illusive API key should contain only the API key and no keywords such as “Bearer” or “Basic”.
- You will not be prompted for missing information when saving the custom deployment configuration. If the playbook is incorrect or incomplete, the incident response playbook will not be able to isolate hosts, and you will get a playbook execution level error message.
-
On Azure home page, filter for Deploy a custom template.

-
Under Custom Deployment>Select a template, click Build your own template in the editor.

-
From Edit template, click Load file, the mainTemplate.json file provided by Illusive and click Save.


-
Under Custom Deployment>Basics:
- Specify the Subscription that contains the dedicated Azure app that will run the Illusive Sentinel solution
- Specify the Resource group that contains the Workspace where you want to install the playbook.
- Under Instance details:
Field Instructions Region Filled automatically based on the subscription and cannot be changed. Location Specify the resource group location. Workspace-location Specify the workspace location. Workspace Specify the Azure Sentinel Workspace Name where you want to create the playbook. Analytic1-id Specify the id of the Illusive analytic rule. Illusive API URL
Illusive API KeySupply the authentication parameters required to access the Illusive API Important: Enter the API key without the keyword Azure-Sentinel Client ID:
Azure-Sentinel Client Secret:
Azure-Sentinel Tenant ID:Supply the authentication parameters required to access the Azure-Sentinel API EDR deployed The EDR which is deployed in the organization and can be used for incident mitigation
Note Though it is possible to enter integration information for both CrowdStrike and Microsoft Defender for Endpoint, the Illusive solution requires you to select just one tool for incident response.CrowdStrike API URL
CrowdStrike Client ID
CrowdStrike Client SecretIf EDR deployed = CrowdStrike, specify CrowdStrike authentication parameters
Note Use the generic CrowdStrike API URL: . The playbook will fail to execute if the URL contains a hyphen which is not supported by Sentinel (i.e., certain region-specific URLs).Azure MDE Client ID
Azure MDE Client Secret
Azure MDE Tenant IDIf EDR deployed = MDE, specify MDE authentication parameters 
-
When finished entering details, click Review + Create.

-
On successful validation, click Create.

-
Perform steps 2, 3 and 5 in the Incident Response playbook workflow:
- Add API permissions to the Azure app for incident response capabilities.
- Enable Microsoft Defender for Endpoint
- Connect the playbook to Azure Sentinel
- Continue with Configure the Illusive analytic rule below.
Configure the Illusive analytic rule
The analytic rule instructs Azure Sentinel to search for information of interest and to supply this information to the Illusive solution playbooks.
-
Log onto http://portal.azure.com/
-
Click Azure Sentinel.
-
Select the resource group and workspace in which the Illusive playbooks are deployed.
-
Select Analytics.
-
Click Create>Scheduled query rule and click Next.
-
Enter the analytics rule details:
Field Instructions Name Specify a display name for the rule. (e.g., “Illusive analytic rule”) Description Add a description for what the rule does. Description Add a description for what the rule does.
E.g.: Triggers a Sentinel alert upon detecting an Illusive event and creates a Sentinel incident. The Sentinel incident will correspond to the Illusive incident and will include all subsequent associated Illusive events.Tactics Do not select any tactics. Severity Select the severity level of incidents created by the Illusive solution.
Recommended severity level: HighStatus Ensure the rule is Enabled. 
-
When finished entering Analytic rule details, click Next: Set rule logic.
-
In Set rule logic, under Rule query, copy and paste the following KQL query: Note: You can skip this step if you deployed the complete solution package using the mainTemplate.json, which automatically configures the rule query.
CommonSecurityLog | where DeviceProduct == "illusive" | extend DeviceCustomNumber2 = coalesce(column_ifexists("FieldDeviceCustomNumber2", long(null)), DeviceCustomNumber2, long(null)), | summarize arg_max(TimeGenerated, *) by DeviceCustomNumber2, AdditionalExtensions, TimeGenerated | extend Category = coalesce(column_ifexists("DeviceEventCategory", ""), extract(@'cat=([^;]+)(\;|$)', 1, AdditionalExtensions), ""), HasForensics = extract(@'cs7=([^;]+)(\;|$)', 1, AdditionalExtensions) | where Category == "illusive:alerts" | extend isHostIsolated = false | extend isProcessIsolated = false
-
Under Alert Enrichment, expand Entity Mapping and add entities as below:
- Host > FullName : SourceHostName
- IP > Address : SourceIP
- Host > OMSAgentID : Computer

-
Under Alert Enrichment, expand Custom details and add key-value pairs as below:
- isHostIsolated : isHostIsolated
- isProcessIsolated : isProcessIsolated
- IllusiveIncidentId : DeviceCustomNumber2
- HasForensics : HasForensics
- Account : SourceUserName

-
Under Alert Enrichment, expand Alert details, and configure the following fields:
- Alert Name Format: Illusive Incident: {{DeviceCustomNumber2}}
- Alert Description Format: {{DeviceCustomNumber2}} generated at {{TimeGenerated}}

-
Under Query scheduling, configure the following details:
- Run query every = “5 minutes”. This is because the minimum time for an analytic rule to trigger is 5 minutes.
- Lookup data from the last = “5 minutes”. This is because the lookup data (Illusive incidents inserted in Azure Sentinel) will run only for 5 minutes.

-
Under Alert Threshold, set Generate alert when number of query results “is greater than 0”.

-
Under Event grouping, select Trigger an alert for each event (preview).

-
Keep Suppression “Off”.
-
Click Next.
-
On the Incident setting (Preview) tab, enable Create incidents from alerts triggered by this analytics rule.
-
Enable Alert Grouping.
Note: Up to 150 alerts can be grouped into a single incident. If more than 150 alerts are generated, a new incident will be created with the same incident details as the original. Additional alerts will be grouped into the new incident. -
Under Alert Grouping, select the time range during which an alert’s associated events will be grouped into a single incident in the Sentinel system. (This can be configured based on customer requirements)

-
Under Group alerts triggered by this analytics rule into a single incident by, select Grouping alerts into a single incident if the selected entity types and details match: and select the IllusiveIncidentId entity as in the image below:
-
Enable Re-open closed matching incidents to allow incidents to be reopened.

-
On Automated response tab, from the dropdown list under the Alert automation section, select the configured Illusive solution playbooks:
- **IllusiveSentinelIncidentEnrichment **
- **IllusiveSentinelIncidentResponse **
-
Then, click Next:Review.
-
On the Review and create tab, review all the entered data, and click Save.
The new analytic rule can be seen in the Analytics>Active rules table.
Access and view a playbook
You can view and manage Illusive playbooks as well as review playbook run history. This can be helpful for understanding how the playbook responds when triggered, and for troubleshooting.
- Find the playbook on the Azure Sentinel or All resources pages.
- Click on the playbook to view the playbook run History.
- Select any executed playbook to view the results.
Sample playbook history (incident response):




