2.2 KiB
2.2 KiB
Identity Protection - response from Teams
author: Lior Tamir
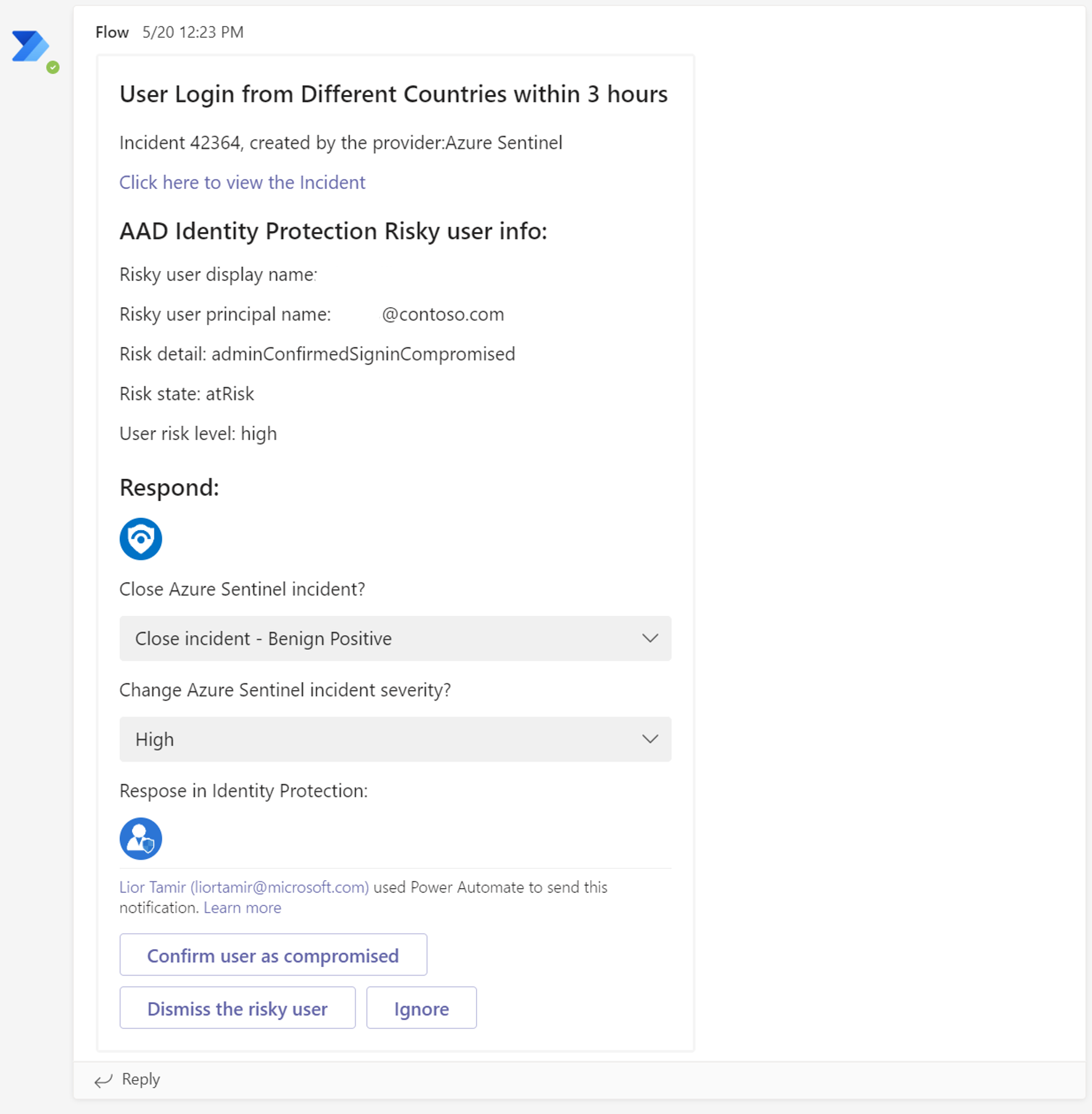
Run this playbook on incidents which contains suspicious AAD identities. When a new incident is created, this playbook iterates over the Accounts. It then posts an adaptive card in the SOC Microsoft Teams channel, including the potential risky user information given by Azure AD Identity Protection. The card offers to confirm the user as compromised or dismiss the compromised user in AADIP. It also allows to configure the Azure Sentinel incident. A summary comment will be posted to document the action taken and user information. Learn more about Azure AD Identity Protection
Prerequisites
- Using the riskyUsers API requires an Azure AD Premium P2 license.
- Have a user which has permissions on Identity Protection API. Learn more
- (optional) Create policies in Azure AD Identity protection to run when users are confirmed as compromised. Learn more
Card to be sent by Microsoft Teams bot:
Documentation references:

