This pr is auto merged as it contains a mandatory file and is opened for more than 10 days. |
||
|---|---|---|
| AzureB2BInvite | ||
| B2BPortal | ||
| B2BPortal.Common | ||
| B2BPortal.Data | ||
| B2BPortal.Interfaces | ||
| B2BPortalDeploy | ||
| BatchInviteProcessor | ||
| DocImages | ||
| .gitignore | ||
| B2BPortal.sln | ||
| CodeMap1.dgml | ||
| CustomDeploy.ps1 | ||
| Deploy-AzureResourceGroup.ps1 | ||
| LICENSE | ||
| README.md | ||
| SECURITY.md | ||
| Setup.md | ||
| azuredeploy.json | ||
| azuredeploy.parameters.json | ||
README.md
Azure Active Directory/ASP.Net MVC/GraphAPI B2BPortal
Sample/Prototype project enabling self-service B2B capabilities for an Azure AD Tenant
This code is a sample to demonstrate the Azure Active Directory B2B Invitation API. It was last updated in 2017.
If you wish to enable users from other organizations to request access, and upon approval be provisioned with guest accounts and assigned to groups, apps and SharePoint Online sites, then instead use Azure AD entitlement management to configure policies that manage access for external users.
Quick Start
Detailed step-by-step deployment instructions
Update (Notes here will be reflective of any changes made in the most recent update.)
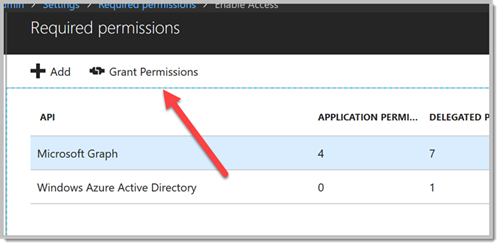
An additional permission is required to facilitate batch processing with automatic directory addition.
- DELEGATED PERMISSIONS
- Access the directory as the signed-in user
This permission will allow a guest user, that has been added to the "Guest Inviter" role, to invite additional guests from their home directory. Those guests are automatically added as new guests without needing to go through an invitation redemption process. They will have immediate, automatic access. The list of groups that can be assigned to these guests are limited to groups where the inviting guest is already a member.
After adding this permission, because user's previous consents will be invalidated, you will need to click "Grant Permissions" to update the consents for users in the tenant.
Details
- Allows self-service provisioning of guest accounts in a tenant. Portal enables this via API calls to the Microsoft Graph
- Leverages Azure CosmosDB. For development, a downloadable emulator is available: https://aka.ms/documentdb-emulator
- ARM template deploys the following:
- Azure Web App
- Azure CosmosDB
- Requires the following (see step-by-step deployment instructions above for details):
- Azure AD application with the following:
- Microsoft Graph - app permissions
- Read and write directory data
- Read and write all users' full profiles
- Microsoft Graph - delegated permissions
- Sign in and read user profile
- Azure AD application with the following:
- Microsoft Graph - delegated permissions
- Sign in and read user profile
- Multi-Tenant enabled
- Optional - custom DNS name and SSL cert
Operation
- Guests access the home page and may enter their login email to request access to the host tenant/company. Optionally, they may click to "Require Sign-In" - this will allow them to login to the guest's home tenant, authenticate, then return with the form pre-filled AND with the request authenticated and validated.
- Once the request is submitted, the request will be queued in a CosmosDB repo.
- A user in the home company with the "Guest Inviter" role granted can then access the portal, log in, and browse the pending requests, either approving, denying, or leaving in a pending state for others to review. Additionally, internal comments can be attached to the request records.
- Optionally, authorized users may login and add a "Partner Organization" profile record. This will allow potential guests with a matching domain suffix, to be optionally auto-approved for B2B guest access in the tenant.
- Whether a user is automatically approved, or manually approved, once an approval occurs, a welcome email is generated to the requester with a link that allows for redemption of the request.
As-Is Code
This code is made available as a sample to demonstrate usage of the Azure Active Directory B2B Invitation API. It should be customized by your dev team or a partner, and should be reviewed before being deployed in a production scenario.
Contributing
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.